- Install and Configure Linux LDAP Server
- What is LDAP?
- Uses of LDAP
- LDAP server implementations
- Installing OpenLDAP
- Configuring LDAP
- LDAP terminology
- Modifying entries
- Adding entries
- Adding organizational units
- Adding users
- Adding groups
- Deleting entries
- LDAP port
- Authenticating users with LDAP
- Using LDAP web interface (phpldapadmin)
- How to Add LDAP Users and Groups in OpenLDAP on Linux
- Create a LDIF file for New User
- Add a LDAP User using ldapadd
- Assign Password to LDAP User
- Create LDIF file for New Group
- Add a LDAP Group using ldapadd
- Create LDIF file for an existing Group
- Add an User to an existing Group using ldapmodify
- Verify LDAP Entries
- Delete an Entry from LDAP using ldapdelete
- If you enjoyed this article, you might also like..
Install and Configure Linux LDAP Server
Two days ago, one of the website visitors was searching on the website for LDAP and found nothing, that drives me to make a post about the LDAP server, so we fill the gaps and bring the loved content to the visitors.
Table of Contents
What is LDAP?
We know that Linux keeps registered users on /etc/passwd file, so if you want to access the machine, you must have a user on that file.
If you are working with one or few machines, that should be OK, but what if you have hundreds of machines or maybe thousands, and how you will maintain user management tasks like password modification or any other administrative task like somebody left the work and you need to close his account, would you go to every machine to do that?
That could be a nightmare, or you need to create a new account. In this case, we need a centralized user account management system, a database to keep all information related to user accounts.
The most used solution for this problem is the Lightweight Directory Access Protocol (LDAP).
LDAP uses the usual client/server paradigm.
Uses of LDAP
LDAP not only keeps a list of users, but you can also use it as storage for your files.
You can use it for authenticating users as we mentioned above. Also, you can store DNS records in the LDAP server.
Another usage for LDAP, you can use it as a yellow pages directory service for an organization to provide information about users or employees, departments, contact information, phone numbers, addresses, private data, or whatever.
LDAP server implementations
LDAP is an open standard protocol that many companies make their implementation of the protocol.
There are commercial implementations of LDAP like:
- Microsoft Active Directory.
- Oracle Internet Directory.
- Oracle Unified Directory.
- IBM Security Directory Server.
- UnboundID Directory Server.
- NetIQ eDirectory or eDirectory.
- CA Directory or CA eTrust Directory.
And free open source implementations like:
- OpenLDAP.
- ForgeRock OpenDJ.
- Apache DS.
- 389 Directory Server.
In this post, we will use OpenLDAP, which is very common and loved by the community.
OpenLDAP is the open-source implementation of LDAP that runs on Linux/UNIX systems.
Installing OpenLDAP
To install OpenLDAP, you have to install openldap, openldap-servers, and openldap-clients packages.
Or, if you are using CentOS 7, you can use dnf or Dandified Yum.
If you are using a Debian based system like Ubuntu, you can install it like this:
Then we can enable the service to run automatically at startup:
Configuring LDAP
After successful installation, you need to make a password for the admin user using the ldappasswd command:
The configuration files for OpenLDAP are in /etc/openldap/slapd.d directory.
You can modify these files directly or use the ldapmodify command. It is strongly recommended to modify OpenLDAP using the ldapmodify command.
LDAP terminology
If we are going to deal with LDAP protocol, there are some terms that we need to know because we will use them a lot.
Entry (or object): every unit in LDAP considered an entry.
dn: the entry name.
o: Organization Name.
dc: Domain Component. For example, you can write likegeeks.com like this dc=likegeeks,dc=com.
cn: Common Name like the person name or name of some object.
Modifying entries
OpenLDAP stores its information in bdb or hdb files. You can find the hdb file in:
To identify an element, use the dn (distinguished name) attribute. So the first line in our LDIF file will be:
Then we specify if we want to add or modify
We also must clarify if we’ll replace it or delete it
And, finally, we type the new value of the changed attribute.
