- Digital signatures and certificates
- What do you want to do?
- What is a digital signature?
- Signing certificate and certificate authority
- Digital signature assurances
- Digital Signatures
- Obtain a digital certificate and create a digital signature
- What is a digital signature?
- Get a digital signature from a certificate authority or a Microsoft partner
- Create a digital certificate to digitally sign a document immediately
- How can I get my own digital signature?
- Get a digital signature from a Microsoft partner
- Create your own digital signature
- Digital Signatures and PnP Device Installation (Windows Vista and Later)
Digital signatures and certificates
More and more people and organizations are using digital documents instead of paper documents to conduct day-to-day transactions. By reducing dependency on paper documents, we are protecting the environment and saving the planet’s resources. Digital signatures support this change by providing assurances about the validity and authenticity of a digital document.
What do you want to do?
What is a digital signature?
A digital signature is an electronic, encrypted, stamp of authentication on digital information such as email messages, macros, or electronic documents. A signature confirms that the information originated from the signer and has not been altered.
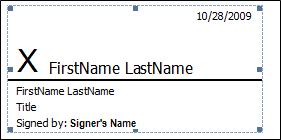
The following is an example of a signature line.
Signing certificate and certificate authority
Signing certificate To create a digital signature, you need a signing certificate, which proves identity. When you send a digitally-signed macro or document, you also send your certificate and public key. Certificates are issued by a certification authority, and like a driver’s license, can be revoked. A certificate is usually valid for a year, after which, the signer must renew, or get a new, signing certificate to establish identity.
Note: You can learn more about public and private keys in this article.
Certificate authority (CA) A certificate authority is an entity similar to a notary public. It issues digital certificates, signs certificates to verify their validity and tracks which certificates have been revoked or have expired.
Digital signature assurances
The following terms and definitions show what assurances are provided by digital signatures.
Authenticity The signer is confirmed as the signer.
Integrity The content has not been changed or tampered with since it was digitally signed.
Non-repudiation Proves to all parties the origin of the signed content. Repudiation refers to the act of a signer denying any association with the signed content.
Notarization Signatures in Microsoft Word, Microsoft Excel, or Microsoft PowerPoint files, which are time stamped by a secure time-stamp server, under certain circumstances, have the validity of a notarization.
To make these assurances, the content creator must digitally sign the content by using a signature that satisfies the following criteria:
The digital signature is valid.
The certificate associated with the digital signature is current (not expired).
The signing person or organization, known as the publisher, is trusted.
Important: Signed documents, which have a valid time stamp, are considered to have valid signatures, regardless of the age of the signing certificate.
The certificate associated with the digital signature is issued to the signing publisher by a reputable certificate authority (CA).
Digital Signatures
Digital signatures are based on Microsoft public key infrastructure technology, which is based on Microsoft Authenticode combined with an infrastructure of trusted certification authorities (CAs). Authenticode, which is based on industry standards, allows vendors, or software publishers, to sign either a file or a collection of files (such as a driver package) by using a code-signing digital certificate that is issued by a CA.
Windows uses a valid digital signature to verify the following:
The file, or the collection of files, is signed.
The signer is trusted.
The certification authority that authenticated the signer is trusted.
The collection of files was not altered after it was published.
For example, this signing process for a driver package involves the following:
A publisher obtains an X.509 digital certificate from a CA. An Authenticode certificate is also referred to as a signing certificate. A signing certificate is a set of data that identifies a publisher, and is issued by a CA only after the CA has verified the identity of the publisher. A CA can be a Microsoft CA, a third-party commercial CA, or an Enterprise CA.
The signing certificate is used to sign the catalog file of a driver package or to embed a signature in a driver file. Certificates that identify trusted publishers and trusted CAs are installed in certificate stores that are maintained by Windows.
The signing certificate includes a private key and a public key, which is known as the key pair. The private key is used to sign the catalog file of a driver package or to embed a signature in a driver file. The public key is used to verify the signature of a driver package’s catalog file or a signature that is embedded in a driver file.
