- Guest access in SMB2 disabled by default in Windows
- Symptoms
- Log entry 1
- Guidance
- Log entry 2
- Guidance
- Cause
- Resolution
- More information
- Как включить функцию Share (Поделиться) в Windows 10
- Как включить скрытую страницу Share в приложении Параметры
- Set up a shared or guest PC with Windows 10
- Shared PC mode concepts
- Account models
- Account management
- Maintenance and sleep
- App behavior
- Customization
- Configuring Shared PC mode for Windows
- Create a provisioning package for shared use
- Apply the provisioning package
- Guidance for accounts on shared PCs
- Policies set by shared PC mode
Guest access in SMB2 disabled by default in Windows
This article describes information about Windows disabling guest access in SMB2 by default, and provides settings to enable insecure guest logons in Group Policy. However, this is generally not recommended.
Original product version: В Windows 10 — all editions, Windows Server 2019, Windows Server 2016
Original KB number: В 4046019
Symptoms
In Windows 10, Windows Server 2019, or Windows Server 2016, the SMB2 client no longer allows the following actions:
- Guest account access to a remote server.
- Fall back to the Guest account after invalid credentials are provided.
SMBv2 has the following behavior in these versions of Windows:
- Windows 10 Enterprise and Windows 10 Education no longer allow a user to connect to a remote share by using guest credentials by default, even if the remote server requests guest credentials.
- Windows Server 2016 Datacenter and Standard editions no longer allow a user to connect to a remote share by using guest credentials by default, even if the remote server requests guest credentials.
- Windows 10 Home and Professional editions are unchanged from their previous default behavior.
If you try to connect to devices that request credentials of a guest instead of appropriate authenticated principals, you may receive the following error message:
You can’t access this shared folder because your organization’s security policies block unauthenticated guest access. These policies help protect your PC from unsafe or malicious devices on the network.
Also, if a remote server tries to force you to use guest access, or if an administrator enables guest access, the following entries are logged in the SMB Client event log:
Log entry 1
Guidance
This event indicates that the server tried to log on the user as an unauthenticated guest but was denied by the client. Guest logons do not support standard security features such as signing and encryption. So, guest logons are vulnerable to man-in-the-middle attacks that can expose sensitive data on the network. Windows disables insecure (nonsecure) guest logons by default. We recommend that you don’t enable insecure guest logons.
Log entry 2
Default registry value:
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\LanmanWorkstation\Parameters] «AllowInsecureGuestAuth»=dword:0
Configured registry value:
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\LanmanWorkstation\Parameters] «AllowInsecureGuestAuth»=dword:1
Guidance
This event indicates that an administrator has enabled insecure guest logons. An insecure guest logon occurs when a server logs on the user as an unauthenticated guest. It typically occurs in response to an authentication failure. Guest logons do not support standard security features, such as signing and encryption. So, allowing guest logons makes the client vulnerable to man-in-the-middle attacks that can expose sensitive data on the network. Windows disables insecure guest logons by default. We recommend that you don’t enable insecure guest logons.
Cause
This change in default behavior is by design and is recommended by Microsoft for security.
A malicious computer that impersonates a legitimate file server could allow users to connect as guests without their knowledge. We recommend that you don’t change this default setting. If a remote device is configured to use guest credentials, an administrator should disable guest access to that remote device and configure correct authentication and authorization.
Windows and Windows Server have not enabled guest access or allowed remote users to connect as guest or anonymous users since Windows 2000. Only third-party remote devices might require guest access by default. Microsoft-provided operating systems do not.
Resolution
If you want to enable insecure guest access, you can configure the following Group Policy settings:
- Open the Local Group Policy Editor (gpedit.msc).
- In the console tree, select Computer Configuration >Administrative Templates >Network >Lanman Workstation.
- For the setting, right-click Enable insecure guest logons and select Edit.
- Select Enabled and select OK.
By enabling insecure guest logons, this setting reduces the security of Windows clients.
More information
This setting has no effect on SMB1 behavior. SMB1 continues to use guest access and guest fallback.
SMB1 is uninstalled by default in latest Windows 10 and Windows Server configurations. For more information, see SMBv1 is not installed by default in Windows 10 version 1709, Windows Server version 1709 and later versions.
Как включить функцию Share (Поделиться) в Windows 10
При помощи приложения Параметры можно настроить множество опций, но казалось, что возможность делиться контентом можно настроить на странице Share. На самом деле это не так. Эти опции по неизвестным причинам в системе Windows 10 скрыты. Если вы хотите настроить использование кнопки Share в браузере Microsoft Edge, приложениях магазина Windows Store и проводнике, нужно активировать секретную скрытую страницу настроек Share.
В этом руководстве по Windows 10 мы поговорим о шагах по редактированию реестра для включения секретной страницы Share, где можно настраивать разные опции обмена контентом.
Как включить скрытую страницу Share в приложении Параметры
Важно: не следует забывать о том, что редактирование реестра может повредить операционную систему и компьютер станет работать некорректно. Перед внесением изменений в реестр рекомендуется выполнить резервное копирование системы.
- Откройте окно Выполнить при помощи сочетания клавиш Windows + R.
- Введите команду regedit.
- Перейдите по адресу HKEY_CURRENT_USER\\Control Panel.
- Справа нажмите правой кнопкой мыши, выберите команду Создать параметр DWORD 32 бита.
После этого в приложении Параметры должна появиться новая страница Share.
Для изменения опций обмена сделайте следующее: откройте Параметры > Система > Поделиться (Share). На этой странице можно устанавливать приложения, которым позволено делиться контентом, количество объектов на странице и отображение наиболее часто используемых приложений наверху списка. Вызвать боковую панель Share (Поделиться) можно при помощи комбинации клавиш Win + H.
