- Subclassed
- 24 May 2018
- How to securely wipe an NVMe drive
- 2 comments:
- Solid state drive/Memory cell clearing
- Contents
- SATA drive
- Step 1 — Make sure the drive security is not frozen
- Dell Systems
- Step 2 — Enable security by setting a user password
- Step 3 — Issue the ATA Secure Erase command
- NVMe drive
- Format command
- Sanitize command
- Troubleshooting
- UEFI boot entries get removed after wiping a drive
- Securely Erasing Your SSD with Linux: A How-To
- Preparing the SSD & Enabling Hotplugging
- Discovering the Appropriate Drive in Linux
- #1 – Using Parted Magic
- #2 – Command-line Simple Secure Erase
- #3 – Command-line Advanced Secure Erase
- Rob Williams
Subclassed
24 May 2018
How to securely wipe an NVMe drive
NVMe drives are great: they are fast and they are huge. That huge size, however, can be a pain when it comes to securely erasing data. Old-school commands like wipe are simply not up to the task; and even if they were, they work on assumptions that do not map properly to a solid-state world. Writing random data over and over is going to dramatically reduce the lifespan of a solid-state drive, and it’s pointless when all NVMe disks already have built-in tools that can take care of this task quickly and safely.
So what do you do when you want to wipe a NVMe drive?
- Download a recent Linux distribution. I would recommend Debian/Ubuntu or one of their smaller derivatives (like Knoppix). Burn it on a cdrom or USB drive and boot the system from it.
- Make sure your package manager is up-to-date (under Debian/Ubuntu, sudo apt-get update ), then install nvme-cli ( sudo apt-get install nvme-cli )
- If your drive is a Samsung, it now has to be put to sleep (you can do that with sudo systemctl suspend ) and then woken up. This is a weird bug that Samsung doesn’t seem in any hurry to fix.
- Now you can securely wipe the disk: sudo nvme format -s1 /dev/nvme0n1
For the curious: the -s option triggers Secure Erase mode, which can be set to 1 (wipe) or 2 (delete encryption keys for encrypted data). 1 looks like the safest option, because it will automatically do what 2 does if it detects that all data is encrypted. Reference here.
The latest NVMe specification adds other commands, to scrub every nook and cranny (bus caches etc), but as far as I know they have not been implemented yet.
2 comments:
If your SSD is from Lenovo, it’ll be locked out. Even the newest Parted Magic can’t factory erase it. Gotta use «ThinkPad Drive Erase Utility for Resetting the Cryptographic Key and Erasing the Solid State Drive — ThinkPad»
I revisit this post semi-frequently, so thanks for the help. However, an update:
Newer versions of nvme-cli (I’m not sure when it changed) — like the one in Fedora 31/32’s repositories — needs a little extra effort:
«nvme format -s1 » throws an «invalid lbaf:255» error, but if you use «nvme format -s1 -lb=0 » it works perfectly after a ten second remorse timer.
Источник
Solid state drive/Memory cell clearing
On occasion, users may wish to completely reset the SSD to the initial «clean» state it was manufactured with, thus restoring it to its factory default write performance. Write performance is known to degrade over time even on SSDs with native TRIM support. TRIM only safeguards against file deletes, not replacements such as an incremental save.
Performing the Secure Erase does not reset the wear leveling status of SSD cells — a drive close to the end of its lifespan may become writable for a short while, but it will still fail after a limited amount of writes.
Contents
SATA drive
Step 1 — Make sure the drive security is not frozen
Issue the following command:
In the security section of the output it should say «not frozen». If it shows as just «frozen» then you cannot continue to the next step. Some BIOSes block the ATA Secure Erase command by issuing a «SECURITY FREEZE» command to «freeze» the drive before booting an operating system.
A possible solution is to simply suspend the system. Upon waking up, it is likely that the freeze will be lifted. If unsuccessful, one can try hot-(re)plug the data cable (which might crash the kernel). If hot-(re)plugging the SATA data cable crashes the kernel try letting the operating system fully boot up, then quickly hot-(re)plug both the SATA power and data cables. If hot-(re)plugging of SATA cables still crashes the kernel, make sure that AHCI is enabled in the BIOS (AHCI allows hot-(re)plugging operations without a crash). Using a USB-to-SATA adapter is an option if it supports hotplugging. One can also use hdparm via USB.
