- Создание аудитов безопасности Generate security audits
- Справочные материалы Reference
- Возможные значения Possible values
- Рекомендации Best practices
- Location Location
- Значения по умолчанию Default values
- Управление политикой Policy management
- Групповая политика Group Policy
- Вопросы безопасности Security considerations
- Уязвимость Vulnerability
- Противодействие Countermeasure
- Возможное влияние Potential impact
- 4634(S): An account was logged off.
- Computer Hangs microsoft windows security auditing event id 4624.
- 4624(S): An account was successfully logged on.
- Logon types and descriptions
- Security Monitoring Recommendations
Создание аудитов безопасности Generate security audits
Область применения Applies to
В этой статье описываются лучшие методики, расположение, значения, управление политиками и вопросы безопасности для параметра политики безопасности «Создание аудита безопасности». Describes the best practices, location, values, policy management, and security considerations for the Generate security audits security policy setting.
Справочные материалы Reference
Этот параметр политики определяет, какие учетные записи могут использоваться процессом для создания записей аудита в журнале событий безопасности. This policy setting determines which accounts can be used by a process to generate audit records in the security event log. Служба подсистемы локального органа безопасности (LSASS) записывает события в журнал. The Local Security Authority Subsystem Service (LSASS) writes events to the log. Сведения в журнале событий безопасности можно использовать для трассировки несанкционированного доступа к устройству. You can use the information in the security event log to trace unauthorized device access.
Константа: SeAuditPrivilege Constant: SeAuditPrivilege
Возможные значения Possible values
- Определяемый пользователей список учетных записей User-defined list of accounts
- Локализованная служба Local Service
- Сетовая служба Network Service
Рекомендации Best practices
- Так как журнал аудита потенциально может быть вектором атаки при компрометации учетной записи, убедитесь, что только учетные записи локальной и сетевой служб имеют право на создание аудитов безопасности, которые им назначены. **** Because the audit log can potentially be an attack vector if an account is compromised, ensure that only the Local Service and Network Service accounts have the Generate security audits user right assigned to them.
Location Location
Computer Configuration\Windows Settings\Security Settings\Local Policies\User Rights Assignment Computer Configuration\Windows Settings\Security Settings\Local Policies\User Rights Assignment
Значения по умолчанию Default values
По умолчанию этот параметр имеет значение Local Service and Network Service на контроллерах домена и автономных серверах. By default, this setting is Local Service and Network Service on domain controllers and stand-alone servers.
В следующей таблице перечислены фактические и эффективные значения политики по умолчанию для последних поддерживаемых версий Windows. The following table lists the actual and effective default policy values for the most recent supported versions of Windows. Значения по умолчанию также можно найти на странице свойств политики. Default values are also listed on the policy’s property page.
| Тип сервера или объект групповой политики Server type or GPO | Значение по умолчанию Default value |
|---|---|
| Default Domain Policy Default Domain Policy | Не определено Not defined |
| Политика контроллера домена по умолчанию Default Domain Controller Policy | Локализованная служба Local Service Сетовая служба Network Service |
| Параметры по умолчанию для автономного сервера Stand-Alone Server Default Settings | Локализованная служба Local Service Сетовая служба Network Service |
| Действующие параметры по умолчанию для контроллера домена Domain Controller Effective Default Settings | Локализованная служба Local Service Сетовая служба Network Service |
| Действующие параметры по умолчанию для рядового сервера Member Server Effective Default Settings | Локализованная служба Local Service Сетовая служба Network Service |
| Действующие параметры по умолчанию для клиентского компьютера Client Computer Effective Default Settings | Локализованная служба Local Service Сетовая служба Network Service |
Управление политикой Policy management
В этом разделе описаны компоненты, средства и рекомендации, которые помогут в управлении этой политикой. This section describes features, tools, and guidance to help you manage this policy.
Для активации этого параметра политики не требуется перезагрузка компьютера. A restart of the computer is not required for this policy setting to be effective.
Изменения прав пользователя вступают в силу при его следующем входе в учетную запись. Any change to the user rights assignment for an account becomes effective the next time the owner of the account logs on.
