- How to stop ICMP ping flood attack (DOS) on Linux
- Denial-of-Service Attacks
- What is ping flood attack? Why you should worry?
- Lab Environment
- Example-1: Stop ICMP ping flood attack (IPv4) with iptables
- Example-2: Stop ICMP ping flood attack (IPv6) with iptables
- Example-3: Protect ping flood DOS attack using firewalld (IPv4)
- Example-4: Protect ping flood DOS attack using firewalld (IPv6)
- Conclusion
- References
- Related Posts
- Как отключить/включить ответ ping в Linux
- 1 Отключить/включить постоянный ответ ping (через sysctl)
- 2 Временно отключить/включить ответ ping (через sysctl)
- 3 Временно отключить ответ ping (через брандмауэр/iptables)
- 4 Временно включить ответ ping (через брандмауэр/iptables)
- Бонус
- Allow/deny ping on Linux server – iptables rules for icmp
- Okay let’s start, Allow/deny ping on Linux server rules.
- Required iptables command switches
- What is iptables in Linux?
- How to block PING to your server with an error message?
- To block without any messages use DROP as Jump to target.
- Allow Ping from Outside to Inside
- How to block PING from your server?
- To block with out any error messages
- Allow Ping from Inside to Outside
- Hooooray…. It’s time to relax!! Just watch A Breakfast Ride To Chota Ladakh
- Post navigation
- Arunlal Ashok
- 23 thoughts on “ Allow/deny ping on Linux server – iptables rules for icmp ”
- Linux Ping Command Tutorial with Examples
- How ping Works in Linux
- How to Use the ping Command
- ping Commands in Linux with Examples
- ping “localhost” to Check Local Network
- Specify the Internet Protocol
- Change Time Interval Between Ping Packets
- Change Ping Packet Size
- Flood a Network Using ping to Test Performance
- How to Limit the Number of Pings
- Limit Number of Ping Packets
- Set Time Limit for ping Command
- Other Uses for ping
- Suppress Ping Output to Print only Summary Statistics
- Add Timestamp Before Each Line in ping Output
- Get an Audible Ping When a Host is Reachable
- Show Ping Version and Exit
How to stop ICMP ping flood attack (DOS) on Linux
Table of Contents
I really don’t think ping needs any sort of introduction. ping is a network troubleshooting tool that reports whether or not a remote node is reachable. ping sends an ICMP echo request to the remote node that should then reply with an ICMP echo reply. Because ping and ICMP can be used very effectively to map out a network, many network packet filters and firewalls are configured to drop ICMP to provide tighter security.
Besides checking if a node is responding (or other simple connectivity issues), ping also can be used to troubleshoot other network-related matter. But today we plan to discuss a scenario when someone can use to overload the network of a server by sending a flood of ping request.
Denial-of-Service Attacks
DoS attacks are based on the idea of flooding your system with packets to disrupt or seriously degrade your Internet connection, tying up local servers to the extent that legitimate requests can’t be honored or, in the worst case, crashing your system altogether. The two most common results are keeping the system too busy to do anything useful and tying up critical system resources.
You can’t protect against DoS attacks completely. They can take as many different forms as the attacker’s imagination allows. Anything that results in a response from your system, anything that results in your system allocating resources (including logging of the attack), anything that induces a remote site to stop communicating with you—all can be used in a DoS attack.
These attacks usually involve one of several classic patterns, including TCP SYN flooding, ping flooding, UDP flooding, fragmentation bombs, buffer overflows, and ICMP routing redirect bombs.
What is ping flood attack? Why you should worry?
- A ping flood is a denial-of-service attack in which the attacker attempts to overwhelm a targeted device, causing the target to become inaccessible to normal traffic.
- The -f parameter must be used with ping command which causes Linux to send as many ICMP echo requests as possible, which can quickly cause network problems on burdened networks.
- The parameter can be used to create a load that simulates a heavy network or to create an additional load on the target machine.
- Flood ping-output packets as fast as they come back or 100 times per second, whichever is greater.
