- Restricting what programs a user can run on Windows via Group Policy Objects
- How to run a program without admin rights in Windows 10
- What is RunWithRestrictedRights?
- How do I use RunWithRestrictedRights?
- A great tool for bypassing UAC restrictions
- Prevent Users From Running Certain Programs
- Option 1 – Apply Group Policy
- Option 2 – Apply Via Registry
- You Might Also Like
- Easily Start a Windows Application With Restricted, Non-Admin Rights
- A free, standalone command-line utility to run your Windows executable without admin rights or UAC elevation
- Command-line interface
- Why run an application with restricted rights/permissions?
- How do I know that my program is running without administrative rights?
- How does this utility compare to Runas?
- How does this utility compare to PsExec?
- Does RunWithRestrictedRights.exe work on Windows XP and Windows Server 2003, where there is no UAC?
Restricting what programs a user can run on Windows via Group Policy Objects
At Browserling I just solved an interesting Windows sysadmin problem of how to allow Windows users to run just a few programs and nothing else. Since anyone can use Browserling for free, I had to find a way to restrict them from downloading and running viruses and trojans. So I took time to investigate and found a very elegant solution. No one had really documented this so this blog post will be very handy for people who can’t figure it out themselves.
The solution is to configure the Software Restriction Policy (SRP) in the user’s Group Policy Object (GPO) and disallow the user to run everything except the programs that are necessary to login and the programs you want the user to use.
The hardest part was figuring out all the programs that the user absolutely must be allowed to run for him/her to login the system:
- C:\Windows\explorer.exe
- C:\Windows\System32\csrss.exe
- C:\Windows\System32\dwm.exe
- C:\Windows\System32\rdclip.exe
- C:\Windows\System32\taskhost.exe
- C:\Windows\System32\TSTheme.exe
- C:\Windows\System32\userinit.exe
If you don’t have these in the SRP, then the user will never be able to login. So make sure they are in the SRP’s «Additional Rules» and their security level is «Unrestricted.»
After you add these, the user will be able to login but he wont be able to run anything! He’ll just see desktop and that’s it. If you want to allow the user to run, let’s say, Paint, then add C:\Windows\System32\paint.exe the Unrestricted Access list.
Here is a precise list of steps to take to disallow running programs. Run them from Administrator account:
- Open up the Microsoft Management Console (Start -> Run -> mmc):
- Select File -> Add/Remove Snap-in.
- Select Group Policy Object.
- Click Add.
- Click Browse, select the user you want to configure the GPO for.
- Click Finish, and OK. Now you’ll see the tree view with » Policy.»
- Navigate to User Configuration -> Windows Settings -> Security Settings -> Software Restriction Policies.
- Right click on Software Restriction Policies and click New Software Restriction Policies.
- Two new items will appear the tree. Click the Security Levels.
- Double click the Disallowed security level and click «Set as Default.»
- Go to the other item, the Additional Rules.
- Delete the crap that Windows adds there by default (%HKEY_LOCAL_MACHINE. something).
- Add the rules that I documented in the beginning of the article. They are absolutely necessary for the user to login into the machine (either via desktop or remote desktop).
- Add full paths to programs that you want to allow the user to run (such as C:\windows\system32\paint.exe, . etc.). Make sure the users can’t overwrite the programs with their own, otherwise they might be able to execute their own programs.
- Save the GPO.
- Done.
I hope this was helpful and see you next time!
How to run a program without admin rights in Windows 10
- RunWithRestrictedRights is a great tool that allows you to open programs without admin rights.
- The guide below will show you how to use it to the full extent of its capacities.
- To read more about the topic, visit our Administrator Rights Hub.
- Need more great tutorials? Visit our dedicated How-To page.
Whenever you share a PC with someone else, and you are not the administrator, there are many drawbacks.
The first thing that comes to mind is that a lot of programs can be set up to only run while having administrator rights. This means that if you are logged in using a sub-account, you are pretty much limited in what you can do.
For example, a security program or program that manages Windows features that triggers a UAC prompt may not launch at all if you deny it.
Fortunately, all of that is part of the past if you use a program such as RunWithRestrictedRights.
What is RunWithRestrictedRights?
RunWithRestrictedRights is essentially a command-line tool that uses the Windows Integrity Mechanism to restrict permissions for other applications. This makes it so that they don’t harm your computer.
