- Block or Unblock Programs in Windows Defender Firewall
- You Might Also Like
- Reader Interactions
- Comments
- Did this help? Let us know! Cancel reply
- Primary Sidebar
- Recent Posts
- Who’s Behind Technipages?
- What Firewall Rule(s) Will Allow Windows Update and ONLY Windows Update To Work
- 2 Answers 2
- What blocks windows firewall updates
- Asked by:
- General discussion
- Windows Firewall is blocking Windows Update
- 6 Answers 6
Block or Unblock Programs in Windows Defender Firewall
By Mitch Bartlett 15 Comments
In Microsoft Windows 10 you can set the Windows Defender Firewall to block or unblock certain applications. Here’s how.
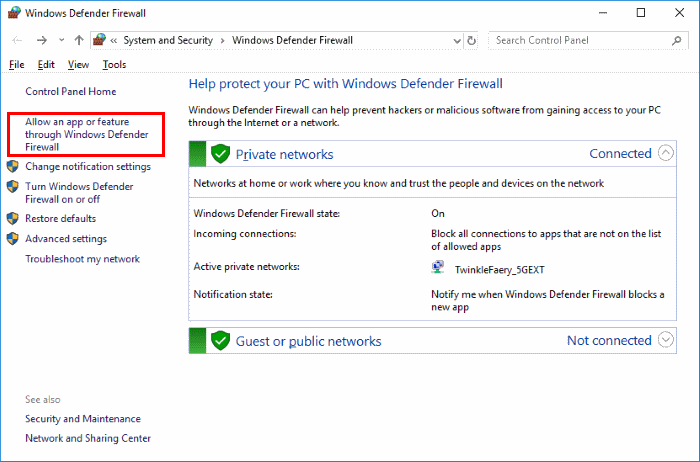
- Select the “Start” button, then type “firewall“.
- Select the “Windows Defender Firewall” option.
- Choose the “Allow an app or feature through Windows Defender Firewall” option in the left pane.
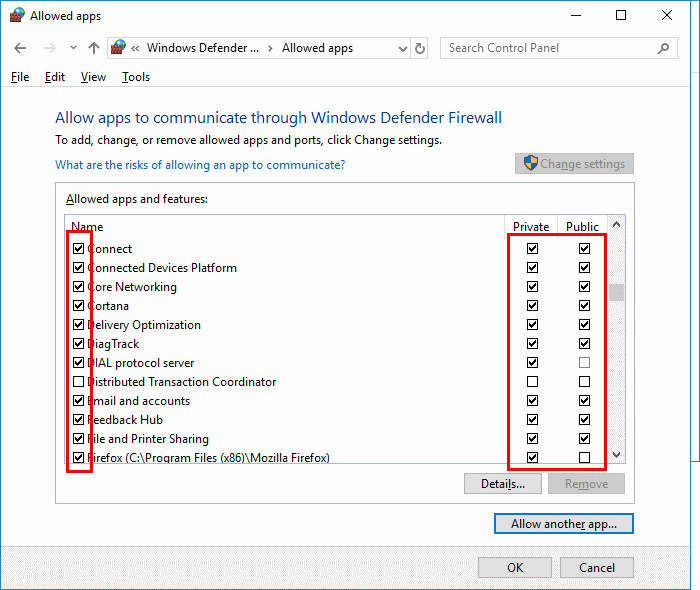
- Unchecking the box to the left of the application name disallows it from accessing network resources, while checking it allows access. You can also check the boxes to the right of the name labeled “Private” or “Public” to allow and disallow the app on private or public networks respectively.
- If the program you wish to block or unblock is not listed, you can click the “Allow another app…” button to add it. Choose the application in the list and select “Add“. If the program is not in this list, use the “Browse…” button to select the program file manually.
You Might Also Like
Filed Under: Windows Tagged With: Windows 10
Reader Interactions
Comments
Susan Olson says
No…I am definitely not a pro…so a little more explanation would be great…say, what about gallery or settings….?
Susan Olon says
Could you give me an example as to what applications should NOT cross the firewall??
Any application can block any crack microsoft office .. can you help me how to block any crack microsoft on my laptop ..
Richard Jordan says
The firewall is blocking access to open areas of the United Nations website. Even public press releases. How do I uninstall Micrsoft Edge, if that is what is blocking me.
So, what’s the meaning of a checked box and an unchecked box?
I am trying to allow zoom to have access but firewall is blocking it.
I’m trying to block Microsoft family features so it won’t send me the annoying pop-ups about signing in.
I’m on the correct thing but I can’t uncheck the box beside it. If I click the box it does nothing,
Do we have any registry settings for the same.
Thanks, it worked
What if when you click “Allow another app” and then Choose the app in the directory and it gives an error about a possible virus?
Josh Everett says
Is there any way to do this without Administrator rights?
Settings for some pro, doesn’t change!
its somehow locked, as if a registry rule is overriding this windows rules.
