- Windows command line SSH
- Information Security Squad
- Как использовать команды SSH в командной строке Windows 10
- Что нужно знать о SSH
- 2) Соединение SSh с Windows Powershell и командной строкой
- а) SSh из Windows Powershell
- б) SSH из командной строкой
- Sharing SSH keys between Windows and WSL 2
- Setup SSH on Windows first
- Copy keys to WSL
- Fix permissions
- Sharing is caring
- Run ssh and immediately execute command [duplicate]
- 3 Answers 3
- openssh in Windows 7, run ssh-add once for all cmd instances
- 2 Answers 2
Windows command line SSH
Openssh for windows is a freely downloadable command line ssh client for windows operating system. This can be downloaded from http://sshwindows.sourceforge.net/
A snapshot with the options is given below. (Click on the image to see the options more clearly).
- Open the above download link and click on Binary Installer Releases
- Download the zip file
- Unzip the file and run the setupssh.exe file
- Select the options based on your requirement. Unselect server component if you just need the client version.
- After completing installation, open command window and then run ssh
If you want a GUI ssh client you can use Putty.exe. Use Putty connection manager in combination with Putty to have tabbed ssh sessions like the Terminal on Linux.
Good info, but with Windows (7 at least) OpenSSH for windows client Ignores private keys for authentication becuase the Linux file permissions always read 0644 whatever you do!!
Annoying – if you know a soloution, except using Cygwin please post.
Thanks!
PS. and yes I tried the windows ACL & chmod ports, they don’t affect what the binary sees.
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@ WARNING: UNPROTECTED PRIVATE KEY FILE! @
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
Permissions 0644 for ‘C:/users/User/desktop/openssh-id_rsa’ are too open.
It is recommended that your private key files are NOT accessible by others.
This private key will be ignored.
OK I found a soloution to my above problem, to use key auth command line ssh on windows 7:
Just use copssh
In this command prompt, type:
cd “c:\program files\cwrsync\bin”
and hit enter. Then type:
ssh-keygen -t rsa -N ”
accept the default location, the pretend root ‘/’ is the Program Files\ICW folder, so then you can use this command perfectly even from a normal Windows CMD prompt and it works!:
C:\Program File\ICW\bin>ssh -i /.ssh/id_rsa [email protected] uptime
and it works omg sweet. That’s OpenSSH_5.9p1, OpenSSL 0.9.8r 8 Feb 2011
My bad I copied the instructions, there’s one path error, this:
cd “c:\program files\cwrsync\bin”
cd “c:\program files\icw\bin”
Is this secure. Would it result in virus attack.
Also, Is putty safe to use?
Warning, the installation removes everything in PATH environment variable and replaces it with the path to the ssh cmd line client.
Hello, guys! How do you solve a problem with the attempt to search “/ home / *”? The program can not write or read the known_hosts file, as does not refer to “C: \ Users \ MyCoolUser \ .ssh”, and on “/home/MyCoolUser/.ssh”(. Tell me, please , because the password is 37 characters constantly do not want to enter .
@mary
I consider putty and ssh save to use for myself.
Of course it is up to you to decide or investigate.
You can read the openssh sourcecode, but I think putty does not offer that option.
Just need a confirmation i need to run commands on a remote windows system from an other windows system, can you let me know how i can achive this using open ssh
It doesn’t work with newer alg implementations, so new type of servers with stronger kex will not work…
You should not advertise this, there is a major bug in the install of OpenSSH that could cripple your system. The installation overwrites the system PATH environment variable. Something that is not easy to reconfigure if you don’t have the original path.
Information Security Squad
stay tune stay secure
- Home
- 2019
- Январь
- 15
- Как использовать команды SSH в командной строке Windows 10
Как использовать команды SSH в командной строке Windows 10
Что нужно знать о SSH
Secure Shell – это защищенный и зашифрованный протокол соединения, позволяющий осуществлять удаленный и безопасный вход по незащищенным соединениям.
Соединение работает в режиме клиент-сервер, поэтому соединение устанавливается клиентом SSH, подключающимся к серверу SSH.
SSH предлагает несколько вариантов аутентификации пользователя, и наиболее распространенными являются пароли и методы аутентификации с открытым ключом:
- Пароль: SSH работает как обычный процесс для локального компьютера, что означает, что вам нужно иметь имя пользователя и пароль существующей учетной записи на сервере.
- Открытый ключ: принцип состоит в том, чтобы иметь пару открытый ключ криптографического ключа и закрытый ключ, где открытый ключ сконфигурирован на сервере, чтобы разрешить доступ и предоставить любому, у кого есть копия закрытого ключа, доступ к серверу.
1) Установить функцию OpenSSH в Windows 10 клиенте
Компьютеры с Windows теперь позволяют вам использовать собственные инструменты для установки SSH-соединения, но сначала вам нужно убедиться, что установлена функция Openssh Windows Client.