Back to our file. Change the following entries like this:
So our LDIF file will be like this:
file. The dn attribute is dn:
olcDatabase=<2>hdb, and because the file is inside the config folder, so the full dn attribute is dn:
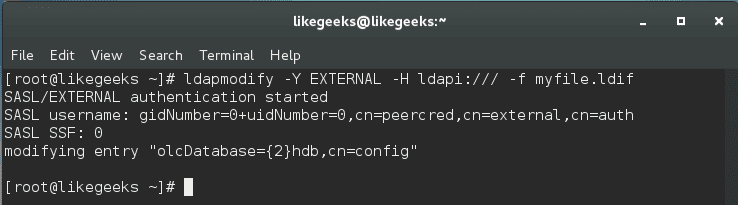
Then we save our file and use ldapmodify:
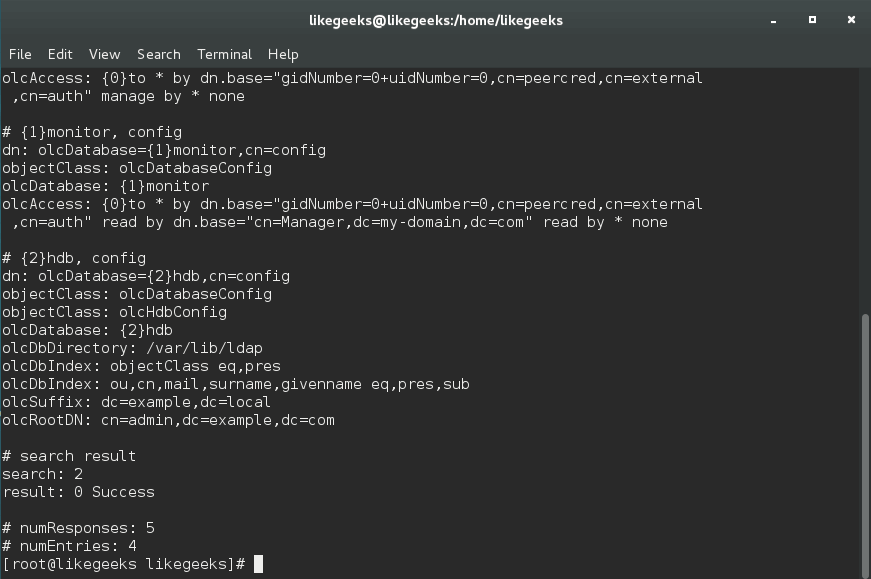
You can use the ldapsearch command to check the changes:
And yes, the data has been changed.
Also, you can use the slaptest command to check the configuration.
Adding entries
To add entries, use the ldapadd command.
First, we create our ldif file:
We specify a series of attributes, like domain component ( dc ), distinguished name ( dn ), and organization ( o ).
According to the type of the object we are creating, which is dcObject in our case, some attributes are required, others are optional.
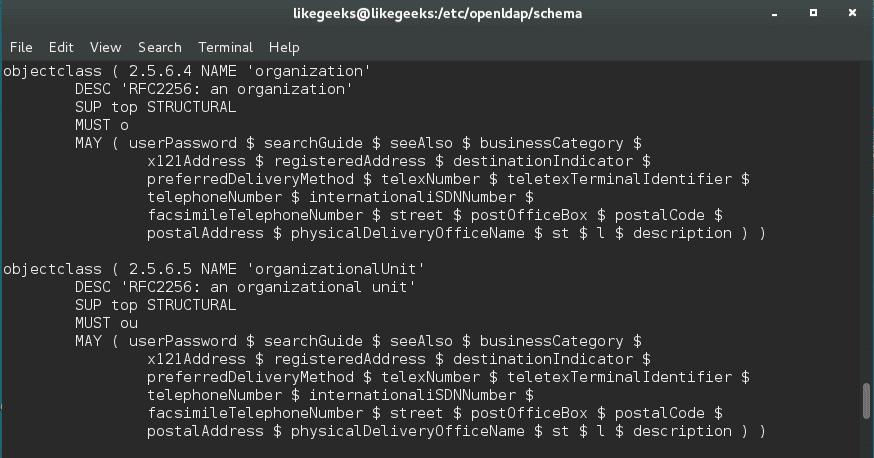
You check the schema according to your system.
On CentOS 6, you can go to
On CentOS 7, you can go to
Or you can use grep command to get the .schema files from your system.
