Access Control Entries
An access control entry (ACE) is an element in an access control list (ACL). An ACL can have zero or more ACEs. Each ACE controls or monitors access to an object by a specified trustee. For information about adding, removing, or changing the ACEs in an object’s ACLs, see Modifying the ACLs of an Object in C++.
There are six types of ACEs, three of which are supported by all securable objects. The other three types are Object-specific ACEs supported by directory service objects.
All types of ACEs contain the following access control information:
- A security identifier (SID) that identifies the trustee to which the ACE applies.
- An access mask that specifies the access rights controlled by the ACE.
- A flag that indicates the type of ACE.
- A set of bit flags that determine whether child containers or objects can inherit the ACE from the primary object to which the ACL is attached.
The following table lists the three ACE types supported by all securable objects.
| Type | Description |
|---|---|
| Access-denied ACE | Used in a discretionary access control list (DACL) to deny access rights to a trustee. |
| Access-allowed ACE | Used in a DACL to allow access rights to a trustee. |
| System-audit ACE | Used in a system access control list (SACL) to generate an audit record when the trustee attempts to exercise the specified access rights. |
For a table of object-specific ACEs, see Object-specific ACEs.
System-alarm object ACEs are not currently supported.
ACL structure (winnt.h)
The ACL structure is the header of an access control list (ACL). A complete ACL consists of an ACL structure followed by an ordered list of zero or more access control entries (ACEs).
Syntax
Members
Specifies the revision level of the ACL. This value should be ACL_REVISION, unless the ACL contains an object-specific ACE, in which case this value must be ACL_REVISION_DS. All ACEs in an ACL must be at the same revision level.
Specifies a zero byte of padding that aligns the AclRevision member on a 16-bit boundary.
Specifies the size, in bytes, of the ACL. This value includes both the ACL structure and all the ACEs.
Specifies the number of ACEs stored in the ACL.
Specifies two zero-bytes of padding that align the ACL structure on a 32-bit boundary.
Remarks
An ACL includes a sequential list of zero or more ACEs. The individual ACEs in an ACL are numbered from 0 to n, where n+1 is the number of ACEs in the ACL. When editing an ACL, an application refers to an ACE within the ACL by the ACE’s index.
There are two types of ACL: discretionary and system.
A discretionary access control list (DACL) is controlled by the owner of an object or anyone granted WRITE_DAC access to the object. It specifies the access particular users and groups can have to an object. For example, the owner of a file can use a DACL to control which users and groups can and cannot have access to the file.
An object can also have system-level security information associated with it, in the form of a system access control list (SACL) controlled by a system administrator. A SACL allows the system administrator to audit any attempts to gain access to an object.
For a list of currently defined ACE structures, see ACE.
A fourth ACE structure, SYSTEM_ALARM_ACE, is not currently supported.
The ACL structure is to be treated as though it were opaque and applications are not to attempt to work with its members directly. To ensure that ACLs are semantically correct, applications can use the functions listed in the See Also section to create and manipulate ACLs.
Each ACL and ACE structure begins on a DWORD boundary.
The maximum size for an ACL, including its ACEs, is 64 KB.
Creating or Modifying an ACL
Windows supports a set of functions that create an access control list (ACL) or modify the access control entries (ACEs) in an existing ACL.
The SetEntriesInAcl function creates a new ACL. SetEntriesInAcl can specify a completely new set of ACEs for the ACL, or it can merge one or more new ACEs with the ACEs of an existing ACL. The SetEntriesInAcl function uses an array of EXPLICIT_ACCESS structures to specify the information for the new ACEs. Each EXPLICIT_ACCESS structure contains information that describes a single ACE. This information includes the access rights, the type of ACE, the flags that control ACE inheritance, and a TRUSTEE structure that identifies the trustee.
To add a new ACE to an existing ACL
- Use the GetSecurityInfo or GetNamedSecurityInfo function to get the existing DACL or SACL from an object’s security descriptor.
- For each new ACE, call the BuildExplicitAccessWithName function to fill an EXPLICIT_ACCESS structure with the information that describes the ACE.
- Call SetEntriesInAcl, specifying the existing ACL and an array of EXPLICIT_ACCESS structures for the new ACEs. The SetEntriesInAcl function allocates and initializes the ACL and its ACEs.
- Call the SetSecurityInfo or SetNamedSecurityInfo function to attach the new ACL to the object’s security descriptor.
If the caller specifies an existing ACL, SetEntriesInAcl merges the new ACE information with the existing ACEs in the ACL. Consider the case, for example, in which the existing ACL grants access to a specified trustee and an EXPLICIT_ACCESS structure denies access to the same trustee. In this case, SetEntriesInAcl adds a new access-denied ACE for the trustee and deletes or modifies the existing access-allowed ACE for the trustee.
For sample code that merges a new ACE into an existing ACL, see Modifying the ACLs of an Object in C++.
Access Control Lists
An access control list (ACL) is a list of access control entries (ACE). Each ACE in an ACL identifies a trustee and specifies the access rights allowed, denied, or audited for that trustee. The security descriptor for a securable object can contain two types of ACLs: a DACL and a SACL.
