- SMS Spoofing with Kali Linux
- SMS Spoofing with Kali Linux
- What Is SMS Spoofing?
- SMS Spoofing Tutorial
- Sms spoofing with kali linux
- Burpsuite
- Mitmproxy
- Wireshark
- sslstrip
- No SMS Spoofing attack vector in Kali Linux! [closed]
- 3 Answers 3
- The Hacks of Mr. Robot : How to Send a Spoofed SMS Text Message
- The Spoofed Text Message in Episode 5
- Step 1: Fire Up BackTrack & Start Social Engineering Toolkit (SET)
- Step 2: Set Up a Spoofed Text Message
- Step 3: Craft the Text Message
- Step 4: Send the Message!
- Kali Linux — Sniffing & Spoofing
- Burpsuite
- mitmproxy
- Wireshark
- sslstrip
SMS Spoofing with Kali Linux
SMS Spoofing with Kali Linux
What Is SMS Spoofing?
Small communication service (SMS) is actually on cellphones, I, A person along with everybody making use of TEXT MESSAGE for your communication. TEXT MESSAGE spoofing ways to a collection that this communication seems to come from simply by replacing this coming initially from cell range (Sender ID) with alphanumeric text/ an additional range. (Wikipedia).
I most certainly will examine the vast majority of theoretical features below just like the best way to perform TEXT MESSAGE spoofing? Exactly how TEXT MESSAGE spoofing work? So a lot of problems.
SMS Spoofing Tutorial
The newest Kali-Linux (BT6) is included with many moves forward and increasing capabilities and one involving it is an incredible element is actually it is SMS spoofing system. Consequently, nowadays most of us can have fun with this particular element and pay attention to precisely how very easily we can spoof SMS. This can be a wonderful and enhanced element containing manufactured many safety measures specialists feel. Any person can certainly spoof text message through several volumes and there’s no possibility to possibly be captured. This particular element is found in your ESTABLISHED.
Start the SET toolkit. You will see the following welcome screen:
Next select option 7: SMS spoofing attacks
Then select the option no 1: Perform SMS spoofing attack
After that again select option no 1: SMS Attack single phone number
Now enter the victim’s Phone-number with its country code
Now select a template or use predefined templates
I am selecting a fake police SMS option 19
Now it’s almost done, from here you can choose the predefined android emulator or use your SMS accounts. Thus, either you can start a war or stop it by sending SMS from fake locations.
Источник
Sms spoofing with kali linux
Основная концепция инструментов для снифинга так же проста, как перехват данных. И Kali Linux имеет некоторые известные инструменты для этого. В этой статье вы узнаете об инструментах для снифинга и спуфинга, которые доступны в Kali Linux.
Burpsuite
Burpsuite может использоваться в качестве инструмента для снифигна между браузером и веб-сервером, для поиска параметров, используемых веб-приложением.
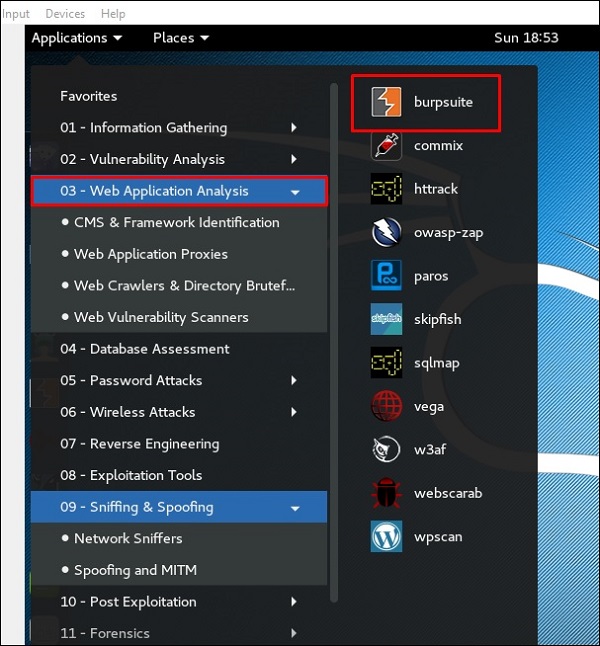
Чтобы открыть Burpsuite, перейдите в Applications → Web Application Analysis → burpsuite.
