- PGP Guide for Mac OSX
- GPGTools
- One simple package with everything you need, to protect your emails and files.
- GPG Mail
- GPG Keychain
- GPG Services
- MacGPG
- GPG Suite at a glance
- It’s all about the keys
- Create your own key
- Upload your key to a key server so your friends can find it
- Already an expert?
- See all your keys
- The toolbar
- More options
- Add additional email addresses
- Write secure messages with Mail
- The lock button
- The sign button
- Choose between PGP and S/MIME
- Receive secure messages with Mail
- Signed messages
- Encrypted or signed attachments
- Sometimes things go wrong
- Find out what went wrong
- GnuPG: Безопасная почта для Win, Mac и *nix
- Скачивание
- Установка
- Создание ключей
- Использование
- Переписка
- Финал
PGP Guide for Mac OSX
Part 0 – Introduction
Here’s my basic guide for PGP on OS X. The OS in question is OS X 10.9 Mavericks, but it should still work for other versions. As for the tool itself, we’ll be using GPG Suite Beta 5. This is my first time using OS X in… years. If you see anything I’m doing wrong, or could be done easier, feel free to correct me in the comments.
If you’ve done your research, you’ll see it’s not recommended to do anything darknet related on OS X, but I’m not going to go over the details here. You’ve obviously made your decision.
Part 1 – Installing the software
Like I said above, we’ll be using GPG Suite Beta 5. If you’re curious and want to see the source code, you can do so here.
- Head on over to https://gpgtools.org, and download ‘GPG Suite Beta 5′
- Open the file you downloaded, you should see this screen. Double click on ‘Install’
- Follow the installation process. If successful, you should see this screen. You can now close the window
Part 2 – Creating your keypair
GPG Suite actually makes this a super simple process. Just like the Linux guide, we’ll be using 4096 bit length for encryption.
- Open up GPG Keychain, you should be greeted by this beautiful window
- Click ‘New’ at the top left of the window
- You should see a small popup. Click the arrow beside ‘Advanced options’, make sure the key length is 4096. For our purposes, we’ll uncheck ‘key expires’. Put your username where it says ‘full name’, fill out what you want for email, and create a secure passphrase. Check the picture for an example on how to fill it out. When complete, click ‘Generate key’
- GPG Keychain will begin generating your key. Move the mouse around, mash keys in a text editor, have something downloading. Do random stuff to create entropy for a secure key.
- annndddddd we’re done!
Part 3 – Setting up the environment
This is where OS X differs from other platforms. The suite itself doesn’t provide a window to encrypt/decrypt messages, so we need to enable some options.
- Go into system preferences, open up ‘Keyboard’
- You should see this window. Click the ‘Keyboard Shortcuts’ tab at the top, then ‘Services’ in the left pane. Scroll down in the right pane to the subsection labeled ‘Text’, and to the OpenPGP options. Here you can create keyboard shortcuts. We’ll uncheck everything OpenPGP that’s under ‘Text’, and delete their shortcuts. Now we’ll enable ‘Decrypt’, ‘Encrypt’, and ‘Import key’. Create keyboard shortcuts for these if you wish. Check the picture to make sure you’re doing everything correctly. You can now close the window.
Part 4 – Obtaining your public key
This part is super simple.
- Open up GPG Keychain, select your key
- At the top of the window, click ‘Export’
- Give it a name, make sure ‘include secret key in exported file’ is unchecked, and click ‘save’
- Open your text editor of choice, browse to where you saved the key, open it
- There it is. Copy and paste this on your market profile to make it easier for people to contact you
Part 5 – Obtaining your private key
Again, super simple.
- Open up GPG Keychain, select your key
- At the top of the window, click ‘Export’
- Keep the file name it gives you, check ‘Include secret key in exported file’, then click save
Keep this file in a safe place, and don’t forget your passphrase. You’re fucked without it!
Part 6 – Importing a public key
This is really easy.
- Find the key you want to import.
- Copy everything from ‘—–BEGIN PGP PUBLIC KEY BLOCK—–‘ to ‘—–END PGP PUBLIC KEY BLOCK—–‘
- Paste it into your favourite text editor, highlight everything, right click, go to ‘Services’, then ‘OpenPGP: Import key’
- You’ll see this window pop up confirming the key has been imported, click ‘Ok’
- Open up GPG Keychain just to confirm the key is there
Part 7 – Importing a private key
Again, really easy.