Неправильное использование этого права пользователя может привести к генерации многих событий аудита, потенциально скрывая признаки атаки или вызывая отказ в обслуживании (DoS), если аудит: немедленное завершение работы системы, если не удается занося в журнал параметр политики безопасности аудита безопасности. Misuse of this user right can result in the generation of many auditing events, potentially hiding evidence of an attack or causing a denial-of-service (DoS) if the Audit: Shut down system immediately if unable to log security audits security policy setting is enabled.
Групповая политика Group Policy
Параметры применяются в следующем порядке с помощью объекта групповой политики (GPO), который будет перезаписывать параметры на локальном компьютере при следующем обновлении групповой политики: Settings are applied in the following order through a Group Policy Object (GPO), which will overwrite settings on the local computer at the next Group Policy update:
- Параметры локальной политики Local policy settings
- Параметры политики сайта Site policy settings
- Параметры политики домена Domain policy settings
- Параметры политики подразделения OU policy settings
Если локальный параметр затеняется, это означает, что в настоящее время этот параметр контролируется GPO. When a local setting is greyed out, it indicates that a GPO currently controls that setting.
Вопросы безопасности Security considerations
В этом разделе описывается, каким образом злоумышленник может использовать компонент или его конфигурацию, как реализовать меры противодействия, а также рассматриваются возможные отрицательные последствия их реализации. This section describes how an attacker might exploit a feature or its configuration, how to implement the countermeasure, and the possible negative consequences of countermeasure implementation.
Уязвимость Vulnerability
Злоумышленник может использовать учетные записи, которые могут записываться в журнал безопасности, чтобы заполнить этот журнал бессмысленными событиями. A malicious user could use accounts that can write to the Security log to fill that log with meaningless events. Если компьютер настроен для перезаписи событий по мере необходимости, злоумышленники могут использовать этот метод, чтобы удалить признаки своих несанкционированных действий. If the computer is configured to overwrite events as needed, malicious users could use this method to remove evidence of their unauthorized activities. Если компьютер настроен на завершение работы, когда не удается записать данные в журнал безопасности и не настроен на автоматическое создание архива файлов журнала, этот метод можно использовать для создания условия DoS. If the computer is configured to shut down when it is unable to write to the Security log, and it is not configured to automatically back up the log files, this method could be used to create a DoS condition.
Противодействие Countermeasure
Убедитесь, что только учетные записи **** локальных и сетевых служб имеют право на создание аудитов безопасности, которые им назначены. Ensure that only the Local Service and Network Service accounts have the Generate security audits user right assigned to them.
Возможное влияние Potential impact
Нет. None. Настройка по умолчанию ограничивает права пользователя «Создание аудитов безопасности» на учетные записи локальной службы и сетевой службы. Restricting the Generate security audits user right to the Local Service and Network Service accounts is the default configuration.
4634(S): An account was logged off.
Applies to
- Windows 10
- Windows Server 2016
Event Description:
This event shows that logon session was terminated and no longer exists.
The main difference between “4647: User initiated logoff.” and 4634 event is that 4647 event is generated when logoff procedure was initiated by specific account using logoff function, and 4634 event shows that session was terminated and no longer exists.
4647 is more typical for Interactive and RemoteInteractive logon types when user was logged off using standard methods. You will typically see both 4647 and 4634 events when logoff procedure was initiated by user.
It may be positively correlated with a “4624: An account was successfully logged on.” event using the Logon ID value. Logon IDs are only unique between reboots on the same computer.
NoteВ В For recommendations, see Security Monitoring Recommendations for this event.
Event XML:
Required Server Roles: None.
Minimum OS Version: Windows Server 2008, Windows Vista.
Event Versions: 0.
Field Descriptions:
Subject:
- Security ID [Type = SID]: SID of account that was logged off. Event Viewer automatically tries to resolve SIDs and show the account name. If the SID cannot be resolved, you will see the source data in the event.
NoteВ В A security identifier (SID) is a unique value of variable length used to identify a trustee (security principal). Each account has a unique SID that is issued by an authority, such as an Active Directory domain controller, and stored in a security database. Each time a user logs on, the system retrieves the SID for that user from the database and places it in the access token for that user. The system uses the SID in the access token to identify the user in all subsequent interactions with Windows security. When a SID has been used as the unique identifier for a user or group, it cannot ever be used again to identify another user or group. For more information about SIDs, see Security identifiers.