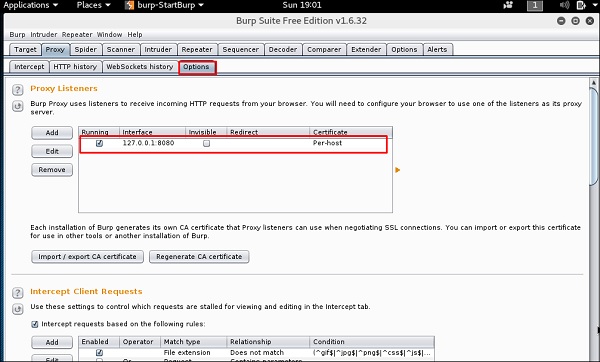
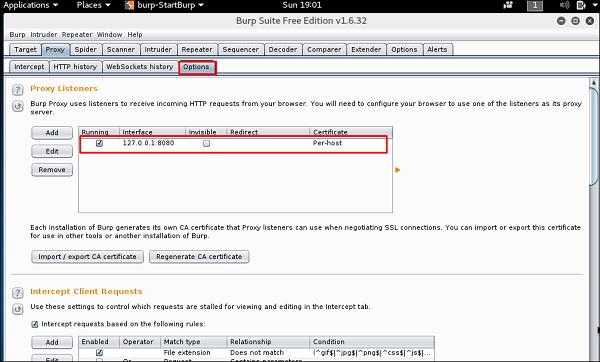
Чтобы настроить снифинг, мы настраиваем burpsuite для работы в качестве прокси-сервера. Для этого перейдите в раздел Options, установите чекбокс, как показано на следующем скриншоте.
В этом случае IP-адрес прокси-сервера будет 127.0.0.1 с портом 8080.
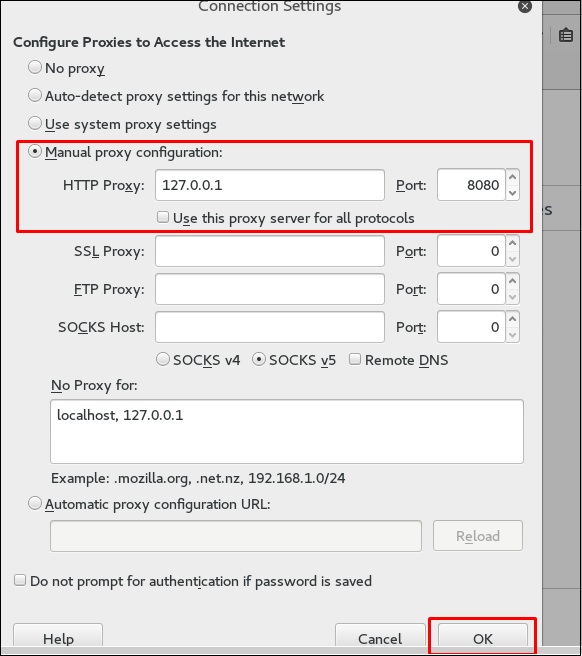
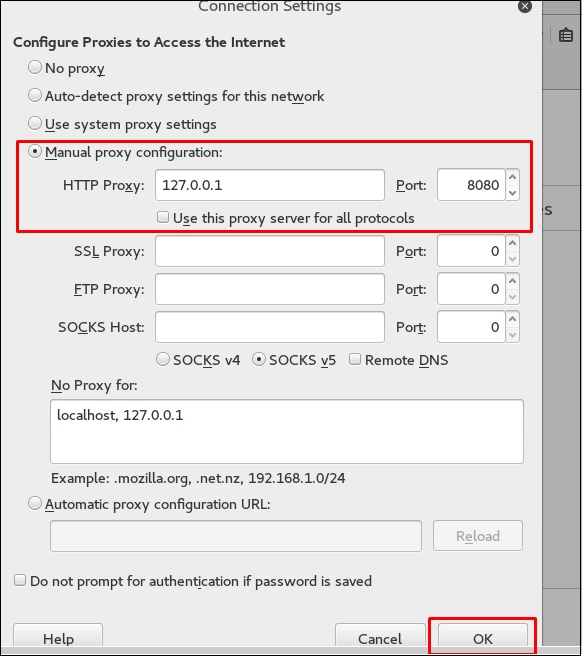
Затем настройте прокси-сервер в браузере, который и есть наш IP-адрес машины с burpsuite и порт, который был указан выше.
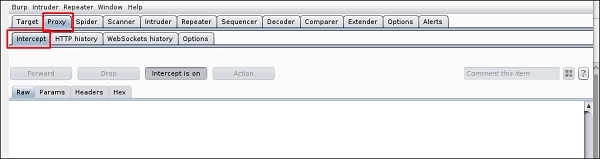
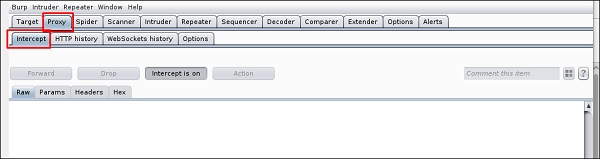
Чтобы начать перехват, перейдите в раздел Proxy → Intercept → нажмите “Intercept is on”.
