- Certify your desktop application
- Step 1: Prepare for certification
- Step 2: Test your app with the Windows App Certification Kit
- Step 3: Use the Windows Certification Dashboard
- Step 4: Promote your desktop app
- See also:
- What are Root Certificates for Windows10?
- How does Public Key Cryptography work
- What are Root Certificates in Windows 10
- Where are SSL certificates are stored?
- 1 Answer 1
- Password Recovery
Certify your desktop application
Certification for Win32 desktop apps is deprecated. Instead, submit files here.
Follow these steps to get your desktop app certified for Windows 7, Windows 8, Windows 8.1, and Windows 10.
If you wish to convert your desktop app to be compatible with the Universal Windows Platform and Windows Store, you will use the Windows Desktop Bridge, in which case you should follow the Desktop Bridge guidance for certification steps.
If you are developing and certifying a UWP app from the start, see Guidance for Windows App Certification in UWP for info on certification.
Step 1: Prepare for certification
| Topic | Description |
|---|---|
| What are the benefits? | Certifying your desktop app provides several benefits for you and your customers. |
| Read the requirements | Review the technical requirements and eligibility qualifications that a desktop app must meet. |
Step 2: Test your app with the Windows App Certification Kit
| Topic | Description |
|---|---|
| Get the Kit | To certify your app, you have to install and run the Windows App Certification Kit (included in the Windows SDK). |
| Using the Kit | Before you can submit your app, you must test it for readiness. You can also download a copy of the app certification white paper. |
| Review test details | Get the list of the tests your app needs to pass to qualify for compatibility with the latest Windows operating system. |
Step 3: Use the Windows Certification Dashboard
To submit your app for certification, you’ll need to log in or register a company account on the Windows Certification Dashboard. Once you do, not only will you be able to get your app certified, but you’ll also gain access to tools to review and manage your app at all stages of the process.
| Topic | Description |
|---|---|
| Set up your account | If your company isn’t already registered, you must register it through the Windows Certification Dashboard. |
| Get a code signing certificate | Before you can establish a Windows Certification Dashboard account, you need to get a code signing certificate to secure your digital information. |
| Test locally and upload the results | After your run the Windows App Certification Kit tests, upload the results to the Windows Certification Dashboard. |
| Manage your submission | After you submit your app for certification, you can review your submission through the Windows Certification Dashboard. |
Step 4: Promote your desktop app
| Topic | Description |
|---|---|
| Check app compatibility | If you are building an app for Windows 8.1, investigate compatibility concerns. |
| Use the logo with your app | Display the logo on packaging and in ads and other promotional materials according to the guidelines. For Windows 7 only. |
See also:
App compatibility forum: Find support from the community about compatibility and logo certification.
Windows SDK blog: Find tips and news related to app certification.
Windows Server forum: Visit the Certification forum to get answers.
Compatibility cookbook: Get info about what’s new or changed in the latest version of Windows.
What are Root Certificates for Windows10?
Certificates are like a confirmation that the message sent to you is original and not tampered with. Of course, there are methods to fake the confirmations like Lenovo’s SuperFish certificate – and we’ll talk about it in a while. This article explains what are Root Certificates in Windows and if you should update them – because Windows always shows them as non-critical updates.
How does Public Key Cryptography work
Before talking about Root Certificates, it is necessary to take a look at how cryptography works in the case of web conversations, between websites and browsers or between two individuals in the form of messages.
There are many types of cryptography out of which, two are essential and are used extensively for different purposes.
- Symmetric cryptography is used where you have a key, and only that key can be used to encrypt and decrypt messages (mostly used in email communications)
- Asymmetric cryptography, where there are two keys. One of those keys is used to encrypt a message while the other key is used to decrypt the message
Public key cryptography has a public and a private key. Messages can be decoded and encrypted using either of the two. The use of both keys is essential to complete communication. The Public key is visible to everyone and is used to make sure that the origin of the message is exactly the same as it appears to be. The Public key encrypts the data and is sent to the recipient having the public key. The recipient decrypts the data using the Private key. A trust relationship is established, and communication continues.