Dell Systems
If the command output shows «frozen», you may be able to work around it by:
- Reboot into the Dell BIOS by pressing F2 on startup.
- Set the Internal HDD Password in the BIOS (be careful, the keymap is en_US / qwerty).
- Apply the changes and reboot.
- When prompted for the password by Dell Security Manager, press Escape rather than entering it. The drive will remain locked but not frozen.
- Skip step 2, and go directly to Step 3 below.
Step 2 — Enable security by setting a user password
Any password will do, as this should only be temporary. After the secure erase the password will be set back to NULL. In this example, the password is PasSWorD as shown:
As a sanity check, issue the following command
The command output should display «enabled»:
Step 3 — Issue the ATA Secure Erase command
The final step is to issue the secure erase command, instructing the device’s BIOS to erase its contents. Note for the device used in this example, earlier output states:
As per ATA specification the enhanced security erase ( —security-erase-enhanced ) performs a more elaborate wipe. If the estimated completion time for both commands is equal, it indicates the drive manufacturer shortcut the specification and uses the same erase function for both. A short time (like 2 minutes) in turn indicates the device is self-encrypting and its BIOS function will wipe the internal encryption key instead of overwriting all data cells.[2]
Wait until the command completes. This example output shows it took about 40 seconds for an Intel X25-M 80GB SSD.
The drive is now erased. After a successful erasure the drive security should automatically be set to disabled (thus no longer requiring a password for access). Verify this by running the following command:
The command output should display «not enabled»:
NVMe drive
The NVMe specification defines a standardized way to format NVMe drives, since those do not use the SATA interface protocol and therefore cannot be cleared in the same way as SATA SSDs. Originally it was the nvme-format(1) command (part of the nvme-cli ) which provided this feature, but while it still does Specification 1.3 added support for a dedicated nvme-sanitize(1) command. As described by Jonmichael Hands, NVMe MWG Co-Chair, Sr. Strategic Planner / Product Manager, Intel[3]:
«These commands are used to securely erase user data from the device. This can be used when deploying a new device, retiring or at device end-of-life, using an SSD for a new application and so on. Sanitize was introduced in NVMe 1.3 specification, so before then NVMe Format was used exclusively to perform secure erase. While both options work, Sanitize is more robust for ensuring the data was properly wiped; format is good for everyday use and testing.«
In order to verify what is supported by your drive, use the Identify Controller command:
Then proceed with either format or sanitize.
Format command
The Format command is conceptually closer to a mix of hdparm and fdisk, as it allows to set low-level parameters for the drive and additionally to send a secure erase command.
nvme-format(1) gives the following details about the Secure Erase Settings ( -s , —ses= ) option:
Secure Erase Settings: This field specifies whether a secure erase should be performed as part of the format and the type of the secure erase operation. The erase applies to all user data, regardless of location (e.g., within an exposed LBA, within a cache, within deallocated LBAs, etc). Defaults to 0.
| Value | Definitions |
|---|---|
| 0 | No secure erase operation requested |
| 1 | User Data Erase: All user data shall be erased, contents of the user data after the erase is indeterminate (e.g., the user data may be zero filled, one filled, etc). The controller may perform a cryptographic erase when a User Data Erase is requested if all user data is encrypted. |
| 2 | Cryptographic Erase: All user data shall be erased cryptographically. This is accomplished by deleting the encryption key. |
While the Format command accepts either the whole NVMe character device (e.g. /dev/nvme0 ) or a specific namespace block device (e.g. /dev/nvme0n1 ), make sure this feature is supported by your drive before triggering it. E.g. in the output of the Identify Controller command above, we see that the Crypto Erase Applies to Single Namespace(s) and Format Applies to Single Namespace(s) bits are set to zero, which according to the spec means that «the controller supports format on a per namespace basis» (see figure 249 byte row 524 «Format NVM Attributes (FNA)»).