Account Name [Type = UnicodeString]: the name of the account that was logged off.
Account Domain [Type = UnicodeString]: subject’s domain or computer name. Formats vary, and include the following:
Domain NETBIOS name example: CONTOSO
Lowercase full domain name: contoso.local
Uppercase full domain name: CONTOSO.LOCAL
For some well-known security principals, such as LOCAL SERVICE or ANONYMOUS LOGON, the value of this field is “NT AUTHORITY”.
For local user accounts, this field will contain the name of the computer or device that this account belongs to, for example: “Win81”.
Logon ID [Type = HexInt64]: hexadecimal value that can help you correlate this event with recent events that might contain the same Logon ID, for example, “4624: An account was successfully logged on.”
Logon Type [Type = UInt32]: the type of logon which was used. The table below contains the list of possible values for this field:
Computer Hangs microsoft windows security auditing event id 4624.
Hi all.. Im having some problems with my comp hanging while i listen to music lately..I looked at Windows event viewer and this is what i found with the corresponding times. This is quiite annoying any help you can suggest would be terrific. Im using Windows 7 64 bit
Description of the error:
An account was successfully logged on.
Subject:
Security ID: SYSTEM
Account Name: MATT-PC$
Account Domain: WORKGROUP
Logon ID: 0x3e7
New Logon:
Security ID: SYSTEM
Account Name: SYSTEM
Account Domain: NT AUTHORITY
Logon ID: 0x3e7
Logon GUID:
Process Information:
Process ID: 0x204
Process Name: C:\Windows\System32\services.exe
Network Information:
Workstation Name:
Source Network Address: —
Source Port: —
Detailed Authentication Information:
Logon Process: Advapi
Authentication Package: Negotiate
Transited Services: —
Package Name (NTLM only): —
Key Length: 0
This event is generated when a logon session is created. It is generated on the computer that was accessed.
The subject fields indicate the account on the local system which requested the logon. This is most commonly a service such as the Server service, or a local process such as Winlogon.exe or Services.exe.
The logon type field indicates the kind of logon that occurred. The most common types are 2 (interactive) and 3 (network).
The New Logon fields indicate the account for whom the new logon was created, i.e. the account that was logged on.
The network fields indicate where a remote logon request originated. Workstation name is not always available and may be left blank in some cases.
The authentication information fields provide detailed information about this specific logon request.
— Logon GUID is a unique identifier that can be used to correlate this event with a KDC event.
— Transited services indicate which intermediate services have participated in this logon request.
— Package name indicates which sub-protocol was used among the NTLM protocols.
— Key length indicates the length of the generated session key. This will be 0 if no session key was requested.
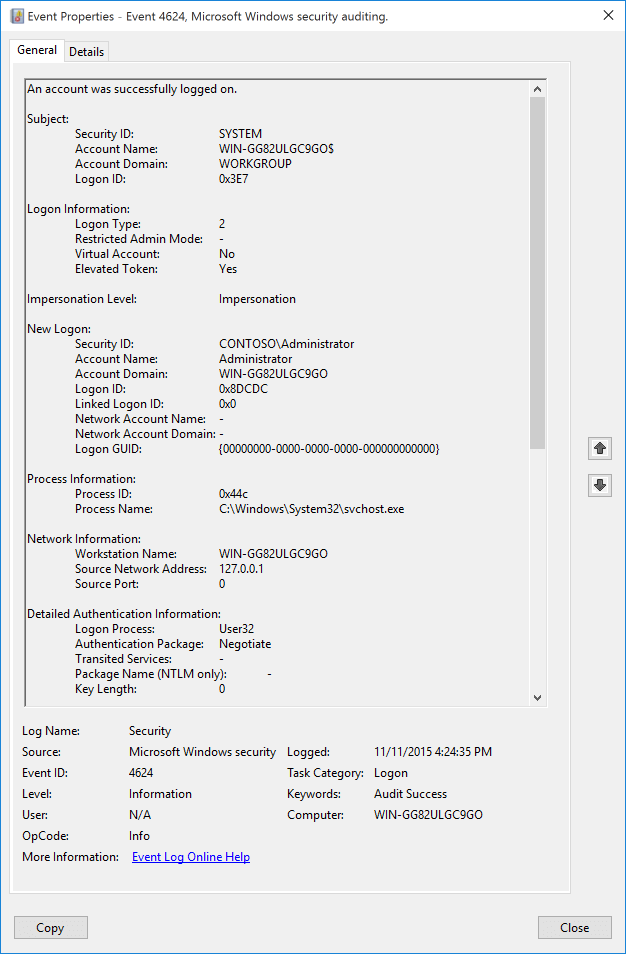
4624(S): An account was successfully logged on.
