- Как включить предварительную загрузку ПИН-кода BitLocker в Windows
- Шаг первый: включите BitLocker (если вы этого еще не сделали)
- Шаг второй: Включите ПИН-код запуска в редакторе групповой политики
- Шаг третий: добавьте PIN-код к вашему диску
- Как изменить свой PIN-код BitLocker
- Как удалить ПИН-код
- BitLocker Countermeasures
- Protection before startup
- Trusted Platform Module
- UEFI and Secure Boot
- BitLocker and reset attacks
- Security policies
- Pre-boot authentication
- Protecting Thunderbolt and other DMA ports
- Attack countermeasures
- Bootkits and rootkits
- Brute force attacks against a PIN
- DMA attacks
- Paging file, crash dump, and Hyberfil.sys attacks
- Memory remanence
- Attacker countermeasures
- Attacker without much skill or with limited physical access
- Attacker with skill and lengthy physical access
Как включить предварительную загрузку ПИН-кода BitLocker в Windows
Если вы шифруете системный диск Windows с помощью BitLocker, вы можете добавить PIN-код для дополнительной безопасности. Вам нужно будет вводить PIN-код каждый раз, когда вы включаете компьютер, прежде чем Windows запустится. Это отдельный от PIN-кода входа в систему, который вы вводите после загрузки Windows.
Предварительный PIN-код предотвращает автоматическую загрузку ключа шифрования в системную память в процессе загрузки, что защищает от атак прямого доступа к памяти (DMA) на системы с уязвимым для них оборудованием. Документация Microsoft объясняет это более подробно.
Шаг первый: включите BitLocker (если вы этого еще не сделали)
Это функция BitLocker, поэтому вы должны использовать шифрование BitLocker для установки ПИН-кода перед загрузкой. Это доступно только в Профессиональных и Корпоративных выпусках Windows. Прежде чем вы сможете установить PIN-код, вы должны включить BitLocker для вашего системного диска.
Обратите внимание, что если вы не сможете включить BitLocker на компьютере без доверенного платформенного модуля, вам будет предложено создать пароль запуска, который будет использоваться вместо доверенного платформенного модуля. Следующие шаги необходимы только при включении BitLocker на компьютерах с доверенными платформенными модулями, которые есть на большинстве современных компьютеров.
