- How to Install FatRat Tool in Kali Linux?
- Uses of FatRat Tool In Kali Linux:
- Features of FatRat Tool:
- Installation of FatRat Tool:
- Working with TheFatRat Tool :
- Example 1: Create Backdoor with msfvenom.
- Example 2: Create Fud 100% Backdoor with Fudwin 1.0.
- Example 3: Create Fud Backdoor with Avoid v1.2
- Example 4: Create Fud Backdoor 1000% with PwnWinds [Excelent]
- Example 5: Trojan Debian Package For Remote Acces [Trodebi]
- Example 6: Searchsploit
- Example 7: File Pumper [Increase Your Files Size]
- Thefatrat kali linux install
- About
- Thefatrat kali linux install
- About
How to Install FatRat Tool in Kali Linux?
The FatRat is a free and open-source tool used as an exploiting tool. The FatRat tool adds malware with a payload and after that, the malware that you have developed can be executed on different types of operating systems such as android, windows, mac, Linux. The FatRat is a powerful tool that can bypass most of the Antivirus easily and can maintain the connection between attacker and victim. Fatrat Tool can help in generating backdoors, system exploitation, post-exploitation attacks, browser attacks, DLL files, FUD payloads against Linux, Mac OS X, Windows, and Android. We can create malware in different formats using FatRat so that it can be executed easily on the target operating system.
Uses of FatRat Tool In Kali Linux:
- FatRat is used for exploitation.
- FatRat is used to create malware
- Fatrat is used to combine payload with malware.
- Fatrat is used for creating Backdoors for Post Exploitation.
- FatRat is used for browser attacks.
- FatRat is used to get DDL files from Linux.
- FatRat can create malware in different extensions.
Features of FatRat Tool:
- FatRat is Free and Open Source
- FatRat create payloads
- FatRat can bypass most the antivirus.
- FatRat can work with MSFvenom and Metasploit
- FatRat can Generate payloads in Various formats.
- FatRat generates Local or remote listener Generation.
- FatRat can easily make Backdoor by category Operating System such as Linux, android etc.
Installation of FatRat Tool:
Step 1: Open Your Kali Linux and move to the Desktop directory.
Step 2: Now on desktop create a new Directory named fatrat.
Step 3: Now move to fatrat directory.
Step 4: Now you have to download the fatrat tool from GitHub to do that you have to clone it from GitHub. Just clone the tool using the following command.
Step 5: The TheFatRat tool has been downloaded into your Kali Linux now move to the directory where you have downloaded the tool and list out the content.
Step 6: Now you have to give the permission of execution to the setup.sh using the following command.
Step 7: Now run the tool using the following command.
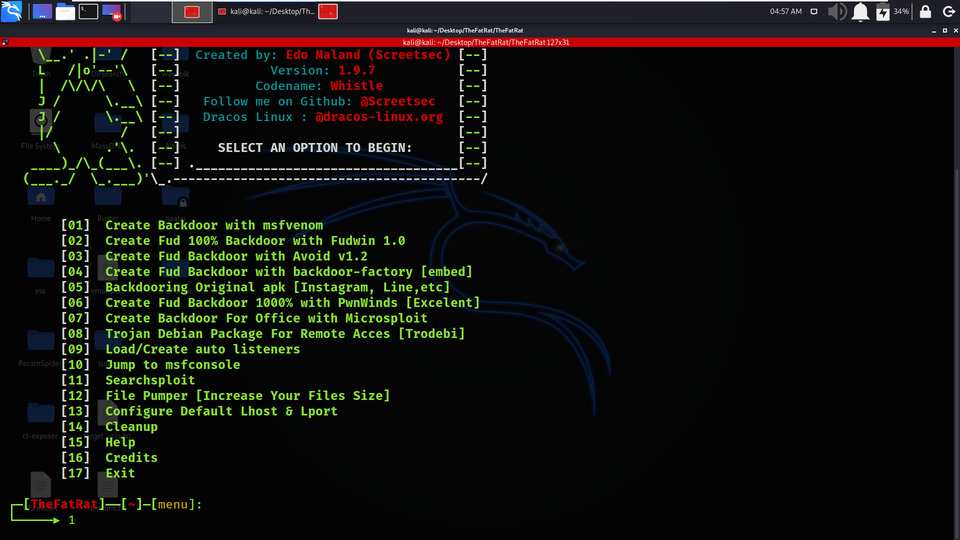
Working with TheFatRat Tool :
Example 1: Create Backdoor with msfvenom.
We are Creating a Backdoor using msfvenom utility. So we have chosen Option 1.
2. Backdoors can be of various extensions like .elf,.bat,.php,.asp etc. So in this example, we are selection option 5 which is .php Backdoor.
