- Биосетный процесс — какова его функция?
- Johan Louwers — Tech blog
- Friday, October 27, 2017
- Oracle Linux — digging into the bioset Kernel working
- Thread: Possible virus? Process ‘bioset’
- Possible virus? Process ‘bioset’
- Re: Possible virus? Process ‘bioset’
- Re: Possible virus? Process ‘bioset’
- Re: Possible virus? Process ‘bioset’
- Re: Possible virus? Process ‘bioset’
- Re: Possible virus? Process ‘bioset’
- Re: Possible virus? Process ‘bioset’
- Re: Possible virus? Process ‘bioset’
- bioset
- Question information
- Related bugs
- Related FAQ:
Биосетный процесс — какова его функция?
Какова функция биореактивного процесса? Почему нет документации для процесса биореактивности? Почему нет четких ответов на вопросы о биосетном процессе, которые уже опубликованы?
То, что было найдено до сих пор, является лишь предположением:
- вирус; потому что нет документации, подтверждающей, что это законный процесс, даже нет ответа о том, что это законный процесс
- процесс ядра; потому что символ для процесса такой же, как и у других процессов ядра, и пользователь не может изменить, остановить, завершить или убить процесс bioset
- регистратор ключей; кажется, что доступ к Интернету и связан с приложениями, которые имеют доступ к Интернету
- часовая бомба; со временем начнет нарушать функции приложений
- Другие; спекуляции гораздо менее вероятны или совершенно возмутительны
Это часть блока ввода-вывода ядра:
Эти биореактивные нити являются частью некоторой системы восстановления.
Я только заметил этот процесс, и мне было любопытно, поэтому я провел небольшое исследование .
Я до сих пор не уверен, но, похоже, это процесс ядра, связанный с блочным вводом-выводом (отсюда и «био» в bioset) . он также появляется в коде устройства-устройства отображения: https://github.com / Торвалдс / Linux / поиск? utf8 =% E2% 9C% 93 & д = bioset
Биосет на моем компьютере вроде бы встроен в ядро. Он начинается с родительского процесса 2. Он кодирует все внутренние коммуникации.
Ранее я поймал хакера на своем последовательном терминале. После копания кажется, что я был скомпрометирован несколькими предметами. Может быть, Виндиго и Эбуни. Троянский тип.
Я могу подключиться к Интернету с низким уровнем привилегированных пользователей, root подключается к серверу ключей, и вскоре у меня открывается множество процессов dns / udp и открываются сокеты ядра.
Этот парень любит общение с пакетами udp на своих основных серверах.
Просто сообщаю тебе мой опыт. Также, если вы подключаетесь к серверам, вы должны удалить все свои локальные личные ключи и обновить ключи сервера. Он распространяется через ssh.
Рекомендую всем установить идентификаторы, audd и настроить их Firefox действительно хорошо. Это была кривая обучения для меня.
bioset Процесс исходит из потока ядра (часто PID 2) и используется в почти ничего , что с помощью Block IO операции памяти или устройства. Я предполагаю, что bioset расшифровывается как «Планировщик ввода-вывода блочного уровня . что-то».
Ссылки, уже предоставленные в предыдущих комментариях, объяснят это более подробно. Но вот полная картина подсистемы ввода-вывода Linux.
Источник
Johan Louwers — Tech blog
The personal view on the IT world of Johan Louwers, specially focusing on Oracle technology, Linux and UNIX technology, programming languages and all kinds of nice and cool things happening in the IT world.
Friday, October 27, 2017
Oracle Linux — digging into the bioset Kernel working
when you are looking into the processes that are running on your Oracle Linux machine you might notice a process, or processes named bioset. In our example we are running an Oracle Linux 6 machine in a vagrant box, and for informational purposes, we are using it to run dockerd to serve Docker containers for development purposes.