Продолжайте пользоваться веб-страницей (сайтом) на которой вы хотите найти параметр для проверки на наличие уязвимостей.
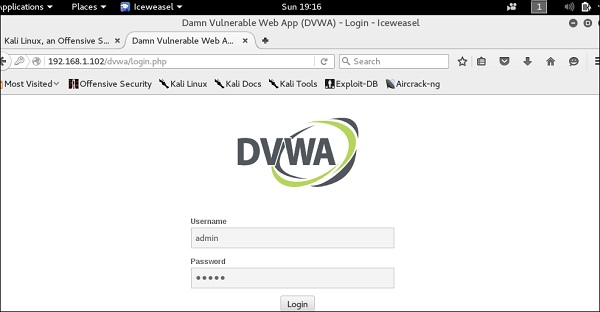
В данном случае это хост с metasploit’ом с IP 192.168.1.102
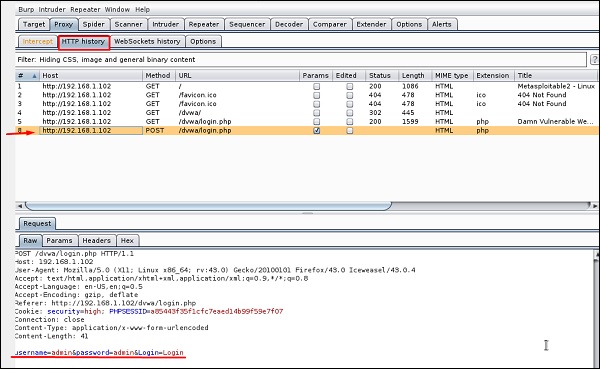
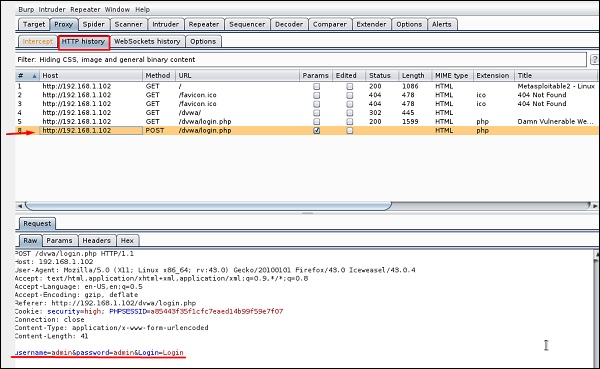
Перейдите в раздел «HTTP History». На следующем снимке экрана строка (отмеченная красной стрелкой) показывает последний запрос. В закладке Raw (исходный код) видны скрытые параметры: идентификатор сеанса, имя пользователя и пароль (подчеркнуты красным цветом).
Mitmproxy
mitmproxy с поддерживает SSL атаку MITM (человек-в-середине) с помощью прокси-сервера http. Утилита предоставляет собой консольный интерфейс, позволяющий сканировать потоки трафика и редактировать их на лету.
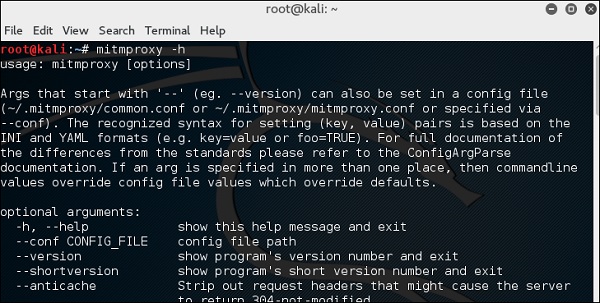
Для запуска, запустите терминал и напишите
Для получения доступных команд напишите
Для запуска MITM-прокси, напишите
И на порту 80 у нас будет слушать наш прокси.
Wireshark
Wireshark является одним из лучших анализаторов пакетов данных. Он анализирует пакеты на уровне кадра. Вы можете получить дополнительную информацию о Wireshark на официальном сайте: https://www.wireshark.org/.