Applies to
- Windows 10
- Windows Server 2016
Event Description:
This event generates when a logon session is created (on destination machine). It generates on the computer that was accessed, where the session was created.
For recommendations, see Security Monitoring Recommendations for this event.
Event XML:
Required Server Roles: None.
Minimum OS Version: Windows Server 2008, Windows Vista.
Event Versions:
0 — Windows Server 2008, Windows Vista.
1 — Windows Server 2012, Windows 8.
- Added «Impersonation Level» field.
2 – Windows 10.
Added «Logon Information:» section.
Logon Type moved to «Logon Information:» section.
Added «Restricted Admin Mode» field.
Added «Virtual Account» field.
Added «Elevated Token» field.
Added «Linked Logon ID» field.
Added «Network Account Name» field.
Added «Network Account Domain» field.
Field Descriptions:
Subject:
Security ID [Type = SID]: SID of account that reported information about successful logon or invokes it. Event Viewer automatically tries to resolve SIDs and show the account name. If the SID cannot be resolved, you will see the source data in the event.
A security identifier (SID) is a unique value of variable length used to identify a trustee (security principal). Each account has a unique SID that is issued by an authority, such as an Active Directory domain controller, and stored in a security database. Each time a user logs on, the system retrieves the SID for that user from the database and places it in the access token for that user. The system uses the SID in the access token to identify the user in all subsequent interactions with Windows security. When a SID has been used as the unique identifier for a user or group, it cannot ever be used again to identify another user or group. For more information about SIDs, see Security identifiers.
Account Name [Type = UnicodeString]: the name of the account that reported information about successful logon.
Account Domain [Type = UnicodeString]: subject’s domain or computer name. Formats vary, and include the following:
Domain NETBIOS name example: CONTOSO
Lowercase full domain name: contoso.local
Uppercase full domain name: CONTOSO.LOCAL
For some well-known security principals, such as LOCAL SERVICE or ANONYMOUS LOGON, the value of this field is «NT AUTHORITY».
For local user accounts, this field will contain the name of the computer or device that this account belongs to, for example: «Win81».
Logon ID [Type = HexInt64]: hexadecimal value that can help you correlate this event with recent events that might contain the same Logon ID, for example, «4672(S): Special privileges assigned to new logon.»
Logon Information [Version 2]:
- Logon Type [Version 0, 1, 2] [Type = UInt32]: the type of logon which was performed. The table below contains the list of possible values for this field.
Logon types and descriptions
| Logon Type | Logon Title | Description |
|---|---|---|
| 0 | System | Used only by the System account, for example at system startup. |
| 2 | Interactive | A user logged on to this computer. |
| 3 | Network | A user or computer logged on to this computer from the network. |
| 4 | Batch | Batch logon type is used by batch servers, where processes may be executing on behalf of a user without their direct intervention. |
| 5 | Service | A service was started by the Service Control Manager. |
| 7 | Unlock | This workstation was unlocked. |
| 8 | NetworkCleartext | A user logged on to this computer from the network. The user’s password was passed to the authentication package in its unhashed form. The built-in authentication packages all hash credentials before sending them across the network. The credentials do not traverse the network in plaintext (also called cleartext). |
| 9 | NewCredentials | A caller cloned its current token and specified new credentials for outbound connections. The new logon session has the same local identity, but uses different credentials for other network connections. |
| 10 | RemoteInteractive | A user logged on to this computer remotely using Terminal Services or Remote Desktop. |
| 11 | CachedInteractive | A user logged on to this computer with network credentials that were stored locally on the computer. The domain controller was not contacted to verify the credentials. |
| 12 | CachedRemoteInteractive | Same as RemoteInteractive. This is used for internal auditing. |
| 13 | CachedUnlock | Workstation logon. |
Restricted Admin Mode [Version 2] [Type = UnicodeString]: Only populated for RemoteInteractive logon type sessions. This is a Yes/No flag indicating if the credentials provided were passed using Restricted Admin mode. Restricted Admin mode was added in Win8.1/2012R2 but this flag was added to the event in Win10.