- It is most successful if the attacker has more bandwidth than the victim
- If the target system is slow enough, it is possible to consume enough of its CPU cycles for a user to notice a significant slowdown.
- PING-based Distributed Denial of Service (DDoS) attacks are infamous as they are known to have brought down high profile web sites such as Ebay, ETrade and Yahoo. They have also been used in an attempt to bring down the entire Internet by attacking its DNS root servers.
- This Ping Flood Attack is a Layer-3 attack in the TCP/IP suite. One of the earlier work shows that a simple Ping attack can make the target host busy in processing the ping requests consuming 100% of the CPU utilization
Here we are sending ping flood from server1 to server2 :
As you can see that there is
0% packet loss and almost 12935 packets were transmitted in 658ms.
Lab Environment
I have two virtual machines running with CentOS 7 and 8 Linux. The hostname of these VMs are server-1 and server-2 . In all my examples I will use server-1 as my client and server-2 as my server so all the iptables or firewalld related changes must be done on the server node i.e. server-2 for us.
Example-1: Stop ICMP ping flood attack (IPv4) with iptables
It is always recommended to BLOCK all incoming requests to your Linux Server and only allow requests as per the ALLOW rules. But before your DROP all the incoming requests, at least allow port 22 so that you are able to connect to your server using SSH.
Now DROP all the incoming request via INPUT chain:
List the applied rules:
So we have to apply hash limit to ICMP type 8 which is for Echo Request.
List the applied rules:
Now attempt to send ping flood from server-1 to server-2 :
So we have not completely blocked ICMP packets, instead just applied hash limit to avoid ping flood attacks which is why there is 84% packet loss instead of 100%.
Example-2: Stop ICMP ping flood attack (IPv6) with iptables
Similar to IPv4 we can also control ICMP Echo request by applying a hash limit for IPv6 traffic. To limit ping flood for IPv6 packets you must apply iptables rule to ICMPv6 type 128:
First of all DROP all incoming requests:
Now apply hash limit to ICMPv6 type 128 using the following rule:
List this applied rules for IPv6:
Verify if ICMPv6 Echo Request is limited for ping flood for this node where we have applied the iptables rule:
Our 78% of ping6 packets were dropped so our hash limit is working as expected.
Example-3: Protect ping flood DOS attack using firewalld (IPv4)
In this example we will use firewalld to control the ping flood based DOS attack. There are different ways you can use firewalld, we will apply a direct rule which is sort of one-to-one mapping to iptables.
Activate the changes:
You can list the applied direct rules using:
Verify if ping flood traffic is blocked by firewalld:
So 49% of the flood requests are dropped which means our rule is working as expected.
Example-4: Protect ping flood DOS attack using firewalld (IPv6)
Similar to IPv4 we can also limit ping flood requests using firewalld for IPv6. You may add this direct rule in your environment:
Activate the changes:
Currently I don’t have an IPv6 environment with firewalld to test this rule, but if you face any issues then let me know using the comments section.
Conclusion
In this article we explored ICMP i.e. Internet Control Message Protocol and covered the areas related to Ping flood based DOC attacks. ICMP doesn’t use ports. Instead it talks to the Ethernet card at a low level. But ICMP does have types to identify itself. Since we wanted to limit the ICMP Echo request so we have applied our iptables and firewalld rules to limit ICMP and ICMPv6 Echo request type.
References
Related Posts
Didn’t find what you were looking for? Perform a quick search across GoLinuxCloud
If my articles on GoLinuxCloud has helped you, kindly consider buying me a coffee as a token of appreciation.

For any other feedbacks or questions you can either use the comments section or contact me form.
Thank You for your support!!
