- Как узнать PID (идентификатор процесса) в Windows
- Как узнать PID (идентификатор процесса) в диспетчере задач
- Как узнать PID (идентификатор процесса) в командной строке
- Windows Process from PID
- 4 Answers 4
- !process
- Parameters
- Additional Information
- Remarks
- Как просмотреть Process Identifier (идентификатор процесса или PID) в ОС Windows.
- Get process name by PID
- 5 Answers 5
- Not the answer you’re looking for? Browse other questions tagged python process pid or ask your own question.
- Linked
- Related
- Hot Network Questions
- Subscribe to RSS
Как узнать PID (идентификатор процесса) в Windows
В данной статье показаны действия, с помощью которых можно узнать PID (идентификатор процесса) в операционной системе Windows.
Идентификатор процесса (process identifier, PID) — уникальный номер процесса в операционной системе Windows.
Все процессы имеют уникальные идентификаторы PID, которые автоматически присваиваются каждому процессу когда он создается в операционной системе, что позволяет ядру системы различать процессы.
При необходимости можно узнать PID (идентификатор процесса).
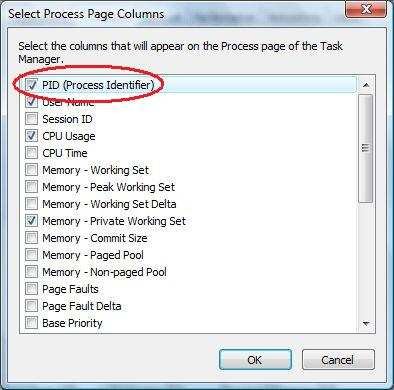
Как узнать PID (идентификатор процесса) в диспетчере задач
Чтобы узнать PID (идентификатор процесса), откройте диспетчер задач и перейдите на вкладку Процессы, затем нажмите правой кнопкой мыши на заголовок таблицы и в контекстном меню выберите пункт ИД процесса .
Теперь найдите нужный процесс, и в столбце ИД процесса будет отображен идентификатор соответствующего процесса.
Как узнать PID (идентификатор процесса) в командной строке
Также узнать PID (идентификатор процесса) можно используя командную строку.
Запустите командную строку и выполните следующую команду:
Найдите нужный процесс, в столбце PID будет отображен идентификатор процесса.
Также можно отобразить процессы в виде списка, для этого в командной строке выполните следующую команду:
Найдите нужный процесс, в строке PID будет отображен идентификатор процесса.
Используя рассмотренные выше действия, можно узнать PID (идентификатор процесса) в операционной системе Windows.
Windows Process from PID
I’m trying to determine which application or system program is using a particular port on a Windows 2008 R2 machine.
And have determined that PID is holding open port 445, which I’m interested in.
But when I run tasklist or Microsoft’s pslist program, it tells me that the process holding the port open is simply named ‘Sys’.
Is there another tool or approach I can use to find which is the real process holding it open?
4 Answers 4
PID 4 is the system process — if PID 4 is holding a port open, it means that some device driver has opened the port. Given that it’s port 445, my guess is that it’s the CIFS network filesystem or server. Try doing a «net stop srv» and «net stop rdr» from an elevated command prompt — that should shut down the service using the port.
The sysinternals tool procexp (process explorer) shows both processes and if the process is a service — it can show which services are running in the same process. (Windows service processes can contain a number of service threads).
Port 445 is normally the SMB port for Windows domain activities and file sharing and so on.
Have you looked at TCPView http://technet.microsoft.com/en-us/sysinternals/bb897437? It’s another tool from sysinternals.