If not a RemoteInteractive logon, then this will be «-» string.
Virtual Account [Version 2] [Type = UnicodeString]: a «Yes» or «No» flag, which indicates if the account is a virtual account (e.g., «Managed Service Account»), which was introduced in Windows 7 and Windows Server 2008 R2 to provide the ability to identify the account that a given Service uses, instead of just using «NetworkService».
Elevated Token [Version 2] [Type = UnicodeString]: a «Yes» or «No» flag. If «Yes», then the session this event represents is elevated and has administrator privileges.
Impersonation Level [Version 1, 2] [Type = UnicodeString]: can have one of these four values:
SecurityAnonymous (displayed as empty string): The server process cannot obtain identification information about the client, and it cannot impersonate the client. It is defined with no value given, and thus, by ANSI C rules, defaults to a value of zero.
SecurityIdentification (displayed as «Identification«): The server process can obtain information about the client, such as security identifiers and privileges, but it cannot impersonate the client. This is useful for servers that export their own objects, for example, database products that export tables and views. Using the retrieved client-security information, the server can make access-validation decisions without being able to use other services that are using the client’s security context.
SecurityImpersonation (displayed as «Impersonation«): The server process can impersonate the client’s security context on its local system. The server cannot impersonate the client on remote systems. This is the most common type.
SecurityDelegation (displayed as «Delegation«): The server process can impersonate the client’s security context on remote systems.
New Logon:
Security ID [Type = SID]: SID of account for which logon was performed. Event Viewer automatically tries to resolve SIDs and show the account name. If the SID cannot be resolved, you will see the source data in the event.
A security identifier (SID) is a unique value of variable length used to identify a trustee (security principal). Each account has a unique SID that is issued by an authority, such as an Active Directory domain controller, and stored in a security database. Each time a user logs on, the system retrieves the SID for that user from the database and places it in the access token for that user. The system uses the SID in the access token to identify the user in all subsequent interactions with Windows security. When a SID has been used as the unique identifier for a user or group, it cannot ever be used again to identify another user or group. For more information about SIDs, see Security identifiers.
Account Name [Type = UnicodeString]: the name of the account for which logon was performed.
Account Domain [Type = UnicodeString]: subject’s domain or computer name. Formats vary, and include the following:
Domain NETBIOS name example: CONTOSO
Lowercase full domain name: contoso.local
Uppercase full domain name: CONTOSO.LOCAL
For some well-known security principals, such as LOCAL SERVICE or ANONYMOUS LOGON, the value of this field is «NT AUTHORITY».
For local user accounts, this field will contain the name of the computer or device that this account belongs to, for example: «Win81».
Logon ID [Type = HexInt64]: hexadecimal value that can help you correlate this event with recent events that might contain the same Logon ID, for example, «4672(S): Special privileges assigned to new logon.»
Linked Logon ID [Version 2] [Type = HexInt64]: A hexadecimal value of the paired logon session. If there is no other logon session associated with this logon session, then the value is «0x0«.
Network Account Name [Version 2] [Type = UnicodeString]: User name that will be used for outbound (network) connections. Valid only for NewCredentials logon type.
If not NewCredentials logon, then this will be a «-» string.
Network Account Domain [Version 2] [Type = UnicodeString]: Domain for the user that will be used for outbound (network) connections. Valid only for NewCredentials logon type.
If not NewCredentials logon, then this will be a «-» string.
Logon GUID [Type = GUID]: a GUID that can help you correlate this event with another event that can contain the same Logon GUID, «4769(S, F): A Kerberos service ticket was requested event on a domain controller.
It also can be used for correlation between a 4624 event and several other events (on the same computer) that can contain the same Logon GUID, «4648(S): A logon was attempted using explicit credentials» and «4964(S): Special groups have been assigned to a new logon.»
This parameter might not be captured in the event, and in that case appears as «<00000000-0000-0000-0000-000000000000>«.