- Open GPG Keychain, click ‘Import’ at the top
- Browse to where your key is, click it, then click ‘Open’. It should have a .asc file extension
- You’ll see this pop up confirming your key has been imported. Click ‘Close’
Part 8 – Encrypting a message
- Open your text editor of choice, write your message
- Highlight the message, right click, ‘Services’, ‘OpenPGP: Encrypt’
- A window should appear. Select who you’re sending it to, sign it with your key if you wish, click ‘Ok’
- Copy everything, and send it to the recipient
Part 9 – Decrypting a message
Pretty much the same process as encrypting
- Open your text editor of choice, paste the message
- Highlight everything, right click, ‘Services’, ‘OpenPGP: Decrypt’
- A window should pop up. Enter your passphrase, then click ‘Ok’
- aannnddddd there’s your message
Part 10 – Conclusion
That wasn’t too hard, was it? Like I said in the intro, you shouldn’t be using OS X for DNM activities due to privacy issues, but I won’t go into it. This took forever to complete because OS X is a bitch to get running properly in a virtual machine. A guide for Windows will be coming next week!
Источник
GPGTools
One simple package
with everything you need,
to protect your emails and files.
By downloading, you agree to our Terms of Distribution
Use GPG Suite to encrypt, decrypt, sign and verify files or messages. Manage your GPG Keychain with a few simple clicks and experience the full power of GPG easier than ever before.
GPG Mail
integrates the full power of GPG seamlessly into macOS Mail. Protecting your emails has never been so simple.
GPG Keychain
allows you to manage your OpenPGP keys. Create new keys, modify existing ones and import your colleagues’ keys from a key server.
GPG Services
integrates the power of GPG into almost any application via the macOS Services context menu. It allows you to encrypt/decrypt, sign/verify text selections, files, folders and much more.
MacGPG
is the underlying encryption engine of GPG Suite. If you are familiar with the command line, you can use its raw powers. Based on the latest version of GnuPG.
GPG Suite at a glance
It’s all about the keys
To use GPG to encrypt and verify mails or files you and your friends need GPG keys.
GPG Keychain lets you manage your own keys and find and import keys of your friends.
Create your own key
Enter your name and the email address you want to use your key with and you are ready to go.
You don’t have to bother with more advanced settings, we set good defaults for you.
Upload your key to a key server so your friends can find it
When creating a key, you have the option to upload it to a key server, which makes it very easy for your friends to find and import it.
Already an expert?
When creating a key, you can enable the advanced view, which lets you choose key size, expiration date and algorithm to use for your keys. Have full control over your keys.
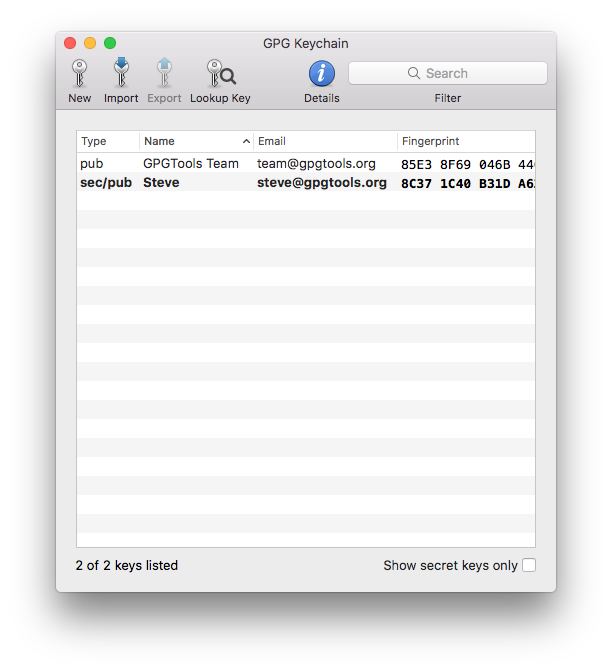
See all your keys
The main window of GPG Keychain shows you all your keys and the keys of your friends.
Enable the «Show secret keys only» checkbox, to see only the keys you created.
The toolbar
gives you quick access to the most important actions. Create a new key, import or export an existing key, or search for a specific key using the search field.
More options
Select a key and right-click on it to bring up a context menu, letting you send your key to a key server, update or manage the details of your key.
Add additional email addresses
Select your key and press the info button in the toolbar to add additional email addresses.