Both the public and private keys contain information about the Certificate Issuing Authority such as Equifax , DigiCert, Comodo, and so on. If your operating system considers the certificate-issuing authority as trustworthy, the messages are sent back and forth between the browser and the websites. If there is a problem identifying the certificate-issuing authority or if the public key is expired or corrupt, you will see a message saying There is a problem with the website’s certificate.
Now talking about public-key cryptography, it is like a bank vault. It has two keys – one with the branch manager and one with the user of the vault. The vault opens only if the two keys are used and matched. Similarly, both the public and private keys are used while establishing a connection with any website.
What are Root Certificates in Windows 10
Root Certificates are the primary level of certifications that tell a browser that the communication is genuine. This information that the communication is genuine is based upon the identification of certification authority. Your Windows operating system adds several root certificates as trusted so that your browser can use it to communicate with websites.
This also helps in encryption of communications between the browsers and websites and automatically makes other certificates under it, valid. Thus the certificate has many branches. For example, if a certificate from Comodo is installed, it will have a top-level certificate that will help web browsers communicate with websites in an encrypted fashion. As a branch in the certificate, Comodo also includes email certificates, which will automatically be trusted by browsers and email clients because the operating system has marked the root certificate as trusted.
Root Certificates determine if a communication session with a website should be opened. When a web browser approaches a website, the site gives it a public key. The browser analyses the key to see who is the certificate issuing authority, whether the authority is trusted according to Windows, the expiry date of the certificate (if the certificate is still valid) and similar things before proceeding to communicate with the website. If anything is out of order, you will get a warning, and your browser may block all communications with the website.
On the other hand, if everything is fine, messages are sent and received by the browser as communication happens. With every incoming message, the browser also checks the message with its own private key to see it is not a fraudulent message. It responds only if it can decrypt the message using its own private key. Thus, both keys are required to carry on communications. Furthermore, all the communications are carried forward in encrypted mode.
Fake Root Certificates
There are cases where companies, hackers, etc. have tried to dupe the users. The recent case of an invalid certificate being trusted as root is still doing the rounds. This was the ‘SuperFish’ certificate in Lenovo computers. The Superfish adware installed a root certificate that seemed legitimate and allowed browsers to carry on communications with websites. However, the encryption system was so weak it could easily be pried upon.
Lenovo said it wanted to enhance the shopping experience of users and instead exposed their private data to hackers on the prowl on the Internet. This private data could be anything, including credit card information, social security number, etc. If you have a Lenovo machine, make sure you do not have the adware installed by checking out the trusted certificates in your browsers. If there is one, update and run Windows Defender to get rid of the certificate. There is also an automatic removal tool released by Lenovo.
You can check for unsigned or untrusted Windows Root Certificates using Root Certificates Scanner or SigCheck.
Conclusion
Root Certificates are important so that your browsers can communicate with the websites. If you delete all the trusted certificates, out of curiosity or to stay safe, you will always get a message that you are on an untrusted connection. You can download trusted root certificates via the Microsoft Windows Root Certificates Program, if you think you do not have all the proper root certificates.
You should always check the non-critical updates once in a while to see if there are updates available for root certificates. If yes, download them using Windows Update only and not from third party sites.
There are fake certificates too but chances of you getting the fake certificates are limited – only when your computer manufacturer adds one to the list of trusted root certificates as Lenovo did or when you download root certificates from third-party websites. It is better to stick to Microsoft and let it handle the root certificates rather than going on your own to install them from anywhere on the Internet. You can also see if a root certificate is trusted by opening it and running a search on the name of the certificate issuing authority. If the authority seems reputed, you can install it or keep it. If you cannot make out the certificate issuing authority, it is better to remove it.
Where are SSL certificates are stored?
I understand how SSL works, but my question is more regarding the storage of certs on client side. To understand the exact context you can assume that I am sort of writing my own browser. My Rendering part will be done by WebKit and http request handling part will be done by libCurl. libCurl has an option called CURLOPT_CAPATH using which i can tell one folder location to libCurl and that’s what libCurl will refer to for perhaps trusted certificates authorities. But I do not know which location is that? IS it operating system specific, my browser sort of app is suppose to work on multiple plateforms.
