Supported Cipher Suites and Protocols in the Schannel SSP
Applies To: Windows Vista, Windows Server 2008, Windows 7, Windows 8.1, Windows Server 2008 R2, Windows Server 2012 R2, Windows Server 2012, Windows 8
This reference topic for IT professional lists the cipher suites and protocols that are supported by the Schannel Security Support Provider (SSP), and it describes the different types of algorithms that are used by the suites.
The following table lists the protocols implemented by the Schannel SSP. For more information about how changes to the following protocols are implemented in the Schannel SSP, see Differences in the Schannel SSP by Operating System Version.
IETF RFC 5246 is defined TLSВ 1.2, and it made the following RFCs obsolete: 3268, 4346, and 4366. The significant improvements over TLSВ 1.1 included handshake and renegotiation improvements.
The IETF RFC 4346 made the original RFCВ 2246 obsolete because it defined TLSВ 1.1. The significant improvements over TLSВ 1.0 included:
The implicit initialization vector was replaced with an explicit initialization vector to protect against cipher-block chaining attacks.
Handling of padding errors was changed to use the “bad record message authentication code” alert rather than the “decryption failed” alert to protect against cipher-block chaining attacks.
Internet Assigned Numbers Authority (IANA) registries were defined for protocol parameters. The IANA was administered under the U.S Department of Commerce, and it is responsible for the allocation of globally unique names and numbers, which are used in Internet protocols that are published as RFC documents.
Premature closures no longer cause a condition where the session cannot be resumed.
SSLВ 3.0 was standardized through the IETF as RFCВ 2246, which resulted in the public protocol TLSВ 1.0.
The protocol is composed of two layers: the TLS record protocol and the TLS handshake protocol. The TLS record protocol provides connection security that has two basic properties:
The connection is private. Symmetric cryptography is used for data encryption, and the keys for this encryption are generated uniquely for each connection. In addition, the keys are based on a secret negotiated by another protocol (such as the TLS handshake protocol). The record protocol can also be used without encryption.
The connection is reliable. Message transport includes a message integrity check that uses a keyed message authentication code (MAC). Secure hash functions are used for MAC computations. The record protocol can operate without a MAC, but it is generally only used in this mode while another protocol is using the record protocol as a transport for negotiating security parameters.
SSLВ 3.0 was a Netscape Corporation private protocol that has not been upgraded with modern cipher suites. It is dependent on the MD5 hash function for half of the master key. The Schannel SSP will use SSLВ 3.0, which is useful for backwards compatibility, if all other protocol versions of TLS fail to negotiate.
SSLВ 2.0 was a Netscape Corporation proprietary protocol. It is disabled by default on Windows client computers designated in the Applies To list at the beginning of this topic.
The Datagram Transport Layer Security (DTLS) protocol provides communications privacy for datagram protocols. The protocol allows client and server applications to communicate in a way that is designed to prevent eavesdropping, tampering, or message forgery. The DTLS protocol is based on the Transport Layer Security (TLS) protocol, and it provides equivalent security guarantees, reducing the need to use IPsec or designing a custom application layer security protocol.
The Private Communications Technology protocol is a technology developed by Microsoft, which was replaced by more robust protocols(SSLВ 3.0 and TLS).
The Schannel SSP will not use PCTВ 1.0.
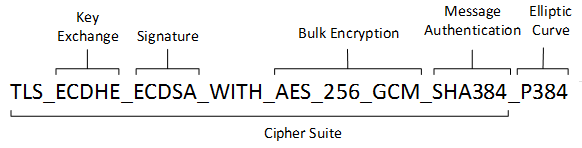
A cipher suite is a set of cryptographic algorithms. Schannel protocols use algorithms from a cipher suite to create keys and encrypt information. A cipher suite specifies one algorithm for each of the following tasks:
Key exchange algorithms protect the information that is required to create shared keys. These algorithms are asymmetric (public key algorithms), and they perform well for relatively small amounts of data.
Bulk encryption algorithms encrypt messages that are exchanged between client computers and servers. These algorithms are symmetric, and they perform well for large amounts of data.
Message authentication algorithms generate message hashes and signatures that ensure the integrity of a message.
For information about each supported cipher suite in Windows Server 2012 R2 and Windows 8.1, FIPS-compliance enablement, key exchange algorithms, encryption algorithms, and message hashes that are used in SSL 3.0, TLSВ 1.0, TLSВ 1.1, and TLSВ 1.2, see article 2929781 in the Microsoft Knowledge Base.