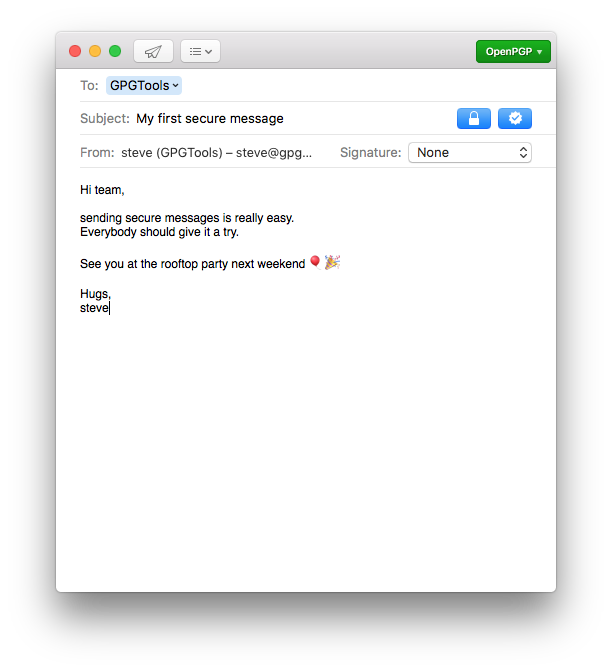
Write secure messages with Mail
After installing GPG Suite, you’ll see two new buttons when writing a new email: the lock button and the sign button next to it.
The lock button
Activate the lock button to encrypt an email. Only you and the recipient will be able to read the contents of your message. Toggle between encrypting and not encrypting your email pressing ⌥ ⌘ Y.
The sign button
Activate the sign button to sign an email. The recipient will be able to tell, that the email came from you and whether or not it was tampered with in any way.
Toggle between signing and not signing your email pressing ⌥ ⌘ X.
Choose between PGP and S/MIME
Using the security method indicator in the upper right corner, you can quickly switch between PGP and S/MIME. This is very handy if you use both.
Press ⌥ ⌘ P to activate PGP or ⌥ ⌘ S to activate S/MIME.
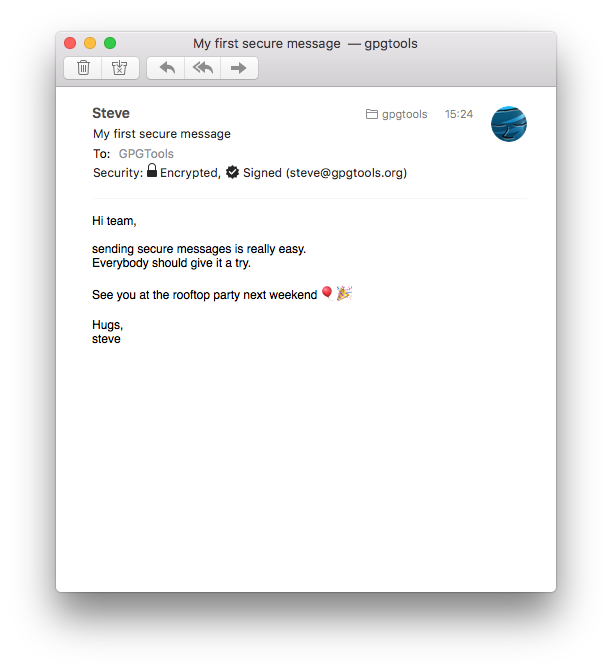
Receive secure messages with Mail
The «Security:» header will tell you, if the message you’ve received was signed or encrypted.
If the message was successfully decrypted, you’ll see an open lock. If the signature of the message is valid, you’ll see a star icon with a checkmark.
Make sure to click «Details» to see the security header.
Signed messages
will show the email address associated with your friend’s key that was used to sign this message.
Click on the signature icon to see more infos regarding the key and signature.
Encrypted or signed attachments
If the message contains encrypted or signed attachments, they will be automatically decrypted and verified. The attachments will look like any other non-encrypted attachments to you, while still being protected.