- Where OSx and Windows keep their certificates?
- Is it one unified directory ? or its splitted in multiple locations?
- Windows keep them in registry not in directory?
multiple browsers on same operating system use the same certificate store or all of them have their on certificate store?
Do i need to worry about nss?
1 Answer 1
Where OSx and Windows keep their certificates?
OS X stores certificates in the Keychain. Windows stores certificates in the Certificate Store.
or its splitted in multiple locations?
Windows keep them in registry not in directory?
Windows stores certificates in the Certificate Store. Its backed by a file(s), but you don’t operate on the file directly.
multiple browsers on same operating system use the same certificate store or all of them have their on certificate store?
Firefox and Opera carry around their own collection of trust anchors (CA Certifcates).
Chrome uses the operating system provided store.
Safari uses the certificates in the Keychain.
IE uses uses the certificates in the Certificate Store.
I’m not sure what other browsers do. For example, I don’t know from where Iceweasel and Dillo fetch the list of trust anchors.
Do i need to worry about nss?
Password Recovery
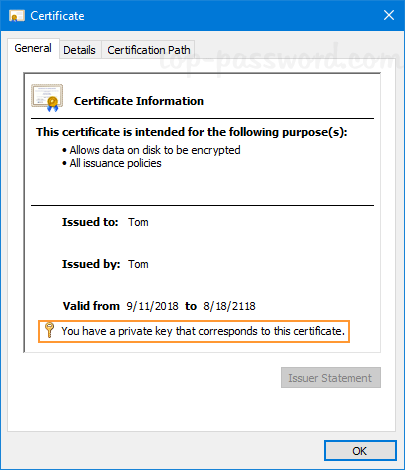
How can I get a list of installed certificates on Windows? Is there a way to check if my certificate has the private key attached? In this tutorial we’ll show you easy ways to view all certificates installed on your Windows 10 / 8 / 7 computer, so you can check the certificate status, export, import, delete or request new certificates.
Method 1: View Installed Certificates for Current User
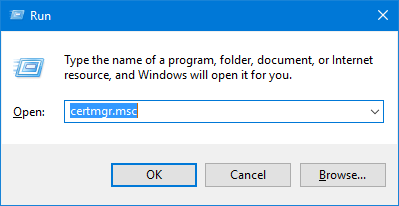
- Press the Windows key + R to bring up the Run command, type certmgr.msc and press Enter.
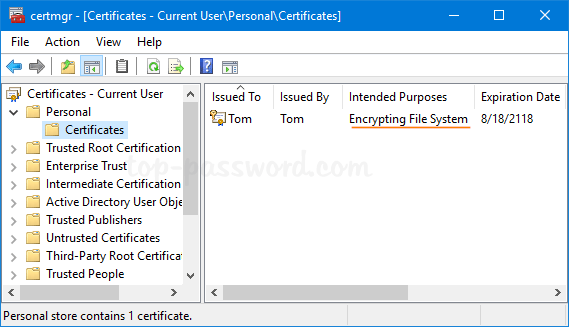
When the Certificate Manager console opens, expand any certificates folder on the left. In the right pane, you’ll see details about your certificates. Right-click on them and you can export or delete it.
By default, the EFS certificate could be found under the “Personal” -> “Certificates” folder. Double-click on the EFS certificate and you can know if it has the private key attached. Without the private key, you’re unable to decrypt your EFS files.
Method 2: View Installed Certificates for Local Computer
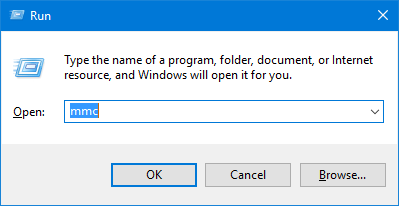
- Press the Windows key + R to bring up the Run command, type mmc and press Enter to open Microsoft Management Console.