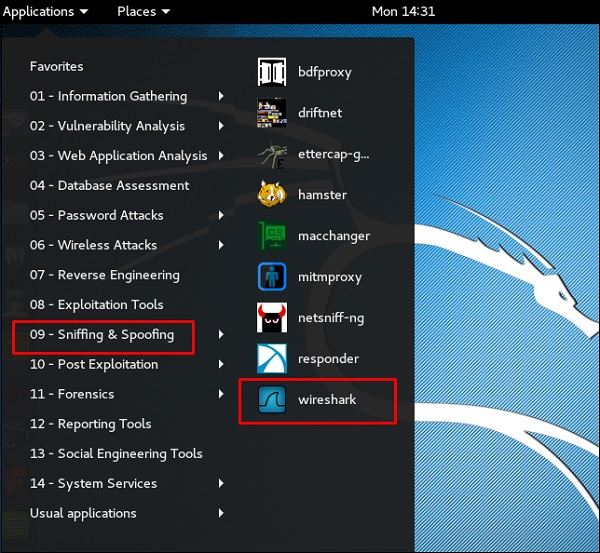
В Kali Linux она находится в Applications → Sniffing & Spoofing → wireshark.
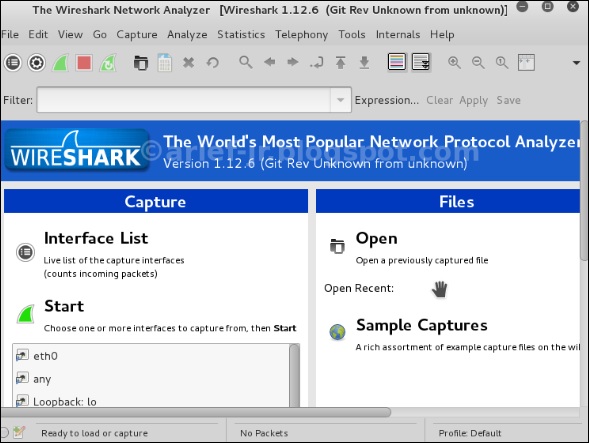
После запуска wireshark, перед нами появляется GUI.
Жмем “Start” и начинается захват пакетов на интерфейсе (показано ниже на скриншоте)
sslstrip
sslstrip это инструмент для MITM атаки это заставляет браузер жертвы общаться plain текстом по HTTP, и прокси изменяет содержимое, которое получено с сервера HTTPS.
https://адрес_сайта подменяется на http://адрес_сайта
Для открытия, перейдем в Applications → 09-Sniffing & Spoofing → Spoofing and MITM → sslstrip.
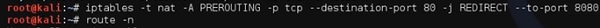
Настроим заворачивание трафика так, чтобы переслать все соединения с порта 80 на 8080.
Затем запустим sslstrip на том порту, который нам необходим (8080)
Источник
No SMS Spoofing attack vector in Kali Linux! [closed]
Want to improve this question? Update the question so it’s on-topic for Information Security Stack Exchange.
Closed 6 years ago .
I just realized that there is no SMS spoofing attack vector included in the latest version of Kali Linux. Is there a work around?
3 Answers 3
They took it out. You will need to find an old version of the SET kit or an older version of KALI. However the SMS spoofing will fail unless you can find a SMS gateway to use and most will cost money.
I suggest finding an SMS messaging API that allows you to change the Sender ID. Some of the more popular, well-known SMS messaging APIs such as Twilio do not allow you to change the Sender ID to a random value, for it has to be a valid phone number that you have bought through the Twilio API service. When you do find an API service that allows customers to choose the Sender ID, check out their terms of service just to check if spoofing the sender ID is a breach of contract or not.
As others suggest, you could use SEToolkit, however, I am not sure if the most recent version supports the SMS spoofing attack vector. Regardless, you will still need an SMS gateway, so I would suggest finding an SMS messaging API that allows you to change the Sender ID which will probably be quite hard.
Источник
The Hacks of Mr. Robot : How to Send a Spoofed SMS Text Message
Welcome back, my rookie hackers!
As most of you know, Mr. Robot is probably the best hacker TV show ever! This is a great show about a cyber security engineer who is being enticed to hack the very corporation he’s being paid to protect. This show is so good, I began a series to demonstrate how to do the hacks he uses in the show.
The Spoofed Text Message in Episode 5
In episode 5, when Elliot is able to social engineer his way into the Steel Mountain’s state of the art, «impenetrable» storage facility, a manager gets suspicious and begins to escort him out of the building before he can implant the Raspberry Pi (which we made in the last guide).
He intends to place the RP inside the network to manipulate the HVAC system to raise the temperature in the storage facility and destroy the tapes that contain the records of 70% of the world’s consumer debt, including student loans. At the very moment that she is about to escort him to the elevator and out of the facility, she receives a text message from her husband that is urgent and distracts here. The text message did not actually come from her husband, but rather from one of Elliot’s f/society comrades.
