- User Name Formats
- User Principal Name
- Down-Level Logon Name
- Changing Domain Users’ ‘User Logon Names’ and UPN’s
- Problem
- В Solution
- Adding A New UPN Suffix
- The Effect of Changing a User Logon Name
- How Does Changing a User Logon NameВ Affect Profile and Home Drive Paths?
- Does the User Have to Change their Logon Name?
- Whats the Point of a UPN Then?
- Some Users Don’t Have UPN’s?
- So Nothing Broke?
- Remove Spaces From User Logon Names
- Change UPN Suffix For All Users Script
- User Naming Attributes
- userPrincipalName
- UPN Format
- UPN Management
- objectGUID
- sAMAccountName
- objectSid
- sIDHistory
- Windows: Автоматический вход в систему (автологин)
- Использование control userpasswords2
- Использование программы Autologon
- Настройка через реестр
User Name Formats
When an application uses the Credentials Management API to prompt for credentials, the user is expected to enter information that can be validated, either by the operating system or by the application. The user can specify domain credentials information in one of the following formats:
User Principal Name
User principal name (UPN) format is used to specify an Internet-style name, such as UserName@Example.Microsoft.com. The following table summarizes the parts of a UPN.
| Part | Example |
|---|---|
| User account name. Also known as the logon name. | UserName |
| Separator. A character literal, the at sign (@). | @ |
| UPN suffix. Also known as the domain name. | Example.Microsoft.com |
A UPN can be implicitly or explicitly defined. An implicit UPN is of the form UserName@DNSDomainName.com. An implicit UPN is always associated with the user’s account, even if an explicit UPN is not defined. An explicit UPN is of the form Name@Suffix, where both the name and suffix strings are explicitly defined by the administrator.
Down-Level Logon Name
The down-level logon name format is used to specify a domain and a user account in that domain, for example, DOMAIN\UserName. The following table summarizes the parts of a down-level logon name.
Changing Domain Users’ ‘User Logon Names’ and UPN’s
KB ID 0001238
Problem
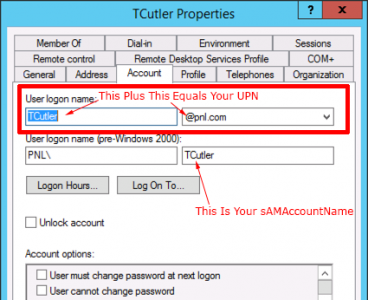
Changing a users UPN suffix is easyВ (as long as it’s been added – see below). There is some confusion about the User Login Name though.
A few weeks ago I had a client that needed this done, (for an office 365 migration). But they had the added problem that some of their User Logon Names had spaces in them, they were in first-name
What would happen if I changed their user logon names? Would they have to use a different logon name? Would their profile break? Or worse still, would they all lose their roaming profiles?
В Solution
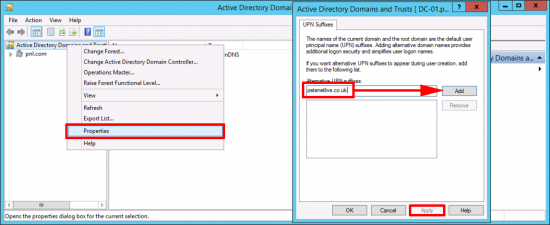
Adding A New UPN Suffix
Before you can add a new UPN suffix you need to make it available in the domain. Administrative Tools > Active Directory Domains and Trusts > Right Click ‘Active Directory Domains and Trusts’ В > Properties > Add the new Suffix В >Apply > OK.
From this point forward you can add that as a new suffix for any/all users.
The Effect of Changing a User Logon Name
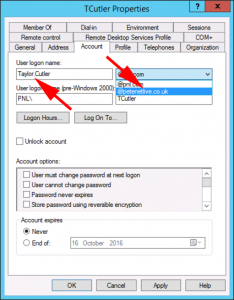
Using the same user as above, I’ve changed the ‘User Logon Name’, and added the new UPN Suffix to test.