As you can see in the below example, we find a number of bioset processes running on our Oracle Linux machine;
Finding bioset
To find out what bioset is and where it is being spawned from you can look at your processes in a number of ways. You can use the below command which provides a nice tree view of all the processes based upon the ps command or you can use the standard pstree command.
using the above command we get the below output (cut down to the relevant part only);
As you can see bioset is a mentioned a number of times, and always as a «child» from kthreadd. Where kthreadd is within Oracle Linux (Linux in general) the kernel thread daemon and by doing so it is one of the backbone components of the Linux kernel which makes sure your kernel threads are handled in the right manner.
However, now we know where bioset is commong from and the parent is the kernel thread daemon we still do not know what bioset is doing.
What is bioset
As we now known bioset is part of the Linux kernel, it is used to Block Input Output instructions. This means it is an integrated part of the inner workings of the kernel when operations to a block device need to be done. bioset finds its origin in the struct bios_set located in bio.h within the Linux kernel code. The bio_set struct is shown below and can also be found in the kernel Github code repository.
If you explore the Linux kernel code you will find that within /block/bio.c will be include /linux/bio.h . The Linux block I/O subsystem includes bioset and this is a vital part of how BIOs are handled within the kernel.
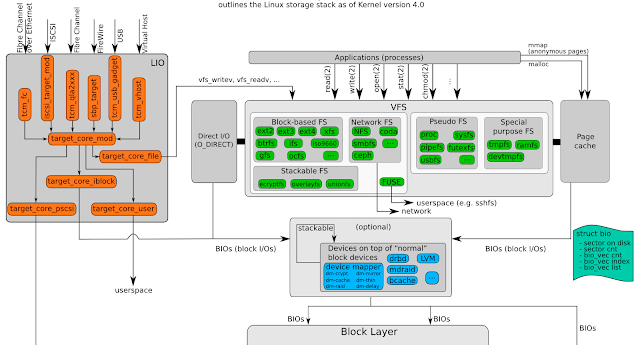
Below images shows the Linux storage stack for kernel version 4.0 where you can see the flow of BIOs. BIOs are send from LIO (Linux I/O) or the VFS to the block I/O layer who in return will communicate with the I/O scheduler who will schedule the I/O operation to be send on the actual block device.
In conclusion
A lot of posts are being written that would indicate that bioset would be something that could be removed or would be malicious for the system, as outlined in the above post bioset is however a vital part of the Linux Kernel and an integrated part of the I/O subsystem for handling I/O requests in combination with block devices.
Источник
Thread: Possible virus? Process ‘bioset’
Thread Tools
Display
Possible virus? Process ‘bioset’
I can’t really find much info online and there are multiple instances running.
Would this post be better suited in Security?
Edit: Even in the event it isn’t anything, how can I go about finding more information about where it runs from and what it does?
Edit 2: Observation. The first link has a date of 7/2013. Result of searches in the forum for ‘bioset’ start 10/2013
Last edited by dshauld; June 4th, 2014 at 03:46 AM . Reason: added question edit2 — observation
Re: Possible virus? Process ‘bioset’
Re: Possible virus? Process ‘bioset’
Are you running a raid configuration?
Re: Possible virus? Process ‘bioset’
Thank you for the reply.
No. I have three drives. One 30G ssd for the OS and two 1TBs for media. The two larger drives are not automatically mounted and not in a RAID configuration.
This is from the second link:
Have a bunch of new processes. Bioset is one of them.
http://linux.die.net/man/3/bio_set_nbio
This is a wrapper round the platform’s TCP/IP socket connection routines.
Using connect BIOs, TCP/IP connections can be made and data transferred using only BIO routines. In this way any platform specific operations are hidden by the BIO abstraction.
TCP/IP connections hidden by abstraction sounds scary.
Being at 67, this process is loaded pretty early in the chain. How can I find out about where it is run from and what it does?
Last edited by cariboo; June 5th, 2014 at 05:34 AM . Reason: remove table
Re: Possible virus? Process ‘bioset’
Re: Possible virus? Process ‘bioset’
Thank you for the reply.
