- Question: Q: ssh «Permission denied (publickey,keyboard-interactive)»
- All replies
- How to Fix SSH Failed Permission Denied (publickey,gssapi-keyex,gssapi-with-mic)
- What is Causing SSH Permission Denied (publickey,gssapi-keyex,gssapi-with-mic)?
- How to fix SSH Permission denied
- Solution 1: Enable Password Authentication
- Solution 2: Change File System Permissions
- Permission denied (publickey) — mac
- 2 Answers 2
- Permissions error when connecting to EC2 via SSH on Mac OSx
- 16 Answers 16
- ssh : Permission denied (publickey,gssapi-with-mic)
- 26 Answers 26
Question: Q: ssh «Permission denied (publickey,keyboard-interactive)»
Trying to ssh and I get the following message:
Permission denied (publickey,keyboard-interactive)
The first time I ran ssh it added the (RSA) to the list of know hosts. But then drop’d to the command line with the above message. Any ideas, why?
iMac, Mac OS X (10.4.10)
Posted on Sep 19, 2007 5:57 PM
All replies
Loading page content
Page content loaded
Sep 19, 2007 6:48 PM
Then you will not be prompted for a password.
Sep 20, 2007 7:08 AM
Sep 21, 2007 7:59 PM
.ssh/authorized_keys
or
cat /Volumes/NameOfMemStick/id_dsa.pub >>
.ssh/authorized_keys2
(assuming that you physically delivered it to the other computer via memstick) depending on what kind of key pair you created.
Sep 21, 2007 11:49 PM
I only use DSA keys to login to the servers I administrate. The command to generate a public and private key is
ssh-keygen -b 1024 -t dsa
you will then be prompted where to save the keys press enter to save them in the default location.
Generating public/private dsa key pair.
Enter file in which to save the key (/Users/user/.ssh/id_dsa):
The keys will then be saved
then you will be prompted to enter a passphrase. Dont enter a passphrase just press enter twice.
Enter passphrase (empty for no passphrase):
The terminal will now display the key fingerprint.
Now in your .ssh directory you need to copy id_dsa.pub to your user account on the server and add it to the file authorized_keys2
they way I do this is to use the scp command
scp /Users/user/.ssh/id_dsa.pub serveraddress:
I then ssh into the server and issue this command
cat id_dsa.pub >> /Users/user/.ssh/authorized_keys2
This is useful as it will add the key to the end of the file authorized_keys2. so if you add any subsequent keys you will not overwrite the previous key. This is useful if you login to servers from different computers.
Once you have your public key working you can disabled password authentication and use public key authentication only. This makes your server very secure.
Источник
How to Fix SSH Failed Permission Denied (publickey,gssapi-keyex,gssapi-with-mic)
Home » SysAdmin » How to Fix SSH Failed Permission Denied (publickey,gssapi-keyex,gssapi-with-mic)
The SSH Permission denied error appears after permission-related settings are modified on the SSH server. Usual scenarios include a new package installation or the creation of new users.
In this tutorial, you will learn how to troubleshoot the SSH Permission denied error and reconnect to your SSH server.
- SSH client on the local machine and SSH server on the remote system
- A user account to access the remote server (for password-based login)
- A user account with sudo or root privileges
What is Causing SSH Permission Denied (publickey,gssapi-keyex,gssapi-with-mic)?
The SSH Permission denied error appears when trying to SSH into a server:
Following the Permission denied statement, the bracket contains the attempted authentication methods that failed at the initiation of the connection. The error suggests that the public key is the issue, which is misleading.
One reason for the error may be sshd_config , the file that contains SSH server configuration. The other possibility is that the authorized_keys file has insufficient permissions. This file contains the list of public keys for the clients allowed to SSH into the server. Consequently, the system’s inability to read from the file results in the Permission denied error.
How to fix SSH Permission denied
Both solutions contain steps you need to perform on the server-side. Start by opening the terminal on your server and proceed with one of the solutions below.
Solution 1: Enable Password Authentication
If you want to use a password to access the SSH server, a solution for fixing the Permission denied error is to enable password login in the sshd_config file.
To do this, open the file in a text editor. This example uses the nano editor:
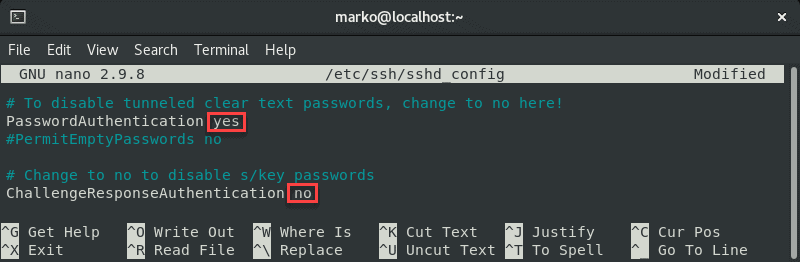
In the file, find the PasswordAuthentication line and make sure it ends with yes .
