- Penetration Testing Tools
- Kali Linux Tools Listing
- WiFi-Pumpkin (ex 3vilTwinAttacker)
- WiFi-Pumpkin Description
- Plugins
- WiFi-Pumpkin Plugins
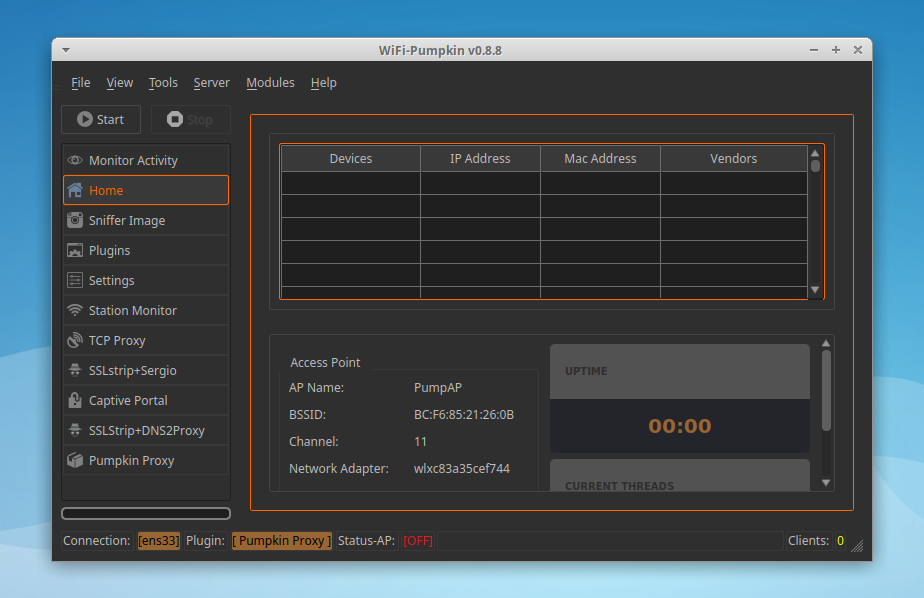
- WiFi-Pumpkin Usage Example
- How to install WiFi-Pumpkin
- Инструменты Kali Linux
- Список инструментов для тестирования на проникновение и их описание
- WiFi-Pumpkin (ранее 3vilTwinAttacker)
- Описание WiFi-Pumpkin (3vilTwinAttacker)
- Wifi pumpkin kali linux
- WiFi-Pumpkin 3 — Dangerous Access Point
- Key Features of WiFi-Pumpkin
- Installing WiFi Pumpkin3 on Kali Linux
- Using WiFi Pumpkin3 on Kali Linux
Penetration Testing Tools
Kali Linux Tools Listing
WiFi-Pumpkin (ex 3vilTwinAttacker)
WiFi-Pumpkin Description
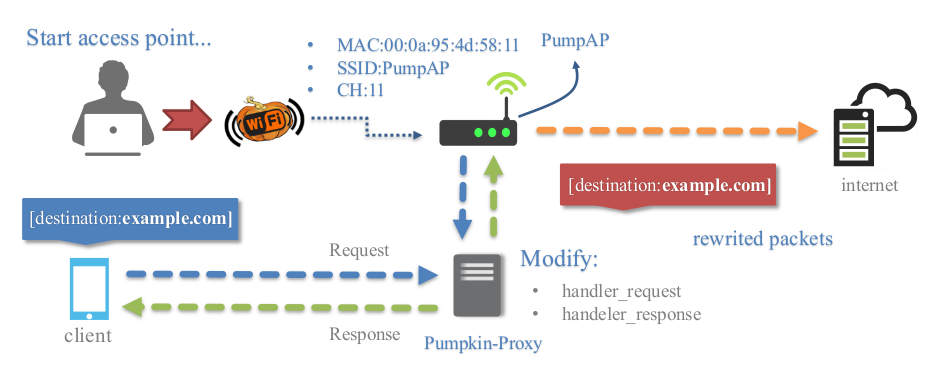
Framework for Rogue Wi-Fi Access Point Attack.
WiFi-Pumpkin is a very complete framework for auditing Wi-Fi security. The main feature is the ability to create a fake AP and make Man In The Middle attack, but the list of features is quite broad.