Источник
Как отключить/включить ответ ping в Linux
Главное меню » Linux » Как отключить/включить ответ ping в Linux
1 Отключить/включить постоянный ответ ping (через sysctl)
1.1 Добавьте следующую строку в «/etc/sysctl.conf» (чтобы включить, измените 1 на 0)
Мы можем использовать следующую команду для достижения этого
1.2 Применить изменение
2 Временно отключить/включить ответ ping (через sysctl)
2.1 Выполните следующую команду, чтобы временно отключить ответ ping (чтобы включить, измените 1 на 0)
2.2 Применить изменение
3 Временно отключить ответ ping (через брандмауэр/iptables)
3.1 Выполните следующую команду, чтобы заблокировать/сбросить ping-трафик
Примечание. Хотя правила iptables будут действовать после перезагрузки в CentOS и RHEL, они не будут действовать после перезагрузки в Debian/Ubuntu/Kali Linux и т. д..
4 Временно включить ответ ping (через брандмауэр/iptables)
4.1 Выполните следующую команду, чтобы включить/разрешить ping-трафик
Примечание. Как и в разделе 3, правила firewall/iptables будут действовать после перезагрузки в CentOS и RHEL, они не будут действовать после перезагрузки в Debian/Ubuntu/Kali Linux и т. д.
Бонус
Еще один способ легко разрешить ответ ping – просто временно отключить iptables/firewall.
Если вы нашли ошибку, пожалуйста, выделите фрагмент текста и нажмите Ctrl+Enter.
Источник
Allow/deny ping on Linux server – iptables rules for icmp
Allow/deny ping on Linux server. PING – Packet InterNet Gopher, is a computer network administration utility used to test the reachability of a host on an Internet Protocol (IP) network and to measure the total round-trip time for messages sent from the originating host to a destination computer and back.
Blocking PING on server is helpful sometimes, if the server is continue to face any type of DDoS attack by using the PING feature. By using iptables we can simply stop the PING option to and from your server. Before starting this, you must have an idea about What is iptables in Linux?
We can call it is the basics of Firewall in Linux. Iptables is a rule based firewall system and is normally pre-installed on a Unix operating system which is controlling the incoming and outgoing packets. By-default the iptables is running without any rules, we can create, add, edit rules to it. You will get more details from the abouve link. In this article I am going to explain how we can alow/block PING in and out to a server. This would be more useful as you are Linux server admin.
We can manage it by the help of ‘iptables‘. The ‘ping‘ is using ICMP to communicate. We can simply manage the ‘icmp : Internet Controlled Message Protocol’ from iptables.
Okay let’s start, Allow/deny ping on Linux server rules.
Required iptables command switches
The below pasted switches are required for creating a rule for managing icmp.
Normally using icmp types and its Codes Click here for ICMP Types and Codes
Here I am explaining some examples.
What is iptables in Linux?
What is iptables in Linux? We can call, it’s the basics of Firewall for Linux. Iptables is a rule based firewall system and it is normally pre-installed on a Unix operating system which is controlling the incoming and outgoing packets. By-default the iptables is running without any rules, we can create, add, edit rules into it.
In this article I am trying to explain the basics of iptables with some common practices.
How to block PING to your server with an error message?
In this way you can partially block the PING with an error message ‘Destination Port Unreachable’. Add the following iptables rules to block the PING with an error message. (Use REJECT as Jump to target)
Example:
To block without any messages use DROP as Jump to target.
Allow Ping from Outside to Inside
How to block PING from your server?
In this way you can block PING option from your server to outside. Add these rules to your iptables to do the same.
Block PING operation with message ‘Operation not permitted’
Example:
To block with out any error messages
For this, DROP the echo-reply to the INPUT chain of your iptables.
Allow Ping from Inside to Outside
You can use the icmp code instead of icmp-type name for adding rule to iptables.
That’s it. Try this and let me know your feedback.
Hooooray…. It’s time to relax!! Just watch A Breakfast Ride To Chota Ladakh
Related Posts
Post navigation
Arunlal Ashok
Senior Operations Engineer (SRE) at NewFold Digital. Linux lover. Traveller. Father of two princesses.
Always happy for an open discussion! Write to arun ((@)) crybit ((dot)) com.
LinkedIn: https://www.linkedin.com/in/arunlal-a-18037773/
23 thoughts on “ Allow/deny ping on Linux server – iptables rules for icmp ”
Thank you so very much for showing how to block pings using iptables. Would you be able to block pings using firewalld using the rich rules?