The object organization in our example is in
file on CentOS 7.
As we can see, the only required attribute is o which is the organization.
Now we can use the ldapadd command to add our object:
We specify the filename using -f, the admin user using -D, and the password using -w.
To search for an entry, you can use the ldapsearch command:
Adding organizational units
You can add an organizational unit (ou). First, create a new LDIF file. Let’s name it users.ldif, and put this:
Then we use ldapadd to add the unit:
This organizational unit holds all LDAP users.
Adding users
We can add users to the newly created organizational unit.
First, we create our ldif file:
Then add the user using ldapadd command:
Adding groups
Also, we create the ldif file first:
Then run ldapadd to add the group:
Deleting entries
Deleting an entry is very easy, just use ldapdelete command with the cn you want:
You can check if the entry is deleted using ldapsearch:
LDAP port
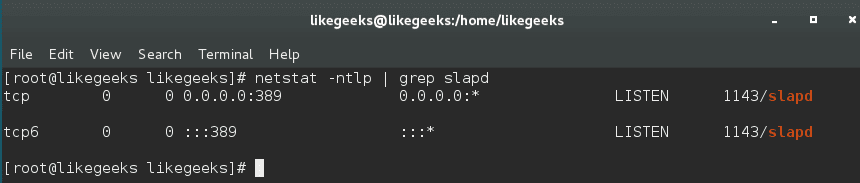
LDAP port is 389, and in case you secure your LDAP using TLS, the port will be 636.
You can ensure what port your OpenLDAP is running using the netstat command.
Authenticating users with LDAP
By default, Linux authenticates users using /etc/passwd file. Now we will see how to authenticate users using OpenLDAP.
Make sure you allow the OpenLDAP ports (389, 636) on your system.
If you are using the iptables firewall, I recommend you review the iptables post to understand these commands Linux iptables firewall.
Now the certificates are in /etc/openldap/cacerts.
When we create a user, you have to define some needed fields.
If you want to create a user adam, you will create adam.ldif file and write the following:
If you are using CentOS 7 you should encrypt passwords using slappasswd command before putting it in your LDIF file like this:
Then we copy the encrypted password on the ldif file, so the file will be like this:
Now we can use ldapadd to add the user:
Using LDAP web interface (phpldapadmin)
It might be a little tricky for a beginner to work from a terminal. However, there is a web-based tool called phpldapadmin, which is written in PHP to simplify working with OpenLDAP.
You can install it like this:
The above command will install the Apache web server, so you don’t need to install it.
Now you need to configure phpldapadmin.
And change this line:
If you want to use likegeeks.local as a domain you should write it like this:
Also, you need to change the line of bind_id like this:
And don’t forget to put your apache alias:
Now you can access your phpldapadmin like this:
in my example, I will use:
On login DN field you will use something like the following:
You can do all we’ve done in this web interface, adding users, organizations, and groups.
I hope you find the tutorial useful and easy. We can’t cover all LDAP server uses in one post, but this was a brief look into LDAP protocol and how to use it.
Источник
How to Add LDAP Users and Groups in OpenLDAP on Linux
To add something to the LDAP directory, you need to first create a LDIF file.
The ldif file should contain definitions for all attributes that are required for the entries that you want to create.
With this ldif file, you can use ldapadd command to import the entries into the directory as explained in this tutorial.
If you are new to OpenLDAP, you should first install OpenLDAP on your system.
Create a LDIF file for New User
The following is a sample LDIF file that will be used to create a new user.
Add a LDAP User using ldapadd
Now, use ldapadd command and the above ldif file to create a new user called adam in our OpenLDAP directory as shown below:
Assign Password to LDAP User
To set the password for the LDAP user we just created above, use ldappasswd command as shown in the below example:
In the above command:
- -s specify the password for the username entry
- -x The username entry for which the password is changed
- -D specify your DN here. i.e Distinguished name to authenticate in the server
Create LDIF file for New Group
Similar to adding user, you’ll also need a ldif file to add a group.
To add a new group to the LDAP groups OU, you need to create a LDIF with the group information as shown in the example ldif file below.
Add a LDAP Group using ldapadd
Just like adding user, use ldapadd command to add the group from the group1.ldif file that we created above.