In the below screenshot, you can see that our payload.php is ready and saved in a specific path. Now to perform an attack you can send this payload to the victim and ask him to execute it.
In the below Screenshot, you can see that we have displayed the contents or the coding of payload.php, in which LHOST and Port Number is specified.
Example 2: Create Fud 100% Backdoor with Fudwin 1.0.
We will Create Fud Backdoor using Fudwin 1.0. So we have selected Option 2 from the menu.
In the below Screenshot, you can see that there are 2 primary options.
Slow but Powerfull
So we have selected option 1 which seems to be NEW.
In the below Screenshot, we have to specify the name of our payload and the Architecture of our Target System, so in this example we have selected 64Bit (XP64,Vista,7,8,10).
Now, we have to select the icon name in which payload will hide. So we have selected excel.ico.
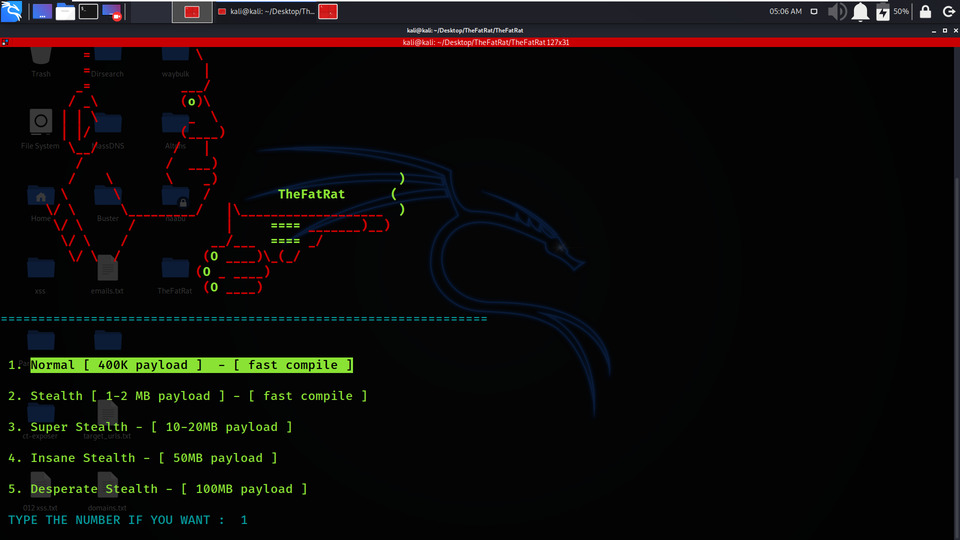
Example 3: Create Fud Backdoor with Avoid v1.2
We will be Creating a backdoor with Avoid Utility.
We are specifying backdoor name which is backdoor.exe
We have to select the strength or the size of the payload so in this example we have selected Normal payload stealth.
Selecting Payload Stealth
In the below Screenshot , you can see that our Payload is successfully created with the name backdoor.exe in the specified path.
Example 4: Create Fud Backdoor 1000% with PwnWinds [Excelent]
We will create backdoor using PwnWinds Utility which is more powerful among others.
You can see that there is the various option of backdoor type, so in this example, we are creating a .bat extension payload which is a batch script in Windows Target.
Now, we are specifying the name for the payload and selecting the purpose of the payload. So in this case the payload is designed to give reverse tcp connection to the attacker.
You can see that, our payload is created and saved in the specified path.
Example 5: Trojan Debian Package For Remote Acces [Trodebi]
We are Creating Trojan Package for Remote Access.
In the below Screenshot, we have specified the name of the Trojan and the pah of the Debian package in which Trojan will be merged or hide. So in this case we have selected the google_chrome Debian package.
In the below Screenshot, we are specifying the purpose of the Trojan, so in this example, we have selected shell_reverse_tcp connection.
In the below Screenshot, you can see that our Trojan have integrated with the .deb package and stored in the specified path.
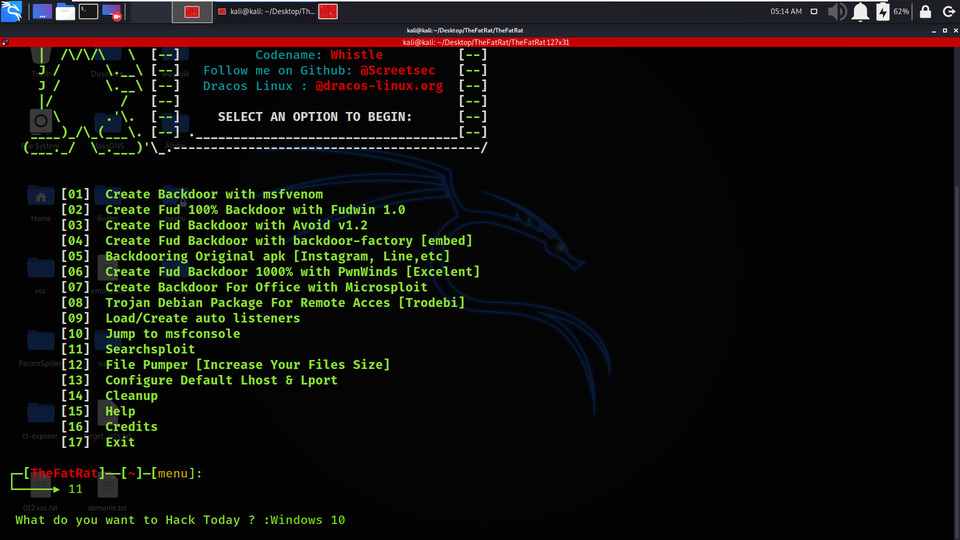
Example 6: Searchsploit
We will be using the SearchSploit option which consists of a list od databases of various payloads and backdoors for every type of target.