In this tutorial, I will show you how Elliot’s comrades at f/society were able to send the Steel Mountain manager an urgent, spoofed text message that appeared to come from her husband indicating that he was at the hospital and had a serious health issue.
On the show, Elliot’s f/society comrades use Kali to send the spoofed SMS, but this feature has been discontinued in recent versions of Kali. Luckily, though, it is still in BackTrack, so for this tutorial, we will be reverting to our trusty BackTrack installation (one more example that the newest is not always the best).
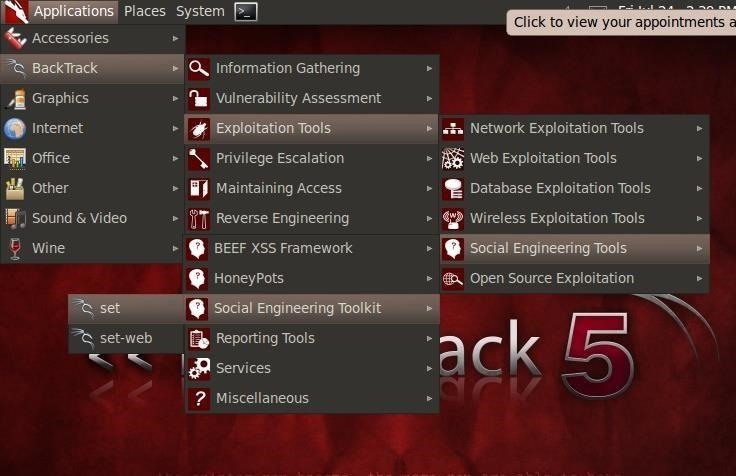
Step 1: Fire Up BackTrack & Start Social Engineering Toolkit (SET)
Let’s begin by firing up Backtrack 5 and then navigating to Applications -> Exploitation Tools -> Social Engineering Tools -> Social Engineering Toolkit (SET), then select «set» as I have done in the screenshot below.
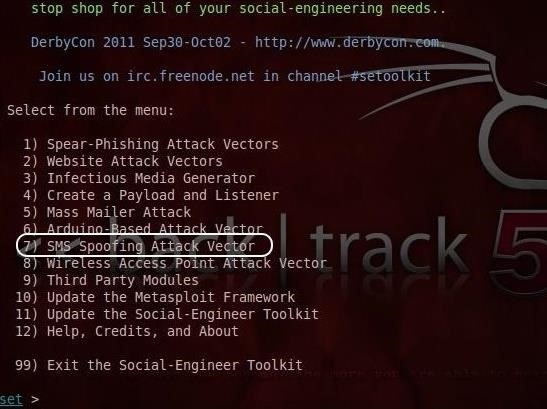
This will start the SET opening screen as seen below. SET is capable of numerous social engineering attacks. We have previously used SET to spear phish in BackTrack, but the one we want this time is «SMS Spoofing Attack Vector.» To begin this attack, Select #7.
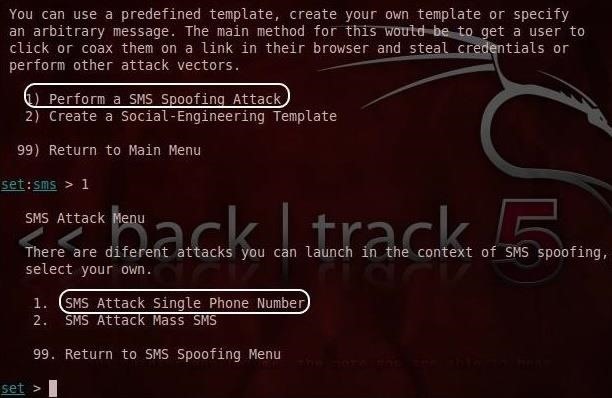
In the following screen we are asked whether we want «Perform a SMS Spoofing Attack» or «Create a Social Engineering Template.» Select #1. Once you have made that selection, you will be queried whether you want to spoof a single number or a mass attack. Select #1 for a single number.
Step 2: Set Up a Spoofed Text Message
Here, I want to send a spoofed text message from Mary (my best friend’s girlfriend) to John (my best friend) where she breaks up with him. This should rattle him a bit and give me a few chuckles as he is madly in love with her.
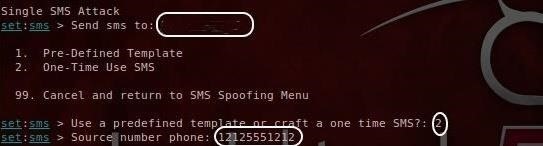
First, enter his phone number where it asks you «Send sms to.» Then select #2 to craft a One-Time Use SMS. Finally, enter her phone number. Make certain both numbers are preceded by the «+».