For example, to format /dev/nvme0 with a crypto erase to namespace 1:
See nvme-format(1) for more information and important warnings regarding device/namespace selection.
Sanitize command
The Sanitize command was created to be «functionally equivalent to the command of the same name in SATA and SAS implementations»[4]. From the aforementionned article[5]:
«According to the NVMe 1.4 specification, “a sanitize operation alters all user data in the NVM subsystem such that recovery of any previous user data from any cache, the non-volatile media, or any Controller Memory Buffer is not possible.” The big difference between Sanitize and Format is that sanitize ensures caches are deleted, and the process starts again after an unexpected power loss. Sanitize also supports a pattern overwrite for a secure erase operation, which is terrible for NAND endurance but can be used with other types of storage and memory classes, or for more certainty that user data cannot be recovered.»
Usage and possible values for the -a/—sanact options are[6]:
See nvme-sanitize(1) for more informations.
You can get an estimation of the time the various methods would take on your drive (if supported):
If instead you get a result such as:
Then be sure that the operation will take a long time to complete. For reference, a Block Erase took around 2-3 hours to complete on the Intel 660p 512GB reporting those results.
To start a Crypto Erase sanitize operation:
For a Block Erase:
You can follow the progress with the Sanitize Log:
Example output for a drive with a Crypto Erase in progress:
When the command has completed successfully:
Troubleshooting
UEFI boot entries get removed after wiping a drive
Some UEFI implementations remove boot entries referencing nonexistent files upon system startup. If you plan to restore the system from a backup after memory cell clearing, make sure to also restore the boot entry using efibootmgr or by reinstalling the boot loader.
Источник
Securely Erasing Your SSD with Linux: A How-To
Tired of dealing with slowed performance or some bizarre partition error with your SSD? Sometimes, the solution is as simple as a secure erase – that is, to bring the drive back to its innate, factory-fresh state. Thanks to Linux, getting this job done is easier than ever. Join us, as we cover multiple methods for getting the job done.
Whether for slowed performance or some other issue that’s crept up, sometimes securely erasing your SSD is the solution needed. While there are a number of ways to get the deed done, most solutions are hit-or-miss, and are generally not that elegant. In my personal experience, the easiest way to secure erase a drive is through Linux, and as the title of this article suggests, that’s exactly the route we’re taking here. The best part? You don’t need to understand Linux to follow this guide.
First things first: if you don’t already have a version of Linux installed, you’ll need to download a distro and create a bootable CD-ROM or flash drive. If your intention is to only secure erase an SSD, it’s recommended you download Parted Magic, a distro designed around managing storage. If you’d rather have a bootable Linux environment that’s setup like a real desktop, then another distro can be used, such as Ubuntu, Fedora, and openSUSE. For this article, I’m using Linux Deepin, in addition to Parted Magic.
Update: Since this article went live, the developer of Parted Magic began charging $4.99 for the software. Given all that the live CD can do, I believe it’s well-worth the cost-of-entry. However, if you are merely looking to secure erase your SSD, you might feel that any fee is a bit much. If that’s the case, forego grabbing Parted Magic and check out the other options below for secure erasing your SSD.
Once your chosen ISO is downloaded, you can burn it to a CD-ROM or go the flash drive route. When given the choice, I recommend using a flash drive, as it’s more flexible, and faster to boot (no pun). To create a bootable flash drive, you’ll want to grab UNetbootin, run it (no install necessary), click the “Diskimage” option, search for your ISO, select the proper drive, and hit “OK”. Once all of the files are copied over, you’ll be able to boot into that flash device.
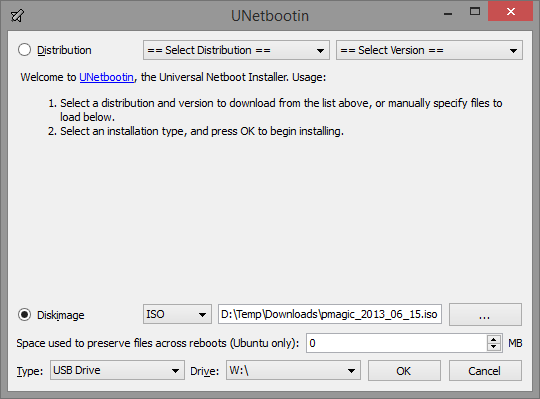
Use UNetbootin to create a bootable Linux OS
Because there’s no one secure erase solution that will work for everyone, we’re giving you three options here, ordered from easiest to most difficult (though no solution is that difficult). You can feel free to jump to any section that you need, but for absolute beginners I’d recommend continuing with the first section below.