Hi, I have an HP server with Centos. I used to login as root from outside. Yesterday for testing purposes I enabled the Selinux enforcing and reboot the server for relabeling. After that I am unable to ssh to the server. Cannot login locally as root even though Root login is permitted in sshd_config. I have disabled the Selinux now completely from sysconfig/selinux and rebooted the server and did the relabeling again using fixfiles command also. still, locally i cannot login from root as it gives me error “root logins are not allowed”(root login is permitted in sshdconf). I restarted the sshd service also but still it is not possible to login locally from root. remote login from ssh is also not possible. When I do ssh it gives me output of “connection timeout” and when i do ping it gives me “no answer from server”. The ILO is working fine.
¡Very useful post!
You can also block ICMP IPv6 reply traffic using:
iptables -A INPUT -p icmpv6 –icmp-type echo-request -j DROP
Источник
Linux Ping Command Tutorial with Examples
Home » SysAdmin » Linux Ping Command Tutorial with Examples
Most Linux users are familiar with the ping command and know how to use it in its basic form. However, there are many additional ping options and variations. In this guide, we will walk you through some of the most useful Linux ping commands with examples.
The commands in this article work with any UNIX or Linux distribution. The test system we used to provide the examples and output samples is Ubuntu 18.04.2 LTS.
- Linux or UNIX-like system
- Access to a terminal
- A user with the necessary permissions to run the commands
How ping Works in Linux
The Linux ping command is a simple utility used to check whether a network is available and if a host is reachable. With this command, you can test if a server is up and running. It also helps with troubleshooting various connectivity issues.
The ping command allows you to:
- Test your internet connection.
- Check if a remote machine is online.
- Analyze if there are network issues, such as dropped packages or high latency.
When you try to “ping” a remote host, your machine starts sending ICMP echo requests and waits for a response. If the connection is established, you receive an echo reply for every request.
The output for the ping command contains the amount of time it takes for every packet to reach its destination and return.
The terminal keeps printing the responses until interrupted. After every session, there are a few lines with ping statistics.
How to Use the ping Command
The basic ping syntax includes ping followed by a hostname, a name of a website, or the exact IP address.
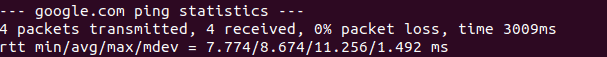
Hence, to check whether a remote host is up, in this case, google.com, type in your terminal:
Press Ctrl + C on your keyboard to stop the process.
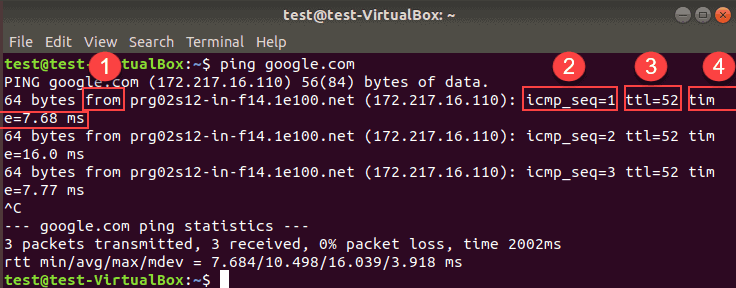
- from : The destination and its IP address. Note that the IP address may be different for a website depending on your geographical location.
- icmp_seq=1 : The sequence number of each ICMP packet. Increases by one for every subsequent echo request.
- ttl=52 : The Time to Live value from 1 to 255. It represents the number of network hops a packet can take before a router discards it.