Features
- Rogue Wi-Fi Access Point
- Deauth Attack Clients AP
- Probe Request Monitor
- DHCP Starvation Attack
- Credentials Monitor
- Transparent Proxy
- Windows Update Attack
- Phishing Manager
- Partial Bypass HSTS protocol
- Support beef hook
- ARP Poison
- DNS Spoof
- Patch Binaries via MITM
- Karma Attacks (support hostapd-mana)
- LLMNR, NBT-NS and MDNS poisoner (Responder)
- Pumpkin-Proxy (ProxyServer (mitmproxy API))
- Capture images on the fly
- TCP-Proxy (with scapy)
Plugins
- dns2proxy — This tools offer a different features for post-explotation once you change the DNS server to a Victim.
- sslstrip2 — Sslstrip is a MITM tool that implements Moxie Marlinspike’s SSL stripping attacks based version fork @LeonardoNve/@xtr4nge.
- sergio-proxy — Sergio Proxy (a Super Effective Recorder of Gathered Inputs and Outputs) is an HTTP proxy that was written in Python for the Twisted framework.
- BDFProxy — Patch Binaries via MITM: BackdoorFactory + mitmProxy, bdfproxy-ng is a fork and review of the original BDFProxy @secretsquirrel.
- Responder — Responder an LLMNR, NBT-NS and MDNS poisoner. Author: Laurent Gaffie
WiFi-Pumpkin Plugins
Transparent Proxy
Transparent proxies(mitmproxy) that you can use to intercept and manipulate HTTP traffic modifying requests and responses, that allow to inject javascripts into the targets visited. You can easily implement a module to inject data into pages creating a python file in directory «plugins/extension/» automatically will be listed on Pumpkin-Proxy tab.
TCP-Proxy Server
A proxy that you can place between in a TCP stream. It filters the request and response streams with (scapy module) and actively modify packets of a TCP protocol that gets intercepted by WiFi-Pumpkin. this plugin uses modules to view or modify the intercepted data that possibly easiest implementation of a module, just add your custom module on «plugins/analyzers/» automatically will be listed on TCP-Proxy tab.
WiFi-Pumpkin Usage Example
How to install WiFi-Pumpkin
Installation on Kali Linux, WifiSlax, Parrot, Ubuntu
To remove 3vilTwinAttacker:
Installation on Arch Linux
Installation on BlackArch
Installation on Ubuntu, Linux Mint
Источник
Инструменты Kali Linux
Список инструментов для тестирования на проникновение и их описание
WiFi-Pumpkin (ранее 3vilTwinAttacker)
Описание WiFi-Pumpkin (3vilTwinAttacker)
Этот инструмент создаёт мошенническую точку доступа Wi-Fi, якобы для обеспечения беспроводных услуг Интернет, а на самом деле следящую за трафиком. Может использоваться для захвата учётных данных неподозревающего пользователя как перехватом данных так и фишингом.
WiFi-Pumpkin — это очень законченная платформа для аудита Wi-Fi. Главная функция — возможность создавать фальшивую ТД и выполнять атаку человек-посередине, но помимо этого список функций довольно широк.
- Фальшивая точка доступа Wi-Fi
- Деаутентификация клиентов ТД
- Наблюдение за зондирующими запросами
- Голодная (Starvation) атака DHCP
- Наблюдение за учётными данными
- Прозрачный прокси
- Атака обновления Windows
- Менеджер фишинга
- Частичный обход протокола HSTS протокола
- Поддержка beef hook
- ARP травление
- DNS спуфинг
- Пропатчивает исполнимые файлы при MITM
- Атаки Karma (поддержка hostapd-mana)
- Травитель LLMNR, NBT-NS и MDNS (Responder)
- Pumpkin-Proxy (Прокси Сервер (mitmproxy API))
- захват изображений на лету
- TCP-прокси (с scapy)
- dns2proxy — Этот инструмент предлагает различные функции последующей эксплуатации после того, как вы изменили DNS для жертвы.
- sslstrip2 — Sslstrip — это инструмент MITM (атаки человек-посередине), который реализует атаку раскрытия SSL, предложенную Moxie Marlinspike, версия основана на форке @LeonardoNve/@xtr4nge.
- sergio-proxy — Sergio Proxy (a Super Effective Recorder of Gathered Inputs and Outputs) — это HTTP прокси, написан на Python для Twisted framework.
- BDFProxy-ng — Пропатчивает исполнимые файлы при MITM: BackdoorFactory + mitmProxy, bdfproxy-ng — это ответвление и пересмотр оригинального BDFProxy.
- Responder — травитель LLMNR, NBT-NS и MDNS.