In order to use RunWithRestrictedRights, you will need two things:
- Adjust memory quotas for a process
- Replace a process level token.
Some extensive documentation on what permissions are and how do they function has been made available by Microsoft.
How do I use RunWithRestrictedRights?
- Start the Command Prompt, and type in the following command line:
- C:RunWithRestrictedRights.exe «application» “
- You will need to specify where RunWithRestrictedRights.exe is located.
- Replace “application” with the name of whatever program you want to launch.
By following the above-mentioned steps, the application should open with limited rights and more importantly, without any UAC pop-ups.
A great tool for bypassing UAC restrictions
RunWithRestrictedRights is a lightweight program that comes in a portable form and can run on Windows XP, but it can also be used on Windows Server 2003 and above.
Do you think bypassing UAC restrictions and giving more power to the common user is a good idea? Share your opinions in the comments section below.
Prevent Users From Running Certain Programs
By Mitch Bartlett 16 Comments
If you’re a system administrator, you may have problems with your users running programs like iTunes or BitTorrent in your Microsoft Windows environment? If you want to stop such programs from running, here’s how to use Group Policy or the Registry to prevent users from running certain programs.
Option 1 – Apply Group Policy
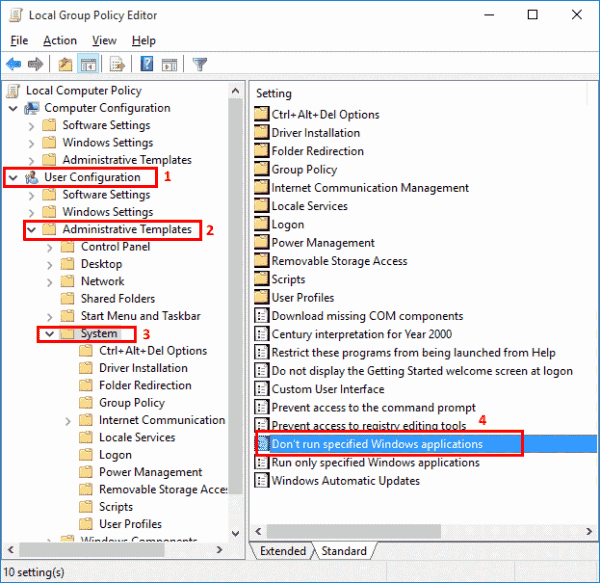
- Hold down the Windows Key and press “R” to bring up the Run dialog box.
- Type “gpedit.msc“, then press “Enter“. The Group Policy Editor appears.
- Expand “User Configuration” > “Administrative Templates“, then select “System“.
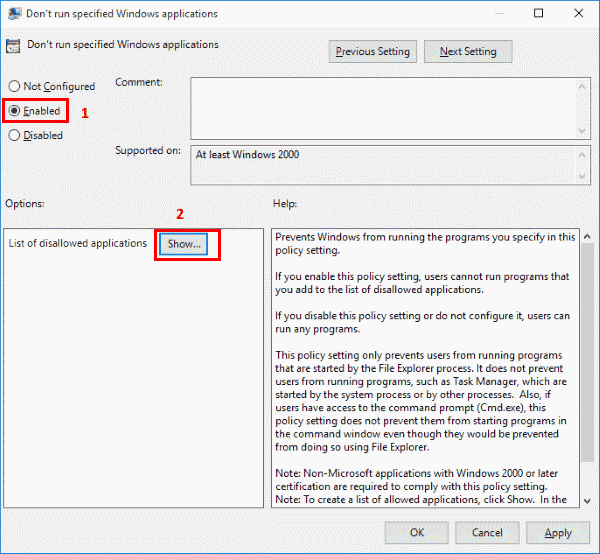
- Open the policy “Don’t run specified Windows applications“.
- Set the policy to “Enabled“, then select “Show…”
- Add the programs you would like to prevent the user from running to the List of disallowed applications. Use the name of the application launching file such as “itunes.exe“, “bittorent.exe“, etc.
Option 2 – Apply Via Registry
- Hold down the Windows Key and press “R” to bring up the Run dialog box.
- Type “regedit“, then press “Enter“. The Registry Editor appears.