Jump to:
Preparing the SSD & Enabling Hotplugging
Hotplugging is the act of connecting an SSD (or an HDD, for that matter) to a machine that’s powered-on. Some chassis have this support built-in with special bays, and if you happen to have one, you can use it if the SSD in question is not already installed internally. For everyone else, you’ll need to take the side off of your computer, and while its powered-down, disconnect the SATA data cable for that drive from the motherboard, leaving the SATA power cable plugged into the drive.
Most BIOSes do not offer hotplug options, but most EFIs do. You can see an example of the option in the EFI below, taken from GIGABYTE’s Z77X-UP4 TH motherboard.
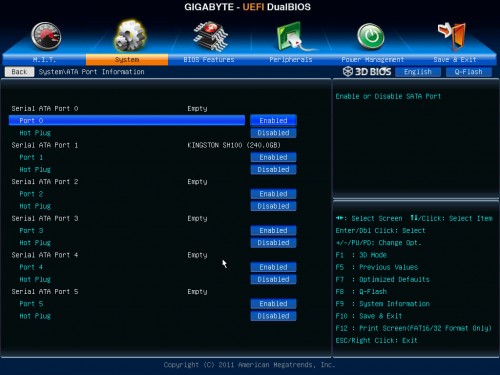
Hotplug option inside of an EFI
If you happen to know the exact port number you’re going to be plugging the target drive into, you can enable hotplugging for that one port. Otherwise, you can enable hotplugging for every available port; there are no downsides to this, performance or otherwise. Set the options that are needed, save and reboot.
Can’t Use Hotplugging? A lot of modern USB HDD/SSD docks can manage the ATA commands required to secure erase, so it’s worth trying to use one for the purpose if you have one around. Thermaltake’s BlacX is an example of an enclosure that can be used to secure erase an SSD.
Discovering the Appropriate Drive in Linux
Boot into either your installed Linux desktop or the live environment you’ve prepared earlier. Once you’re booted to the desktop, connect the SSD’s SATA data cable back to the appropriate motherboard port.
Once ready, open GParted. With Parted Magic, double-click “Partition Editor” on the desktop; for other distros, search through the main menu, or hit Alt + F2 and type ‘gparted’ to (hopefully) bring it up as a search result. If you’re not doing this through a live environment, you will have to enter your password.
GParted can be found in most Linux distros
With GParted open, navigate to the drop-down menu near the top-right corner and find the drive that you wish to be securely erased. If the density isn’t enough to tip you off as to whether or not you have the correct drive selected, its partition layout should be.
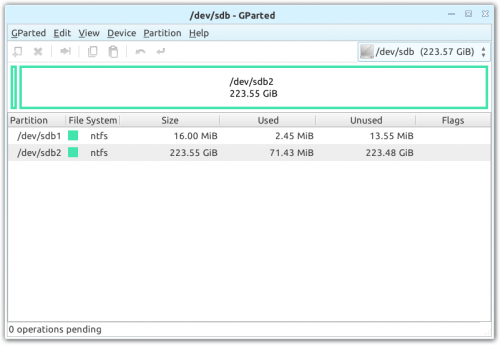
GParted showing an SSD before secure erase
With the proper drive selected, note its “/dev/sdX” value, which is its drive letter (think C:\ in Windows).
#1 – Using Parted Magic
Parted Magic offers the easiest method of securely erasing a drive, as it negates the need for a command-line. However, it might not work for all systems, so for that reason we give more advanced methods later.
At the main desktop, double-click the “Erase Disk” icon, and with the tool loaded, click “Internal Secure Erase command writes zeros to entire data area”.