Прозрачный прокси
Прозрачные прокси вы можете использовать для вмешательства и манипулирования HTTP/HTTPS трафиком, модифицируя запросы и ответы, что позволяет внедрить javascript’ы в посещённые целью страницы. Вы можете с лёгкостью реализовать внедрение данных в страницы, создав файл на python в директории «Proxy», и он автоматически будет показан в списке на вкладке PumpProxy.
Источник
Wifi pumpkin kali linux
WiFi-Pumpkin — Framework for Rogue Wi-Fi Access Point Attack
The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target. It comes stuffed with features, including rogue Wi-Fi access points, deauth attacks on client APs, a probe request and credentials monitor, transparent proxy, Windows update attack, phishing manager, ARP Poisoning, DNS Spoofing, Pumpkin-Proxy, and image capture on the fly. moreover, the WiFi-Pumpkin is a very complete framework for auditing Wi-Fi security check the list of features is quite broad.
or download .deb file to install
refer to the wiki for Installation
- Rogue Wi-Fi Access Point
- Deauth Attack Clients AP
- Probe Request Monitor
- DHCP Starvation Attack
- Credentials Monitor
- Transparent Proxy
- Windows Update Attack
- Phishing Manager
- Partial Bypass HSTS protocol
- Support beef hook
- ARP Poison
- DNS Spoof
- Patch Binaries via MITM (BDF-Proxy)
- LLMNR, NBT-NS and MDNS poisoner (Responder)
- Pumpkin-Proxy (ProxyServer (mitmproxy API))
- Capture images on the fly
- TCP-Proxy (with scapy)
- Moduled plugins and proxys
- Wireless Mode support hostapd-mana/hostapd-karma attacks
- Capitve-portals [new]
| Plugin | Description |
|---|---|
| Dns2proxy | This tools offer a different features for post-explotation once you change the DNS server to a Victim. |
| Sstrip2 | Sslstrip is a MITM tool that implements Moxie Marlinspike’s SSL stripping attacks based version fork @LeonardoNve/@xtr4nge. |
| Sergio_proxy | Sergio Proxy (a Super Effective Recorder of Gathered Inputs and Outputs) is an HTTP proxy that was written in Python for the Twisted framework. |
| BDFProxy | Patch Binaries via MITM: BackdoorFactory + mitmProxy, bdfproxy-ng is a fork and review of the original BDFProxy @secretsquirrel. |
| Responder | Responder an LLMNR, NBT-NS and MDNS poisoner. Author: Laurent Gaffie |
| PumpkinProxy | Intercepting HTTP data, this proxy server that allows to intercept requests and response on the fly |
| CaptivePortals | Captive-Portal allow the Attacker block Internet access for users until they open the page login page where a password is required before being allowed to browse the web. |
Transparent proxies(mitmproxy) that you can use to intercept and manipulate HTTP traffic modifying requests and responses, that allow to inject javascripts into the targets visited. You can easily implement a module to inject data into pages creating a python file in directory «plugins/extension/» automatically will be listed on Pumpkin-Proxy tab.
Источник
WiFi-Pumpkin 3 — Dangerous Access Point
Sometime on some places we got free WiFi networks. Free WiFi is always a weakness of modern day people. As a cybersecurity expert we always say to not connect to publicly available networks. But why?
In our this detailed article we learn how WiFi-Pumpkin3 works on Kali Linux 2020 and how black-hat guys steel other’s credentials using a rouge access point. We also discuss about how to be safe.
We can do this manually, but using Aircrack-ng, configuring the IP tables and using some other tools are time consuming. WiFi-Pumpkin3 do these manually.
Key Features of WiFi-Pumpkin
- Rouge WiFi access point.
- Deauth attacks on clients AP.
- Intercept, inspect, modify and replay web traffic.
- Probe request monitor.
- DHCP Starvation attack.
- Credential monitor.
- Transparent proxy.
- Windows update attack.
- Phishing manager.
- ARP poisoning.
- DNS spoof.
- Pumpkin proxy (MITM proxy server).
- Capture images on the fly.