Обычно он не устанавливается по умолчанию, поэтому сначала вам нужно будет это сделать
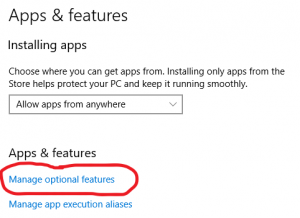
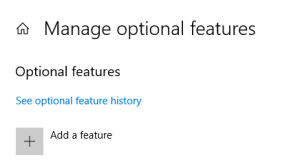
Зайдите в Windows -> Settings -> Apps -> Manage optional feature
Нажмите Add a feature
2) Соединение SSh с Windows Powershell и командной строкой
Теперь вы можете использовать командную строку или Windows PowerShell для доступа к вашему Linux-серверу через ssh.
а) SSh из Windows Powershell
Собственный инструмент Windows Powershell позволяет удаленно подключаться к серверу через ssh.
Вы просто должны открыть его с Windows + R, а затем нажмите клавишу A
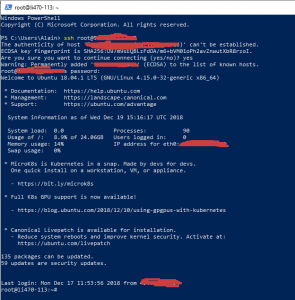
Теперь введите команду ssh для подключения к удаленному серверу Linux: ssh root@hostname-or-ip-address
б) SSH из командной строкой
Чтобы удаленно получить доступ к вашему серверу с помощью команды, вам просто нужно запустить его с помощью комбинации клавиш Windows + r и затем ввести cmd
Теперь в командной строке вы можете использовать команду ssh, как в случае с powershell
Теперь вы знаете, как можно подключиться к удаленному серверу Linux с помощью SSH с помощью встроенных в Windows инструментов.
Вы также можете использовать инструмент putty, но теперь проще и удобнее использовать инструменты, предлагаемые по умолчанию.
Sharing SSH keys between Windows and WSL 2
October 22nd, 2019
I recently wrote an article for Smashing Magazine that covers how I set up my personal development environment to use the Windows Subsystem for Linux version 2 (WSL 2). One of the things that I cover in that article is how to get SSH setup in WSL with Github. I mention in that section that you can share SSH keys between Windows and WSL, but I never showed exactly how to do it. There’s a good reason for that.
I couldn’t figure it out.
An SSH key is specific to a machine. Your machine. The problem is that the Linux distro you install in WSL see’s itself as it’s own operating system, and it wants its own set of SSH keys. The primary value propositions of WSL is that you can have both Linux AND Windows. As a developer, this is quite compelling as you can develop for both platforms on both platforms but with only one machine and without having to constantly switch OS’s. This means that you would need a set of SSH keys for Linux and one for Windows, ultimately treating your machine as 2 machines instead of one.
A better solution would be to share the same set of SSH keys between Windows and WSL so that you have one set of keys for one machine.
Setup SSH on Windows first
My recommendation is that you set up SSH on the Windows side first. Follow the instructions over on Github’s documentation to do this. It will walk you through generating the key, starting the agent and then adding your key to Github.
Copy keys to WSL
To use this same set of keys in WSL, you first need to copy them over. The keys are almost always located at c:\Users\ \.ssh . That’s a folder. You will need to copy that entire folder from Windows, to WSL.
Open a terminal instance attached to WSL. Might I recommend the free Windows Terminal? You’ll love it. I promise. If you’re not 100% satisfied, you can get your money back – no questions asked.
Execute the following command to copy the keys from Windows to WSL.
cp -r /mnt/c/Users/ /.ssh
Note that if you installed Github desktop, you do not need to setup SSH keys on the Windows side, and the .ssh folder will not be present. Make sure you follow the Github instructions above to generate the SSH keys on Windows.
Fix permissions
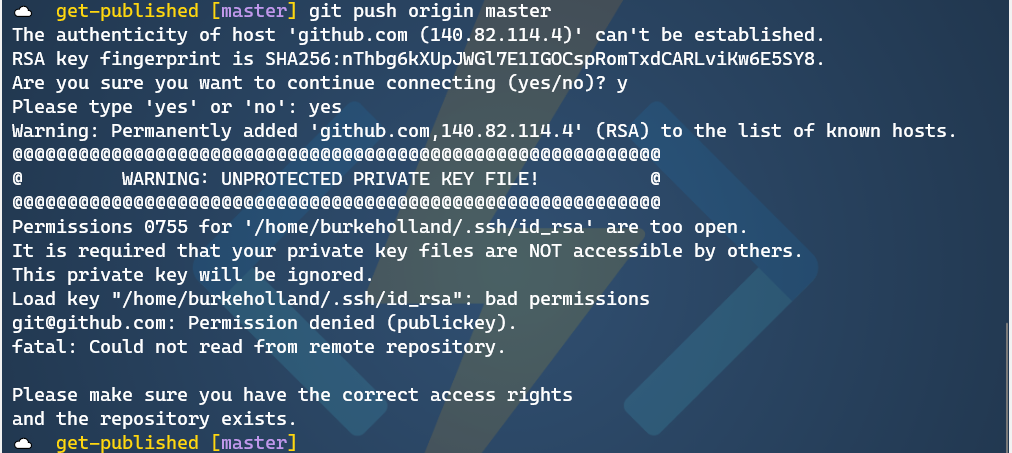
If you were to try and push something to Github from WSL, it will warn you that it doesn’t recognize the remote host and it will ask you if you want to connect. Type “yes”. Then you will get an error that looks something like this…
Like nearly everything that goes wrong on Linux, this is a permissions issue. You need to adjust the permissions on the key file to get this working. To do that, run the following command from WSL.