- time=7.68 ms : The time it took a packet to reach the destination and come back to the source. Expressed in milliseconds.
ping Commands in Linux with Examples
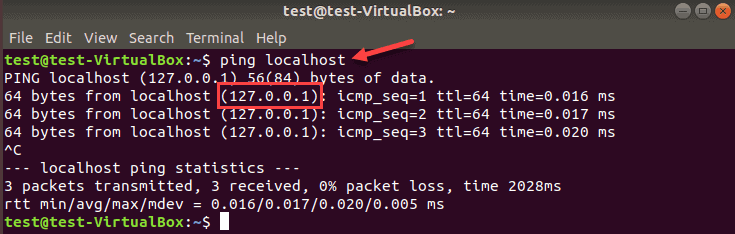
ping “localhost” to Check Local Network
If you encounter issues reaching a website or a remote machine, you can ping localhost to confirm you have a network connection. Use one of the three ways to check the local network interface:
- ping 0 – This is the quickest way to ping localhost. Once you type this command, the terminal resolves the IP address and provides a response.
- ping localhost – You can use the name to ping localhost. The name refers to your computer, and when we use this command, we say: “ping this computer.”
- ping 127.0.0.1 – Some people prefer using the IP address to ping localhost.
Whichever method you choose, the ping output looks the same.
Specify the Internet Protocol
IPv6 is the IP address alphanumeric format that will supersede IPv4. The reason for this is there is a limited number of IPv4 address, and we are running out of possible combinations.
To request IPv6 or IPv4 address, add -6 or -4 after the ping command and before a hostname/IP.
Change Time Interval Between Ping Packets
The default interval between each ping request is set to one second. You can increase or decrease that time using the –i switch. To decrease the ping interval, use values lower than 1.
To increase the ping interval, enter any value higher than 1.
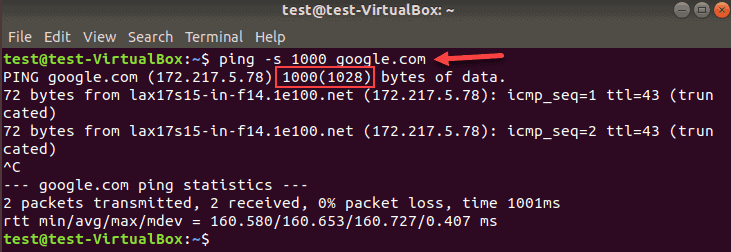
Change Ping Packet Size
In some scenarios, you may want to use -s to increase the packet size from the default value of 56 (84) bytes. The number in parenthesis represents the ping bytes sent including 28 bytes of the header packet.
For example, to increase the packet size to 1000 bytes:
You get this output:
This command is useful when testing network performance. You can test if a network link throttles when you increase the packet size to a few thousand bytes.
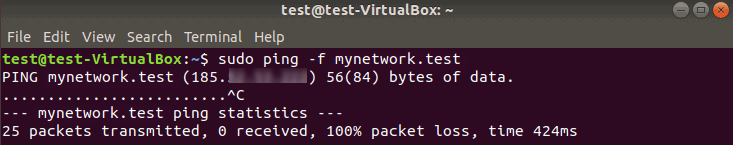
Flood a Network Using ping to Test Performance
You can use ping flood to test your network performance under heavy load.
Ping flood -f option requires root to execute. Otherwise, apply sudo to your ping command to flood a host. This command sends a large number of packets as soon as possible.
The output prints a dot for every sent package, and a backspace for every response. The statistics line shows a summary of the ping command.
How to Limit the Number of Pings
The default setting for the ping command is to keep sending the request until you interrupt it. You can limit the number of pings using one of the two methods.
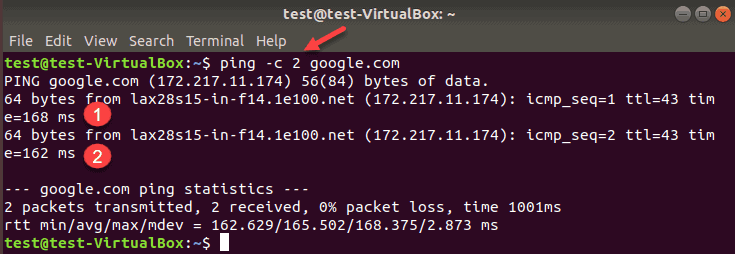
Limit Number of Ping Packets
To make the ping command automatically stop after it sends a certain number of packets, use -c and a number. This sets the desired amount of ping requests, as shown in this example:
As you can see on the image above, the ping command stopped sending packets after two requests.
