- How To Find Out Which Proccess is Listening On A Port for Windows?
- List Listening Port with netstat Command
- How To Find Out Which Proccess is Listening On A Port for Windows Infographic
- Use Netstat to See Listening Ports and PID in Windows
- What Is Netstat?
- Using Netstat To See Listening Ports & PID
- What’s Using That Port?
- How To Get Port, PID, & Process Name In PowerShell
- Go Get Them
- FileCloud Blog
- How to find what application is listening on a TCP/IP port in windows using netstat?
- Why is the ‘System’ process listening on port 443?
- 17 Answers 17
- Get the process number of the port that you are looking for (443 in this case):
How To Find Out Which Proccess is Listening On A Port for Windows?
System or Network administrators looks ports and applications to solve problems. Getting port and application info in Linux can be done lsof command. But in Windows? netstat is a very popular and useful tool used to get network and port-related information.
List Listening Port with netstat Command
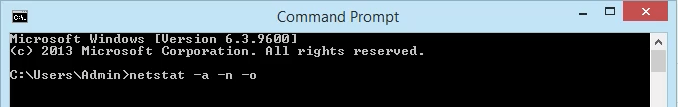
We will use netstat command like below in order to list which process, application or service listening which port on Windows.
- -a Display all connections and listening ports
- -b Display port and connection related executable/application
- -n Display port numbers as a number, not port name
- -o Display process/executable owner
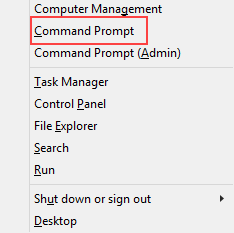
What is that? it says we need Administrator privileges. Open command prompt with Administrator privileges

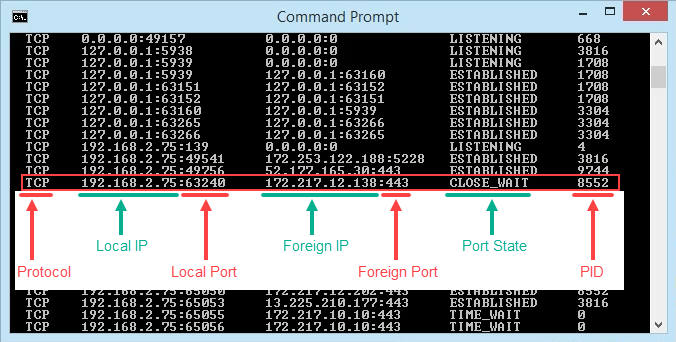
From the output following information is provided
- The protocol is the transport layer protocol like TCP or UDP
- Local Address is the current local system IP address. `0.0.0.0` means every IP address current system have. Because the current system may have multiple interfaces and IP addresses.
- Foreign Address is the remote system address or Hostname which is connected or waiting
- State specifies the given port status like LISTENIN, CLOSED, CONNECTED etc.
How To Find Out Which Proccess is Listening On A Port for Windows Infographic
Use Netstat to See Listening Ports and PID in Windows
You never know when this will come in handy
In another article, we explained computer ports and what they’re used for. Other than that, what can we do with port information? Since all traffic in and out of the computer goes through ports, we can check on them to see what they’re doing. Maybe the port isn’t listening for traffic? Maybe something is using a port that shouldn’t be?
We’re going to use the Windows command netstat to see our listening ports and PID (Process ID). We’re also going to see what we can do with that information.
What Is Netstat?
The netstat command is a combination of the words ‘network’ and ‘statistics’. The netstat command works in all versions of Windows from Windows XP right up to Windows 10. It’s also used in other operating systems (OS) like Unix and Linux, but we’ll stick to Windows here.
Netstat can provide us with:
- The name of the protocol the port is using (TCP or UDP).
- The local IP address and name of the computer and the port number being used.
- The IP address and port number to which we’re connecting.
- The state of a TCP connection. For details on what these states are, read the Event Processing section of RFC 793.
Using Netstat To See Listening Ports & PID
- Use the key combination Win Key + X. In the menu that opens, select Command Prompt.
- Enter the command . The parameters for netstat are preceded with a hyphen, not a forward slash like many other commands. The -a tells it to show us all active connections and the ports on which the computer is listening.
The -n tells netstat to show the IP addresses and ports as numbers only. We’re telling it to not try to resolve the names. This makes for a quicker and neater display. The -o tells netstat to include the PID. We’ll use the PID later to find out what process is using a specific port.
