- tasklist tasklist
- Синтаксис Syntax
- Параметры Parameters
- Имена фильтров, операторы и значения Filter names, operators, and values
- Примеры Examples
- Processes, Threads, and Jobs in the Windows Operating System
- Process Internals
- Data Structures
- Table 5-1. Contents of the EPROCESS Block
- Kernel Variables
- Table 5-2. Process-Related Kernel Variables
- Performance Counters
- Table 5-3. Process-Related Performance Counters
- Relevant Functions
- Table 5-4. Process-Related Functions
tasklist tasklist
Отображает список запущенных в данный момент процессов на локальном или удаленном компьютере. Displays a list of currently running processes on the local computer or on a remote computer. Tasklist заменяет средство TList . Tasklist replaces the tlist tool.
Эта команда заменяет средство TList . This command replaces the tlist tool.
Синтаксис Syntax
Параметры Parameters
| Параметр Parameter | Описание Description |
|---|---|
| ключ /s | Указывает имя или IP-адрес удаленного компьютера (не используйте символы обратной косой черты). Specifies the name or IP address of a remote computer (do not use backslashes). По умолчанию это локальный компьютер. The default is the local computer. |
| /u \ /u \ | Выполняет команду с разрешениями учетной записи пользователя, заданного или пользователем \ . Runs the command with the account permissions of the user who is specified by or by \ . Параметр /u может быть указан только в том случае, если задано также значение /s . The /u parameter can be specified only if /s is also specified. По умолчанию заданы разрешения пользователя, который в данный момент вошел в систему компьютера, выполняющего команду. The default is the permissions of the user who is currently logged on to the computer that is issuing the command. |
| /p |
| Указывает формат, используемый для выходных данных. Specifies the format to use for the output. Допустимые значения: Table, List и CSV. Valid values are table, list, and csv. Формат выходных данных по умолчанию — Table. The default format for output is table. | |
| использован /nh | Подавляет вывод заголовков столбцов в выходных данных. Suppresses column headers in the output. Допустим, если для параметра /FO задано значение Table или CSV. Valid when the /fo parameter is set to table or csv. |
| /Fi /fi | Указывает типы процессов, включаемых в запрос или исключаемых из него. Specifies the types of processes to include in or exclude from the query. Можно использовать более одного фильтра или использовать подстановочный знак ( \ ) для указания всех задач или имен изображений. You can use more than one filter or use the wildcard character ( \ ) to specify all tasks or image names. Допустимые фильтры перечислены в разделе имена фильтров, операторы и значения этой статьи. The valid filters are listed in the Filter names, operators, and values section of this article. |
| /? /? | Отображение справки в командной строке. Displays help at the command prompt. |
Имена фильтров, операторы и значения Filter names, operators, and values
| Имя фильтра Filter Name | Допустимые операторы Valid Operators | Допустимые значения Valid Value(s) |
|---|---|---|
| Состояние STATUS | eq, ne eq, ne | RUNNING | NOT RESPONDING | UNKNOWN . RUNNING | NOT RESPONDING | UNKNOWN . Этот фильтр не поддерживается, если указана удаленная система. This filter isn’t supported if you specify a remote system. |
| IMAGENAME IMAGENAME | eq, ne eq, ne | Имя образа Image name |
| ИД процесса PID | eq, ne, gt, lt, ge, le eq, ne, gt, lt, ge, le | Значение PID PID value |
| SESSION SESSION | eq, ne, gt, lt, ge, le eq, ne, gt, lt, ge, le | Номер сеанса Session number |
| SESSIONNAME SESSIONNAME | eq, ne eq, ne | Имя сеанса Session name |
| CPUtime CPUtime | eq, ne, gt, lt, ge, le eq, ne, gt, lt, ge, le | Время ЦП в формате чч: мм: СС, где mm и SS находятся в диапазоне от 0 до 59, а чч — любое число без знака CPU time in the format HH:MM:SS, where MM and SS are between 0 and 59 and HH is any unsigned number |
| мемусаже MEMUSAGE | eq, ne, gt, lt, ge, le eq, ne, gt, lt, ge, le | Использование памяти в КБ Memory usage in KB |
| USERNAME USERNAME | eq, ne eq, ne | Любое допустимое имя пользователя ( или ) Any valid user name ( or ) |