Set Time Limit for ping Command
To stop receiving a ping output after a specific amount of time, add -w and an interval in seconds to your command.
For example, to stop printing ping results after 25 seconds, enter the ping command:
Other Uses for ping
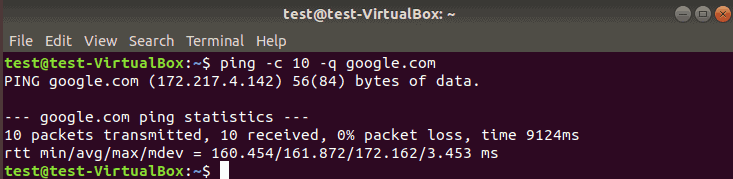
Suppress Ping Output to Print only Summary Statistics
If you do not want to clog your screen with information for every packet, use the -q switch to display the summary only.
The -q option prints one line with the regular ping information and then provides the statistics at the end. The letter “q” in this command stands for “quiet” output.
We usually combine the quiet output with other options. In this case, we will limit the ping to send 10 packets and suppress the output.
Add Timestamp Before Each Line in ping Output
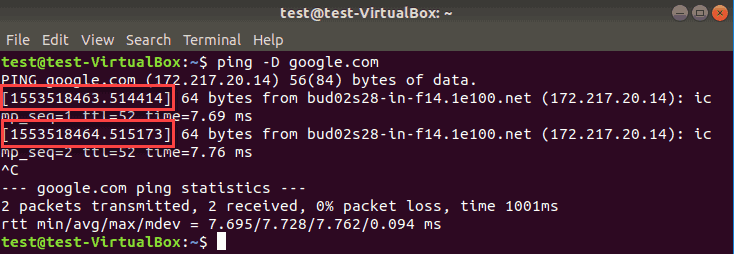
If you want to note the time of day when you execute the ping command, add the -D option.
This prints a timestamp in UNIX format before each line.
Note: You need to use uppercase D, as these commands are case sensitive.
Get an Audible Ping When a Host is Reachable
When you use the –a switch, the system plays a sound when there is a response from a host.
An audible ping is useful when you are troubleshooting network issues and do not want to look at the screen until there is a response.
The output looks the same as a regular ping command output.
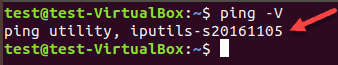
Show Ping Version and Exit
At any time, you can check the version of the ping tool on your system.
Append -V to the ping command to display the version of this utility.
Commonly used Ping Commands include:
| Ping Option | What The Command Does |
| a | Generates a sound when the peer can be reached. |
| b | Allows to ping a broadcast IP address. |
| B | Prevents the ping to change the source address of the probe. |
| c (count) | Limits the number of sent ping requests. |
| d | Sets the SO-DEBUG option on the used socket. |
| f | Floods the network by sending hundreds of packets per second. |
| i (interval) | Specifies an interval between successive packet transmissions. The default value is one second. |
| I (interface address) | Sets the source IP address to the specified interface IP address. The option is required when pinging IPv6 link local address. You can use an IP address or name of the device. |
| l (preload) | Defines the number of packets to send without waiting for a reply. To specify a value higher than 3, you need superuser permissions. |
| n | Displays IP addresses in the ping output rather than hostnames. |
| q | Shows a quiet output. One ping line is displayed and the summary of the ping command at the end. |
| T (ttl) | Sets the Time To Live. |
| v | Provides verbose output. |
| V | Displays the ping version and exits to a new command prompt line. |
| w (deadline) | Specifies a time limit before the ping command exits, regardless of how many packets have been sent or received. |
| W (timeout) | Determines the time, in seconds, to wait for a response. |
Now you know how to use the Linux ping command. The examples in the tutorial should help you understand how to use “ping” on a day-to-day basis.
Ping helps you check the network connectivity both locally and with a remote host.
To view the complete list with the remaining ping options, run the man command man ping inside the terminal.
Источник