- Expand the following:
- HKEY_CURRENT_USER
- SOFTWARE
- Microsoft
- Windows
- CurrentVersion
- Policies
- Explorer
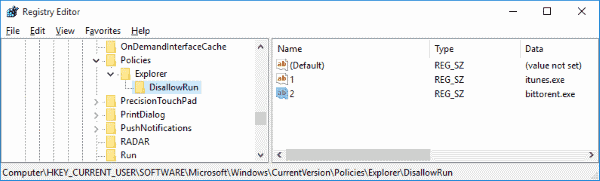
- Right-click a blank area on the right side and add a new “DWORD (32-bit) Value” named “DisallowRun“.
- Open “DisallowRun” and give it a Value of “1“.
- Right-click and add a new “Key“, also named “DisallowRun“. The folder is then created.
- Select the “DisallowRun” folder on the left pane.
- Right-click a blank area on the right side and add a new “DWORD (32-bit) Value” named “1“.
- Open “1” and give it a Value with the application you would like to block, like “itunes.exe“.
- Repeat steps 8 and 9 with any additional applications you wish to block, only increase the number used in the “DWORD (32-bit) Value” each time (2, 3, 4 ,5, etc)
So if I wanted to block two applications, “itunes.exe” and “bittorrent.exe“, my Registry Editor would look like this…
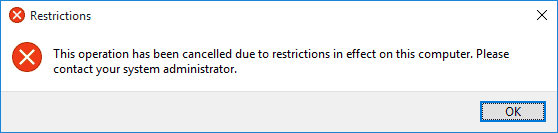
From now on the user will get a message “This operation has been cancelled due to restrictions in effect on this computer. Please contact your system administrator.” when he tries to run the programs you added.
I should mention that if the user is smart enough to rename the program file, they will be able to run the program again.
If this tutorial does not meet your needs, you might be able to use Applocker for your needs. Using Applocker allows you to deny access to applications based on publisher, path, or file hash. See more info about Applocker at Microsoft Technet.
You Might Also Like
Filed Under: Windows Tagged With: Windows 10
Easily Start a Windows Application With Restricted, Non-Admin Rights
A free, standalone command-line utility to run your Windows executable without admin rights or UAC elevation
RunWithRestrictedRights.exe is a small Windows command line utility that enables you to launch a Windows application safely & securely, without access to files, printers and other resources available only to administrators.
Use RunWithRestrictedRights.exe to start an untrusted application on your desktop or call it from a batch file to run a background task with the full protection of the Windows Integrity Mechanism.
Command-line interface
Upon completion, the exit code is the new process identifier (PID) if the application was successfully started and -1 if it was not. You can access that exit code via the standard ERRORLEVEL variable.
Why run an application with restricted rights/permissions?
For one reason: Security.
As this recent Computerworld article points out, a staggering 94% of Microsoft vulnerabilities can be mitigated by simply turning off Administrator’s rights when running applications!
The article states:
Privilege management and application control should be the cornerstone of your endpoint security strategy, building up from there to create ever stronger, multiple layers of defense. These measures can have a dramatic impact on your ability to mitigate today’s attacks. Times have changed; removing admin rights and controlling applications is no longer difficult to achieve.
How do I know that my program is running without administrative rights?
Confirming that your application is running without admin permisions can be tricky, but Microsoft’s free Process Explorer will come to the rescue.