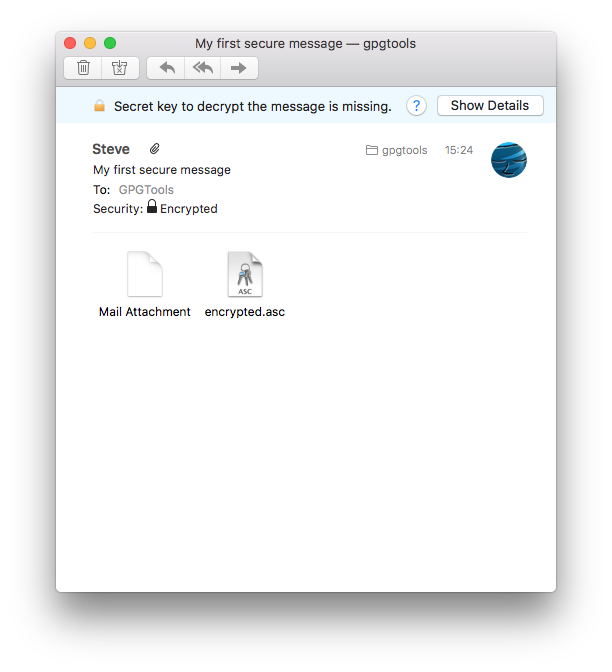
Sometimes things go wrong
It might happen that someone encrypted a mail for another recipient but mistakenly sent it to you and so you’re not able to read it. Or a signed message you’re receiving was modified without your knowledge. Or anything else could have gone wrong. In these cases we’re trying to be as helpful as possible by providing good explanations of what happened.
Find out what went wrong
Whenever we detect that something’s not right, you’ll see a banner with an error message, letting you know what the problem is.
To get detailed information about a problem, click on «Show Details» which contains a better description of the problem and possible solutions to it.
Источник
GnuPG: Безопасная почта для Win, Mac и *nix

Рассмотрим установку и первичную настройку GnuPG для трёх ОС: Windows, Mac OS X и Linux.
Подразумевается, что читатель имеет достаточные знания для того, чтобы выполнить несколько команд в консоли ОС (CMD/Terminal/xterm соответственно).
Скачивание
Windows: GPG4Win — готовая сборка GnuPG + GUI + Claws-Mail.
Mac OS X: Установить GPG Suite
Linux: В зависимости от вашего дистрибутива. Ключевое слово — gnupg2.
В связи с многообразием клиентов под *nix, расписывать установку для каждого — бесполезно.
Список клиентов, поддерживающих GNUPG — тут.
Установка
Windows: Стандартная установка. Не забываем поставить галочку около «Claws Mail».
Mac OS X: Устанавливаем GPG Suite.
Linux: В зависимости от дистрибутива и почтового клиента :)l.
Создание ключей
Запускаем терминал (cmd.exe/Terminal/xterm).
Для ОС Windows делаем cd «Папка_Куда_установлена_GPG4Win» (C:\Program Files\GNU\GnuPG\ по умолчанию )
Для всех: выполняем команду gpg2 —gen-key
Вам зададут несколько вопросов.
2048 должно хватить. Просто жмём Enter.
Через какое время ключ будет считаться недействительным? Жмите «Enter» 🙂 Пусть будет вечным.
Далее жмём «Y». И отвечаем на 3 вопроса.
Real Name: — вводим своё имя латинскими буквами (напр. Vasily Pupkin ).
Email: — вводим e-mail (напр. v.pupkin@gmail.com)
Comment: — что угодно, от названия фирмы до ника )
Если всё правильно — жмём «O».
Теперь нас спросят пароль для ключа. Вводим 2 раза один и тот-же (или 2 раза жмём Enter для ключа без пароля).
Несколько секунд… И ключ готов! Ура! )
Проверяем: gpg2 —list-keys
pub 2048R/5C35B909 2010-01-31
uid Vasily Pupkin
sub 2048R/40ADD978 2010-01-31
Использование
Windows: Запускаем Claws-Mail. Подключаем аккаунт почты (тот, для которого создавали ключ! ).
Идём в настройки-модули, проверяем, что там есть модуль GPG.
Теперь, создаём сами себе сообщение и выбираем Параметры->Зашифровать.
Кстати, можем сразу создать новые ключи для другой учетной записи — Настройки-Настройки учетной записи-Модуль-GPG-Генерировать новую пару ключей
Mac OS X: Запускаем Mail, создаём новое сообщение, видим галочки «Signed» и «Encryped». Можем выбрать ключ для подписи/шифрования. Для 10.6 и Claws-mail аналогично Windows.
Linux:В зависимости от клиента. Для Claws-Mail аналогично Windows.
Переписка
Для переписки с абонентом необходимо иметь его публичный ключ. Свой ключ можно получить командой gpg2 -a —export ваш e-mail.
Импортировать чужой — gpg2 —import файл ключа
Финал
Вот собственно, и всё. Удачного Вам шифрования )
Если хотите проверить — пишите мне (не забывайте прикладывать свой публичный ключ аттачем ).
Мой ключ — тут.
Удачи!
Источник