For information about each supported cipher suite, FIPS-compliance enablement, key exchange algorithms, encryption algorithms, and message hashes that are used in SSL 3.0, TLSВ 1.0, TLSВ 1.1, and TLSВ 1.2, see Cipher Suites in Schannel.
For information about each supported cipher suite, FIPS-compliance enablement, key exchange algorithms, encryption algorithms, and message hashes that are used in SSLВ 2.0, SSL 3.0, and TLSВ 1.0 in WindowsВ ServerВ 2008 and WindowsВ Vista, see Schannel Cipher Suites in WindowsВ Vista.
Cipher suite and protocol support
The following table shows information about protocol and ciper suite support in the Windows operating systems.
Cipher Suites in TLS/SSL (Schannel SSP)
A cipher suite is a set of cryptographic algorithms. The schannel SSP implementation of the TLS/SSL protocols use algorithms from a cipher suite to create keys and encrypt information. A cipher suite specifies one algorithm for each of the following tasks:
- Key exchange
- Bulk encryption
- Message authentication
Key exchange algorithms protect information required to create shared keys. These algorithms are asymmetric (public key algorithms) and perform well for relatively small amounts of data.
Bulk encryption algorithms encrypt messages exchanged between clients and servers. These algorithms are symmetric and perform well for large amounts of data.
Message authentication algorithms generate message hashes and signatures that ensure the integrity of a message.
Developers specify these elements by using ALG_ID data types. For more information, see Specifying Schannel Ciphers and Cipher Strengths.
In earlier versions of Windows, TLS cipher suites and elliptical curves were configured by using a single string:
Different Windows versions support different TLS cipher suites and priority order. See the corresponding Windows version for the default order in which they are chosen by the Microsoft Schannel Provider.
Windows Server 2022: For information about supported cipher suites, see TLS Cipher Suites in Windows Server 2022
Windows 10, version 1903: For information about supported cipher suites, see TLS Cipher Suites in Windows 10 v1903
Windows 10, version 1809: For information about supported cipher suites, see TLS Cipher Suites in Windows 10 v1809
Windows 10, version 1803: For information about supported cipher suites, see TLS Cipher Suites in Windows 10 v1803
Windows 10, version 1709: For information about supported cipher suites, see TLS Cipher Suites in Windows 10 v1709
Windows 10, version 1703: For information about supported cipher suites, see TLS Cipher Suites in Windows 10 v1703
Windows Server 2016 and Windows 10, version 1607: For information about supported cipher suites, see TLS Cipher Suites in Windows 10 v1607
Windows 10, version 1511: For information about supported cipher suites, see TLS Cipher Suites in Windows 10 v1511
Windows 10, version 1507: For information about supported cipher suites, see TLS Cipher Suites in Windows 10 v1507
Windows Server 2012 R2 and Windows 8.1: For information about supported cipher suites, see TLS Cipher Suites in Windows 8.1
Windows Server 2012 and Windows 8: For information about supported cipher suites, see TLS Cipher Suites in Windows 8
Windows Server 2008 R2 and Windows 7: For information about supported cipher suites, see TLS Cipher Suites in Windows 7
Windows Server 2008 and Windows Vista: For information about supported cipher suites, see TLS Cipher Suites in Windows Vista
Windows Server 2003 and Windows XP: For information about supported cipher suites, see the following topics.
| Topic | Description |
|---|---|
| TLS Cipher Suites | Information about the cipher suites available with the TLS protocol in Windows Server 2003 and Windows XP. |
| Secure Sockets Layer Protocol | General information about SSL 2.0 and 3.0, including the available cipher suites in Windows Server 2003 and Windows XP. |
Prior to Windows 10, cipher suite strings were appended with the elliptic curve to determine the curve priority. Windows 10 supports an elliptic curve priority order setting so the elliptic curve suffix is not required and is overridden by the new elliptic curve priority order, when provided, to allow organizations to use group policy to configure different versions of Windows with the same cipher suites.
TLS 1.2 Cipher Suite Support in Windows Server 2012 R2
I am running Windows Server 2012 R2 as an AD Domain Controller, and have a functioning MS PKI. I am having trouble getting various LDAP clients to connect using LDAP over SSL (LDAPS) on port 636. I would like to see if anyone can suggest how to enable Windows to use specific TLS 1.2 ciphers that are supported by my clients.
The SChannel service is tearing down the TCP connection and offering the following description in the event logs.
Log Name: System
Source: Schannel
Date: 7/28/2015 12:28:04 PM
Description:
An TLS 1.2 connection request was received from a remote client application, but none of the cipher suites supported by the client application are supported by the server. The SSL connection request has failed.