Richard S Nye says
I have been trying for hours to Block “Fortnite” from my PC windows 10
Edwin Wetzel says
nothing helps. i’ve been trying to hook up my wifi scanner and i’ve been doing this for hours without any success. i’ve followed all the different procedures on line including going into the defender advanced settings and allowing file and printer sharing rules and still does not work.
What if you cant click the “Allow the app or feature through windows defender firewall”?
Mike Bading says
Mitch,
First, I hope this note finds all well with you and yours.
Second, thank you for your effort here.
Third, my question(s):
What do you do when Windows Defender keeps resetting Microsoft Apps you have unchecked/deselected in Windows 10 Home or Windows 10 Pro?
Example: Let’s say I wish to block Cortana (or any other app). I then follow your instructions here and uncheck/deselect all the boxes pertaining to Cortana and then close the window.
Let’s say, that for whatever reason(s), I return to the window in your example only to find that Windows has reset/unblocked Cortana without notice and without my permission. This would happen all the time in Win10Home; and I would like to know if this would happen in Win10Pro and what to do about it if it does.
Respectfully,
Mike Bading
Did this help? Let us know! Cancel reply
This site uses Akismet to reduce spam. Learn how your comment data is processed.
Primary Sidebar
Recent Posts
Who’s Behind Technipages?

Follow me on Twitter, or visit my personal blog.
What Firewall Rule(s) Will Allow Windows Update and ONLY Windows Update To Work
What Firewall Rules Will Allow Windows Update and ONLY Windows Update to Work For Windows 8.1? If that is not possible please provide the minimum rules necessary and the names of the additional program(s)/service(s) that must be granted access.
2 Answers 2
I debugged this problem for hours. In the end, to get Windows Update through Windows firewall you must allow svchost. You cannot narrow the protocol, scope, application packages or services.
So I have 0 inbound firewall rules, and 3 outbound firewall rules two of which are active at any point in time. Those rules are:
WFC — Core Networking — Dynamic Host Configuration Protocol (DHCP-out)
AND Other applications that require internet (i.e., your web browser)
To connect to the internet, I must turn on 1 and 3. After I can turn off 1 and 3 and turn on 2. If my internet is on, and I want to use windows update, I then disable 2 and enable 1. That means after I have connected to the internet and don’t plan on using windows update that the only weakness in my firewall is my browser assuming I haven’t added any other exceptions.
So far it doesn’t look like windows firewall actually performs the functions it offers, blocking individual services under the umbrella of the svchost. Microsoft releases windows updates every second Tuesday of each month give or take 24 hours or so. You could create a script that automatically enables svchost out each month, and one for every day for defender updates; (for 5-10 minutes) or do it manually.
Or, you could for example block everything, enable packet logging, monitor the ip addresses and ports for every windows update server connection, then only allow svchost out for those specific ip addresses, this will narrow it down to only allow windows update. If you use cidr format replacing the last 3 digits with .1/24, you will be able to reach every ips on that subnet if they change over time. After hammering this out enough, should you notice other ip’s pop up outside that scope, you will over time know its not windows update. I am not sure how one can detect exactly what program/service is operating under the svchost umbrella other than triggering it manually.
For Windows Updates, use Group Policy «Delivery Optimization» Download Mode, set to 99, (meaning no P2P or cloud services, just microsofts servers alone; so you don’t get 1,000,000,000 different ips) Then you must create a blacklist for each ip that comes up through svchost that does not involve windows update.
Remote addresses: 65.55.163.1/24,13.74.179.1/24,191.232.139.1/24,20.36.222.1/24,20.42.23.1/24,191.232.139.2/24,20.36.218.1/24,95.101.0.1/24,95.101.1.1/24,13.78.168.1/24,93.184.221.1/24,13.83.184.1/24,13.107.4.1/24,13.83.148.1/24
This worked for me. [Using WFC a Windows Defender Firewall Front End GUI]
What blocks windows firewall updates
This forum has migrated to Microsoft Q&A. Visit Microsoft Q&A to post new questions.
Asked by:
General discussion
Can anyone kindly give me a Windows Firewall rule that allows Windows Update? Assume I’m running MMC’s «Windows Firewall with Advanced Security» snap-in as Administrator. Note that a «solution» that takes down the outbound firewall is not acceptable.
===== Solution =====
Suppose that, as the default, you’ve set the outbound firewall to block (see To close the outbound firewall, below). In order for Windows Update to check whether an update is available and then to download the update files, you first need an outbound firewall allow-rule that allows the Windows Update service to pass through the outbound firewall.
Prerequisite: Knowledge of the Microsoft Management Console (MMC) and its «Windows Firewall with Advanced Security» plug-in.
What you will do: You will use the «Windows Firewall with Advanced Security» MMC plug-in to create an outbound firewall rule that allows ‘%SystemRoot%\System32\svchost.exe’ (the generic service driver) to pass through the outbound firewall on behalf of ‘wuauserv’ (the name of the specific service that performs the update).