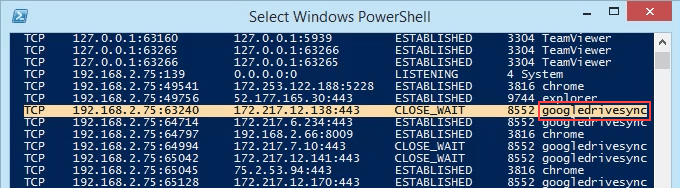
- View the results and take note of the addresses, port numbers, state, and PID. Let’s say we want to know what’s using port 63240. Note that its PID is 8552 and it’s connecting to the IP address 172.217.12.138 on port 443.
What’s Using That Port?
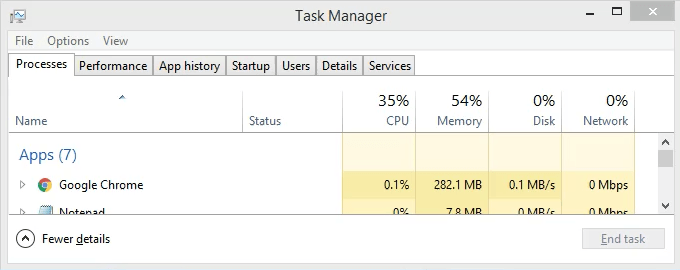
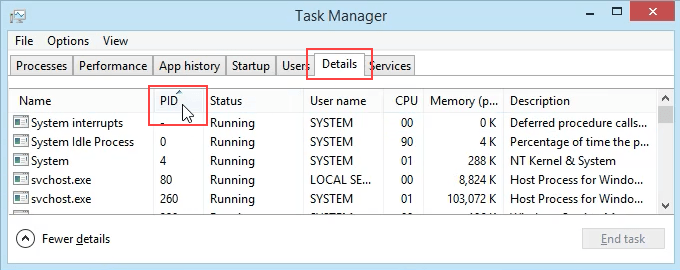
- Open Task Manager. That’s most easily done by using the key combination Ctrl + Shift + Esc.
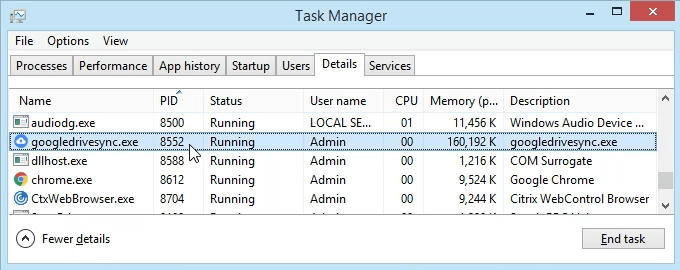
- Click on the Details tab. To make this easier to find, click on the PID column header to sort the PIDs numerically.
- Scroll down to PID 8552 and see what process it is. In this case, it’s googledrivesync.exe. But is it really? Sometimes viruses can make themselves look like legitimate processes.
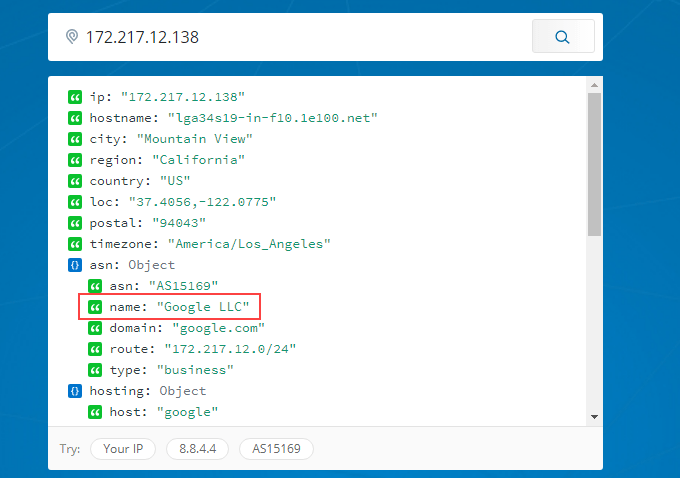
- In a web browser, go to ipinfo.io. Enter the IP address 172.217.12.138. As we can see, the IP address is registered to Google. So this googledrivesync.exe is a legitimate one.
How To Get Port, PID, & Process Name In PowerShell
PowerShell is Microsoft’s newer way to use a command-line interface with Windows. We say newer, but it’s been around for several versions. You should learn PowerShell even if you’re a home user.