Если у вас есть домашняя версия Windows, вы не сможете использовать BitLocker. Вместо этого у вас может быть функция шифрования устройства, но она работает не так, как BitLocker, и не позволяет предоставить ключ запуска.
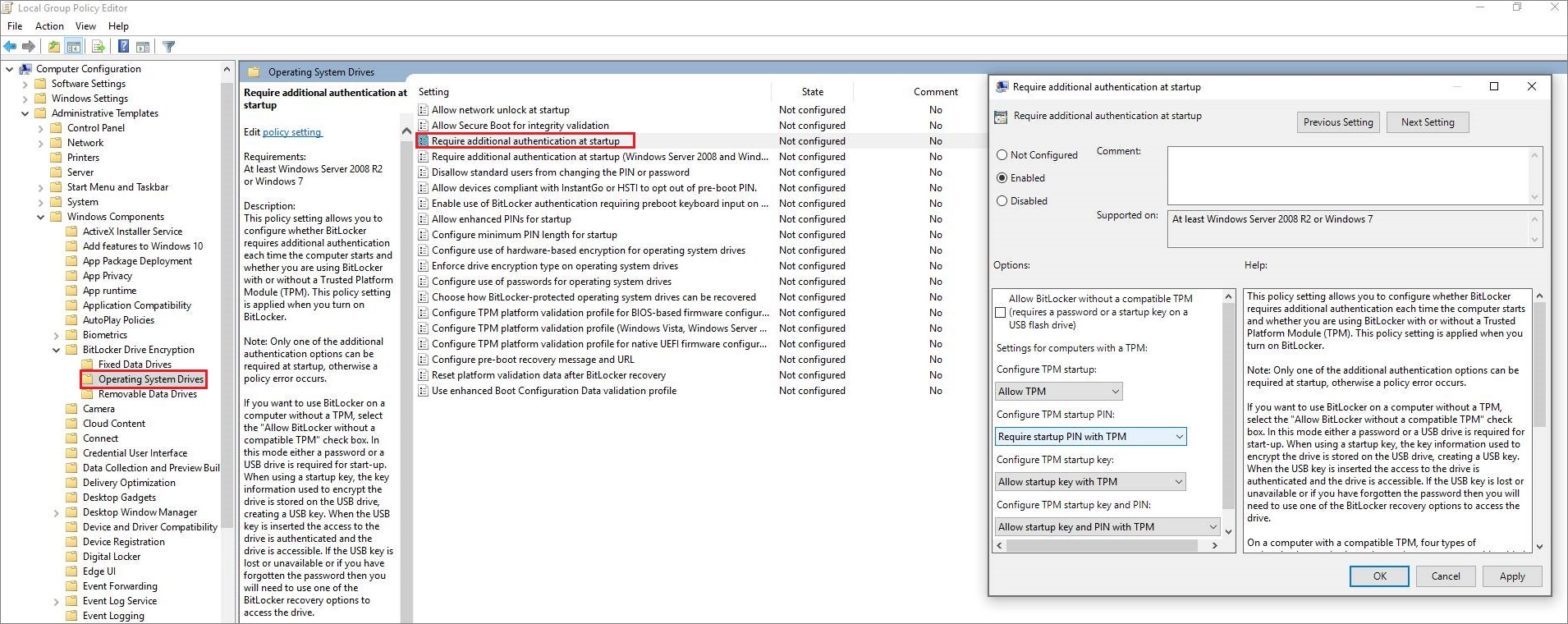
Шаг второй: Включите ПИН-код запуска в редакторе групповой политики
После того, как вы включили BitLocker, вам нужно будет приложить все усилия, чтобы включить с ним ПИН-код. Это требует изменения параметров групповой политики. Чтобы открыть редактор групповой политики, нажмите Windows + R, введите «gpedit.msc» в диалоговом окне «Выполнить» и нажмите Enter.
Перейдите в раздел Конфигурация компьютера> Административные шаблоны> Компоненты Windows> Шифрование диска BitLocker> Диски операционной системы в окне групповой политики.
Дважды щелкните параметр «Требовать дополнительную аутентификацию при запуске» на правой панели.
Выберите «Включено» в верхней части окна здесь. Затем установите флажок «Настроить ПИН-код запуска TPM» и выберите «Требовать ПИН-код запуска с TPM». Нажмите «ОК», чтобы сохранить изменения.
Шаг третий: добавьте PIN-код к вашему диску
Теперь вы можете использовать команду manage-bde чтобы добавить PIN-код на диск с шифрованием BitLocker.
Для этого запустите окно командной строки от имени администратора. В Windows 10 или 8 щелкните правой кнопкой мыши кнопку «Пуск» и выберите «Командная строка (Admin)». В Windows 7 найдите ярлык «Командная строка» в меню «Пуск», щелкните его правой кнопкой мыши и выберите «Запуск от имени администратора».
Запустите следующую команду. Приведенная ниже команда работает на вашем диске C :, поэтому, если вам требуется ключ запуска для другого диска, введите его букву вместо c:
Вам будет предложено ввести свой PIN-код здесь. При следующей загрузке вам будет предложено ввести этот PIN-код.
Чтобы дважды проверить, был ли добавлен защитник TPMAndPIN, вы можете выполнить следующую команду:
(Защитная кнопка «Числовой пароль», отображаемая здесь, является вашим ключом восстановления.)