Find the ChallengeResponseAuthentication option and disable it by adding no .
If lines are commented out, remove the hash sign # to uncomment them.
Save the file and exit.
Restart the SSH service by typing the following command:
Solution 2: Change File System Permissions
Using the password-based login as the SSH authentication method is not recommended due to security concerns. Therefore, the following solution may be preferable since it troubleshoots the public key authentication method.
First, open the sshd_config file using a text editor:
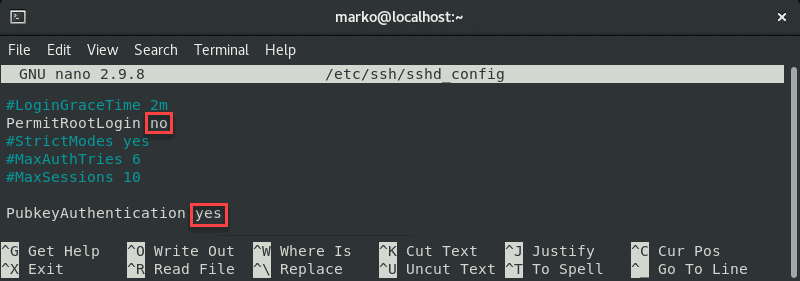
In the file, make sure the following options are set as follows:
Note: The steps above are considered best security practices. If you need to use root login, set the relevant line to yes .
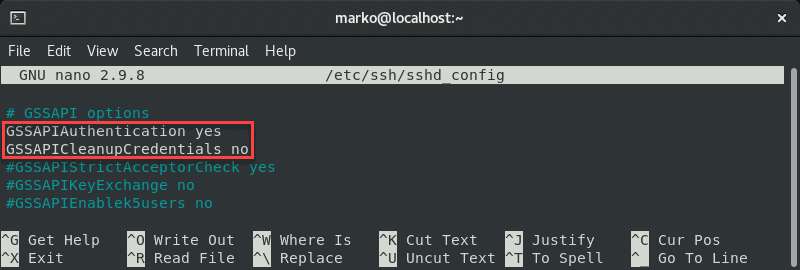
Comment out the GSSAPI-related options by adding the hash sign at the beginning of the line:
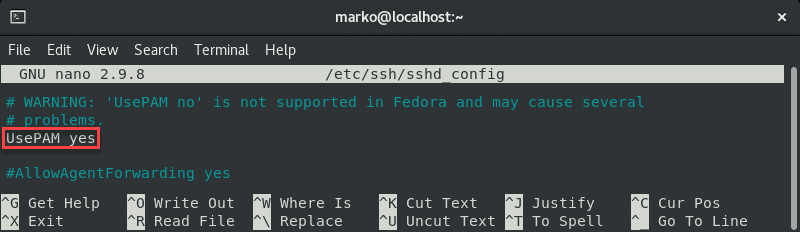
Also, make sure the UsePAM line is set to yes :
Save the file and restart the sshd service:
Now navigate to your home folder and check the permissions:
If your owner permissions are not set to read, write, and execute ( drwx—— ), use the chmod command to change them:
Now go to the .ssh folder and recheck the permissions:
This directory should also have read, write, and execute permissions for the file owner. To enforce them, use chmod again:
The .ssh folder contains the authorized_keys file. Check its permissions with:
The file owner should have read and write permissions. To set them, use:
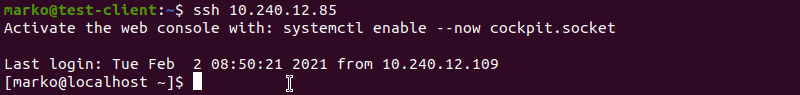
Now try logging in with the key pair again. The output below shows a successful login attempt.
Note: For more information about Linux file permission, read the Linux File Permissions Tutorial.
This tutorial covered the steps necessary to troubleshoot the SSH Permission denied (publickey,gssapi-keyex,gssapi-with-mic) error. By completing the steps in the guide, you should fix the error and successfully SSH into your server.
Источник
Permission denied (publickey) — mac
I can’t log into my droplet. This is another post I made about the issue that did not solve my problem, but explains some of what I have tried. https://stackoverflow.com/questions/52917470/permission-denied-publickey-digital-ocean/52972508?noredirect=1#comment92856534_52972508
What I just tried:
ssh-key gen . Naming the keys portfolio . Could this naming be a problem? The only keys that work on my machine are the keys with the default name id_rsa , but there cannot be more than one set with that name. There is a line in the debug that says Offering public key: RSA SHA256:blahblah /Users/ME/.ssh/id_rsa so it looks like it connecting to the wrong key. I have tried ssh -i
/.ssh/portfolio ME@139.xx.xx.xxx to connect to a specific private key called portfolio . Nope. Permission denied (publickey).