Log Name: System
Source: Schannel
Date: 7/28/2015 12:28:04 PM
Description:
A fatal alert was generated and sent to the remote endpoint. This may result in termination of the connection. The TLS protocol defined fatal error code is 40. The Windows SChannel error state is 1205.
So far, I have tested two clients, LDAPAdmin 1.6 and a Cisco ASA using LDAPS for AAA. Packet captures of both exchanges show the list of ciphers offered by the clients, but I’m not sure of any of these are actually enabled by default. Seems strange that they wouldn’t be.
LDAPAdmin 1.6 Cipher List from PCAP:
Secure Sockets Layer
SSL Record Layer: Handshake Protocol: Client Hello
Content Type: Handshake (22)
Version: TLS 1.2 (0x0303)
Cipher Suites (26 suites)
Cipher Suite: TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (0xc028)
Cipher Suite: TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 (0xc027)
Cipher Suite: TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (0xc014)
Cipher Suite: TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (0xc013)
Cipher Suite: TLS_DHE_RSA_WITH_AES_256_GCM_SHA384 (0x009f)
Cipher Suite: TLS_DHE_RSA_WITH_AES_128_GCM_SHA256 (0x009e)
Cipher Suite: TLS_RSA_WITH_AES_256_GCM_SHA384 (0x009d)
Cipher Suite: TLS_RSA_WITH_AES_128_GCM_SHA256 (0x009c)
Cipher Suite: TLS_RSA_WITH_AES_256_CBC_SHA256 (0x003d)
Cipher Suite: TLS_RSA_WITH_AES_128_CBC_SHA256 (0x003c)
Cipher Suite: TLS_RSA_WITH_AES_256_CBC_SHA (0x0035)
Cipher Suite: TLS_RSA_WITH_AES_128_CBC_SHA (0x002f)
Cipher Suite: TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384 (0xc02c)
Cipher Suite: TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256 (0xc02b)
Cipher Suite: TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384 (0xc024)
Cipher Suite: TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256 (0xc023)
Cipher Suite: TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA (0xc00a)
Cipher Suite: TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA (0xc009)
Cipher Suite: TLS_DHE_DSS_WITH_AES_256_CBC_SHA256 (0x006a)
Cipher Suite: TLS_DHE_DSS_WITH_AES_128_CBC_SHA256 (0x0040)
Cipher Suite: TLS_DHE_DSS_WITH_AES_256_CBC_SHA (0x0038)
Cipher Suite: TLS_DHE_DSS_WITH_AES_128_CBC_SHA (0x0032)
Cipher Suite: TLS_RSA_WITH_3DES_EDE_CBC_SHA (0x000a)
Cipher Suite: TLS_DHE_DSS_WITH_3DES_EDE_CBC_SHA (0x0013)
Cipher Suite: TLS_RSA_WITH_RC4_128_SHA (0x0005)
Cipher Suite: TLS_RSA_WITH_RC4_128_MD5 (0x0004)
Elliptic curves (2 curves)
Elliptic curve: secp256r1 (0x0017)
Elliptic curve: secp384r1 (0x0018)
Signature Hash Algorithms (9 algorithms)
Signature Hash Algorithm: 0x0401
Signature Hash Algorithm Hash: SHA256 (4)
Signature Hash Algorithm Signature: RSA (1)
Signature Hash Algorithm: 0x0501
Signature Hash Algorithm Hash: SHA384 (5)
Signature Hash Algorithm Signature: RSA (1)
Signature Hash Algorithm: 0x0601
Signature Hash Algorithm Hash: SHA512 (6)
Signature Hash Algorithm Signature: RSA (1)
Signature Hash Algorithm: 0x0201
Signature Hash Algorithm Hash: SHA1 (2)
Signature Hash Algorithm Signature: RSA (1)
Signature Hash Algorithm: 0x0403
Signature Hash Algorithm Hash: SHA256 (4)
Signature Hash Algorithm Signature: ECDSA (3)
Signature Hash Algorithm: 0x0503
Signature Hash Algorithm Hash: SHA384 (5)
Signature Hash Algorithm Signature: ECDSA (3)
Signature Hash Algorithm: 0x0603
Signature Hash Algorithm Hash: SHA512 (6)
Signature Hash Algorithm Signature: ECDSA (3)
Signature Hash Algorithm: 0x0203
Signature Hash Algorithm Hash: SHA1 (2)
Signature Hash Algorithm Signature: ECDSA (3)
Signature Hash Algorithm: 0x0202
Signature Hash Algorithm Hash: SHA1 (2)