Как изменить свой PIN-код BitLocker
Чтобы изменить ПИН-код в будущем, откройте окно командной строки от имени администратора и выполните следующую команду:
Вам нужно будет ввести и подтвердить свой новый PIN-код, прежде чем продолжить.
Как удалить ПИН-код
Если вы передумали и хотите прекратить использование PIN-кода позже, вы можете отменить это изменение.
Во-первых, вам нужно перейти в окно групповой политики и изменить опцию обратно на «Разрешить стартовый ПИН с TPM». Вы не можете оставить параметр «Требовать ПИН-код запуска с TPM», иначе Windows не позволит вам удалить ПИН-код.
Затем откройте окно командной строки от имени администратора и выполните следующую команду:
Это заменит требование «TPMandPIN» на требование «TPM», удалив PIN-код. Ваш диск BitLocker автоматически разблокируется через TPM вашего компьютера при загрузке.
Чтобы убедиться, что это выполнено успешно, снова введите команду status:
Если вы забудете ПИН-код, вам нужно будет предоставить код восстановления BitLocker, который вы должны были сохранить в безопасном месте, когда вы включили BitLocker для системного диска.
BitLocker Countermeasures
Applies to
Windows uses technologies including Trusted Platform Module (TPM), Secure Boot, and Measured Boot to help protect BitLocker encryption keys against attacks. BitLocker is part of a strategic approach to securing data against offline attacks through encryption technology. Data on a lost or stolen computer is vulnerable. For example, there could be unauthorized access, either by running a software attack tool against it or by transferring the computer’s hard disk to a different computer.
BitLocker helps mitigate unauthorized data access on lost or stolen computers before the authorized operating system is started by:
- Encrypting volumes on your computer. For example, you can turn on BitLocker for your operating system volume, or a volume on a fixed or removable data drive (such as a USB flash drive, SD card, and so on). Turning on BitLocker for your operating system volume encrypts all system files on the volume, including the paging files and hibernation files. The only exception is for the System partition, which includes the Windows Boot Manager and minimal boot collateral required for decryption of the operating system volume after the key is unsealed.
- Ensuring the integrity of early boot components and boot configuration data. On devices that have a TPM version 1.2 or higher, BitLocker uses the enhanced security capabilities of the TPM to make data accessible only if the computer’s BIOS firmware code and configuration, original boot sequence, boot components, and BCD configuration all appear unaltered and the encrypted disk is located in the original computer. On systems that leverage TPM PCR[7], BCD setting changes deemed safe are permitted to improve usability.
The next sections provide more details about how Windows protects against various attacks on the BitLocker encryption keys in Windows 10, Windows 8.1, and Windows 8.
For more information about how to enable the best overall security configuration for devices beginning with Windows 10 version 1803, see Standards for a highly secure Windows 10 device.
Protection before startup
Before Windows starts, you must rely on security features implemented as part of the device hardware and firmware, including TPM and Secure Boot. Fortunately, many modern computers feature a TPM and Secure Boot.
Trusted Platform Module
A TPM is a microchip designed to provide basic security-related functions, primarily involving encryption keys. On some platforms, TPM can alternatively be implemented as a part of secure firmware. BitLocker binds encryption keys with the TPM to ensure that a computer has not been tampered with while the system was offline. For more info about TPM, see Trusted Platform Module.
UEFI and Secure Boot
Unified Extensible Firmware Interface (UEFI) is a programmable boot environment that initializes devices and starts the operating system’s bootloader.
The UEFI specification defines a firmware execution authentication process called Secure Boot. Secure Boot blocks untrusted firmware and bootloaders (signed or unsigned) from being able to start on the system.
By default, BitLocker provides integrity protection for Secure Boot by utilizing the TPM PCR[7] measurement. An unauthorized EFI firmware, EFI boot application, or bootloader cannot run and acquire the BitLocker key.
BitLocker and reset attacks
To defend against malicious reset attacks, BitLocker leverages the TCG Reset Attack Mitigation, also known as MOR bit (Memory Overwrite Request), before extracting keys into memory.