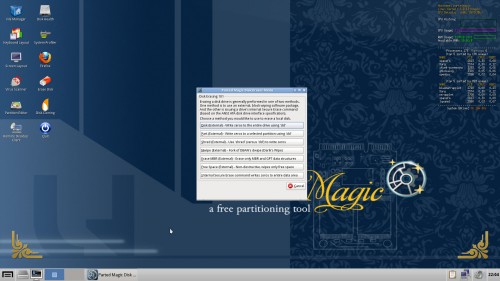
Parted Magic has a useful tool called ‘Erase Disk’
The process is simple at this point; click on the SSD in question, and then “OK”.
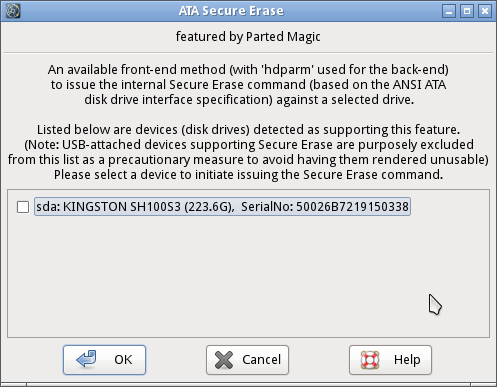
A secure erase is just a step away
After a second or thirty, the SSD will be as clean as a whistle. If not, you’re likely looking at a dialog box that recommends putting the PC into a sleep state, so that you can have a second chance once the PC wakes back up. It’s worth giving that a chance, but don’t expect it to work.
If the process did in fact work, the drive is clean; you can now open GParted (via the “Partition Editor” on the desktop), and with the correct drive selected, click on “Device” at the top, then “Create Partition” and finally, “Apply”. This step is not necessary, but it can prevent potential complications when trying to install an OS.
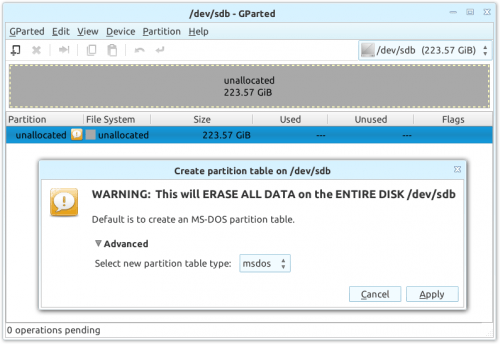
Creating a fresh partition table
If this Parted Magic method doesn’t work for you, it’s time to move onto step #2.
#2 – Command-line Simple Secure Erase
Open up a command-line (terminal) either through the OS menu, or by hitting Alt + F2 and typing in “terminal”. If for some reason “terminal” yields no results, you’ll be forced to navigate the OS menu and find its replacement (eg: ROXTerm, gnome-terminal, Konsole, et cetera).
Useful commands (which require root (su) or sudo (sudo -s, or just type “sudo” before each command):
- hdparm -I /dev/sdX – Displays all information about a drive.
- hdparm -I /dev/sdX | grep Model – Displays the drive brand and model.
- hdparm -I /dev/sdX | grep frozen – Displays whether or not the drive is frozen (“not” is required).
- hdparm –security-erase PASS /dev/sdX – Simple command to secure erase a drive with no hassle.
Note: There are two dashes before the user-master and security- commands. The info commands above use a capital i, not a small L.
An important command here is either the first or third. We need the drive to be “not” frozen, and if that’s the case, then it’s a matter of running the fourth command:
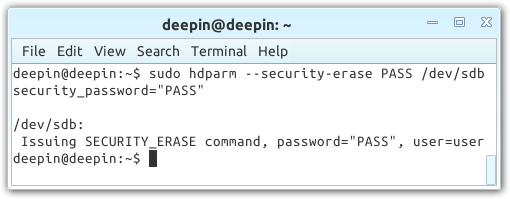
Performing a simple secure erase
If the result matches what’s seen in the above screenshot, you can now open GParted (via the OS menu or Alt + F2 and typing in “gparted”), and with the correct drive selected, click on “Device” at the top, then “Create Partition” and finally, “Apply”. This step is not necessary, but it can prevent potential complications when trying to install an OS.