That command doesn’t return anything with or without the leading /.
sudo lsof | grep bio
Re: Possible virus? Process ‘bioset’
Thanks. Now I don’t know why it lists the binary type as «unknown» (or actually shows an «exe» entry for it) and while its process name can be faked items with a process name between square brackets usually denote kernel threads and the «\_ » part indicates they’re children of process Id 2 (should be kthreadd aka the kernel thread daemon). If that’s the case these commands hopefully won’t return anything of use:
Re: Possible virus? Process ‘bioset’
Thanks for your help. That command returns nothing. Actually I get ‘readlink: extra operand ‘ldd’’ when I run that command but separately they return nothing.
What do you make of that post by the Guest I linked to on the forum? When I was looking for information about this process it was sparse and that post got me thinking it may be a virus.
Every other process I looked for I could find information on. How is it that a process doesn’t have any explanation or documentation?
Last edited by dshauld; June 6th, 2014 at 12:17 AM .
Источник
bioset
Command Line:
bioset
Security Context:
system_ u:system_ r:kernel_ t:SystemLow
When I try to find out about bioset:
:
$ man bioset
No manual entry for bioset
:
When I try to run bioset:
:
$ bioset
No command ‘bioset’ found, did you mean:
Command ‘biosed’ from package ’emboss’ (universe)
bioset: command not found
:
Is bioset a key logger, virus, or other malware? If it is malware, it is highly successful as nobody has a method of stopping, ending, killing, or even finding the process.
If bioset is a legitimate process, then Canonical should confirm that it is legitimate even if the function of the process is not revealed. My search of the internet has yielded only derogatory speculation.
Question information
Related bugs
Related FAQ:
What is the output of:
sudo updatedb; dpkg -S bioset; lsb_release -s
$ sudo updatedb; dpkg -S bioset; lsb_release -s
dpkg-query: no path found matching pattern *bioset*
No LSB modules are available.
:
I hope this helps, but there does not seem to be any useful information.
Please provide also the output of the commands
uname -a
lsb_release -crid
locate bioset
ps ax | grep bioset
Those four lines that you’ve put at the beginning of your question, where did they show up?
I apologize as I should have noted the source as from the gnome-system- monitor output. Additionally, when looking for dependencies, bioset showed up under kthreadd.
Please note that I am using the gnome-terminal. The only edit was to shorten the terminal’s prompt. Text formatting was lost during the copy and paste.
Please note that the third command [locate bioset] did not have any output.
Please note that the four instances of the word «bioset» were colored red in the output of the fourth command [ps ax | grep bioset]. The output conforms to the three instances of bioset using the gnome-system- monitor.
$ uname -a
Linux M68M-S2P 3.13.0-66-generic #108-Ubuntu SMP Wed Oct 7 15:20:27 UTC 2015 x86_64 x86_64 x86_64 GNU/Linux
:
$ lsb_release -crid
Distributor ID: Ubuntu
Description: Ubuntu 14.04.3 LTS
Release: 14.04
Codename: trusty
:
$ ps ax | grep bioset
67 ? S
Do you use Truecrypt by any chance
According to the following 2 links, bioset is part of the Linux source code and not malware at all:
I also have the bioset processes running on my Ubuntu PC.
Yes, I have TrueCrypt. Running truecrypt will not spawn bioset. Six instances of bioset will be spawned for each truecrypt archive opened.
I have no idea what triggers bioset to spawn, but opening an encrypted archive or opening a program that can access the internet seems to trigger bioset to spawn. That the programs that can access the internet also use encryption may be relevant.
I have also tried to run bioset from the terminal. The error message is, «bioset: command not found».
In the first link; I was unable to determine the function of bioset. There was one reference to «Unable to create bioset \n» and one instance of «could not allocate data integrity bioset \n» in the code. The rest contained the keyword bioset as a part of a label or as part of a comment. There were also references to bioset_create and bioset_ create_ nobvec. Another, in reference to bio_set, was bioset_free which may not be relevant to bioset. There may be hints as to function, but I am not able to interpret them as I am not a programmer.
