- The /root Directory
- Linux Root Folders Explained
- Linux Root folders
- / – The Root
- /bin – Binaries
- /boot – Boot Files
- /dev – Device Nodes
- /etc – Configuration Files
- /home – Users’ Folder
- /lib – Libraries
- /lost+found – Recovered Files
- /media – Automatic mount point
- /mnt – Manual mount point
- /opt – Optional Software
- /proc – Kernel Files
- /root – Root Home
- /run – Early temp
- /sbin – System Binaries
- /srv – Service Data
- /tmp – Temporary Files
- /usr – User Binaries
- /var – Variable Files
- Conclusion
- What is the root directory in linux
The /root Directory
The /root directory is the home directory of the root account. It is also referred to as the root user’s home directory (and not as the root directory).
A home directory, also called a login directory, is a directory on a Unix-like operating system that serves as the repository for a user’s personal files (including configuration files), directories and programs. It is also the directory that a user is first in after logging into the system.
/root is a standard first-tier directory in the root directory (as are /bin, /boot, /dev, /etc, /home, /mnt, /sbin and /usr). The root directory is the top level directory on any Unix-like operating system, i.e., the directory that contains all other directories and their subdirectories. It is designated by a forward slash ( / ). As is the case with all other first tier directories in the root directory, /root’s name always begins with a forward slash.
/root contains configuration files for the root account, just as each ordinary user’s home directory (which is by default a subdirectory of the /home directory) contains configuration and other files for that user. It is created automatically when the operating system is installed in order to avoid cluttering the root directory with the root user’s configuration files. If /root does not exist for some reason, most Linux distributions will utilize the root directory for this purpose instead.
Created August 30, 2005.
Copyright © 2005 The Linux Information Project. All Rights Reserved.
Источник
Linux Root Folders Explained
In this post, you will finally get the Linux root folders explained. You will learn how these folders are used by your Linux system and how you can use them.
When you open your file manager, you are usually located in your home directory. But if you go two levels up, you will see this set of directories:
This post exactly about all these directories. You can watch the video where these Linux root folders explained or continue reading below.
Linux Root folders
I won’t use the terminal here and I will show you some visual presentation. But you are of course are encouraged to open the terminal and explore all these directories. Let’s get started.
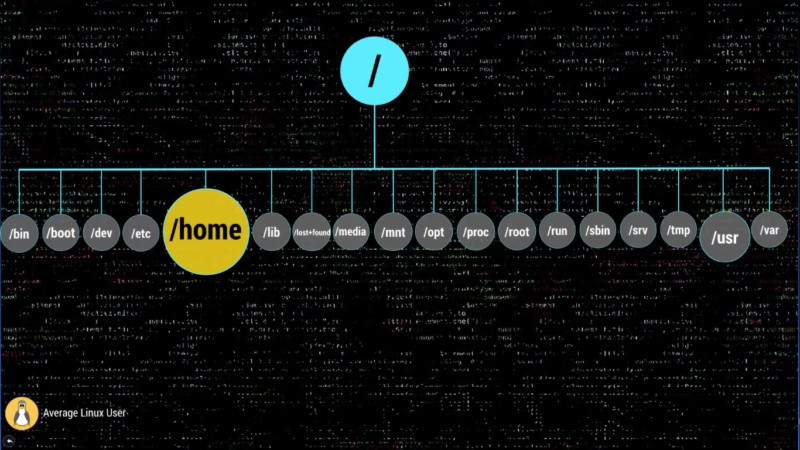
/ – The Root
Everything begins in your system from this directory. All your folders, hard drives, USB drivers, everything is located in this root folder. You cannot go above this directory.
Also, the root directory is designated by the slash sign.
The concept of the root directory may be difficult to understand for Windows users who are used to see something like disk C, disk D and disk E. In Linux, every disk is a represented as a folder that is mounted under this root directory.
This Linux Directory Structure may look like a mess, but believe me when you learn it, you will realize how much sense it makes.