What this does is set Read/Write access for the owner, and no access for anyone else. That means that nobody but you can see this key. The way god intended.
Now try and push to Github…
Now, you will be asked to enter your passphrase every single time you try and push to Github. That’s going to get old in a hurry. This is because the ssh agent isn’t running on the Linux side. To get the agent running when WSL starts, first install keychain.
sudo apt install keychain
Then add the following line to your
eval «keychain —eval —agents ssh id_rsa
Each time you reboot, you’ll have to enter your passphrase. But you only have to do it one time until you reboot or terminate WSL.
There are other ways to auto-start the ssh-agent in WSL. There are instructions in this article that show how to do with with Zsh.
Sharing is caring
While you can set up SSH keys on both the Linux and the Windows side, it feels a bit redundant. It also feels a bit like I’m not utilizing the full potential of WSL, which is that it lets me move between the two operating systems as if they were one. Sharing the same set of keys feels a bit more like I’m on one system instead of two.
I care because I’m always looking for the one “right way” to do things. The reality is that there is no one “right way” to do anything. You can setup SSH keys on both WSL and Windows, or you can set them up just in Windows and share them with WSL. It’s your world. The ssh keys just live in it.
Run ssh and immediately execute command [duplicate]
I’m trying to find UNIX or bash command to run a command after connecting to an ssh server. For example:
The above code works, it lists the sessions, but it then immediately disconnects. Putting it in the sshrc on the server side works, but I need to be able to type it in client side. I want to be able to run a command, it logs in, opens up the window, then runs the command I’ve set. Ive tried
3 Answers 3
will execute the command and then start up a login shell when it completes. For example:
You can use the LocalCommand command-line option if the PermitLocalCommand option is enabled:
For more details about the available options, see the ssh_config man page.
This isn’t quite what you’re looking for, but I’ve found it useful in similar circumstances.
I recently added the following to my $HOME/.bashrc (something similar should be possible with shells other than bash):
I keep a screen session running on one particular machine, and I’ve had problems with ssh connections to that machine being dropped, requiring me to re-run screen -dr every time I reconnect.
With that addition, and after creating that (empty) file in my home directory, I automatically have the screen -dr command in my history when my shell starts. After reconnecting, I can just type Control-P Enter and I’m back in my screen session — or I can ignore it. It’s flexible, but not quite automatic, and in your case it’s easier than typing tmux list-sessions .
You might want to make the history -s command unconditional.
This does require updating your $HOME/.bashrc on each of the target systems, which might or might not make it unsuitable for your purposes.
openssh in Windows 7, run ssh-add once for all cmd instances
I have installed openSSH as part of the latest cygwin distribution. My goal is to use the ssh-agent from native window console (cmd) in order to login passwordless in a various number of Linux machines.
I have generated the keys and uploaded them to the appropriate directories in the remote hosts and everything works fine.
The only issue I have is that everytime I open a new cmd I have to run ‘ssh-add’, enter the passphrase and then I am able login passwordless in the remote hosts. Is there a way to overcome this problem? The ideal solution would be to run ssh-add only once.
fyi: I’m opening the cmd as an argument to the ssh-agent: ‘ssh-agent cmd’
2 Answers 2
I actually created a tool called «ssh-agent-helper» that invokes ssh-agent and makes it available globally, so that, you can use ssh-add , ssh or git from any terminal e.g. CMD, Bash, PowerShell etc without any configuration.
You will not be able to run ssh from the native command window. You will need to run the Cygwin bash «window» in order to run any of the Cygwin binaries.
Having said that, in the Cygwin bash «windows», you need to save the output of ssh-agent to a file and then source that file into any of the login scripts where you want to use the cached credentials. In the first «window», run:
In each of the others, run:
All of the «windows» and child processes started after the . your_save_file command is run will be able to use the credentials cached in ssh-agent. Any time that the ssh-agent is stopped or killed, or after a system reboot, you will need to run the first set of commands again. If you are in doubt about whether or not the cached credentials are available in a particular shell, run