Create LDIF file for an existing Group
To add an existing user to a group, we should still create an ldif file.
First, create an ldif file. In this example, I am adding the user adam to the dbagrp (group id: 678)
Add an User to an existing Group using ldapmodify
To add an user to an existing group, we’ll be using ldapmodify. This example will use the above LDIF file to add user adam to dbagrp.
Verify LDAP Entries
Once you’ve added an user or group, you can use ldapsearch to verify it.
Here is a simple example to verify if the users exists in the LDAP database:
Delete an Entry from LDAP using ldapdelete
If you’ve made a mistake while adding an user or group, you can remove the entry using ldapdelete.
To delete an entry, you don’t need to create an ldif file. The following will delete user “adam” that we created earlier.
If you enjoyed this article, you might also like..
|
|
 |  |  |  |
Thnx a lot. I have waited for this since the first part.
This is kiran sir, I already contact with gmail.My request could you please post a ldap migration from on server to another it is also important
do you have tutorial on how to understand structure of ldap? it is hard to understand the cn and ou and other tags
Dear Sir,
Please continue your next openldap article. It is very simple and interesting. Show us how to authenticate users via nfs and how use phpldapadmin utility. Above you have showed how to add user adam to directory-I am confusing here. should we use useradd command to create a user before adding user to directory? Kindly continue…
With best wishes
Venkatesh
Bangalore
Hi Ramesh!
Many many thanks for your OpenLDAP article. I am very new to Openldap. I was searching this type of basic article. I found many and old-requires previous versions of centos or redhat systems and requires previous knowledge about ldap. Yours is very basic and following step by step. As I told I am very new to openldap, I am facing lot of problems and no-one around me to solve the basic doubts. I have a small doubt, please guide me.
in your above “How to Add LDAP Users and Groups in OpenLDAP on Linux” article, ‘Add a LDAP User using ldapadd ‘ section, should we create a ‘adam user’ by using useradd command before running the command->
ldapadd -x -W -D “cn=ramesh,dc=tgs,dc=com” -f adam.ldif ?
because after running above command, I am not finding a adam directory in /home directory.
Please clarify. I am eagerly waiting for your reply..
Sorry for the grammatical errors.
Thanks
Venkatesh
India
First of all thumbs on both this and the previous article!
I’m getting very confused with setting this up. I’ve got the following user
[root@localhost ldap]# ldapadd -x -W -D “cn=gmullin,dc=lava,dc=com” -f newusers.ldif
Enter LDAP Password:
adding new entry “uid=hduser,ou=users,dc=lava,dc=com”
ldap_add: Invalid syntax (21)
additional info: objectClass: value #1 invalid per syntax
[root@localhost ldap]# cat newusers.ldif
dn: uid=hduser,ou=users,dc=lava,dc=com
objectClass: top
objectClass: account
objectClass: posixAccount
objectClass: shadowAccount
cn: hduser
uid: hduser
uidNumber: 16860
gidNumber: 100
homeDirectory: /home/hduser
loginShell: /bin/bash
gecos: hduser
userPassword:
shadowLastChange: 0
shadowMax: 0
shadowWarning: 0
After a quick Google, I’m told I need to load my schema (how come yours is already loaded?), with something like the following:
ldapadd -Y EXTERNAL -H ldapi:// -f /usr/local/etc/openldap/schema/nis.ldif
How do I get the appropriate schema for this article?
Help is greatly appreciated!
Very very good tutorial. Thanks !
I am sure that it will be suitable for a lot of people. but i think there is a little mistake with the option of ldapadd.
indeed, you should use -l and not -f when you use ldapadd, as the manual says it :
SLAPADD(8)
/usr/sbin/slapadd [-b suffix] [-c] [-d debug-level] [-f slapd.conf] [-F confdir] [-g] [-j lineno] [-l ldif-file] [-n dbnum] [-o option[=value]] [-q] [-s] [-S SID] [-u] [-v] [-w]
Hope it will be useful ! 😉
Question. In our dev environment I need to add many test dummy accounts in order to test the impact on our system. How can I go about adding in 20k, 50, 100k users into OpenLdap? Do I really have to have to build a custom JAVA project that calls the add command that many times or is there another way to get this job done?
Источник