- Linux audit files to see who made changes to a file
- Task: install audit package
- How do I set a watch on a file for auditing?
- File System audit rules
- syscall audit rule
- File system audit rule
- syscall audit rule using pid
- How do I find out who changed or accessed a file /etc/passwd?
- Other useful examples
- How To Monitor File Changes Using fswatch In Linux
- Types of monitoring
- Features
- Monitor File Changes Using fswatch In Linux
- fswatch usage
- Get Last Modified Date of File in Linux
- 7 Answers 7
Linux audit files to see who made changes to a file
This is one of the key questions many new sys admin ask:
How do I audit file events such as read / write etc? How can I use audit to see who changed a file in Linux?
The answer is to use 2.6 kernel’s audit system. Modern Linux kernel (2.6.x) comes with auditd daemon. It’s responsible for writing audit records to the disk. During startup, the rules in /etc/audit.rules are read by this daemon. You can open /etc/audit.rules file and make changes such as setup audit file log location and other option. The default file is good enough to get started with auditd.
- No ads and tracking
- In-depth guides for developers and sysadmins at Opensourceflare✨
- Join my Patreon to support independent content creators and start reading latest guides:
- How to set up Redis sentinel cluster on Ubuntu or Debian Linux
- How To Set Up SSH Keys With YubiKey as two-factor authentication (U2F/FIDO2)
- How to set up Mariadb Galera cluster on Ubuntu or Debian Linux
- A podman tutorial for beginners – part I (run Linux containers without Docker and in daemonless mode)
- How to protect Linux against rogue USB devices using USBGuard
Join Patreon ➔
In order to use audit facility you need to use following utilities
=> auditctl – a command to assist controlling the kernel’s audit system. You can get status, and add or delete rules into kernel audit system. Setting a watch on a file is accomplished using this command:
=> ausearch – a command that can query the audit daemon logs based for events based on different search criteria.
=> aureport – a tool that produces summary reports of the audit system logs.
Note that following all instructions are tested on CentOS 4.x and Fedora Core and RHEL 4/5 Linux.
Task: install audit package
The audit package contains the user space utilities for storing and searching the audit records generate by the audit subsystem in the Linux 2.6 kernel. CentOS/Red Hat and Fedora core includes audit rpm package. Use yum or up2date command to install package
# yum install audit
or
# up2date install audit
Auto start auditd service on boot
# ntsysv
OR
# chkconfig auditd on
Now start service:
# /etc/init.d/auditd start
How do I set a watch on a file for auditing?
Let us say you would like to audit a /etc/passwd file. You need to type command as follows:
# auditctl -w /etc/passwd -p war -k password-file
- -w /etc/passwd : Insert a watch for the file system object at given path i.e. watch file called /etc/passwd
- -p war : Set permissions filter for a file system watch. It can be r for read, w for write, x for execute, a for append.
- -k password-file : Set a filter key on a /etc/passwd file (watch). The password-file is a filterkey (string of text that can be up to 31 bytes long). It can uniquely identify the audit records produced by the watch. You need to use password-file string or phrase while searching audit logs.
In short you are monitoring (read as watching) a /etc/passwd file for anyone (including syscall) that may perform a write, append or read operation on a file.
Wait for some time or as a normal user run command as follows:
$ grep ‘something’ /etc/passwd
$ vi /etc/passwd
Following are more examples:
File System audit rules
Add a watch on “/etc/shadow” with the arbitrary filterkey “shadow-file” that generates records for “reads, writes, executes, and appends” on “shadow”
# auditctl -w /etc/shadow -k shadow-file -p rwxa
syscall audit rule
The next rule suppresses auditing for mount syscall exits
# auditctl -a exit,never -S mount
File system audit rule
Add a watch “tmp” with a NULL filterkey that generates records “executes” on “/tmp” (good for a webserver)
# auditctl -w /tmp -p e -k webserver-watch-tmp
syscall audit rule using pid
To see all syscalls made by a program called sshd (pid – 1005):
# auditctl -a entry,always -S all -F pid=1005
How do I find out who changed or accessed a file /etc/passwd?
Use ausearch command as follows:
# ausearch -f /etc/passwd
OR
# ausearch -f /etc/passwd | less
OR
# ausearch -f /etc/passwd -i | less
Where,
- -f /etc/passwd : Only search for this file
- -i : Interpret numeric entities into text. For example, uid is converted to account name.