GUID is an acronym for ‘Globally Unique Identifier’. It is a 128-bit integer number used to identify resources, activities, or instances.
Process Information:
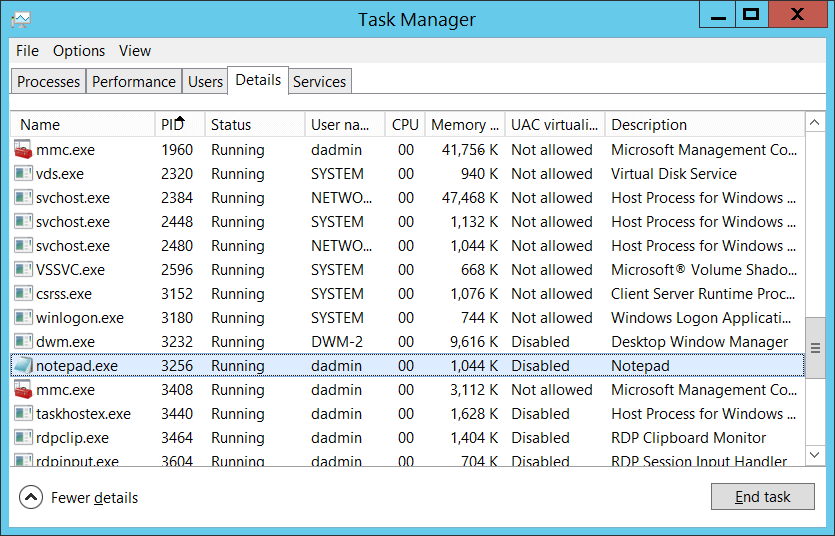
Process ID [Type = Pointer]: hexadecimal Process ID of the process that attempted the logon. Process ID (PID) is a number used by the operating system to uniquely identify an active process. To see the PID for a specific process you can, for example, use Task Manager (Details tab, PID column):
If you convert the hexadecimal value to decimal, you can compare it to the values in Task Manager.
You can also correlate this process ID with a process ID in other events, for example, «4688: A new process has been created» Process Information\New Process ID.
Process Name [Type = UnicodeString]: full path and the name of the executable for the process.
Network Information:
Workstation Name [Type = UnicodeString]: machine name from which a logon attempt was performed.
Source Network Address [Type = UnicodeString]: IP address of machine from which logon attempt was performed.
IPv6 address or ::ffff:IPv4 address of a client.
::1 or 127.0.0.1 means localhost.
Source Port [Type = UnicodeString]: source port which was used for logon attempt from remote machine.
Detailed Authentication Information:
Logon Process [Type = UnicodeString]: the name of the trusted logon process that was used for the logon. See event «4611: A trusted logon process has been registered with the Local Security Authority» description for more information.
Authentication Package [Type = UnicodeString]: The name of the authentication package which was used for the logon authentication process. Default packages loaded on LSA startup are located in «HKLM\SYSTEM\CurrentControlSet\Control\Lsa\OSConfig» registry key. Other packages can be loaded at runtime. When a new package is loaded a «4610: An authentication package has been loaded by the Local Security Authority» (typically for NTLM) or «4622: A security package has been loaded by the Local Security Authority» (typically for Kerberos) event is logged to indicate that a new package has been loaded along with the package name. The most common authentication packages are:
NTLM – NTLM-family Authentication
Kerberos – Kerberos authentication.
Negotiate – the Negotiate security package selects between Kerberos and NTLM protocols. Negotiate selects Kerberos unless it cannot be used by one of the systems involved in the authentication or the calling application did not provide sufficient information to use Kerberos.
Transited Services [Type = UnicodeString] [Kerberos-only]: the list of transmitted services. Transmitted services are populated if the logon was a result of a S4U (Service For User) logon process. S4U is a Microsoft extension to the Kerberos Protocol to allow an application service to obtain a Kerberos service ticket on behalf of a user – most commonly done by a front-end website to access an internal resource on behalf of a user. For more information about S4U, see https://msdn.microsoft.com/library/cc246072.aspx
Package Name (NTLM only) [Type = UnicodeString]: The name of the LAN Manager sub-package (NTLM-family protocol name) that was used during logon. Possible values are:
Only populated if «Authentication Package» = «NTLM».