This does not protect against physical attacks where an attacker opens the case and attacks the hardware.
Security policies
The next sections cover pre-boot authentication and DMA policies that can provide additional protection for BitLocker.
Pre-boot authentication
Pre-boot authentication with BitLocker is a policy setting that requires the use of either user input, such as a PIN, a startup key, or both to authenticate prior to making the contents of the system drive accessible. The Group Policy setting is Require additional authentication at startup and the corresponding setting in the BitLocker CSP is SystemDrivesRequireStartupAuthentication.
BitLocker accesses and stores the encryption keys in memory only after pre-boot authentication is completed. If Windows can’t access the encryption keys, the device can’t read or edit the files on the system drive. The only option for bypassing pre-boot authentication is entering the recovery key.
Pre-boot authentication is designed to prevent the encryption keys from being loaded to system memory without the trusted user supplying another authentication factor such as a PIN or startup key. This helps mitigate DMA and memory remanence attacks.
On computers with a compatible TPM, operating system drives that are BitLocker-protected can be unlocked in four ways:
- TPM-only. Using TPM-only validation does not require any interaction with the user to unlock and provide access to the drive. If the TPM validation succeeds, the user sign in experience is the same as a standard logon. If the TPM is missing or changed or if BitLocker detects changes to the BIOS or UEFI code or configuration, critical operating system startup files, or the boot configuration, BitLocker enters recovery mode, and the user must enter a recovery password to regain access to the data. This option is more convenient for sign-in but less secure than the other options, which require an additional authentication factor.
- TPM with startup key. In addition to the protection that the TPM-only provides, part of the encryption key is stored on a USB flash drive, referred to as a startup key. Data on the encrypted volume cannot be accessed without the startup key.
- TPM with PIN. In addition to the protection that the TPM provides, BitLocker requires that the user enter a PIN. Data on the encrypted volume cannot be accessed without entering the PIN. TPMs also have anti-hammering protection that is designed to prevent brute force attacks that attempt to determine the PIN.
- TPM with startup key and PIN. In addition to the core component protection that the TPM-only provides, part of the encryption key is stored on a USB flash drive, and a PIN is required to authenticate the user to the TPM. This configuration provides multifactor authentication so that if the USB key is lost or stolen, it cannot be used for access to the drive, because the correct PIN is also required.
In the following Group Policy example, TPM + PIN is required to unlock an operating system drive:
Pre-boot authentication with a PIN can mitigate an attack vector for devices that use a bootable eDrive because an exposed eDrive bus can allow an attacker to capture the BitLocker encryption key during startup. Pre-boot authentication with a PIN can also mitigate DMA port attacks during the window of time between when BitLocker unlocks the drive and Windows boots to the point that Windows can set any port-related policies that have been configured.
On the other hand, Pre-boot authentication prompts can be inconvenient to users. In addition, users who forget their PIN or lose their startup key are denied access to their data until they can contact their organization’s support team to obtain a recovery key. Pre-boot authentication can also make it more difficult to update unattended desktops and remotely administered servers because a PIN needs to be entered when a computer reboots or resumes from hibernation.
To address these issues, you can deploy BitLocker Network Unlock. Network Unlock allows systems within the physical enterprise security perimeter that meet the hardware requirements and have BitLocker enabled with TPM+PIN to boot into Windows without user intervention. It requires direct ethernet connectivity to an enterprise Windows Deployment Services (WDS) server.
Protecting Thunderbolt and other DMA ports
There are a few different options to protect DMA ports, such as Thunderboltв„ў3. Beginning with Windows 10 version 1803, new Intel-based devices have kernel protection against DMA attacks via Thunderboltв„ў 3 ports enabled by default. This Kernel DMA Protection is available only for new systems beginning with Windows 10 version 1803, as it requires changes in the system firmware and/or BIOS.