Let us try to understand output
- audit(03/16/2007 14:52:59.985:55) : Audit log time
- uid=lighttpd gid=lighttpd : User ids in numerical format. By passing -i option to command you can convert most of numeric data to human readable format. In our example user is lighttpd used grep command to open a file
- exe=”/bin/grep” : Command grep used to access /etc/passwd file
- perm_mask=read : File was open for read operation
So from log files you can clearly see who read file using grep or made changes to a file using vi/vim text editor. Log provides tons of other information. You need to read man pages and documentation to understand raw log format.
Other useful examples
Search for events with date and time stamps. if the date is omitted, today is assumed. If the time is omitted, now is assumed. Use 24 hour clock time rather than AM or PM to specify time. An example date is 10/24/05. An example of time is 18:00:00.
# ausearch -ts today -k password-file
# ausearch -ts 3/12/07 -k password-file
Search for an event matching the given executable name using -x option. For example find out who has accessed /etc/passwd using rm command:
# ausearch -ts today -k password-file -x rm
# ausearch -ts 3/12/07 -k password-file -x rm
Search for an event with the given user name (UID). For example find out if user vivek (uid 506) try to open /etc/passwd:
# ausearch -ts today -k password-file -x rm -ui 506
# ausearch -k password-file -ui 506
Источник
How To Monitor File Changes Using fswatch In Linux
Fswatch is a free, open source multi-platform file change monitor utility that notifies us when the contents of the specified files or directories are modified or changed. Using fswatch, we can easily monitor the changes being made in files and/or directories. It supports all operating systems, including GNU/Linux, *BSDs, Mac OS X, Solaris, and Microsoft Windows etc. In this brief guide, let me show you how to monitor file changes using fswatch in Unix-like operating systems.
Types of monitoring
fswatch implements the following types of monitors.
- A monitor based on the File System Events API of Apple OS X.
- A monitor based on kqueue, a notification interface introduced in FreeBSD 4.1.
- A monitor based on the File Events Notification API of the Solaris kernel and its derivatives.
- A monitor based on inotify, a Linux kernel subsystem that reports file system changes to applications.
- A monitor based on ReadDirectoryChangesW, a Microsoft Windows API that reports changes to a directory.
- A monitor which periodically stats the file system, saves file modification times in memory, and manually calculates file system changes.
Features
Concerning about the features, we can list the following:
- Cross-platform and open source utility.
- Support for many OS-specific APIs.
- Recursive directory monitoring.
- Path filtering using including and excluding regular expressions.
- Customizable record format.
- Support for periodic idle events.
- And many.
Monitor File Changes Using fswatch In Linux
Since the fswatch utility is not available in the default repositories of most Linux distributions, you need to manually compile and install the latest version from the source as described below.
Before compiling, you need to install Development tools in your Linux distribution. To install Development tools on various Linux distributions, refer the following guide.
Then, download the fswatch source file from here.
Extract the downloaded tarball:
Go to the project’s folder:
Finally, compile and install fswatch by running the following commands one by one.
Finally, run the following command to refresh the links and cache to the dynamic libraries:
If you don’t run the above command, you might get the following error in GNU/Linux systems.
fswatch usage
Usage of fswatch is no big deal. The typical syntax of fswatch is:
To test how fswatch works, open two Terminal windows (Let us call them Terminal 1 and Terminal 2).
In Terminal 1, run the fswatch command to monitor the $HOME directory.
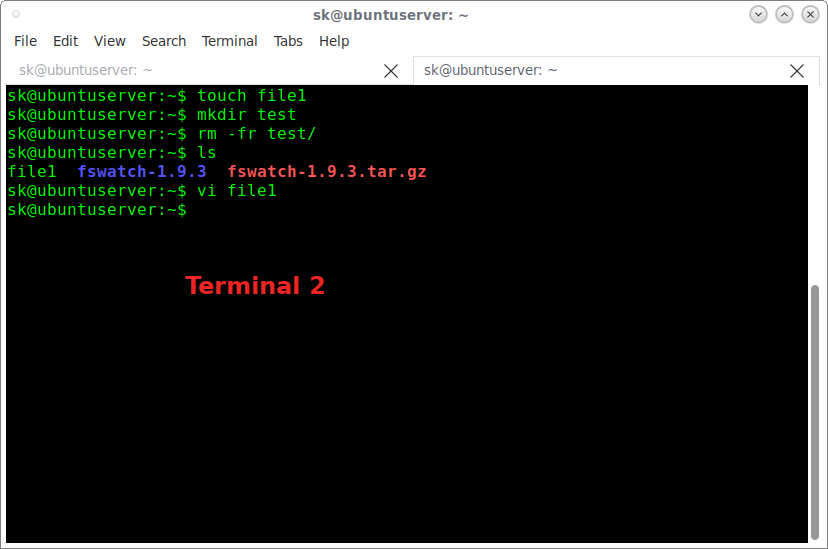
And, in the Terminal 2 do some operations such as creating files/folders, deleting files, modifying files etc.