Step 3: Craft the Text Message
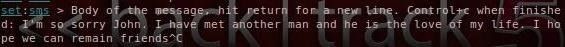
In our final step, we need to type the message we want sent to John from his girlfriend, Mary.
«I’m so sorry John. I have met another man and he is the love of my life. I hope we can remain friends»
When you are finished typing, exit by hitting Control + C.
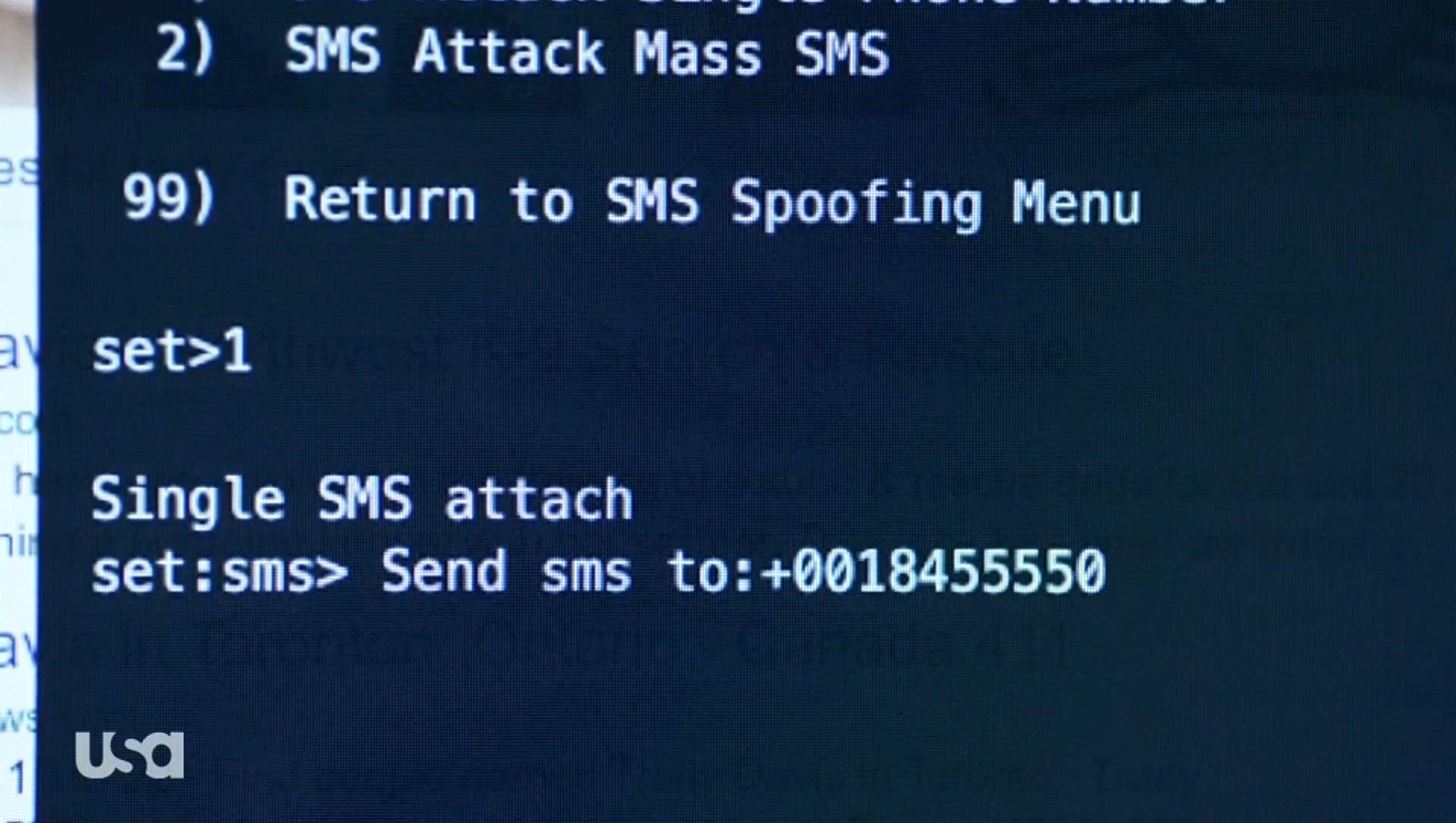
Step 4: Send the Message!