Warning: If you don’t know what I’m writing about, get help.
Name: Allow Windows Update (. or any name you prefer — it doesn’t matter)
Group:
Profile: Public
Enabled: Yes
Action: Allow
Program: %SystemRoot%\System32\svchost.exe
Local Address: Any
Remote Address: Any
Protocol: Any
Local Port: Any
Remote Port: Any
Allowed Computers: Any
Status: OK
Service: wuauserv
Rule Source: Local Setting
Interface Type: All interface types
Excepted Computers: None
Description:
To open the outbound firewall:
More accurate wording would be
Outbound connections are allowed unless explicitly blocked by a rule.
If you look at the standard rules you will find no block-rules. That means that nothing is blocked, everything is allowed, and the outbound firewall is wide open.
To close the outbound firewall:
More accurate wording would be
Outbound connections are blocked unless explicitly allowed by a rule.
If you look at the standard rules you will find only allow-rules that have been crafted to allow the vital Windows connections to pass through the outbound firewall. To an informed observer it’s obvious that the firewall engineers crafted these allow-rules so that users who closed the outbound firewall wouldn’t have to write them. But the firewall engineers left out Windows Update.
Windows Firewall is blocking Windows Update
I recently uninstalled ZoneAlarm and have decided to use Windows Firewall as my firewall as ZoneAlarm was causing me grief when I was syncing my iphone.
Anyway, I’ve noticed just then that Windows Firewall seems to block my Windows updates.
Whenever I have the firewall on, I get a 8024402C error when I try to update, and it seems to update fine when I don’t have the firewall on.
but it seems to assume that the firewall I have is third party, I’m not sure how to fix it if Windows Firewall itself is the firewall that is blocking the automatic updates.
6 Answers 6
I’ve found solution.
Essentially I added a new incoming rule which allowed all connections coming from c:\windows\System32\svchost.exe.
I wonder why my default settings didn’t already have this? Anyway it worked!
In Win 8 Go to Control Panel>Firewall>Advanced Settings. Then click Action>Export policy to make a copy of your current policy in case you want to restore it. Then click Action>New Rule>Custom>Next in the Program step of New Outbound Rule Wizard under the Service heading select Customize>Apply to this service>Windows Update>OK
Optional: Program: select «this program path» and select the program c:\windows\System32\svchost.exe press ok
Optional: Protocol and Ports: specify tcp port 443
Allow this connection; select your profile or leave as is (it should be explained in the wizard pretty well); give it a name; finish
Go to Control Panel>Firewall>Advanced Settings . Then click Action>Export policy to make a copy of your current policy in case you want to restore it. Then click Action>Restore Default Policy .
If it really is just the Firewall, this should allow you to use Windows Update.
Open Command Prompt as administrator and type the following commands, one by one (press ENTER after each command):
Try to install the updates again.
Here is how to change firewall settings in Windows 7, you can watch the video to learn the steps ;
Allow a program to communicate through Windows Firewall
By default, most programs are blocked by Windows Firewall to help make your computer more secure. To work properly, some programs might require you to allow them to communicate through the firewall.
Watch this video to learn how to allow a program to communicate through Windows Firewall (1:12)
Open Windows Firewall by clicking the Start button Picture of the Start button, and then clicking Control Panel. In the search box, type firewall, and then click Windows Firewall.
In the left pane, click Allow a program or feature through Windows Firewall.
Click Change settings. Administrator permission required If you’re prompted for an administrator password or confirmation, type the password or provide confirmation.
Select the check box next to the program you want to allow, select the network locations you want to allow communication on, and then click OK.
Warning Before allowing a program through the firewall, make sure you understand the risks involved. For more information, see What are the risks of allowing programs through a firewall?
In Windows 8 and 10, allowing the Windows Update service through the firewall is not enough. It appears to be because it uses a thread pool, but the security context is not correctly set on those threads, so they are not recognised by the firewall as being from Windows Update. (Link)
The solution that works for me was partially suggested by Uwe Bubeck on the Technet forums (Link):
- Create a link to svchost.exe , for example mysvchost.exe , by using the command mklink /H mysvchost.exe svchost.exe . To do this, you will need permissions on svchost.exe .
- Allow mysvchost through the firewall.
- Change the ImagePath for the Windows Update service in HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\wuauserv from svchost to mysvchost .
- Restart Windows Update to apply the change.
You can now find updates, but they will not download. - Add an exception for TCP/80 on svchost.exe (i.e. all services). Updates can now be downloaded.
Before allowing all services TCP port 80, I tried adding an exception for TrustedInstaller, moving BITS (background transfer) to mysvchost , and some other services suggested by others such as cryptographic services. In the end, I couldn’t find which service is responsible for downloading the updates, so I had to add an exception for all services. Downloading updates now works. If someone figures out the minimal set of changes, rather than a large whitelist for all services, please edit this answer (and maybe also post it to the technet threads).