How Does Changing a User Logon NameВ Affect Profile and Home Drive Paths?
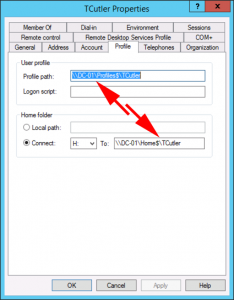
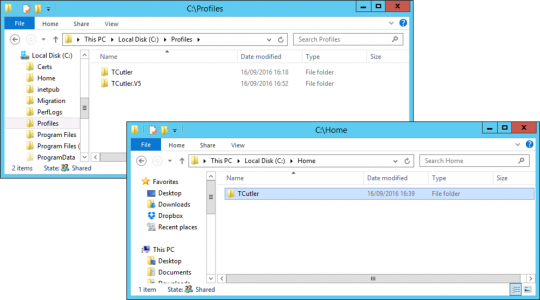
Put simply it does not! To prove it I did some testing. The profile and home drive path of this user’s is set on the ‘profile’ tab of their user object.
It remains the same after the User Logon Name changes. When these users were setup the profile paths and home drive paths were all set ‘on mass’, by selecting multiple users and setting the path to \\server-name\folder-name\%username% and it fills in all the ‘usernames‘ with the sAMAccountName and that has not changed.
Does the User Have to Change their Logon Name?
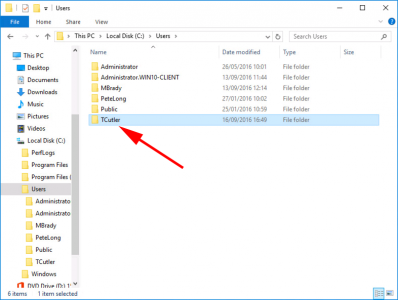
Confusingly users don’t log on with their User Logon Name (Usually, but they can if they wanted to) from all the way back to NT4 we have logged on with the DOMAIN-NAME\USER-NAME format which uses the sAMAccountName, NOT the User Logon Name. If you look at the very first picture at the top of the page you can see that below the UPN. Its called the User name (pre-Windows 2000). You may not of even have noticed, but on Windows 10 they put this right in your face on the logon screen.
Whats the Point of a UPN Then?
You can actually authenticate, and log on with your UPN, (see below)
This logs on as the user in the example above with the correct profile, and group membership etc. Though it’s not common practice to logon with a UPN. Microsoft Now Have a Very BAD HABIT of telling users, (and putting in their documentation), to ‘Log on with your Email Address‘ This is wrong, you actually are logging on with your UPN, Microsoft are making the assumption, that your Email and UPN are the same. This is why blogs and forums are full of scripts to change your UPN so that it matchesВ your email address. They assume, (usually quite rightly, that if you tell users to log on with their UPN they will be confused and not know what that is). So rather than address this problem, they tell users to log on with their Email addresses. That’s the real reason we are talking about changing UPN’s, and probably why your here in the first place.
Some Users Don’t Have UPN’s?
This is normal, don’t panic, a user does not have to have a UPN, if you are seeing blank entries that user was probably migrated via a script or tool into your AD, or simply was migrated from an older version of AD as part of a domain upgrade.
So Nothing Broke?
No, the local cached copy of the profile is still named the same as the sAMAccountName;
And the roaming profile and home drive also stayed the same;
WARNING: Just so I don’t do the same thing Microsoft did and ‘Make an Assumption’. Where changing the User Logon Names would affect you is if users were already logging into their machines with their UPN, Then they would need to change their login names to the new UPN, (or use the pre-Windows 2000 login name). But I’ve never seen a user logon with a UPN, the only time I’ve ever logged onto something with a UPN, is when I can’t type a back slash to log on as DOMAIN\Username (I use a Mac).В
Remove Spaces From User Logon Names
Seriously who does this? I don’t even like spaces in folder names! Below is a PowerShell script that will search through AD and find users with a space in the middle of their logon name and replace the login name with firstname.lastname
Change the values in red.