Key Length [Type = UInt32]: the length of NTLM Session Security key. Typically it has 128 bit or 56 bit length. This parameter is always 0 if «Authentication Package» = «Kerberos», because it is not applicable for Kerberos protocol. This field will also have «0» value if Kerberos was negotiated using Negotiate authentication package.
Security Monitoring Recommendations
For 4624(S): An account was successfully logged on.
| Type of monitoring required | Recommendation |
|---|---|
| High-value accounts: You might have high-value domain or local accounts for which you need to monitor each action. Examples of high-value accounts are database administrators, built-in local administrator account, domain administrators, service accounts, domain controller accounts and so on. | Monitor this event with the «New Logon\Security ID» that corresponds to the high-value account or accounts. |
| Anomalies or malicious actions: You might have specific requirements for detecting anomalies or monitoring potential malicious actions. For example, you might need to monitor for use of an account outside of working hours. | When you monitor for anomalies or malicious actions, use the «New Logon\Security ID» (with other information) to monitor how or when a particular account is being used. |
| Non-active accounts: You might have non-active, disabled, or guest accounts, or other accounts that should never be used. | Monitor this event with the «New Logon\Security ID» that corresponds to the accounts that should never be used. |
| Account whitelist: You might have a specific allow list of accounts that are the only ones allowed to perform actions corresponding to particular events. | If this event corresponds to a «allow list-only» action, review the «New Logon\Security ID» for accounts that are outside the allow list. |
| Accounts of different types: You might want to ensure that certain actions are performed only by certain account types, for example, local or domain account, machine or user account, vendor or employee account, and so on. | If this event corresponds to an action you want to monitor for certain account types, review the «New Logon\Security ID» to see whether the account type is as expected. |
| External accounts: You might be monitoring accounts from another domain, or «external» accounts that are not allowed to perform certain actions (represented by certain specific events). | Monitor this event for the «Subject\Account Domain» corresponding to accounts from another domain or «external» accounts. |
| Restricted-use computers or devices: You might have certain computers, machines, or devices on which certain people (accounts) should not typically perform any actions. | Monitor the target Computer: (or other target device) for actions performed by the «New Logon\Security ID» that you are concerned about. |
| Account naming conventions: Your organization might have specific naming conventions for account names. | Monitor «Subject\Account Name» for names that don’t comply with naming conventions. |
Because this event is typically triggered by the SYSTEM account, we recommend that you report it whenever «Subject\Security ID» is not SYSTEM.
If «Restricted Admin» mode must be used for logons by certain accounts, use this event to monitor logons by «New Logon\Security ID» in relation to «Logon Type«=10 and «Restricted Admin Mode«=»Yes». If «Restricted Admin Mode«=»No» for these accounts, trigger an alert.
If you need to monitor all logon events for accounts with administrator privileges, monitor this event with «Elevated Token«=»Yes».
If you need to monitor all logon events for managed service accounts and group managed service accounts, monitor for events with «Virtual Account«=»Yes».
To monitor for a mismatch between the logon type and the account that uses it (for example, if Logon Type 4-Batch or 5-Service is used by a member of a domain administrative group), monitor Logon Type in this event.
If your organization restricts logons in the following ways, you can use this event to monitor accordingly:
If the user account «New Logon\Security ID» should never be used to log on from the specific Computer:.
If New Logon\Security ID credentials should not be used from Workstation Name or Source Network Address.
If a specific account, such as a service account, should only be used from your internal IP address list (or some other list of IP addresses). In this case, you can monitor for Network Information\Source Network Address and compare the network address with your list of IP addresses.
If a particular version of NTLM is always used in your organization. In this case, you can use this event to monitor Package Name (NTLM only), for example, to find events where Package Name (NTLM only) does not equal NTLM V2.
If NTLM is not used in your organization, or should not be used by a specific account (New Logon\Security ID). In this case, monitor for all events where Authentication Package is NTLM.
If the Authentication Package is NTLM. In this case, monitor for Key Length not equal to 128, because all Windows operating systems starting with Windows 2000 support 128-bit Key Length.
If you monitor for potentially malicious software, or software that is not authorized to request logon actions, monitor this event for Process Name.
If you have a trusted logon processes list, monitor for a Logon Process that is not from the list.