| Обслуживание SERVICES | eq, ne eq, ne | Имя службы Service name |
| WINDOWTITLE WINDOWTITLE | eq, ne eq, ne | Заголовок окна. Window title. Этот фильтр не поддерживается, если указана удаленная система. This filter isn’t supported if you specify a remote system. |
| МОДУЛЕ MODULES | eq, ne eq, ne | Имя DLL DLL name |
Примеры Examples
Чтобы получить список всех задач с идентификатором процесса, превышающим 1000, и отобразить их в формате CSV, введите: To list all tasks with a process ID greater than 1000, and display them in csv format, type:
Чтобы получить список системных процессов, выполняемых в данный момент, введите: To list the system processes that are currently running, type:
Чтобы вывести подробные сведения обо всех выполняющихся процессах, введите: To list detailed information for all processes that are currently running, type:
Чтобы получить список всех сведений о службе для процессов на удаленном компьютере срвмаин с именем DLL, начинающимся с NTDLL, введите: To list all the service information for processes on the remote computer srvmain, which has a DLL name beginning with ntdll, type:
Чтобы получить список процессов на удаленном компьютере срвмаин, используя учетные данные текущей учетной записи пользователя, выполнившего вход в систему, введите: To list the processes on the remote computer srvmain, using the credentials of your currently logged-on user account, type:
Чтобы получить список процессов на удаленном компьютере срвмаин, используя учетные данные хироплн учетной записи пользователя, введите: To list the processes on the remote computer srvmain, using the credentials of the user account Hiropln, type:
Processes, Threads, and Jobs in the Windows Operating System
Where relevant performance counters or kernel variables exist, they are mentioned. Although this book isn’t a Windows programming book, the pertinent process, thread, and job Windows functions are listed so that you can pursue additional information on their use.
Because processes and threads touch so many components in Windows, a number of terms and data structures (such as working sets, objects and handles, system memory heaps, and so on) are referred to in this chapter but are explained in detail elsewhere in the book. To fully understand this chapter, you need to be familiar with the terms and concepts explained in Chapter 1 and Chapter 2, such as the difference between a process and a thread, the Windows virtual address space layout, and the difference between user mode and kernel mode.
Process Internals
This section describes the key Windows process data structures. Also listed are key kernel variables, performance counters, and functions and tools that relate to processes.
Data Structures
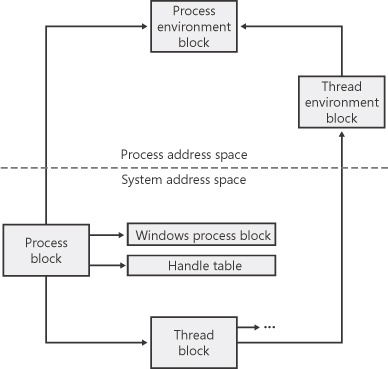
Each Windows process is represented by an executive process (EPROCESS) block. Besides containing many attributes relating to a process, an EPROCESS block contains and points to a number of other related data structures. For example, each process has one or more threads represented by executive thread (ETHREAD) blocks. (Thread data structures are explained in the section Thread Internals later in this chapter.) The EPROCESS block and its related data structures exist in system address space, with the exception of the process environment block (PEB), which exists in the process address space (because it contains information that needs to be accessed by user-mode code).
In addition to the EPROCESS block and the PEB, the Windows subsystem process (Csrss) maintains a parallel structure for each process that is executing a Windows program. Finally, the kernel-mode part of the Windows subsystem (Win32k.sys) will also maintain a per-process data structure that is created the first time a thread calls a Windows USER or GDI function that is implemented in kernel mode.
Figure 5-1 is a simplified diagram of the process and thread data structures. Each data structure shown in the figure is described in detail in this chapter.
Figure 5-1. Data structures associated with processes and threads
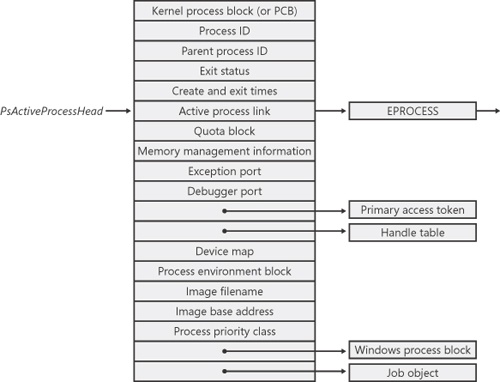
First let’s focus on the process block. (We’ll get to the thread block in the section Thread Internals later in the chapter.) Figure 5-2 shows the key fields in an EPROCESS block.