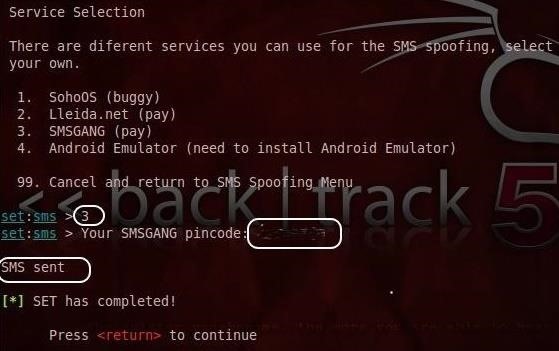
This will bring you to the final screen. In this screen, we will need to select the intermediary for the spoofed SMS message. You have four options here. The first is free, and as they say, it is buggy (when I ran it, SET crashed). Then, there are two for-pay options and, finally, the Android emulator.
I chose the third option, SMSGANG. They charge 3 euros for 5 messages, or about $0.65 in U.S. dollars per message. When you pay (they accept credit cards and PayPal) they send you a PIN code. After selecting #3, it will ask you for a «pincode.» Enter the one SMSGANG emailed you and then your text message is sent!
Keep coming back, my rookie hackers, as we continue to show you all the hacks of Mr. Robot!
Want to start making money as a white hat hacker? Jump-start your hacking career with our 2020 Premium Ethical Hacking Certification Training Bundle from the new Null Byte Shop and get over 60 hours of training from cybersecurity professionals.
Источник
Kali Linux — Sniffing & Spoofing
The basic concept of sniffing tools is as simple as wiretapping and Kali Linux has some popular tools for this purpose. In this chapter, we will learn about the sniffing and spoofing tools available in Kali.
Burpsuite
Burpsuite can be used as a sniffing tool between your browser and the webservers to find the parameters that the web application uses.
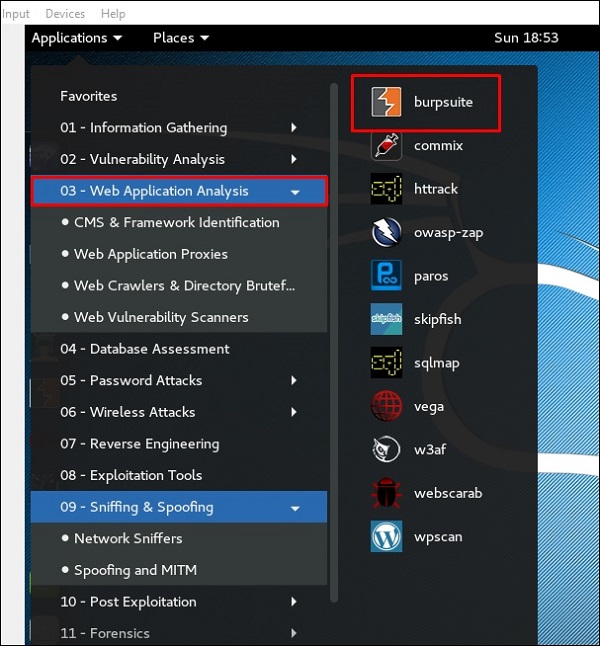
To open Burpsuite, go to Applications → Web Application Analysis → burpsuite.
To make the setup of sniffing, we configure burpsuite to behave as a proxy. To do this, go to Options as shown in the following screenshot. Check the box as shown.
In this case, the proxy IP will be 127.0.0.1 with port 8080.
Then configure the browser proxy which is the IP of burpsuite machine and the port.
To start interception, go to Proxy → Intercept → click “Intercept is on”.
Continue to navigate on the webpage that you want to find the parameter to test for vulnerabilities.
In this case, it is metasploitable machine with IP 192.168.1.102
Go to “HTTP History”. In the following screenshot, the line marked in red arrow shows the last request. In Raw and the hidden parameter such as the Session ID and other parameter such as user name and password has been underlined in red.
mitmproxy
mitmproxy is an SSL-capable man-in-the-middle HTTP proxy. It provides a console interface that allows traffic flows to be inspected and edited on the fly.
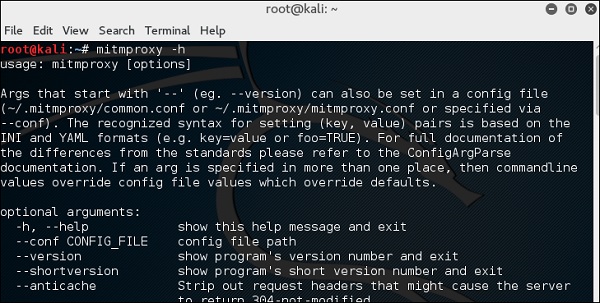
To open it, go to the terminal and type “mitmproxy -parameter” and for getting help on commands, type “mitmproxy –h”.