Creating a fresh partition table
If the process spawns an error about a password being required or otherwise, move onto the next method.
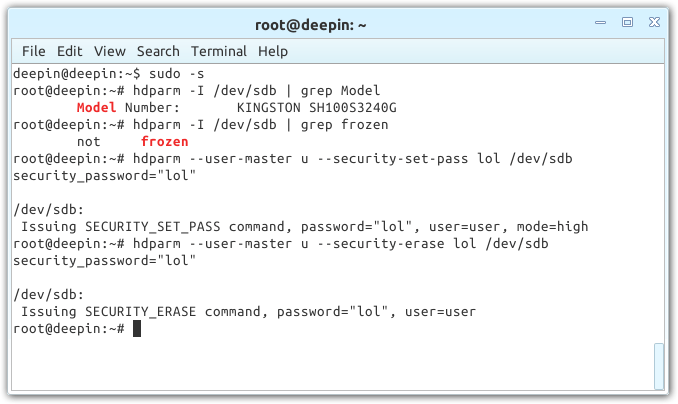
#3 – Command-line Advanced Secure Erase
Open up a command-line (terminal) either through the OS menu, or by hitting Alt + F2 and typing in “terminal”. If for some reason “terminal” yields no results, you’ll be forced to navigate the OS menu and find its replacement (eg: ROXTerm, gnome-terminal, Konsole, et cetera).
Useful commands (which require root (su) or sudo (sudo -s, or just type “sudo” before each command):
- hdparm -I /dev/sdX – Displays all information about a drive.
- hdparm -I /dev/sdX | grep Model – Displays the drive brand and model.
- hdparm -I /dev/sdX | grep frozen – Displays whether or not the drive is frozen (“not” is required).
- hdparm –security-erase PASS /dev/sdX – Simple command to secure erase a drive with no hassle.
- hdparm –user-master u –security-set-pass /dev/sdX – Sets a password.
- hdparm –user-master u –security-erase /dev/sdX – Securely erases the SSD.
Note: There are two dashes before the user-master and security- commands. The info commands above use a capital i, not a small L.
The important command here is either the first or third. We need the drive to be “not” frozen, and if that’s the case, then proceed to password the drive via the fifth command; it doesn’t matter what is, but the same text needs to be used for both commands. Once that’s done, run the sixth command.
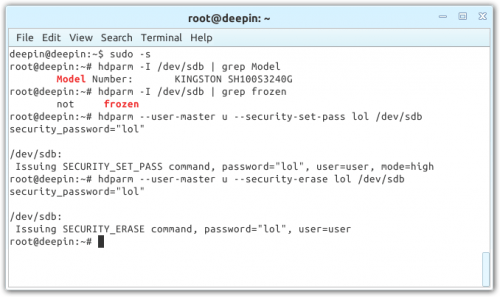
Identifying the SSD and performing a secure erase
If the result matches what’s seen in the above screenshot, you can now open GParted (via the OS menu or Alt + F2 and typing in “gparted”), and with the correct drive selected, click on “Device” at the top, then “Create Partition” and finally, “Apply”. This step is not necessary, but it can prevent potential complications when trying to install an OS.

Creating a fresh partition table
If for some reason this or the earlier commands are not getting the job done, I’d recommend going with the earlier suggestion of attempting the secure erase with the help of an external USB enclosure, such as Thermaltake’s BlacX. If that’s not possible, you might unfortunately be out of luck, short of using one of these methods on another PC.
Questions and comments are welcomed. We might not be able to get your SSD securely erased if none of the above methods work, but we can sure try.
Support our efforts! With ad revenue at an all-time low for written websites, we’re relying more than ever on reader support to help us continue putting so much effort into this type of content. You can support us by becoming a Patron, or by using our Amazon shopping affiliate links listed through our articles. Thanks for your support!
Rob Williams
Rob founded Techgage in 2005 to be an ‘Advocate of the consumer’, focusing on fair reviews and keeping people apprised of news in the tech world. Catering to both enthusiasts and businesses alike; from desktop gaming to professional workstations, and all the supporting software.
Источник