Most Windows commands also work in PowerShell, plus we can combine them with PowerShell’s cmdlets – pronounced command-lets. Joe at Winteltools.com provides the script for this method.
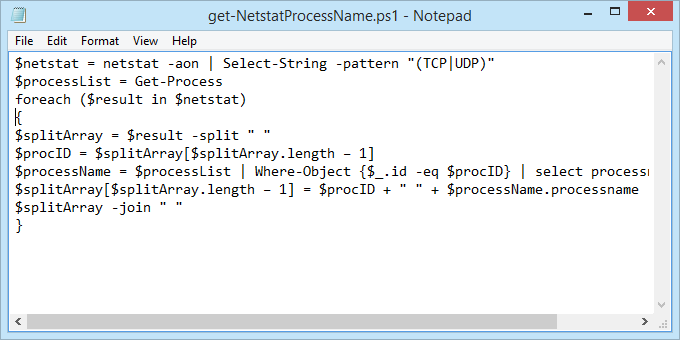
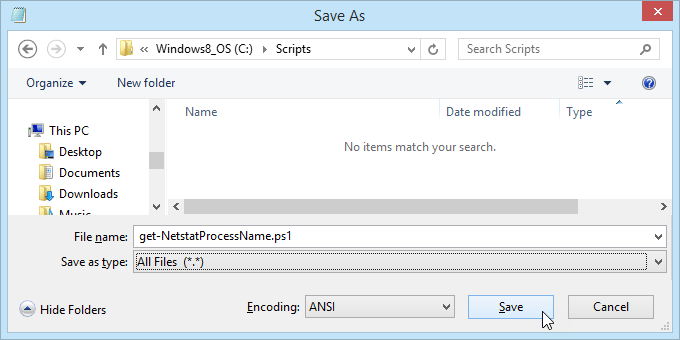
- Open Notepad and enter the following code:
- Save the file as get-NetstatProcessName.ps1. Make sure to note where it’s being saved. It’s important to change the Save as type: to All Files (*.*) or it will get saved as get-NetstatProcessName.ps1.txt and it won’t work for us.
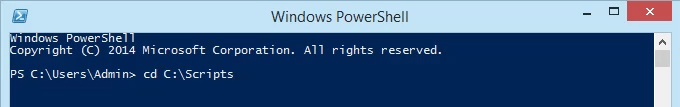
- Open PowerShell and navigate to the location in which the script was saved. In this case, it’s . Hit Enter to run the command.
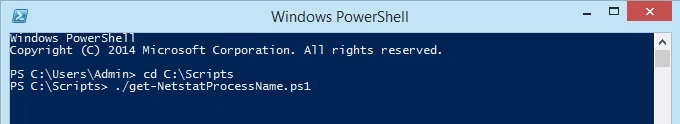
- Run the script using dot-sourcing to make it work. That means use ./ before the name of the file. The command will be
- Now we can see all the traditional netstat info plus the process name. No need to open Task Manager anymore.
Go Get Them
We’ve covered two ways to use the netstat command to see listening ports. It can be used either in the old Command Prompt or within a PowerShell script. With the information it can give us, we’ve looked at how it can help us figure out what our computer is doing.
If you thought netstat is a great utility, take a look at some other Windows TCP/IP utilities like tracert, ipconfig, and nslookup. Or use Resource Monitor to get a better look into hidden website and Internet connections. There is a lot you can do to see exactly what your computer is doing.
Have you used netstat to solve a problem? Please tell us what you did. Any questions about how to use netstat? Please ask us in the comments below.
Guy has been published online and in print newspapers, nominated for writing awards, and cited in scholarly papers due to his ability to speak tech to anyone, but still prefers analog watches. Read Guy’s Full Bio
FileCloud Blog
How to find what application is listening on a TCP/IP port in windows using netstat?
Whenever an application wants to make itself accessible over the network, it claims a TCP/IP port, which means that port can’t be used by anything else. So if you need to use an in-use port, how do you tell what application is holding it?
There’s a number of ways to tell which application has the port locked, here we will use a windows built-in way using the command line and Task Manager.
Using Built-In Tools to See What is Listening on a Port
The first step is to use a command-line tool to see what ports are in use, and use a special flag that tells us which port is assigned to each Windows process identifier number. Then we can use that number to look up exactly which process it is.