To sign a catalog file or to embed a signature in a file, the signing process first generates a cryptographic hash, or thumbprint, of the file. The signing process then encrypts the file thumbprint with a private key and adds the thumbprint to the file.
The signing process also adds information about the publisher and the CA that issued the signing certificate. The digital signature is added to the file in a section of the file that is not processed when the file thumbprint is generated.
To verify the digital signature of a file, Windows extracts the information about the publisher and the CA and uses the public key to decrypt the encrypted file thumbprint.
Windows accepts the integrity of the file and the authenticity of the publisher only if the following are true:
- The decrypted thumbprint matches the thumbprint of the file.
- The certificate of the publisher is installed in the Trusted Publishers certificate store.
- The root certificate of the CA that issued the publisher’s certificate is installed in the Trusted Root Certification Authorities certificate store.
For more information about how the Plug and Play (PnP) device installation uses the digital signature of a driver package’sВ catalog file, see Digital Signatures and PnP Device Installation.
For more information about Microsoft public key infrastructure technology, code signing, and digital signatures, see Introduction to Code Signing and Code Signing Best Practices.
Obtain a digital certificate and create a digital signature
This article explains how you can get or create a digital signature for use in Office documents. To learn more about how to use them in Office documents, see Add or remove a digital signature in Office files.
What is a digital signature?
A digital signature or ID is more commonly known as a digital certificate. To digitally sign an Office document, you must have a current (not expired) digital certificate. Digital certificates are typically issued by a certificate authority (CA), which is a trusted third-party entity that issues digital certificates for use by other parties. There are many commercial third-party certificate authorities from which you can either purchase a digital certificate or obtain a free digital certificate. Many institutions, governments, and corporations can also issue their own certificates.
A digital certificate is necessary for a digital signature because it provides the public key that can be used to validate the private key that is associated with a digital signature. Digital certificates make it possible for digital signatures to be used as a way to authenticate digital information.
Get a digital signature from a certificate authority or a Microsoft partner
If you plan to exchange digitally-signed documents together with other people, and you want the recipients of your documents to be able to verify the authenticity of your digital signature, you can obtain a digital certificate from a reputable third-party certificate authority (CA). For more information, see Find digital ID or digital signature services.
Create a digital certificate to digitally sign a document immediately
If you do not want to purchase a digital certificate from a third-party certificate authority (CA), or if you want to digitally sign your document immediately, you can create your own digital certificate.
- What version of Windows are you using?
- Windows 10
- Windows 8
- Windows 7, Windows Vista, or Windows XP
Go to C:\Program Files (x86)\Microsoft Office\root\ (or C:\Program Files\Microsoft Office\root\Office16 if you’re running the 64-bit version of Office)
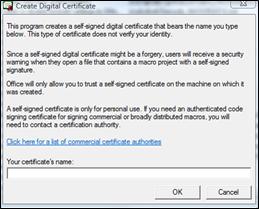
Click SelfCert.exe. The Create Digital Certificate box appears.
In the Your certificate’s name box, type a descriptive name for the certificate.
When the SelfCert Success message appears, click OK.
Go to C:\Program Files\Microsoft Office\ \.
Click SelfCert.exe. The Create Digital Certificate box appears.
In the Your certificate’s name box, type a descriptive name for the certificate.
When the SelfCert Success message appears, click OK.
Click Start, point to All Programs, click Microsoft Office, click Microsoft Office Tools, and then click Digital Certificate for VBA Projects. The Create Digital Certificate box appears.
In the Your certificate’s name box, type a descriptive name for the certificate.
When the SelfCert Success message appears, click OK.
To view the certificate in the Personal Certificates store, do the following:
Open Internet Explorer.
On the Tools menu, click Internet Options, and then click the Content tab.
Click Certificates, and then click the Personal tab.