Note: If you have users with spaces in their GivenName or Surname attributes in AD this wont work, i.e if AD thinks a users first name is Juan Carlos, and the Surname is Rodriquez, then it would change the user logon name to ‘Juan Carlos.Rodriquez’ which is the very problem we are trying to fix! Also the first nameВ and surname fields in AD have to have properties in them as well, or you will see red errors.
Change UPN Suffix For All Users Script
In the script below I’ve targeted a specific OU, but you can change the $ou parameter to point at the root of the domain, and do all users at once if you wish. Change the values in red to suit your domain.
User Naming Attributes
User naming attributes identify user objects, such as logon names and IDs used for security purposes. The cn, name, and distinguishedName attributes are examples of user naming attributes. A user object is a security principal object, so it also includes the following user naming attributes:
- userPrincipalName — the logon name for the user
- objectGUID — the unique identifier of a user
- sAMAccountName — a logon name that supports previous version of Windows
- objectSid — security identifier (SID) of the user
- sIDHistory — the previous SIDs for the user object
You can view and manage these attributes using the Active Directory User and Computers MMC snap-in, which is available in the Remote Server Administration Tools (RSAT).
userPrincipalName
The userPrincipalName attribute is the logon name for the user. The attribute consists of a user principal name (UPN), which is the most common logon name for Windows users. Users typically use their UPN to log on to a domain. This attribute is an indexed string that is single-valued.
A UPN is an Internet-style login name for a user based on the Internet standard RFC 822. The UPN is shorter than a distinguished name and easier to remember. By convention, this should map to the user’s email name. The point of the UPN is to consolidate the email and logon namespaces so that the user only needs to remember a single name.
UPN Format
A UPN consists of a UPN prefix (the user account name) and a UPN suffix (a DNS domain name). The prefix is joined with the suffix using the «@» symbol. For example, «someone@ example.com». A UPN must be unique among all security principal objects within a directory forest. This means the prefix of a UPN can be reused, just not with the same suffix.
A UPN suffix has the following restrictions:
- It must be the DNS name of a domain, but does not need to be the name of the domain that contains the user.
- It must be the name of a domain in the current domain forest, or an alternate name listed in the upnSuffixes attribute of the Partitions container within the Configuration container.
UPN Management
A UPN can be assigned, but is not required, when a user account is created. When a UPN is created, it is unaffected by changes to other attributes of the user object such as the user being renamed or moved. This allows the user to keep the same login name if a directory is restructured. However, an administrator can change a UPN. When you create a new user object, you should check the local domain and the global catalog for the proposed name to ensure it does not already exist.
When a user uses a UPN to log on to a domain, the UPN is validated by searching the local domain and then the global catalog. If the UPN is not found in the global catalog, the logon attempt fails.
objectGUID
The objectGUID attribute is the unique identifier of a user. The attribute is a single-valued 128-bit Globally Unique Identifier (GUID), and is stored as an ADS_OCTET_STRING structure. The GUID is created by the Active Directory server when a user object is created.
Because an object’s distinguished name changes if the object is renamed or moved, the distinguished name is not a reliable identifier of an object. In Active Directory Domain Services, an object’s objectGUID attribute never changes, even if the object is renamed or moved. You can retrieve the string form of the objectGUID using the GUID property method in IADs Property Methods.
sAMAccountName
The sAMAccountName attribute is a logon name used to support clients and servers from previous version of Windows, such as Windows NT 4.0, Windows 95, Windows 98, and LAN Manager. The logon name must be 20 or fewer characters and be unique among all security principal objects within the domain.
objectSid
The objectSid attribute is the security identifier (SID) of the user. The SID is used by the system to identify a user and their group memberships during interactions with Windows security. The attribute is single-valued. The SID is a unique binary value used to identify the user as a security principal.