A discretionary access control list (DACL) identifies the trustees that are allowed or denied access to a securable object. When a process tries to access a securable object, the system checks the ACEs in the object’s DACL to determine whether to grant access to it. If the object does not have a DACL, the system grants full access to everyone. If the object’s DACL has no ACEs, the system denies all attempts to access the object because the DACL does not allow any access rights. The system checks the ACEs in sequence until it finds one or more ACEs that allow all the requested access rights, or until any of the requested access rights are denied. For more information, see How DACLs Control Access to an Object. For information about how to properly create a DACL, see Creating a DACL.
A system access control list (SACL) enables administrators to log attempts to access a secured object. Each ACE specifies the types of access attempts by a specified trustee that cause the system to generate a record in the security event log. An ACE in a SACL can generate audit records when an access attempt fails, when it succeeds, or both. For more information about SACLs, see Audit Generation and SACL Access Right.
Do not try to work directly with the contents of an ACL. To ensure that ACLs are semantically correct, use the appropriate functions to create and manipulate ACLs. For more information, see Getting Information from an ACL and Creating or Modifying an ACL.
ACLs also provide access control to Microsoft Active Directory directory service objects. Active Directory Service Interfaces (ADSI) include routines to create and modify the contents of these ACLs. For more information, see Controlling Access to Active Directory Objects.
What is ACL for Windows ?
ACL for Windows is a single, downloadable product that provides access to:
Access to each component is determined by your Galvanize subscription type.
What can I access using the ACL for Windows main screen?
Using ACL for Windows , you can:
- activate Analytics to begin using the product
- create or open an Analytics project in Analytics , or open an analysis app in the Analysis App window
- connect to HighBond Results , where you can build workflows for organizing, tracking, and remediating exceptions
- access Launchpad , which provides links to all HighBond apps for HighBond users, and links to ScriptHub , Inspirations , and your user profile
- use Offline Projects to check out or check in a section from a HighBond project , and perform work offline
- access resources such as Support , quick start guides, product forums, online Help, and training courses
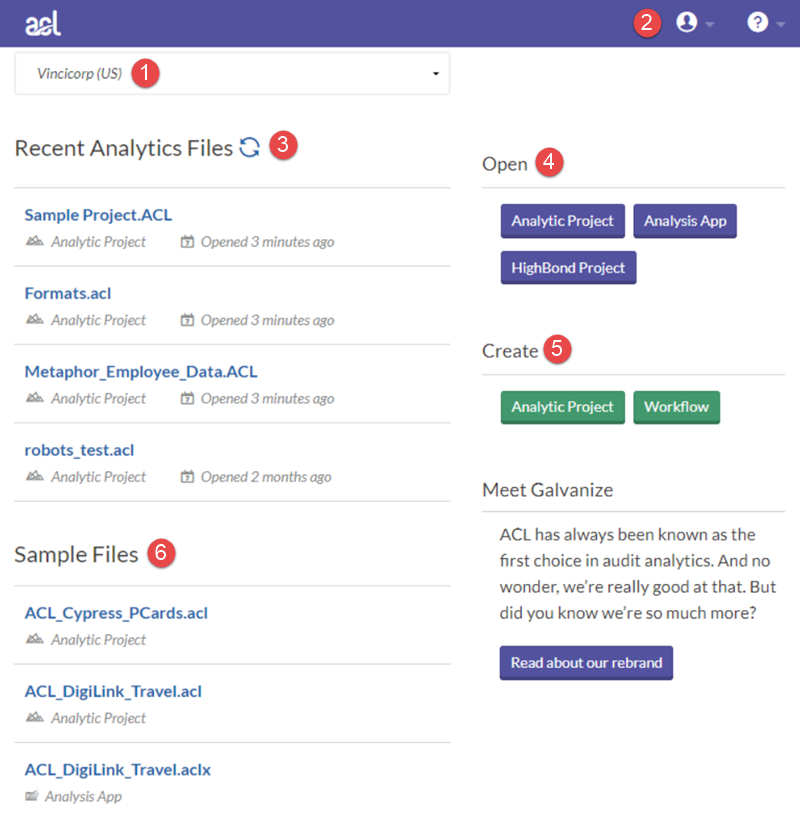
Overview of ACL for Windows main screen
Components
| Number | Component | Description |
|---|---|---|
| 1 | Organization selector | Switch between accounts (organizations) you have access to using this drop-down list. |
| 2 | Toolbar | |
| 5 | Create |
|
| 6 | Sample Files | Open pre-built Analytics projects that include a variety of sample data. |
Switching your HighBond instance
You might belong to multiple instances of HighBond if your organization has more than one subscription, you consult for multiple organizations, or you are part of a training instance. If you belong to more than one HighBond instance, you can use ACL for Windows to switch between them.
Switching between HighBond instances allows you to activate ACL for Windows using different subscriptions, and to access data belonging to different organizations or business units.
To switch your HighBond instance:
- In ACL for Windows , select Sign Out and close from the profile drop-down list .
You are signed out of your current instance.
Double-click the ACL for Windows shortcut on the desktop.
The Launchpad sign-in screen opens.