In the below Screenshot, Tool is asking us about our Target. So we have given Windows 10 as our target.
You can see that TheFatRat tool has returned us a number of payloads and backdoors for our Windows 10 Target.
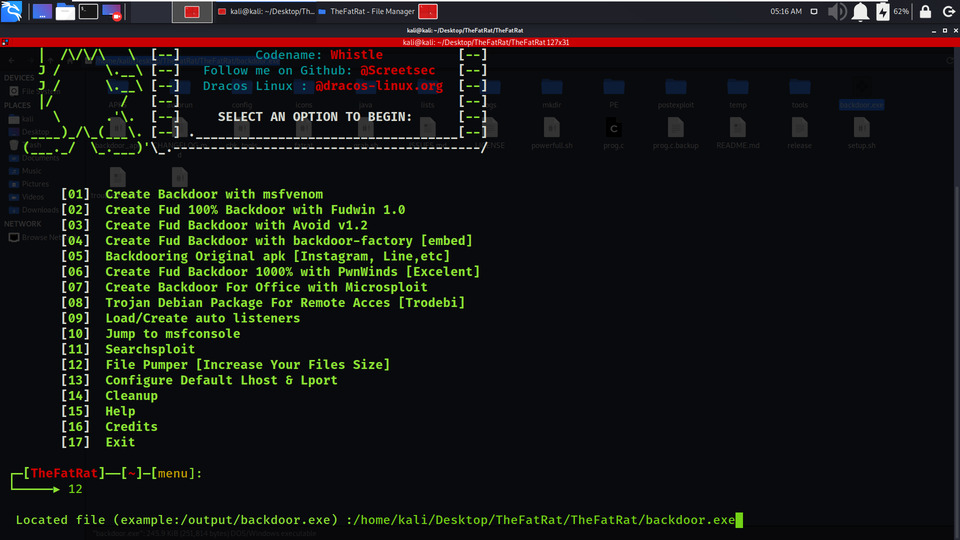
Example 7: File Pumper [Increase Your Files Size]
We will be increasing the size of our payload to make it more stealth.
In the below Screenshot, we have selected the backdoor for which we need to increase the size. Also we need to select the size in mb or kb. So we have selected size in mb.
In the below Screenshot, we have selected the size in mb.
Источник
Thefatrat kali linux install
#TheFatRat ( Unit for bypass av )
##Update: Version 1.6 ##Codename: Tasty
What is TheFatRat ??
An easy tool to generate backdoor with msfvenom (a part from metasploit framework). This tool compiles a malware with popular payload and then the compiled malware can be execute on windows, android, mac . The malware that created with this tool also have an ability to bypass most AV software protection
#Screenshot 



Checks for metasploit service and starts if not present
Easily craft meterpreter reverse_tcp payloads for Windows, Linux, Android and Mac and another
Start multiple meterpreter reverse_tcp listners
Fast Search in searchsploit
Create backdoor with another techniq
Autorunscript for listeners ( easy to use )
Drop into Msfconsole
Some other fun stuff 🙂
- Autorun work if the victim disabled uac ( user acces control ) or low uac ( WINDOWS )
- What is uac ? you can visit ( http://www.digitalcitizen.life/uac-why-you-should-never-turn-it-off )
- I have also created 3 AutoRun files
- Simply copy these files to a CD or USB
- You can change the icon autorun file or exe in folder icon ( replace your another ico and replace name with autorun.ico )
#HOW CHANGE THE ICONS ?