/bin – Binaries
The /bin folder contains programs that are essential for the system to boot and run. So, if you destroy this folder, your system won’t boot and run.
These programs are stored in the binary format. In other words, they are not in text format. You cannot open and read the content of these programs. The advantage of such format is that a computer can read and execute these programs very fast.
/boot – Boot Files
It is easy to guess from the name. This folder is needed to boot your system. It contains the Linux kernel, initial RAM disk image for drives need at boot time, and the bootloader.
I also would like to point out that within this boot folder, you can find the grub folder that contains grub configuration files.
If you read my Arch Linux post, you should remember than I used this command to generate the GRUB configuration file.
The boot folder also contains the Linux kernel.
/dev – Device Nodes
Here, I need to introduce another important concept of Linux – everything is a file. The /dev folder contains files for all devices your Linux is able to recognize.
If you have some Linux experience, you may recall that when you mount a hard drive, you use a name such as /dev/sda1 . The sda is the name of a first hard drive recognized by your Linux kernel and it is located in the dev folder. When the disk is mounted, you see it as a folder in that mounting point.
You can also find here USB devices, CPU etc.
/etc – Configuration Files
The /etc folder comprises all system-wide configuration files and some shell scripts that are executed during the system boot. All files here are text files, so they are human readable.
If you ever did any system-wide configuration, you probably edited some files here.
For example, there is /etc/fstab file that contains a table of storage devices and their mounting points.
/home – Users’ Folder
The home directory contains a home folder for each regular user on your Linux system. For example, I have tow folders in my /home folder. ALU is my home folder. The second folder belongs to another user, whom I named User2. So, the home folder of every user is named by its username.
You have as many folders as many users you have on your system.
These users’ folders are where users store their private data such as documents, videos, picture, music etc. When you open your file manager or your terminal by default you are located in you user’s home folder. It is also often marked as
/lib – Libraries
You already know the /bin directory that contains programs, this /lin folder contains libraries required by those programs from the /bin folder.
A library is a set of functions that are shared between programs. Thus, this /lib folder is also essential for your system to work correctly.
/lost+found – Recovered Files
You will have this directory if you use the ext4 file system. Most of the modern Linux distros use ext4, so most likely you have this folder. This is a file system specific folder that is used for data recovery in case of file corruption. Unless something bad has happened, this folder should be empty on your system.
This /lost+found folder is produced on every separate partition. So, if your /home folder is on a separate partition, you should have this /lost+found folder in your home directory too.
/media – Automatic mount point
This folder is used for automatic mounting of removable media such as USB drives, CD-ROM etc. For example, if your system is configured for automatic mounting, when you insert a USB drive it will be mounted to this folder.
/mnt – Manual mount point
The /mnt folder is similar to the /media folder, it is also used to mount devices, but usually, it is used for manual mounting. You, of course, can manually mount your devices to /media , but to keep some order in your system it is better to separate these two mounting points.
/opt – Optional Software
This folder is not essential for your system to work. Usually, it is used to install commercial programs on your system. For example, my Dropbox installation is located in this folder.
/proc – Kernel Files
This is a virtual file-system maintained by the Linux kernel. Usually, you do not touch anything in this folder. It is needed only for the kernel to run different processes.
/root – Root Home
This is the home directory of your root user. Don’t mix it with the / root directory. The / directory is the parental directory for the whole system, whereas this /root directory is the same as your user home directory but it is for the root account.
If you log in as a root, you will be located in this directory by default. This is a folder for private data and account specific setting of your root account.
/run – Early temp
The /run is a recently introduced folder that is actually a temporary file-system. It is used to store temporary files very early in system boot before the other temporary folders become available.
/sbin – System Binaries
Similar to /bin this folder contains binaries for essential system tasks but they are meant to be run by the super user, in other words, the administrator of the system.
/srv – Service Data
This directory contains service files installed on your system. For example, if you installed a web-served on your Linux system, it will be located in this folder.