Log into server inside DO console. nano /.ssh/authorized_keys . Copy in my public key called portfolio. Got this here
Big fat Permission denied (publickey). Obviously logging in does not work either. Why? The keys match and are in place yet still do not find each other.
Further debugging: Using the digital ocean console, currently the only way I can access my droplet, I see that copy/paste does not work. Pasting in a public key results in a string of totally different characters than the real key. This even happens in nano.
2 Answers 2
I wanted to update how I solved this. The problem was that:
- The key was not making it to the server correctly. Or an incorrect version was making it.
- Once I got the correct keys placed, my local machine and the server were not finding the correct keys to match each other.
Solved 1. — ssh-copy-id -i
/.ssh/mykey root@MY-IP for trying to copy the public key did not work. I also tried pasting it directly into
/.ssh/authorized_keys in the Digital Ocean console since I was locked out locally, but many of the pasted characters were wrong. Something was screwey about the pasting function there and Digital Ocean staff didn’t know anything about that.
So to work locally I reset root PW on DO console then ssh myUser@123.456.789.10 on my local machine but with a password. Then in
/.ssh/authorized_keys I pasted in the public key and used a diff tool to make sure they were the same. This time there were.
Solved 2. — The keys still were not connecting. I could connect using only using -i flag (which means identity _file and connects the keys manually) ssh -i
/.ssh/mykey myUser@123.456.789.10 but I didn’t want to type type this every time so I make a
Then, going ssh myappp I am able to login. Not sure why all these things are occurring. I thought maybe since I did not name them properly since id_rsa works okay, but id_rsa2 does not so not sure what would work then, but these workarounds solved this issue.
Источник
Permissions error when connecting to EC2 via SSH on Mac OSx
I am new to EC2. I created my security credentials from this site:
It worked great, I rebooted and now when I try to connect I get a login/password prompt. (Which I never set up.) After several attempts I get this error:
Permission denied (publickey,gssapi-with-mic).
What am I doing wrong?
16 Answers 16
Two possibilities I can think of, although they are both mentioned in the link you referenced:
You’re not specifying the correct SSH keypair file or user name in the ssh command you’re using to log into the server:
ssh -i [full path to keypair file] root@[EC2 instance hostname or IP address]
You don’t have the correct permissions on the keypair file; you should use
chmod 600 Ssh permission denied mac os ��������
to ensure that only you can read or write the file.
Try using the -v option with ssh to get more info on where exactly it’s failing, and post back here if you»d like more help.
[Update]: OK, so this is what you should have seen if everything was set up properly:
Are you running the ssh command from the directory containing the ec2-keypair file ? If so, try specifying -i ./ec2-keypair just to eliminate path problems. Also check «ls -l [full path to ec2-keypair]» file and make sure the permissions are 600 (displayed as rw——-). If none of that works, I’d suspect the contents of the keypair file, so try recreating it using the steps in your link.
Источник
ssh : Permission denied (publickey,gssapi-with-mic)
i’m use centos 5.9. after installing gitlab by this link ssh not working. before install gitlab ssh correctly working. i’m using this server localy and other services such as elastix and apache,mysql installed on server.
appeare this error :
26 Answers 26
I had the same issue while using vagrant. So from my Mac I was trying to ssh to a vagrant box (CentOS 7)
Solved it by amending the /etc/ssh/sshd_config PasswordAuthentication yes then re-started the service using sudo systemctl restart sshd
Hope this helps.
Setting 700 to .ssh and 600 to authorized_keys solved the issue.
As everybody else has already said you need to edit /etc/ssh/sshd_config and change PasswordAuthentication no to PasswordAuthentication yes
I ran into this problem setting up a Vagrant box — so therefore it makes sense to script this and do it automatically in a shell provisioner:
sudo sed -i ‘s/PasswordAuthentication no/PasswordAuthentication yes/g’ /etc/ssh/sshd_config;
sudo systemctl restart sshd;
Setting PasswordAuthentication to yes, is not the best way to go , is not as secure as using private and public keys for authentication !
First make sure that that you have the fallowing permissions set, on the server side.
First check your home dir (SERVER SIDE)
if it is not like this, run
Now check .ssh folder
if it is not looking like this, run
now make sure that authorized_keys looks like this
After that go to /etc/ssh/sshd_config
For best security set
keep as yes for testing purposes
Comment those lines for GSSAPI
Make sure that is set to UsePAM yes
now restart sshd service
on the client side
generate new keys; setting a password is optional but is a good idea
copy pub key to your server
now your are good to go !
if everything works just fine
make a backup of your private key and then deny PasswordAuthentication
Restart you server
now anyone trying to ssh into your server, without your keys should get
keep script kids away from your business, and good luck
please make sure following changes should be uncommented, which I did and got succeed in centos7
thank you all and good luck
According to the line debug1: Authentications that can continue: publickey,gssapi-with-mic , ssh password authentication is disabled and apparently you are not using public key authentication.