In the second link; I see nothing that even hints at the function of bioset. There was one reference to bioset under ps.csv on line 19: name 18, parent 2, CPU 0.0, SIZE 0, COMMAND bioset, RUSER root, S S. Presuming your assumption that it is legitimate because it was listed, what is the function of bioset?
I am not a kernel programmer, but bioset appears to be a kernel process related to block I/O (hence the «bio» in bioset):
I think bioset is part of a high-performance block I/O subsystem in the GNU/Linux kernel:
The bioset process probably needs to remain active in memory to correctly manage writes to block devices.
The first link is a supposition I have already seen, not an answer.
The second link does not even mention bioset nor does any search.
The guesses are making me even more worried. Since even Canonical is not replying, they must be having the same problem in trying to identify and explain the bioset process. This is understandable only if the bioset process is not a part of the official source code.
My thought is that if bioset were a legitimate function, there would be documentation confirming its legitimacy even if there were no explanation of its purpose. I have been unable to find anything that looks like the source code, just lists that do not include bioset in the source code repository.
I am not a programmer, so I am sure that if the source code exists, it is not where I looked to find it.
It’s a part of the kernel. No, there’s not much written about it, but that’s pretty normal for some random kernel thing, in my experience. But there is documentation on the BIO system: https:/ /lwn.net/ Articles/ 26404/. No, it doesn’t mention the «bioset» process specifically, but it tells us the core of this system is the kernel source file linux/bio.h. And if you look at that file (https:/ /github. com/torvalds/ linux/blob/ master/ include/ linux/bio. h), there’s mentions of «bioset» all over. I’m not familiar enough with the kernel to understand how it works or how it creates a process with that name, but it seems pretty safe to say it’s just a normal, benign part of linux.
By the way, this is not a normal process. It’s part of the kernel, which means it doesn’t compile to an executable file named «bioset» (or «bio»). There isn’t actually a command named «bioset», so the system monitor isn’t exactly correct there. That’s why the output of «ps aux | grep bioset» shows «[bioset]» in the command column, not «bioset».
In general, the most likely explanation for anything that’s running on your computer that you don’t understand isn’t «virus!». It’s way more likely to be just some obscure part of the normal software on your computer. There are tons of processes running on my computer that I don’t recognize (including bioset). And this stuff is so poorly documented, most of them will have very little description online.
Oh, and I forgot:
It actually makes total sense that more bioset processes spawn when you mount a Truecrypt archive. It mounts them as block devices, so this supports the idea that bioset is part of the «block I/O subsystem».
I also have this ‘problem’.
I do not have Truecrypt
The only difference I see from above is in the
sudo updatedb; dpkg -S bioset;lsb_release -s
dpkg-query: no path found matching pattern *bioset*
core-2. 0-amd64: core-2. 0-noarch: core-3. 0-amd64: core-3. 0-noarch: core-3. 1-amd64: core-3. 1-noarch: core-3. 2-amd64: core-3. 2-noarch: core-4. 0-amd64: core-4. 0-noarch: core-4. 1-amd64: core-4. 1-noarch: security- 4.0-amd64: security- 4.0-noarch: security- 4.1-amd64: security- 4.1-noarch
Also at the present time, I have 37 processes ‘bioset’ running
any help in how to kill these processes would be helpful
I am — or have been in the past — a kernel hacker / programmer, and I found this thread while trying to find out what this ‘bioset’ thing was when I booted up this Tails 3.0 distribution on this aged laptop for the first time yesterday.
I have not used a current linux kernel in a couple years, now, but what I was reading at LWN makes perefect sense. The BIO mehodology for block I/O get’s away from the 512k «page» limit using this chain of bio_env (??) structures to efficiently move large data.
What that does NOT answer is what /exactly all those «processes» in the prcess listing represent. That is apparently a «kernel block i/o with encryption» answer, since on this system (Tails) pretty much everything is all encryption, all the time.
Also, from what one poster says, above, TrueCrypt uses this same block i/o facility —
Источник