Installing WiFi Pumpkin3 on Kali Linux
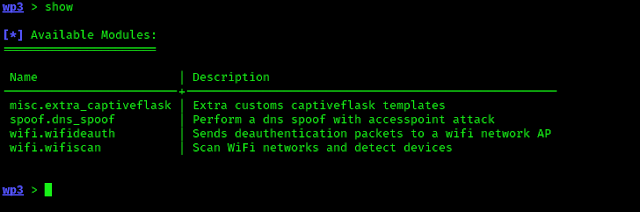
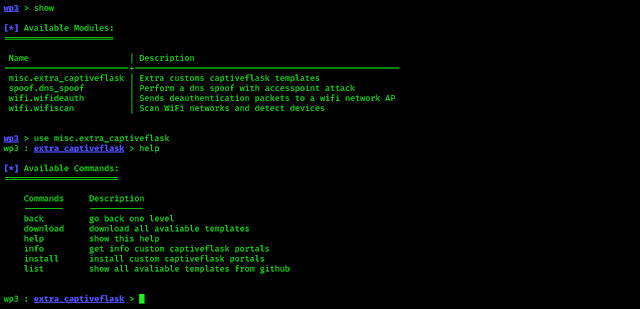
Using WiFi Pumpkin3 on Kali Linux
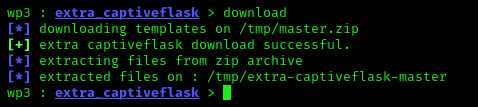
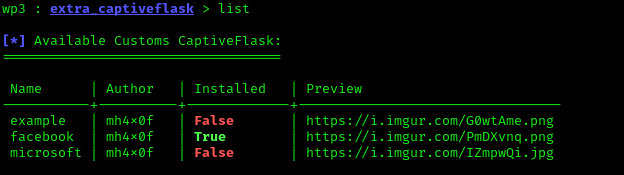
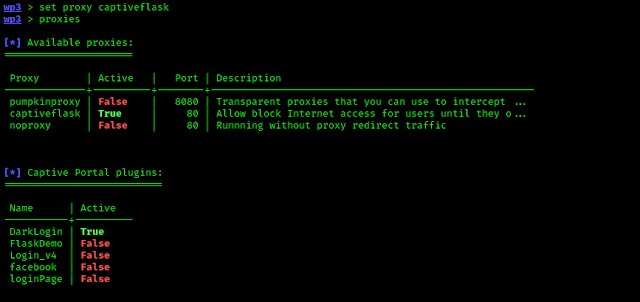
Here we can see the captiveflask module. to use it we simply apply use command:
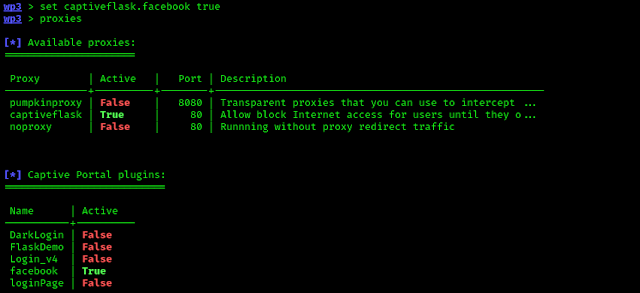
In the above screenshot we can see that Facebook is set to false, so we are going to change it. To make it «true» we run following command:
Now everything is done we can run the WiFiPumpkin3 tool by just using following command:
Then our created WiFi access point will say «Tap here to sign in to network». Our created rouge access point will force our Android device to sign in. It will open Facebook login page as we can see in the following screenshot.
When we puts the credentials here it will be showed on our WiFiPumpkin3’s terminal.
In the above screenshot we can see that we got the credentials here.
That is why we always told that publicly available free WiFi might give us trouble. We need to always be aware.
To create a CapiveFlask proxy we need internet connection. But if we are using a laptop and a home WiFi network for internet then we need to disconnect our WiFi to create an access point.
Then what about the internet connection?
We can get it from LAN connection. In our case we have used a separate USB WiFi adapter (wlan1) to get internet connection for proxy and create the rouge access point using laptop’s inbuilt WiFi module (wlan0).
Note:- This tutorial is for educational purpose only. Stealing account credential is a serious crime. We showed this on our own devices for public awareness. If anyone do any illegal activity then we are not responsible for that.
This is how a malicious access point can be created very easily using WiFiPumpkin3 on Kali Linux 2021. Not only that WiFiPumpkin3 is capable to perform more dangerous attacks. We can try other methods. With some programming knowledge we can create our own captive portals for batter social engineering.
Liked our articles? Make sure to subscribe our e-mail subscription for free. (We send mail whenever new article releases). We are also available on GitHub & Twitter we also posts updates there.
For any problem or anything, we always happy to help. Just leave a comment in the comment section below. We always reply.
Источник