To start the mitmproxy, type “mitmproxy –p portnumber”. In this case, it is “mitmproxy –p 80”.
Wireshark
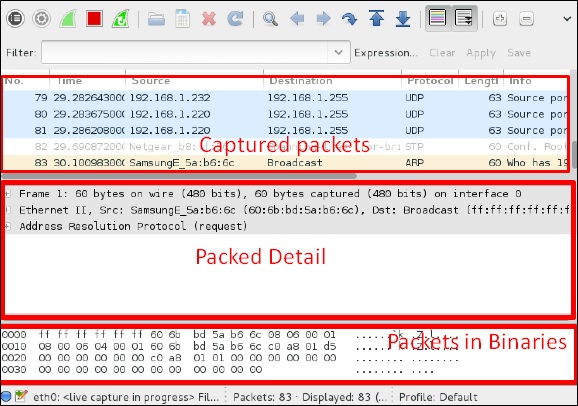
Wireshark is one of the best data packet analyzers. It analyzes deeply the packets in frame level. You can get more information on Wireshark from their official webpage: https://www.wireshark.org/. In Kali, it is found using the following path — Applications → Sniffing & Spoofing → wireshark.
Once you click wireshark, the following GUI opens up.
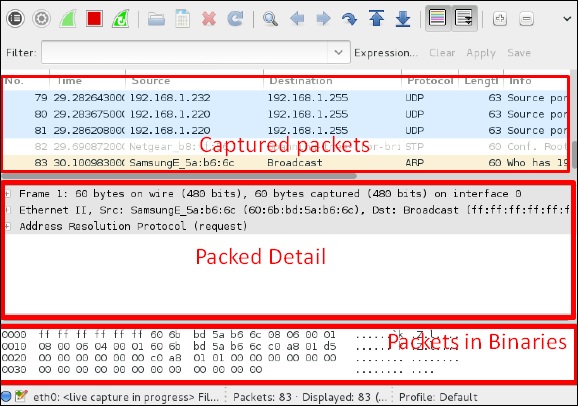
Click “Start” and the packet capturing will start as shown in the following screenshot.
sslstrip
sslstrip is a MITM attack that forces a victim’s browser to communicate in plain-text over HTTP, and the proxies modifies the content from an HTTPS server. To do this, sslstrip is «stripping» https:// URLs and turning them into http:// URLs.
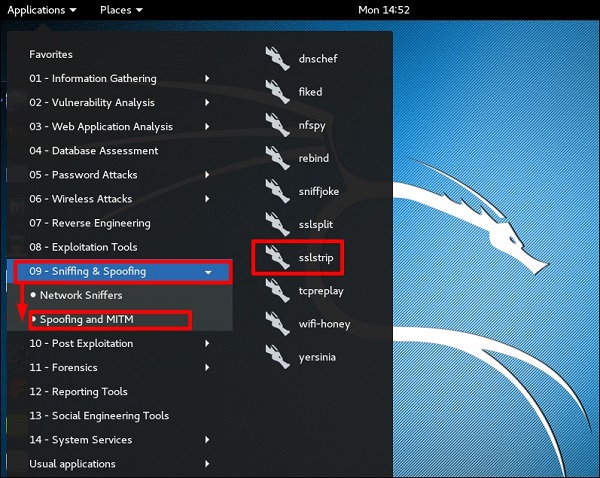
To open it, go to Applications → 09-Sniffing & Spoofing → Spoofing and MITM → sslstrip.
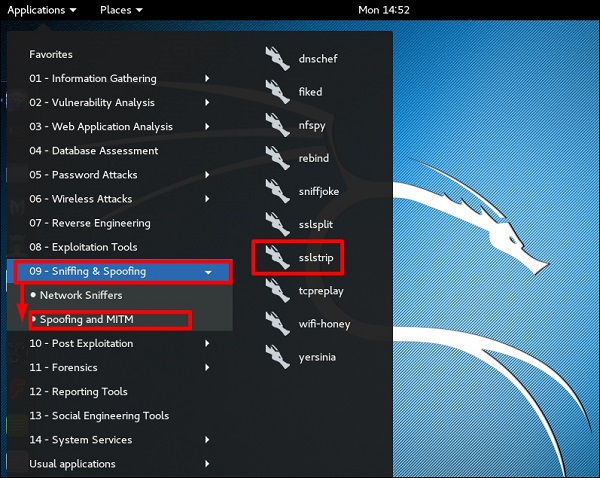
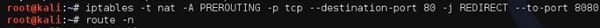
To set it up, write to forward all the 80 port communication to 8080.
Then, start the sslstrip command for the port needed.
Источник