Login to your server using console and open /etc/ssh/sshd_config file with an editor with root user and look for line PasswordAuthentication then set it’s value to yes and finally restart sshd service.
Tried a lot of things, it did not help.
It get access in a simple way:
Note that at the end of the ssh-add -L output must be not a path to the key, but your email.
Ans : Root access to vi /etc/ssh/sshd_config and change the PasswordAuthentication ( no ) to yes.
2 . Restart the sshd services
root> systemctl restart sshd.service
- Logon into local id via putty without key.
Nobody has mention this in. above answers so i am mentioning it.
This error can also come if you’re in the wrong folder or path of your pem file is not correct. I was having similar issue and found that my pem file was not there from where i am executing the ssh command
I had the same problem. In my case, macOS doesn’t load my SSH keys, but I fix it with:
I couldn’t connect to a Droplet on DigitalOcean, but the subsequent commands work for me.
You can go to the forum here.
fixed by setting GSSAPIAuthentication to no in /etc/ssh/sshd_config
Maybe you should assign the public key to the authorized_keys , the simple way to do this is using ssh-copy-id -i your-pub-key-file user@dest .
And I think this will clearify the cause of posted problem, actualy this is bug of pssh itself (contains inside «askpass-client.py»). It is pssh’s lib file. And there is documented issue for -A case: https://code.google.com/archive/p/parallel-ssh/issues/80 There are two possible resolutions to use version of pssh containing this bug in case you forced to use passphrase for private key access:
- Correct your «askpass-client.py» as described in link listed before in my post.
- Using your favorite pass keeper.
Thnks for attention, hope it helps!
First a password login has to be established to remote machine
- Firstly make a password login
you have to enable a password login by enabling the property ie) PasswordAuthentication yes in sshd_config file.Then restart the sshd service and copy the pub key to remote server (aws ec2 in my case), key will be copied without any error
- Without password login works if and only if password login is made first
- copy the pub key contents to authorised keys, cat xxx.pub >>
This can happen if you are missing the correct id_rsa key set up in authorized_keys for an AWS instance.
Exact error I got (this article came up when I googled the error):
ec2-user@X.X.X.X: Permission denied (publickey,gssapi-keyex,gssapi-with-mic).
Note: If you have many keys, you have to either specify the key on the ssh command line or else add it to you ssh-agent keys (see ssh-add -l). Only the first 6 keys from ssh-agent may work — the default sshd MaxAuthTries config value is 6.
Hope, this will help someone. Problem I encountered is, I was completely using wrong key with the IP. Make sure you are using the right key for the right IP
For me it is a completely mistake, someone copy paste the key into the same row with another key, after separating them into two different lines then it works again, so check if your authorized_key file has similar mistakes !
I had same issue Permission denied (publickey, gssapi-keyex, gssapi-with-mic) earlier.
I had to go /etc/ssh/sshd_config to add the user user into AllowUsers section, then restarted sshd service.
Let me share with you how I did it and I am sure you will find good answer here.
Make sure the following
Step 1. You have Public DNS (IPv4) from aws E.g ec2-IPV4.us-east-2.compute.amazonaws.com
Step 2. You remember where your your_secret_key_is.pem E.g its better to keep it far from root of the known folders like Downloads, Desktop or Documents
Step 3 Open terminal and add the command sudo ssh -v -i path-to-key.pem ec2-user@host
ec2-user is important because it for some linux server it is the username
sudo it needs permission to execute
host It is Amazon Public DNS (IPv4) (copy step 1)
I know this is an old question, but thought I’d add my fix in the pot.
I was getting the same error trying to connect to Amazon Linux from Ubuntu. The solution was to simply change this:
. pretty simple change there got me in.
seems like an issue generated by the ssh client rather than the ssh server in my case. Here’s what caused my problem and how I solved. The problem source is I used sudo to generate the keys like this:
This automatically set the owner of these key files to root only, so my current user doesn’t have permission to read the keys.
Now solution #1 is change the file ownership to your current user. This’s what I did.
Solution #2 would be just run ssh client with sudo when you try to connect to the ssh server.
Finally, a trick to find the source of problem with ssh client.
This let me focus on the problem by:
- show verbose info by -v flag.
- the -o option and -i
/.ssh/serverA_ed25519_key force ssh client to try with this key ONLY, not all the keys you have.
Источник