Figure 5-2. Structure of an executive process block
EXPERIMENT: Displaying the Format of an EPROCESS Block
For a list of the fields that make up an EPROCESS block and their offsets in hexadecimal, type dt _eprocess in the kernel debugger. (See Chapter 1 for more information on the kernel debugger and how to perform kernel debugging on the local system.) The output (truncated for the sake of space) on a 32-bit system looks like this:
Note that the first field (Pcb) is actually a substructure, the kernel process block (KPROCESS), which is where scheduling-related information is stored. To display the format of the kernel process block, type dt _kprocess:
An alternative way to see the KPROCESS (and other substructures in the EPROCESS) is to use the recursion (–r) switch of the dt command. For example, typing dt _eprocess –r1 will recurse and display all substructures one level deep.
The dt command shows the format of a process block, not its contents. To show an instance of an actual process, you can specify the address of an EPROCESS structure as an argument to the dt command. You can get the address of all the EPROCESS blocks in the system by using the !process 0 0 command. An annotated example of the output from this command is included later in this chapter.
Table 5-1 explains some of the fields in the preceding experiment in more detail and includes references to other places in the book where you can find more information about them. As we’ve said before and will no doubt say again, processes and threads are such integral parts of Windows that it’s impossible to talk about them without referring to many other parts of the system. To keep the length of this chapter manageable, however, we’ve covered those related subjects (such as memory management, security, objects, and handles) elsewhere.
Table 5-1. Contents of the EPROCESS Block
Element
Purpose
Additional Reference
Kernel process (KPROCESS) block
Common dispatcher object header, pointer to the process page directory, list of kernel thread (KTHREAD) blocks belonging to the process, default base priority, affinity mask, and total kernel and user time and CPU clock cycles for the threads in the process.
Thread scheduling (Chapter 5)
Unique process ID, creating process ID, name of image being run, window station process is running on.
Limits on processor usage, nonpaged pool, paged pool, and page file usage plus current and peak process nonpaged and paged pool usage. (Note: Several processes can share this structure: all the system processes in session 0 point to a single systemwide quota block; all other processes in interactive sessions share a single quota block.)
Virtual address descriptors (VADs)
Series of data structures that describes the status of the portions of the address space that exist in the process.
Virtual address descriptors (Chapter 9)
Working set information
Pointer to working set list (MMWSL structure); current, peak, minimum, and maximum working set size; last trim time; page fault count; memory priority; outswap flags; page fault history.
Working sets (Chapter 9)
Virtual memory information
Current and peak virtual size, page file usage, hardware page table entry for process page directory.
Exception legacy local procedure call (LPC) port
Interprocess communication channel to which the process manager sends a message when one of the process’s threads causes an exception.
Exception dispatching (Chapter 3)
Executive object through which the user-mode debugging infrastructure sends notifications when one of the process’s threads causes a debug event.
User-mode debugging (Chapter 3)
Access token (TOKEN)
Executive object describing the security profile of this process.
Address of per-process handle table.
Object handles and the process handle table (Chapter 3)
Address of object directory to resolve device name references in (supports multiple users).
Object names (Chapter 3)
Process environment block (PEB)
Image information (base address, version numbers, module list), process heap information, and thread-local storage utilization. (Note: The pointers to the process heaps start at the first byte after the PEB.)
Windows subsystem process block (W32PROCESS)
Process details needed by the kernel-mode component of the Windows subsystem.
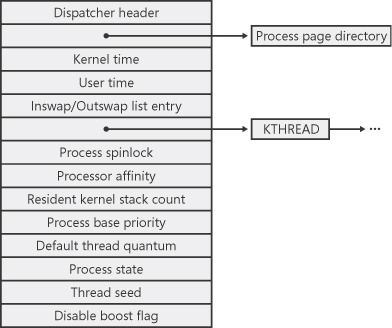
The kernel process (KPROCESS) block, which is part of the EPROCESS block, and the process environment block (PEB), which is pointed to by the EPROCESS block, contain additional details about the process object. The KPROCESS block (which is sometimes called the PCB or process control block) is illustrated in Figure 5-3. It contains the basic information that the Windows kernel needs to schedule the threads inside a process. (Page directories are covered in Chapter 9, and kernel thread blocks are described in more detail later in this chapter.)
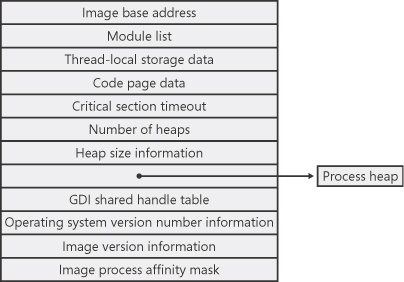
The PEB, which lives in the user process address space, contains information needed by the image loader, the heap manager, and other Windows system DLLs that need to access it from user mode. (The EPROCESS and KPROCESS blocks are accessible only from kernel mode.) The basic structure of the PEB is illustrated in Figure 5-4 and is explained in more detail later in this chapter.