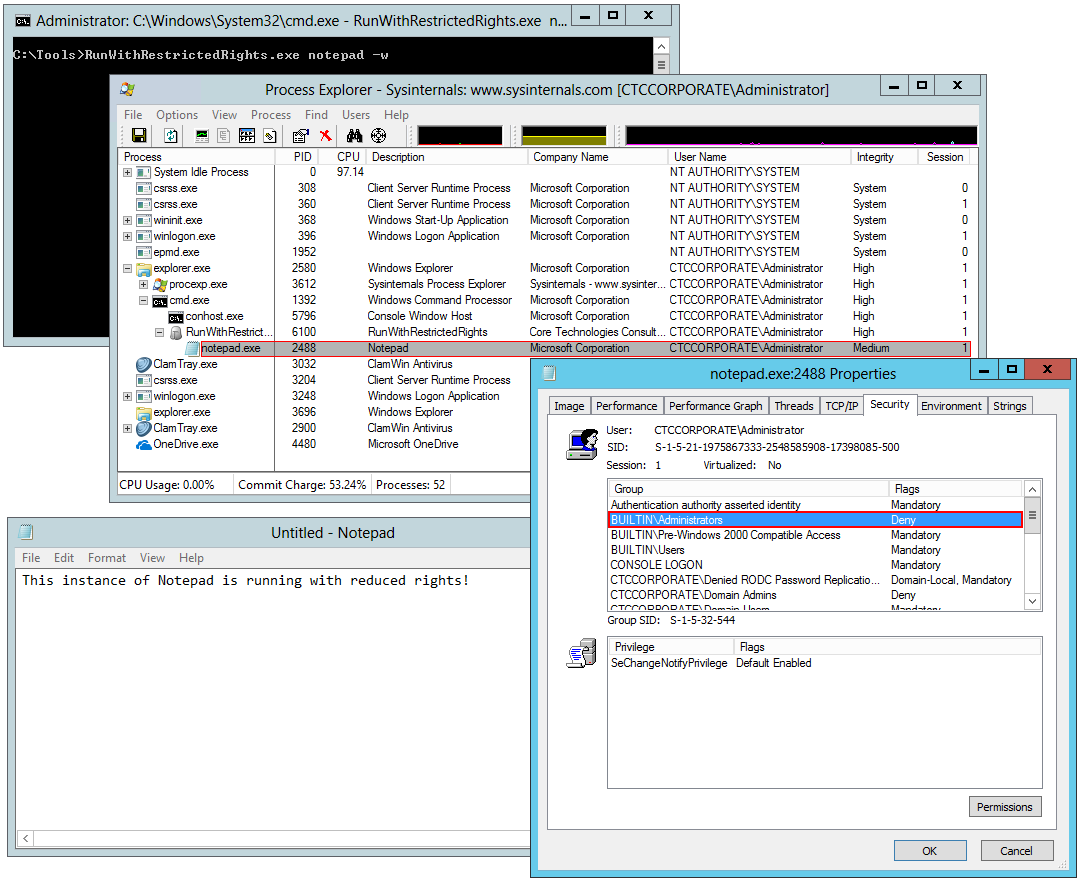
Here is a screenshot of Process Explorer interrogating an instance of Notepad launched with restricted rights:
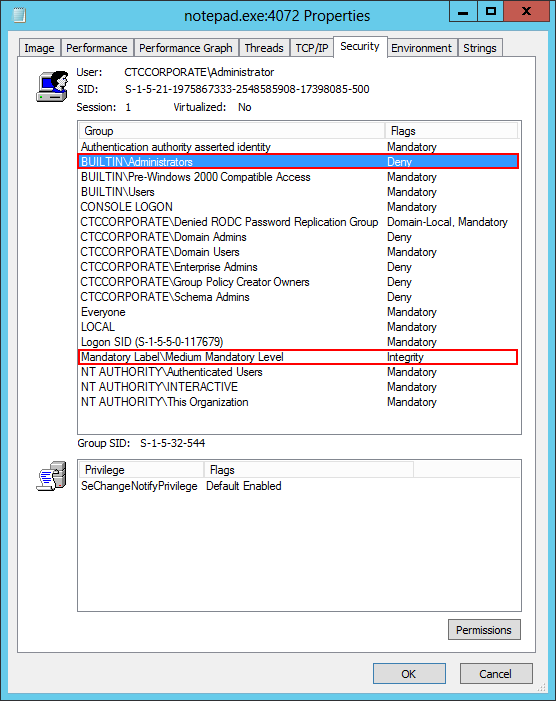
A process running with restricted permissions exhibits three telltale signs:
It is not a member of the BUILTIN\Administrators security group;
It is not a member of the BUILTIN\Local account and member of Administrators security group (in Windows Server 2012 R2 and beyond);
It is a member of the Mandatory Label\Medium Mandatory Label or Mandatory Label\Low Mandatory Label security groups.
You can find these properties in Process Explorer by double-clicking on your application in the list and switching to the Security tab in the window that comes up. Here we see Notepad running securely:
How does this utility compare to Runas?
Microsoft’s Runas utility can also start a program at one or more levels of authorization. Specifying the «Basic User» trust level (0x20000) is usually enough to run in a «non-elevated» UAC context.