Important: If you digitally sign a document by using a digital certificate that you created, and then you share the digitally-signed file, other people cannot verify the authenticity of your digital signature without manually deciding to trust your self-signed certificate.
How can I get my own digital signature?
If you try to digitally sign an Office 2007 document without a digital certificate, the Get a Digital ID dialog box appears, and you are asked to select how you want to get your own digital signature.
You have two options for getting a digital signature:
To learn more about each option, see the following sections.
Get a digital signature from a Microsoft partner
If you select the option Get a digital ID from a Microsoft partner in the Get a Digital ID dialog box, you are redirected to the Microsoft Office website, where you can purchase a digital certificate from one of the third-party certificate authorities (CAs).
If you plan to exchange digitally signed documents with other people, and you want the recipients of your documents to be able to verify the authenticity of your digital signature, it is a good idea to obtain a digital certificate from a reputable third-party certificate authority (CA).
Create your own digital signature
If you do not want to purchase a digital certificate from a third-party certificate authority, or if you want to digitally sign your document immediately, you can create your own digital certificate by selecting the Create your own digital ID option in the Get a Digital ID dialog box.
To create your own digital certificate
In the Get a Digital ID dialog box, select Create your own digital ID.
Important: The Get a Digital ID dialog box appears only if you attempt to digitally sign a document without a digital certificate.
In the Create a Digital ID dialog box, type the following information to include in your digital signature:
In the Name box, type your name.
In the E-mail address box, type your e-mail address.
In the Organization box, type the name of your organization or company.
In the Location box, type your geographic location.
Note: If you digitally sign a document by using a digital certificate that you created, and then you share the digitally signed file, other people cannot verify the authenticity of your digital signature. Your digital signature can be authenticated only on the computer on which you created the digital signature.
Digital Signatures and PnP Device Installation (Windows Vista and Later)
On Windows Vista and later versions of Windows, Plug and Play (PnP) device installation uses the digital signature of a driver package’sВ catalog file to do the following:
Verify the identity of the publisher of the driver package. Windows uses the identity to allow users to choose whether to trust a driver’s publisher.
Determine whether the driver package was altered after it was published.
PnP device installation on Windows Vista and later versions of Windows support the following types of digital signatures for driver packages:
Signature types that can be used for drivers that are released to the general public:
Signatures generated by a Windows signing authority for:
- Inbox drivers
- Drivers certified and signed through the Windows Hardware Quality Labs (WHQL)
- Windows Sustained Engineering (SE) updates.
Signatures that are not generated by a Windows signing authority, but do comply with the following:
- The kernel-mode code signing policy for 64-bit versions of Windows Vista and later versions of Windows.
- The PnP device installation signing requirements for 32-bit and 64-bit versions of Windows Vista and later versions of Windows.
This type of signature is generated by using a Software Publisher Certificate (SPC) that is obtained from a third-party certification authority (CA) that is authorized by Microsoft to issue such certificates.
Signatures that are not generated by a Windows signing authority and do not comply with the kernel-mode code signing policy, but do comply with the PnP device installation signing requirements. This type of signature can be used to sign kernel-mode drivers for 32-bit versions of Windows Vista and later versions of Windows. This type of signature is generated by using a commercial release certificate that is obtained from a CA that is a member of the Microsoft Root Certificate Program.
Signatures for deploying drivers only within corporate network environments, which are created by a digital certificate that is created and managed by Enterprise CA. Detailed information about how to configure an Enterprise CA is outside the scope of this documentation.
For information about how to create an Enterprise CA, see the «Code Signing Best Practices» white paper on the Driver Signing Requirements for Windows website.
Signature types that can be used in-house during the development and test of drivers:
- Signatures generated by the WHQL test signature program
- Signatures generated by a MakeCert test certificate
- Signatures created by a commercial test certificate that is obtained from a CA that is a member of the Microsoft Root Certificate Program
- Signatures generated by an Enterprise CA test certificate
Windows Vista and later versions of Windows include the following features that provide support for signatures that are generated by third parties:
Administrators can control which driver publishers are trusted. Windows Vista and later versions of Windows installs drivers from trusted publishers without prompting. It never installs drivers from publishers that the administrator has chosen not to trust.