- Copy your icon picture to folder /TheFatrat/icons
- Change the name into autorun.ico
- And Replace
- Done
Be sure to check out the [Changelog] and Read CHANGELOG.md
- git clone https://github.com/Screetsec/TheFatRat.git
- cd TehFatrat/Setup
- chmod +x setup.sh && ./setup.sh
- Extract The lalin-master to your home or another folder
- chmod +x fatrat
- chmod +x powerfull.sh
- And run the tools ( ./fatrat )
- Easy to Use just input your number
A linux operating system. We recommend Kali Linux 2 or Kali 2016.1 rolling / Cyborg / Parrot / Dracos / BackTrack / Backbox / and another operating system ( linux )
Must install metasploit framework
- if prog.c file to large when create backdoor with powerfull.sh , you can use prog.c.backup and create another backup when you running option 2
Credits
- Thanks to allah and Screetsec [ Edo -maland- ]
- Dracos Linux from Scratch Indonesia ( Penetration os ) Thanksyou , you can see in http://dracos-linux.org/
- Offensive Security for the awesome OS ( http://www.offensive-security.com/ )
- http://www.kali.org/»
- Jack Wilder admin in http://www.linuxsec.org
- And another open sources tool in github
- Uptodate new tools hacking visit http://www.kitploit.com
Note: modifications, changes, or alterations to this sourcecode is acceptable, however,any public releases utilizing this code must be approved by writen this tool ( Edo -m- ).
About
An easy tool to generate backdoor with msfvenom (a part from metasploit framework). This tool compiles a malware with popular payload and then the compiled malware can be execute on windows, android, mac . The malware that created with this tool also have an ability to bypass most AV software protection
Источник
Thefatrat kali linux install






A Massive Exploiting Tool
TheFatRat is an exploiting tool which compiles a malware with famous payload, and then the compiled maware can be executed on Linux , Windows , Mac and Android. TheFatRat Provides An Easy way to create Backdoors and Payload which can bypass most anti-virus.
This tool is for educational purpose only, usage of TheFatRat for attacking targets without prior mutual consent is illegal. Developers assume no liability and are not responsible for any misuse or damage cause by this program.
- Fully Automating MSFvenom & Metasploit.
- Local or remote listener Generation.
- Easily Make Backdoor by category Operating System.
- Generate payloads in Various formats.
- Bypass anti-virus backdoors.
- File pumper that you can use for increasing the size of your files.
- The ability to detect external IP & Interface address .
- Automatically creates AutoRun files for USB / CDROM exploitation
But it’s shit! And your implementation sucks!
- Yes, you’re probably correct. Feel free to «Not use it» and there is a pull button to «Make it better».
Instructions on how to install TheFatRat
Troubleshoot on TheFatRat
chk_tools script to use in case of problems in setup.sh of fatrat this script will check if everything is in the right version to run fatrat and will also provide you a solution for the problem
- Documentation Available in Modules CEH v9 and V10 , Download source here
- CEHv10 Module 06 System Hacking.pdf
- CEHv10 Module 17 Hacking Mobile Platforms.pdf
- Published in International Journal of Cyber-Security and Digital Forensics
- Malware Analysis Of Backdoor Creator : TheFatRat
- Youtube Videos
- How To Download & Install TheFatRat
- TheFatRat 1.9.6 — Trodebi ( Embed Trojan into Debian Package )
- hacking windows 10 with TheFatRat
- Hacking Windows using TheFatRat + Apache2 Server + Ettercap + Metasploit
- Hacking with a Microsoft Office Word Document from TheFatRat
- XSS to powershell attack and bypass Antivirus using BeEF + TheFatRat + Metasploit
- TheFatRat — Hacking Over WAN — Embedding Payload in Original Android APK — Without Port Forwarding
- How To Automatically Embed Payloads In APK’s — Evil-Droid, Thefatrat & Apkinjector
- Bind FUD Payload with JPG and Hack over WAN with TheFatRat
All notable changes to this project will be documented in this file.
- Read the document before making an issue
Alternative Best Tool — Generating Backdoor & Bypass
- Veil-Framework /Veil — Veil Framework
- Shellter — Shellter AV Evasion Artware
- Unicorn — Trustedsec
- MSFvenom Payload Creator (MSFPC) — g0tmi1k
- Venom — Pedro Ubuntu
- Phantom-Evasion — Diego Cornacchini
- Offensive Security — Offensive Security
- dracOs Linux — Penetration Testing OS From Indonesia
- peterpt — Maintainer & Contributor
- Dana James Traversie — backdoor_apk
- z0noxz — Powerstager
- TrustedSec — Unicorn
- Raphael Mudge — External Source
- astr0baby — Reference Source
- NgeSEC Community
- Gauli(dot)Net — Lab Penetration
TheFatRat is made with 🖤 by Edo Maland & All Contributors. See the License file for more details.
About
Thefatrat a massive exploiting tool : Easy tool to generate backdoor and easy tool to post exploitation attack like browser attack and etc . This tool compiles a malware with popular payload and then the compiled malware can be execute on windows, android, mac . The malware that created with this tool also have an ability to bypass most AV softw…
Источник