However, we encountered a couple of scenarios where Runas wasn’t able to cap permissions:
When UAC is disabled;
When running in the context of a Windows Service, which is always endowed with full administrative rights;
When operating on Windows XP and Windows Server 2003, where UAC does not exist. The /trustlevel option is simply not available.
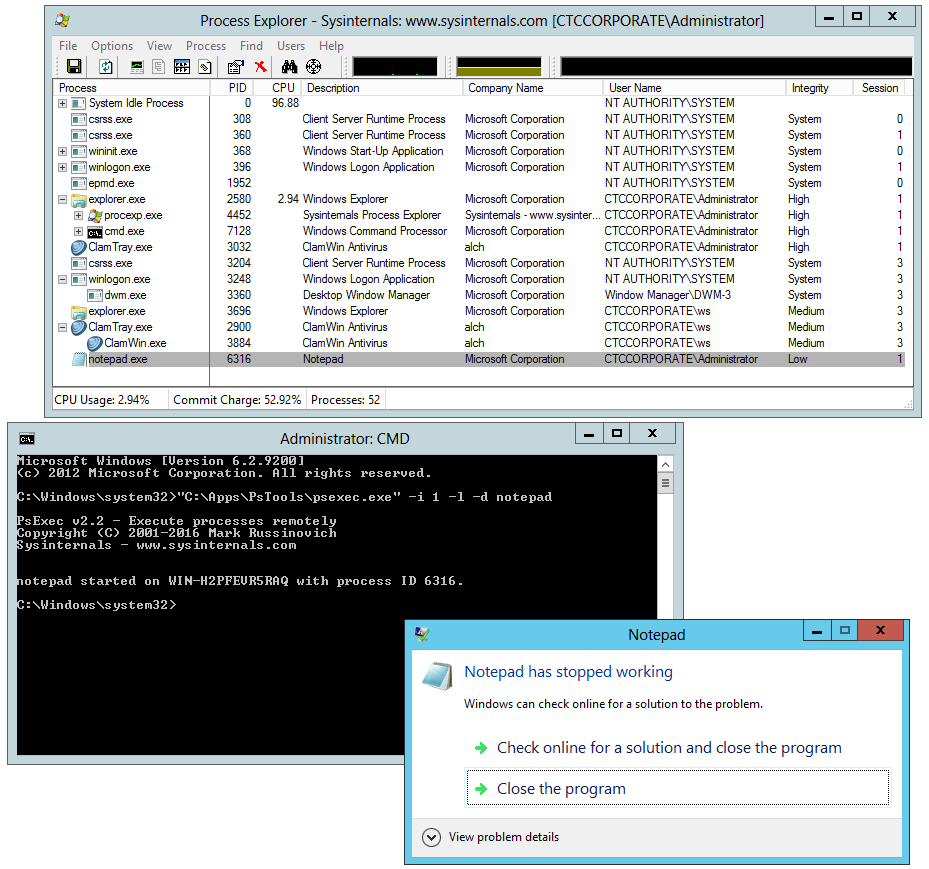
How does this utility compare to PsExec?
PsExec.exe, part of Microsoft’s versatile PsTools suite, is another free alternative. But we encountered a few barriers using it:
PsExec can run an application at Low Integrity but offers no option to start it at Medium Integrity
Notepad failed to start interactively at Low Integrity on our Windows Server 2012 machine:
Does RunWithRestrictedRights.exe work on Windows XP and Windows Server 2003, where there is no UAC?
Yes, it works well on Windows XP and Windows Server 2003. The Windows Integrity Level can’t be set (that feature is only available in Windows Vista and later) but the application is run without admin rights as intended.
One note though: If you receive an error stating that «a required privilege is not held by the client», please ensure that your account has these two rights:







 Privilege management and application control should be the cornerstone of your endpoint security strategy, building up from there to create ever stronger, multiple layers of defense. These measures can have a dramatic impact on your ability to mitigate today’s attacks. Times have changed; removing admin rights and controlling applications is no longer difficult to achieve.
Privilege management and application control should be the cornerstone of your endpoint security strategy, building up from there to create ever stronger, multiple layers of defense. These measures can have a dramatic impact on your ability to mitigate today’s attacks. Times have changed; removing admin rights and controlling applications is no longer difficult to achieve.