/tmp – Temporary Files
This is just a place where programs store temporary files on your system. This directory is usually cleaned on reboot.
/usr – User Binaries
This is probably the largest folder after your home folder. It contains all programs used by a regular user.
I would like to stop little more on sub-directories of this /usr folder.
/usr/bin contains the programs installed by your Linux distribution. There are usually thousands of programs here.
The libraries for this /usr/bin executables are located in the /usr/lib folder.
The /usr/local doesn’t have any programs by default, but if you compile and install a program system-wide it will be placed here.
The most useful folder is /usr/share . It contains all the shared data used by the programs from /usr/bin .
All default configuration files, themes, icons, wallpapers, sound files are stored here, one more folder I would like to mention here is the /usr/share/doc folder, where you can find the documentation files for programs installed on your system.
/var – Variable Files
The /var contains files that are of variable content, so their content is not static and it constantly changes. For example, this is where the log files are stored. If you don’t know, a log file is a file that records all events happening in your system while it is running. These log files often help to find out if something is not working correctly in your system.
Conclusion
Now you have some clue about all those folders in your Linux system.
Please, feel free to add anything in the comments bellow in case I missed something.
Источник
What is the root directory in linux
root is the user name or account that by default has access to all commands and files on a Linux or other Unix-like operating system. It is also referred to as the root account, root user and the superuser.
The word root also has several additional, related meanings when used as part of other terms, and thus it can be a source of confusion to people new to Unix-like systems.
One of these is the root directory, which is the top level directory on a system. That is, it is the directory in which all other directories, including their subdirectories, and files reside. The root directory is designated by a forward slash ( / ).
Another is /root (pronounced slash root), which is the root user’s home directory. A home directory is the primary repository of a user’s files, including that user’s configuration files, and it is usually the directory in which a user finds itself when it logs into a system. /root is a subdirectory of the root directory, as indicated by the forward slash that begins its name, and should not to be confused with that directory. Home directories for users other than root are by default created in the /home directory, which is another standard subdirectory of the root directory.
Root privileges are the powers that the root account has on the system. The root account is the most privileged on the system and has absolute power over it (i.e., complete access to all files and commands). Among root’s powers are the ability to modify the system in any way desired and to grant and revoke access permissions (i.e., the ability to read, modify and execute specific files and directories) for other users, including any of those that are by default reserved for root.
A rootkit is a set of software tools secretly installed by an intruder into a computer that allows such intruder to use that computer for its own, usually nefarious, purposes when desired. Well designed rootkits are able to obtain root access (i.e., access to the root account rather than just to a user account) and to hide most or all traces of their presence and activities.
The use of the term root for the all-powerful administrative user may have arisen from the fact that root is the only account having write permissions (i.e., permission to modify files) in the root directory. The root directory, in turn, takes its name from the fact that the filesystems (i.e., the entire hierarchy of directories that is used to organize files) in Unix-like operating systems have been designed with a tree-like (although inverted) structure in which all directories branch off from a single directory that is analogous to the root of a tree.
The original UNIX operating system, on which Linux and other Unix-like systems are based, was designed from the very beginning as a multi-user system because personal computers did not yet exist and each user was connected to the mainframe computer (i.e., a large, centralized computer) via a dumb (i.e., very simple) terminal. Thus it was necessary to have a mechanism for separating and protecting the files of the individual users while allowing them to use the system simultaneously. It was also necessary to have a means for enabling a system administrator to perform such tasks as entering user directories and files to correct individual problems, granting and revoking powers for ordinary users, and accessing critical system files to repair or upgrade the system.
Every user account is automatically assigned an identification number, the UID (i.e., user ID), by a Unix-like system, and the system uses these numbers instead of the user names to identify and keep track of the users. Root always has a UID of zero. This can be verified by logging in as root (if using a home computer or other system that permits this operation) and running the echo command to display the UID of the current user, i.e.,
echo is used to repeat on the screen what is typed in after it. The dollar sign preceding UID tells echo to display its value rather than its name.