The driver-signing policy is always set to Warn. This eliminates the Ignore and Block options that were available in Windows Server 2003, Windows XP, and Windows 2000. An administrator must always authorize the installation of unsigned drivers or a driver from a publisher that is not yet trusted.
All device setup classes are treated equally. On Windows Server 2003, Windows XP, and Windows 2000, driver packages that were signed by WHQL must have an INF file that specifies a device setup class that is defined in %SystemRoot%/inf/Certclas.inf. Otherwise, Windows treats the driver package as unsigned.
Starting with Windows Vista, when there are several compatible drivers to choose from, the ranking algorithm that the operating system uses to select the best driver includes drivers that have third-party signatures.
This algorithm ranks drivers in the following way:
- If the AllSignersEqual group policy is disabled, the operating system ranks drivers that are signed with a Microsoft signature higher than drivers that are signed with a third-party signature. This ranking occurs even if a driver that is signed with a third-party signature is, in all other ways, a better match for a device.
- If the AllSignersEqual group policy is enabled, the operating system ranks all digitally signed drivers equally.
NoteВ В Starting with Windows 7, the AllSignersEqual group policy is enabled by default. In Windows Vista and Windows Server 2008, the AllSignersEqual group policy is disabled by default. IT departments can override the default ranking behavior by enabling or disabling the AllSignersEqual group policy.
Before installing a driver, Windows analyzes the driver package’s digital signature. If a signature is present, Windows uses the signature to validate the files in the driver package. Based on the results of this analysis, Windows categorizes the digital signature as follows:
Signed by a Windows signing authority. These drivers are either included in the default installation of Windows (inbox drivers), signed for release by WHQL, or signed by Windows SE.
Signed by a trusted publisher. These drivers have been signed by a third-party, and user has explicitly chosen to always trust signed drivers from this publisher.
Signed by an untrusted publisher. These drivers have been signed by a third-party, and the user has explicitly chosen to never trust drivers from this publisher.
Signed by a publisher of unknown trust. These drivers have been signed by a third-party, and the user has not indicated whether to trust this publisher.
Altered. These drivers are signed, but Windows has detected that at least one file in the driver package has been altered after the package was signed.
Unsigned. These drivers are either unsigned or have an invalid signature. Valid signatures must be created by using a certificate that was issued by a trusted CA.
Starting with Windows Vista, when the operating system installs a driver on a computer for the first time, it preinstalls, or stages, the driver in the driver store. To preinstall a driver, Windows copies the driver package to the driver store and saves a copy of the driver package’s INF file in the system INF directory. Windows subsequently will silently install a driver for a matching device by using the copy of the driver package in the driver store. User interaction is not required when Windows installs a preinstalled driver for a device.
Whether Windows will preinstall a driver package depends on the signature category, user credentials, and user interaction, as follows:
Signed by a Windows signing authority or a trusted publisher. Windows silently preinstalls the driver package for system administrators and standard users (users without administrator credentials). Windows does not display any user dialog boxes.
Signed by an untrusted publisher. Windows does not preinstall the driver package.
Signed by a publisher of unknown trust. Windows displays a dialog box to a system administrator that informs the administrator that the publisher of the driver package is not yet trusted. The dialog box provides the administrator the option to install the driver package and the option to always trust the publisher. Windows does not display a dialog box to a standard user and does not preinstall the driver package for the standard user.
Altered or unsigned. Windows displays a dialog box that appropriately warns a system administrator that the signature could not be verified. The dialog box provides the administrator the option to install or not to install the driver package. Windows does not display a dialog box to a standard user and does not preinstall the driver package for a standard user.
For more information about driver signatures and installation, see Signature Categories and Driver Installation.