Figure 5-3. Structure of the executive process block
Figure 5-4. Fields of the process environment block
EXPERIMENT: Examining the PEB
You can dump the PEB structure with the !peb command in the kernel debugger. To get the address of the PEB, use the !process command as follows:
Then specify that address to the !peb command as follows:
Kernel Variables
A few key kernel global variables that relate to processes are listed in Table 5-2. These variables are referred to later in the chapter, when the steps in creating a process are described.
Table 5-2. Process-Related Kernel Variables
Element
Purpose
Additional Reference
Doubly linked list
List head of process blocks
Pointer to EPROCESS
Idle process block
Pointer to EPROCESS
Pointer to the process block of the initial system process that contains the system threads
Array of executive callback objects
Array of callback objects describing the routines to be called on process creation and deletion (maximum of eight)
Count of registered process notification routines
Count of registered extended process notification routines
Array of executive callback objects
Array of callback objects describing the routines to be called on image load (maximum of eight)
Count of registered image-load notification routines
Mask for quickly checking whether any extended or standard notification routines are enabled
Pointer to HANDLE_TABLE
Handle table for process and thread client IDs
Performance Counters
Windows maintains a number of counters with which you can track the processes running on your system; you can retrieve these counters programmatically or view them with the Performance tool. Table 5-3 lists the performance counters relevant to processes.
Table 5-3. Process-Related Performance Counters
Object: Counter
Function
Process: % Privileged Time
Describes the percentage of time that the threads in the process have run in kernel mode during a specified interval.
Process: % Processor Time
Describes the percentage of CPU time that the threads in the process have used during a specified interval. This count is the sum of % Privileged Time and % User Time.
Process: % User Time
Describes the percentage of time that the threads in the process have run in user mode during a specified interval.
Process: Elapsed Time
Describes the total elapsed time in seconds since this process was created.
Process: ID Process
Returns the process ID. This ID applies only while the process exists because process IDs are reused.
Process: Creating Process ID
Returns the process ID of the creating process. This value isn’t updated if the creating process exits.
Process: Thread Count
Returns the number of threads in the process.
Process: Handle Count
Returns the number of handles open in the process.
Relevant Functions
For reference purposes, some of the Windows functions that apply to processes are described in Table 5-4. For further information, consult the Windows API documentation in the MSDN Library.
Table 5-4. Process-Related Functions
Function
Description
Creates a new process and thread using the caller’s security identification
Creates a new process and thread with the specified alternate security token
Creates a new process and thread to run under the credentials of the specified username and password
Creates a new process and thread with the specified alternate security token, with additional options such as allowing the user profile to be loaded
Returns a handle to the specified process object
Ends a process, and notifies all attached DLLs
Ends a process without notifying the DLLs
Empties the specified process’s instruction cache
Empties the specified process’s write queue
Obtains a process’s timing information, describing how much time the threads inside the process spent in user and kernel mode
Obtains a process’s CPU timing information, describing how many clock cycles the threads inside the process have spent in total
Defines whether the process’s affinity is automatically updated if new processors are added to the running system
Returns or sets the DEP (Data Execution Protection) policy for the process
Returns the exit code for a process, indicating how and why the process shut down
Returns a pointer to the command-line string passed to the current process
Returns the full name of the executable image associated with the process
Returns a pseudo handle for the current process
Returns the ID of the current process
Returns the major and minor versions of the Windows version on which the specified process expects to run
Returns the contents of the STARTUPINFO structure specified during CreateProcess
Returns the address of the environment block
Returns or sets a specific environment variable
Defines the shutdown priority and number of retries for the current process
Specifies whether the process is aware of dots per inch (DPI) settings
Returns a count of User and GDI handles
EXPERIMENT: Using the Kernel Debugger !process Command
The kernel debugger !process command displays a subset of the information in an EPROCESS block. This output is arranged in two parts for each process. First you see the information about the process, as shown here (when you don’t specify a process address or ID, !process lists information for the active process on the current CPU):
After the basic process output comes a list of the threads in the process. That output is explained in the EXPERIMENT: Using the Kernel Debugger !thread Command section later in the chapter. Other commands that display process information include !handle, which dumps the process handle table (which is described in more detail in the section Object Handles and the Process Handle Table in Chapter 3). Process and thread security structures are described in Chapter 6.