Open up a command prompt and type in the following—you may have to open in Administrator mode to see all processes:
netstat -ab | more
This will immediately show you a list, although it’s maybe a little complicated. You’ll see the process name in the list, and you can search for it.
You can also use this other method, which takes an extra step, but makes it easier to locate the actual process:
netstat -aon | more
If you look on the right-hand side, you’ll see where I’ve highlighted the list of PIDs, or Process Identifiers. Find the one that’s bound to the port that you’re trying to troubleshoot—for this example, you’ll see that 0.0.0.0:80, or port 80, is in use by PID 1184.
Now you can simply open up Task Manager—you might have to use the option to Show Processes for All Users, and then you’ll be able to find the PID in the list. Once you’re there, you can use the End Process, Open File Location, or Go to Service(s) options to control the process or stop it.
Alternatively you can even use resource monitor to stop any process that is running. To open resource monitor type resmon.exe in run. This will bring up the resource monitor window.
There would be situations were some other process is running at port 80. To stop anything running in port 80 the following command can be used from command prompt.
Why is the ‘System’ process listening on port 443?
I am having problems starting my Apache server, because port 443 is already in use.
It turns out, the system process (PID 4) uses the port 443. I don’t have IIS installed, the services.msc shows (predictably) no Exchange server running, nor WWW-Services, nor IIS. I have no idea how to find out what service uses that port, short of just disabling each service one after the other, and I am not even sure that would help.
I would be grateful if someone could point me towards how I can get my SSL port back, thank you 🙂
P.S.: Of course «just switch Apache to another port for SSL» would solve the problem of not being able to start Apache. But I’d still like to know what is so insistent about hogging port 443. 🙂
I by now took the ‘hard route’ and disabled services one after the other. It turned out that the «Routing and RAS» service was the culprit.
Thank you all for the valuable input and the new tools in the combat against «WTF does my system do now?».
17 Answers 17
Run the following from an elevated command prompt:
I bet it’s Skype. Uncheck the checkbox shown below if you have it installed.
First off, I will answer this question directly and anyone reading this can ignore any answers talking about 3rd-party, non-Microsoft applications using the System Process.
The System process is listed as PID 4 on every modern-day Windows system. It is for kernel-mode access. This rules out most 3rd-party web products like Apache.
Since the inception of WinRM (Windows Remote Management), the HTTP service (%SystemRoot%\system32\drivers\http.sys) has been a standard part of Windows (Vista and later / Server 2008 and later). http.sys runs under the System process (PID 4).
Other Microsoft-developed software may also use the %SystemRoot%\system32\drivers\http.sys under the System process like IIS, SQL Reporting Services, and Microsoft Web Deployment Service (http://support.microsoft.com/kb/2597817).
WinRM 1.0 default ports were:
HTTP = 80
HTTPS = 443
WinRM 2.0 and greater default ports are:
HTTP = 5985
HTTPS = 5986
Check with the following commands:
Winrm enumerate winrm/config/listener
Winrm get http://schemas.microsoft.com/wbem/wsman/1/config
Get the process number of the port that you are looking for (443 in this case):
. from a non-mapped drive of Windows to avoid «Access Denied»:
netstat -aon | find «:443»
Output should look like the following for the System process:
C:>netstat -ano |find «:443»
TCP 0.0.0.0:443 0.0.0.0:0 LISTENING 4
TCP [::]:443 [::]:0 LISTENING 4
The last column is the PID (4).
Running tasklist to find out what is running in the process proves unhelpful:
tasklist /SVC /FI «PID eq 4»
tasklist /m /FI «PID eq 4»
Look in the registry for the HTTP service: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\HTTP\Parameters\UrlAclInfo
There will be a list of URLs (with the port numbers) which can lead you to which application is running and holding which ports:
http:// +:5985/wsman/ —> WinRM
https:// +:5986/wsman/ —> WinRM
http:// +:80/Reports/ —> SQL Reporting Server
http:// +:80/ReportServer/ —> SQL Reporting Server
https:// server_fqdn:443/Reports/ —> SQL Reporting Server
https:// server_fqdn:443/ReportsServer/ —> SQL Reporting Server
http://* :2869/ —> Simple Service Discovery Protocol service (SSDPSRV)
http://* :5357/ —> Web Services Dynamic Discovery (WS-Discovery)
https://* :5358/ —> Web Services Dynamic Discovery (WS-Discovery)
You can then find the corresponding service on the system and stop it and see that wanted port is released by confirming with another netstat -aon | find «:443» command.