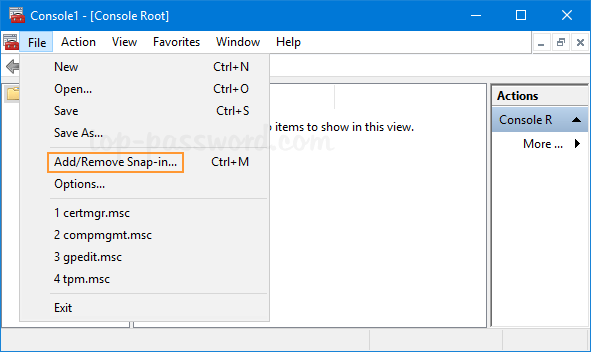
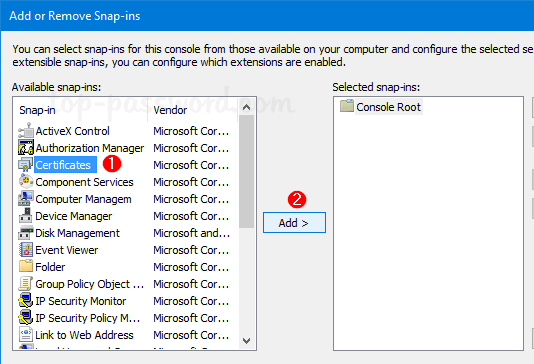
Click the File menu and then select Add/Remove Snap-in.
Select Certificates from the list of snap-ins, and click Add.
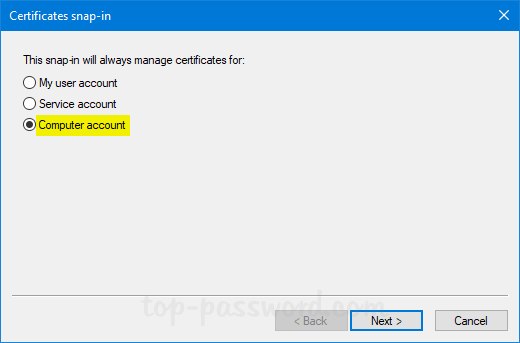
In the next dialog box, select Computer account and click Next.
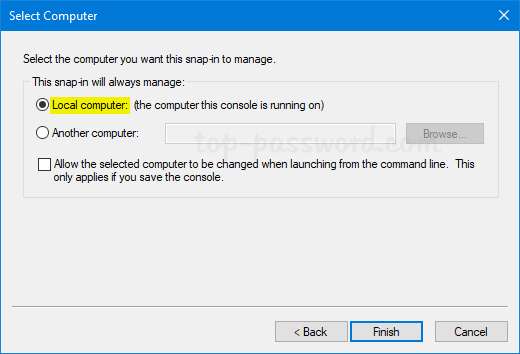
Select Local computer and click Finish.
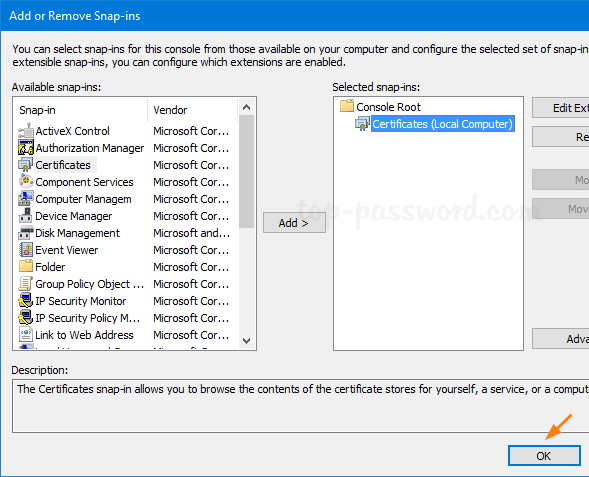
Now you’ll back at the “Add or Remove Snap-ins” window, just click OK.
When you open any certificates folder, you will see that the certificates are displayed in the right pane.