The SID is set by the system when the user is created. Each user has a unique SID issued by a Windows domain and stored in the objectSid attribute of the user object in the directory. Each time a user logs on, the system retrieves the user’s SID from the directory and places it in the user’s access token. The user’s SID is also used to retrieve the SIDs for the groups of which the user is a member and places them in the user’s access token. When a SID has been used as the unique identifier for a user or group, it cannot be used again to identify another user or group.
sIDHistory
The sIDHistory attribute contains the previous SIDs for the user object. This is a multi-valued attribute. A user object has previous SIDs if the user was moved to another domain. Whenever a user object is moved to a new domain, a new SID is created and assigned the objectSid attribute, and the previous SID is added to the sIDHistory attribute.
Windows: Автоматический вход в систему (автологин)
В данной статье пойдет речь о том, как настроить автологин (автоматический вход в систему без ввода пароля) на операционных системах Windows. Это бывает полезно, когда нет необходимости в ограничении доступа к компьютеру/ноутбуку, чтобы не тратить время на ввод пароля каждый раз при его включении.
Использование control userpasswords2
Это один из самых простых способов настройки автологина в системе, с использованием стандартных средств Windows, т. е. не требующий скачивания и установки никаких сторонних программ. Воспользоваться им можно следующим образом:
- Сперва нужно открыть окно программы «Выполнить». Сделать это можно следующим образом:
- В старых версиях Windows достаточно нажать левой кнопкой мыши по меню Пуск, и там выбрать пункт меню «Выполнить«.
- В Windows 8 или Windows 10 можно нажать правой кнопкой мыши на меню Пуск (или зажать поочередно клавиши Win + X ), и в появившемся меню выбрать «Выполнить».
- Поочередно зажать клавиши Win + R .
- В появившемся окне вводите команду control userpasswords2 , после чего нажимаете ОК.
- В появившемся окне убираете галочку с «Требовать ввод имени пользователя и пароля» и нажимаете ОК.


Использование программы Autologon
Другим простым методом для настройки автоматического логина в систему является использование программы Autologon, за авторством Марка Руссиновича (Mark Russinovich) — сотрудника Microsoft. Скачать её можно с сайта Microsoft по этой ссылке.
Использование программы максимально просто — нужно запустить скачанную программу (установка не требуется, но при первом запуске придется принять условия пользования), и ввести все нужные вам данные.
В поле Username следует написать имя пользователя, если пользователь принадлежит домену Active Directory, то следует указать его имя в поле Domain. Ну и наконец в поле Password следует ввести свой пароль. После этого для включения нужно всего-лишь нажать кнопку «Enable«, и после этого автовход в систему будет настроен.
Настройка через реестр
Так же существует способ настроить автоматический вход в систему через реестр.
Для включения автологина в реестре, вам нужно открыть меню Пуск, и выбрать команду Выполнить (либо нажать комбинацию клавиш Win+R). В появившемся окне нужно набрать regedit и нажать ОК.
Далее ищем ветку реестра HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon, и у следующих параметров вводим следующие значения:
AutoAdminLogon — Ставим единицу, иначе автоматический логин не будет срабатывать.
ForceAutoLogon — Если мы хотим, чтобы пользователя «насильно» логинило обратно в систему, то ставим единицу.
DefaultUserName — Имя пользователя, под которым мы хотим автоматически входить в систему.
DefaultPassword — Пароль пользователя, под которым мы хотим автоматически входить в систему. Скорее всего данный параметр будет отсутствовать, и поэтому придется создать его самому. Для этого нажимаем на пустом месте правой кнопкой мыши и выбираем пункт Создать — Строковый параметр, и присваиваем ему имя DefaultPassword.

DefaultDomainName — Домен пользователя, под которым мы хотим автоматически входить в систему. Если домен не используется — оставляем пустым.
Теперь можно закрыть редактор реестра, и попробовать перезагрузить компьютер. Если вы все сделали правильно, то сразу после загрузки операционной системы произойдет автоматический вход в систему под нужным пользователем.