Whatever you do in the terminal 2 will be notified on the Terminal 1. Have a look at the following screenshots.
Terminal 1 — fswatch command is running and the file changes are being monitored:
Monitor File Changes Using fswatch
Terminal 2 — Do some random changes in files/folders:
By default fswatch will choose the best monitor available on the current platform, in terms of performance and resource consumption. In Linux, the default monitor is inotify.
To list the available monitors in the current platform (i.e Linux in our case), run:
Sample output:
To monitor a specific file or directory with a particular monitor option, run:
By default, fswatch will keep monitoring the file changes until you manually stop it by invoking CTRL+C keys.
You can also exit fswatch after the first set of events is received by specifying the option -1 as shown in the following command:
This command will exit just after the first set of events is received.
fswatch will monitor changes in all files/folders in the specified path. If you want to watch the changes made in the directories only, use -d option.
Of course, there are more options. Refer the man pages or the project’s documentation page for detailed instructions.
Источник
Get Last Modified Date of File in Linux
I’m new to Linux. I’m using the command-line. I’m trying to view the last modified date of a file. How do I do that in Linux from the Command Line?
7 Answers 7
As mentioned by @edvinas.me, stat tells you various information about the file including the last modified date.
At first, I was confused with Modify and Change, just to clarify, stat output lists:
- Access shows the time of last data access (e.g. read).
- Modify shows the time of last data modification.
- Change shows the time the file status last changed.
Use stat command for that:
Another way that is more flexible is using date -r . From man date :
This has the advantage of allowing you to specify the output format, e.g.
ls -l should do the work.
Building off of @Adam Taylor ‘s comment in @phoops ‘s answer and @Sparhawk ‘s answer.
To specifically just get the date (using October 3, 2019 for examples because it was my last birthday, here’s my venmo if you feel led to bless me financially: @levi_uzodike)
- stat -c %y file | cut -d’ ‘ -f1 will give you 2019-10-03
- date +%F -r file will also give you 2019-10-03
- date +%D -r file will give you 10/03/19
- date +%x -r file will probably give either 10/03/2019 , or 10/03/19 if you’re in the U.S. and either 03/10/2019 , or 03/10/19 if you’re in the U.K., just to name a couple examples (of course there are more possibilities)
These date format options are, to my understanding, combinations of other format options. Here are some explanations from the man page:
%b locale’s abbreviated month name (e.g., Jan)
%B locale’s full month name (e.g., January)
.
%d day of month (e.g, 01)
%D date; same as %m/%d/%y
%e day of month, space padded; same as %_d
%F full date; same as %Y-%m-%d
.
%m month (01..12)
.
%x locale’s date representation (e.g., 12/31/99)
.
%y last two digits of year (00..99)
%Y year
.
By default, date pads numeric fields with zeroes.
The following optional flags may follow `%’:
— (hyphen) do not pad the field
_ (underscore) pad with spaces
0 (zero) pad with zeros
^ use upper case if possible
# use opposite case if possible
N.B.: These flags don’t work on the «combo formats» like %F , %D and %x . They are for the «singular field formats«.
Apparently this last flag (#) does not work as I’d expect (e.g., if date +%b gives Oct , date +%#b gives OCT as opposed to oCT ) I guess this would be useless, but I’d think a lower case option would be more useful. date +%#p does turn date +%p which might give PM or AM into pm or am , respectively. So I guess it’s not a ‘per-character’ case switch but sets the case of all the characters in the string to the opposite case of the majority of the characters? Also date +%P gives pm or am , but neither date +%^P nor date +%#P change its output. My guess for this case is that %P is just an alias for %#p , and it seems that whenever you add more than one flag, the behavior is undefined/unpredictable ( e.g., date +%0-e gives the same as date +%-e : 3 and date +%-0e gives the same as date +%0e : 03 , which makes you think that only the flag next to the letter works or that it goes left to right, but both date +%#^p and date +%^#p give pm or am , [depending on the time of course] ) unless there’s some hidden order of operations? Sorry for digressing.
Also, if you run the command locale -k LC_TIME | grep ^d_fmt , you can see the combo for the specific locale of your system (e.g., d_fmt=»%m/%d/%Y» ).
And you can make your own combo. For example,
- date +%^b\ %-e\ %Y -r file will give you OCT 3 2019
Источник