Signature Hash Algorithm Signature: DSA (2)
Cisco ASA Cipher List from PCAP:
Cipher Suites (25 suites)
Cipher Suite: TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384 (0xc02c)
Cipher Suite: TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (0xc030)
Cipher Suite: TLS_DHE_RSA_WITH_AES_256_GCM_SHA384 (0x009f)
Cipher Suite: TLS_RSA_WITH_AES_256_GCM_SHA384 (0x009d)
Cipher Suite: TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384 (0xc024)
Cipher Suite: TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (0xc028)
Cipher Suite: TLS_DHE_RSA_WITH_AES_256_CBC_SHA256 (0x006b)
Cipher Suite: TLS_RSA_WITH_AES_256_CBC_SHA256 (0x003d)
Cipher Suite: TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256 (0xc02b)
Cipher Suite: TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (0xc02f)
Cipher Suite: TLS_DHE_RSA_WITH_AES_128_GCM_SHA256 (0x009e)
Cipher Suite: TLS_RSA_WITH_AES_128_GCM_SHA256 (0x009c)
Cipher Suite: TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256 (0xc023)
Cipher Suite: TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 (0xc027)
Cipher Suite: TLS_DHE_RSA_WITH_AES_128_CBC_SHA256 (0x0067)
Cipher Suite: TLS_RSA_WITH_AES_128_CBC_SHA256 (0x003c)
Cipher Suite: TLS_DHE_RSA_WITH_AES_256_CBC_SHA (0x0039)
Cipher Suite: TLS_RSA_WITH_AES_256_CBC_SHA (0x0035)
Cipher Suite: TLS_DHE_RSA_WITH_AES_128_CBC_SHA (0x0033)
Cipher Suite: TLS_RSA_WITH_AES_128_CBC_SHA (0x002f)
Cipher Suite: TLS_RSA_WITH_3DES_EDE_CBC_SHA (0x000a)
Cipher Suite: TLS_RSA_WITH_RC4_128_SHA (0x0005)
Cipher Suite: TLS_RSA_WITH_RC4_128_MD5 (0x0004)
Cipher Suite: TLS_RSA_WITH_NULL_SHA (0x0002)
Cipher Suite: TLS_EMPTY_RENEGOTIATION_INFO_SCSV (0x00ff)
Elliptic curves (4 curves)
Elliptic curve: secp521r1 (0x0019)
Elliptic curve: secp384r1 (0x0018)
Elliptic curve: secp256r1 (0x0017)
Elliptic curve: secp192r1 (0x0013)
Signature Hash Algorithms (13 algorithms)
Signature Hash Algorithm: 0x0000
Signature Hash Algorithm Hash: None (0)
Signature Hash Algorithm Signature: Anonymous (0)
Signature Hash Algorithm: 0x0401
Signature Hash Algorithm Hash: SHA256 (4)
Signature Hash Algorithm Signature: RSA (1)
Signature Hash Algorithm: 0x0501
Signature Hash Algorithm Hash: SHA384 (5)
Signature Hash Algorithm Signature: RSA (1)
Signature Hash Algorithm: 0x0601
Signature Hash Algorithm Hash: SHA512 (6)
Signature Hash Algorithm Signature: RSA (1)
Signature Hash Algorithm: 0x0301
Signature Hash Algorithm Hash: SHA224 (3)
Signature Hash Algorithm Signature: RSA (1)
Signature Hash Algorithm: 0x0201
Signature Hash Algorithm Hash: SHA1 (2)
Signature Hash Algorithm Signature: RSA (1)
Signature Hash Algorithm: 0x0101
Signature Hash Algorithm Hash: MD5 (1)
Signature Hash Algorithm Signature: RSA (1)
Signature Hash Algorithm: 0x0202
Signature Hash Algorithm Hash: SHA1 (2)
Signature Hash Algorithm Signature: DSA (2)
Signature Hash Algorithm: 0x0403
Signature Hash Algorithm Hash: SHA256 (4)
Signature Hash Algorithm Signature: ECDSA (3)
Signature Hash Algorithm: 0x0503
Signature Hash Algorithm Hash: SHA384 (5)
Signature Hash Algorithm Signature: ECDSA (3)
Signature Hash Algorithm: 0x0603
Signature Hash Algorithm Hash: SHA512 (6)
Signature Hash Algorithm Signature: ECDSA (3)
Signature Hash Algorithm: 0x0303
Signature Hash Algorithm Hash: SHA224 (3)
Signature Hash Algorithm Signature: ECDSA (3)
Signature Hash Algorithm: 0x0203
Signature Hash Algorithm Hash: SHA1 (2)
Signature Hash Algorithm Signature: ECDSA (3)
Here’s a list of Microsoft References I have found so far, however I am not finding specifically how to enable any of these ciphers in the registry.