You can use the System Information desktop app (MSINFO32) to check if a device has kernel DMA protection enabled:
If kernel DMA protection not enabled, follow these steps to protect Thunderboltв„ў 3 enabled ports:
Require a password for BIOS changes
Intel Thunderbolt Security must be set to User Authorization in BIOS settings. Please refer to Intel Thunderboltв„ў 3 and Security on Microsoft WindowsВ® 10 Operating System documentation
Additional DMA security may be added by deploying policy (beginning with Windows 10 version 1607):
For Thunderbolt v1 and v2 (DisplayPort Connector), refer to the “Thunderbolt Mitigation” section in KB 2516445. For SBP-2 and 1394 (a.k.a. Firewire), refer to the “SBP-2 Mitigation” section in KB 2516445.
Attack countermeasures
This section covers countermeasures for specific types attacks.
Bootkits and rootkits
A physically-present attacker might attempt to install a bootkit or rootkit-like piece of software into the boot chain in an attempt to steal the BitLocker keys. The TPM should observe this installation via PCR measurements, and the BitLocker key will not be released. This is the default configuration.
A BIOS password is recommended for defense-in-depth in case a BIOS exposes settings that may weaken the BitLocker security promise. Intel Boot Guard and AMD Hardware Verified Boot support stronger implementations of Secure Boot that provide additional resilience against malware and physical attacks. Intel Boot Guard and AMD Hardware Verified Boot are part of platform boot verification standards for a highly secure Windows 10 device.
Brute force attacks against a PIN
Require TPM + PIN for anti-hammering protection.
DMA attacks
Paging file, crash dump, and Hyberfil.sys attacks
These files are secured on an encrypted volume by default when BitLocker is enabled on OS drives. It also blocks automatic or manual attempts to move the paging file.
Memory remanence
Enable Secure Boot and require a password to change BIOS settings. For customers requiring protection against these advanced attacks, configure a TPM+PIN protector, disable Standby power management, and shut down or hibernate the device before it leaves the control of an authorized user.
Attacker countermeasures
The following sections cover mitigations for different types of attackers.
Attacker without much skill or with limited physical access
Physical access may be limited by a form factor that does not expose buses and memory. For example, there are no external DMA-capable ports, no exposed screws to open the chassis, and memory is soldered to the mainboard. This attacker of opportunity does not use destructive methods or sophisticated forensics hardware/software.
- Pre-boot authentication set to TPM only (the default)
Attacker with skill and lengthy physical access
Targeted attack with plenty of time; this attacker will open the case, will solder, and will use sophisticated hardware or software.
Pre-boot authentication set to TPM with a PIN protector (with a sophisticated alphanumeric PIN to help the TPM anti-hammering mitigation).
Disable Standby power management and shut down or hibernate the device before it leaves the control of an authorized user. This can be set using Group Policy:
- Computer Configuration|Policies|Administrative Templates|Windows Components|File Explorer|Show hibernate in the power options menu
- Computer Configuration|Policies|Administrative Templates|System|Power Management|Sleep Settings|Allow standby states (S1-S3) when sleeping (plugged in)
- Computer Configuration|Policies|Administrative Templates|System|Power Management|Sleep Settings|Allow standby states (S1-S3) when sleeping (on battery)
These settings are Not configured by default.
For some systems, bypassing TPM-only may require opening the case, and may require soldering, but could possibly be done for a reasonable cost. Bypassing a TPM with a PIN protector would cost much more, and require brute forcing the PIN. With a sophisticated enhanced PIN, it could be nearly impossible. The Group Policy setting for enhanced PIN is:
Computer Configuration|Administrative Templates|Windows Components|BitLocker Drive Encryption|Operating System Drives|Allow enhanced PINs for startup
This setting is Not configured by default.
For secure administrative workstations, Microsoft recommends TPM with PIN protector and disable Standby power management and shut down or hibernate the device.