The UID for root (as well as for all other users) can also be seen by looking at /etc/passwd, which is the configuration file for user data. This file can be viewed (by default by all users) by using the cat command (which is commonly employed to read files), i.e.,
The output of cat /etc/passwd in this example is piped (i.e., transferred) to the less command to allow it to be read one screenful at a time, which is useful if the file is a long one. The line of output for root will look something like root:x:0:0:root:/root:/bin/bash. The first column shows the user name and the third column shows the UID, which can be seen to be zero.
The permissions system in Unix-like operating systems is set by default to prevent access by ordinary users to critical parts of the system and to files and directories belonging to other users. Thus, it can be very tempting for users new to such systems, especially those who are accustomed to systems with a weak permissions system or without any permissions system (e.g., Microsoft Windows or the older versions of the Macintosh), to bypass this permissions system on their personal computers by logging directly into the root account and staying there. Although this provides momentary relief, it should be avoided and ordinary work on the system should be done via an ordinary user account.
This is because it is very easy to damage a Unix-like system when using it as root — much easier than to damage most other types of operating systems. The designers of most other operating systems devised methods of protecting the system and data to compensate for the lack of a robust permissions system.
However, an important principle of Unix-like operating systems is the provision of maximum flexibility to configure the system, and thus the root user is fully empowered. Unix-like systems assume that the system administrator knows exactly what he or she is doing and that only such individual(s) will be using the root account. Thus, there is virtually no safety net for the root user in the event of a careless error, such as damaging or deleting a critical system file (which could make the entire system inoperable).
Adding to the danger of routinely using the system as root is the fact that all processes (i.e., instances of programs in execution) started by the root user have root privileges. Because even the most widely used and well-tested application programs contain numerous programming errors (due to the huge amount of code required and its great complexity), a skilled attacker can often find and exploit such an error to obtain control of a system when a program is run with root privileges rather than using an ordinary user account, with its very limited privileges.
A critical means for preventing users from directly damaging Unix-like systems or increasing the vulnerability of such systems to damage by others is the avoidance of using the root account except when absolutely necessary, even by knowledgeable and experienced system administrators. That is, rather than routinely logging into the system as root, administrators should log in with their ordinary user accounts and then use commands, such as su, kdesu and sudo, that provide them with root privileges only as needed and without requiring a new login.
For example, to become root with su merely requires typing
at the command line (i.e., in the all-text mode), pressing the Enter key and supplying the root password. The account of the previous user can be returned to by pressing the Ctrl and d keys simultaneously or by typing the word exit and then pressing the Enter key.
The security associated with using su can be increased by using its -c option, which terminates it and causes an immediate return to the former user account after the current command has completed execution or after any program that it has launched has been closed.
Tasks that require root privileges include moving files or directories into or out of system directories (i.e., directories that are critical to the functioning of the operating system), copying files into system directories, granting or revoking user privileges, some system repairs, and the installation of some application programs. By default, it is not necessary to be root to be able to read most configuration files and documentation files in system directories, although it is necessary to be root to modify them.
Root privileges are usually required for installing software in RPM (Red Hat Package Manager) package format because of the need to write to system directories. If an application program is being compiled (i.e., converted into runnable form) from source code (i.e., its original, human-readable form), however, it can usually be configured to install and run from a user’s home directory. Root privileges are not needed by an ordinary user to compile and install software in its home directory. Compiling software as root should be avoided for security reasons.
On large systems used by businesses and other organizations, there will likely be several system administrators. Each will have its own account in which it will ordinarily work (and the activities of which will be automatically recorded in system logs for security and repair purposes) but will also have access to the root account for use when necessary. The system administrator(s) might grant limited root privileges to some individuals, such as assistant administrators.
Created May 29, 2005. Updated October 27, 2007.
Copyright © 2005 — 2007 The Linux Information Project. All Rights Reserved.
Источник