There is a free tool on Nirsoft’s website called «CPORTS» with both 32 and 64 bit versions that might help you. Port 445 is used by Server 2008 R2 and later for communicating with other systens using SAMBA /TCP. I got the list below from «cyberciti.biz»
■netbios-ns — 137/tcp # NETBIOS Name Service ■netbios-dgm — 138/tcp # NETBIOS Datagram Service ■netbios-ssn — 139/tcp # NETBIOS session service ■microsoft-ds — 445/tcp # if you are using Active Directory ■Port 389 (TCP) — for LDAP (Active Directory Mode) ■Port 445 (TCP) — NetBIOS was moved to 445 after 2000 and beyond, (CIFS) ■Port 901 (TCP) — for SWAT service (not related to client communication
If you can run «grep» this is their recommended format: «$ grep -i NETBIOS /etc/services». If not, «AstroGrep» is a little more «user-friendly» Both can be gotten from SourceForge. My own interest lies in a solution to why some systems are unable to map network drives to a server 2008 R2 box yet they have no problem making a VPN connection and running the SQL software on the same server. Port 445 is the one I am most closely looking at due to NETBIOS needs but I really don’t have a clue. One person can be unable to map a drive letter from their laptop on their home internet, but then use their cellphone as a tethered modem and map it with no problem. Same system same everything else.
I hope one of these helps you, as my problem is still ongoing but the Nirsoft tool is the easiest to use by far and the listed use of grep did give me other information that may be of use to you. The tool from Nirsoft provides an excellent map of all ports in use and plenty of other information. Requires no installation and small enough to keep handy on a flashdrive. Grep or Astrogrep from SourceForge.
!process
The !process extension displays information about the specified process, or about all processes, including the EPROCESS block.
This extension can be used only during kernel-mode debugging.
Parameters
/s **** Session
Specifies the session that owns the desired process.
/m **** Module
Specifies the module that owns the desired process.
Process
Specifies the hexadecimal address or the process ID of the process on the target computer.
The value of Process determines whether the !process extension displays a process address or a process ID . If Process is omitted in any version of Windows, the debugger displays data only about the current system process. If Process is 0 and ImageName is omitted, the debugger displays information about all active processes. If -1 is specified for Process information about the current process is displayed.
Flags
Specifies the level of detail to display. Flags can be any combination of the following bits. If Flags is 0, only a minimal amount of information is displayed. The default varies according to the version of Windows and the value of Process. The default is 0x3 if Process is omitted or if Process is either 0 or -1; otherwise, the default is 0xF.
Bit 0 (0x1)
Displays time and priority statistics.
Bit 1 (0x2)
Displays a list of threads and events associated with the process, and their wait states.
Bit 2 (0x4)
Displays a list of threads associated with the process. If this is included without Bit 1 (0x2), each thread is displayed on a single line. If this is included along with Bit 1, each thread is displayed with a stack trace.
Bit 3 (0x8)
Displays the return address and the stack pointer for each function The display of function arguments is suppressed.
Bit 4 (0x10)
Sets the process context equal to the specified process for the duration of this command. This results in a more accurate display of thread stacks. Because this flag is equivalent to using .process /p /r for the specified process, any existing user-mode module list will be discarded. If Process is zero, the debugger displays all processes, and the process context is changed for each one. If you are only displaying a single process and its user-mode state has already been refreshed (for example, with .process /p /r), it is not necessary to use this flag. This flag is only effective when used with Bit 0 (0x1).
ImageName
Specifies the name of the process to be displayed. The debugger displays all processes whose executable image names match ImageName. The image name must match that in the EPROCESS block. In general, this is the executable name that was invoked to start the process, including the file extension (usually .exe), and truncated after the fifteenth character. There is no way to specify an image name that contains a space. When ImageName is specified, Process must be zero.
Additional Information
For information about processes in kernel mode, see Changing Contexts. For more information about analyzing processes and threads, see Microsoft Windows Internals, by Mark Russinovich and David Solomon.
Remarks
The following is an example of a !process 0 0 display:
The following table describes some of the elements of the !process 0 0 output.
| Element | Meaning | ||
|---|---|---|---|
| Element | Meaning |
|---|---|
| WAIT | The parenthetical comment after this heading gives the reason for the wait. The command dt nt!_KWAIT_REASON will display a list of all wait reasons. |