Для просмотра изменений откройте приложение магазина Windows Store, браузер Edge или проводник и нажмите кнопку Share.
Если захотите убрать эту страницу, выполните вышеописанные шаги, в пункте 6 поменяв значение с 1 на 0.
Set up a shared or guest PC with Windows 10
Applies to
Windows 10, version 1607, introduced shared PC mode, which optimizes Windows 10 for shared use scenarios, such as touchdown spaces in an enterprise and temporary customer use in retail. You can apply shared PC mode to Windows 10 Pro, Pro Education, Education, and Enterprise.
If you’re interested in using Windows 10 for shared PCs in a school, see Use Set up School PCs app which provides a simple way to configure PCs with shared PC mode plus additional settings specific for education.
Shared PC mode concepts
A Windows 10 PC in shared PC mode is designed to be management- and maintenance-free with high reliability. In shared PC mode, only one user can be signed in at a time. When the PC is locked, the currently signed in user can always be signed out at the lock screen.
Account models
It is intended that shared PCs are joined to an Active Directory or Azure Active Directory domain by a user with the necessary rights to perform a domain join as part of a setup process. This enables any user that is part of the directory to sign-in to the PC. If using Azure Active Directory Premium, any domain user can also be configured to sign in with administrative rights. Additionally, shared PC mode can be configured to enable a Guest option on the sign-in screen, which doesn’t require any user credentials or authentication, and creates a new local account each time it is used. Windows 10, version 1703, introduces a kiosk mode account. Shared PC mode can be configured to enable a Kiosk option on the sign-in screen, which doesn’t require any user credentials or authentication, and creates a new local account each time it is used to run a specified app in assigned access (kiosk) mode.
Account management
When the account management service is turned on in shared PC mode, accounts are automatically deleted. Account deletion applies to Active Directory, Azure Active Directory, and local accounts that are created by the Guest and Kiosk options. Account management is performed both at sign-off time (to make sure there is enough disk space for the next user) as well as during system maintenance time periods. Shared PC mode can be configured to delete accounts immediately at sign-out or when disk space is low. In Windows 10, version 1703, an inactive option is added which deletes accounts if they haven’t signed in after a specified number of days.
Maintenance and sleep
Shared PC mode is configured to take advantage of maintenance time periods which run while the PC is not in use. Therefore, sleep is strongly recommended so that the PC can wake up when it is not in use to perform maintenance, clean up accounts, and run Windows Update. The recommended settings can be set by choosing SetPowerPolicies in the list of shared PC options. Additionally, on devices without Advanced Configuration and Power Interface (ACPI) wake alarms, shared PC mode will always override real-time clock (RTC) wake alarms to be allowed to wake the PC from sleep (by default, RTC wake alarms are off). This ensures that the widest variety of hardware will take advantage of maintenance periods.
While shared PC mode does not configure Windows Update itself, it is strongly recommended to configure Windows Update to automatically install updates and reboot (if necessary) during maintenance hours. This will help ensure the PC is always up to date and not interrupting users with updates.
Use one of the following methods to configure Windows Update:
- Group Policy: Set Computer Configuration > Administrative Templates > Windows Components > Windows Update > Configure Automatic Updates to 4 and check Install during automatic maintenance.
- MDM: Set Update/AllowAutoUpdate to 4 .
- Provisioning: In Windows Imaging and Configuration Designer (ICD), set Policies/Update/AllowAutoUpdate to 4 .
App behavior
Apps can take advantage of shared PC mode with the following three APIs:
- IsEnabled — This informs apps when the PC has been configured for shared use scenarios. For example, an app might only download content on demand on a device in shared PC mode, or might skip first run experiences.
- ShouldAvoidLocalStorage — This informs apps when the PC has been configured to not allow the user to save to the local storage of the PC. Instead, only cloud save locations should be offered by the app or saved automatically by the app.
- IsEducationEnvironment — This informs apps when the PC is used in an education environment. Apps may want to handle diagnostic data differently or hide advertising functionality.
Customization
Shared PC mode exposes a set of customizations to tailor the behavior to your requirements. These customizations are the options that you’ll set either using MDM or a provisioning package as explained in Configuring Shared PC mode for Windows. The options are listed in the following table.
| Setting | Value |
|---|---|
| EnableSharedPCMode | Set as True. If this is not set to True, shared PC mode is not turned on and none of the other settings apply. This setting controls this API: IsEnabled Some of the remaining settings in SharedPC are optional, but we strongly recommend that you also set EnableAccountManager to True. |
| AccountManagement: AccountModel | This option controls how users can sign-in on the PC. Choosing domain-joined will enable any user in the domain to sign-in. Specifying the guest option will add the Guest option to the sign-in screen and enable anonymous guest access to the PC. — Only guest allows anyone to use the PC as a local standard (non-admin) account. — Domain-joined only allows users to sign in with an Active Directory or Azure AD account. — Domain-joined and guest allows users to sign in with an Active Directory, Azure AD, or local standard account. |
| AccountManagement: DeletionPolicy | — Delete immediately will delete the account on sign-out. — Delete at disk space threshold will start deleting accounts when available disk space falls below the threshold you set for DiskLevelDeletion, and it will stop deleting accounts when the available disk space reaches the threshold you set for DiskLevelCaching. Accounts are deleted in order of oldest accessed to most recently accessed. Example: The caching number is 50 and the deletion number is 25. Accounts will be cached while the free disk space is above 25%. When the free disk space is less than 25% (the deletion number) at a maintenance period, accounts will be deleted (oldest last used first) until the free disk space is above 50% (the caching number). Accounts will be deleted immediately at sign off of an account if free space is under the deletion threshold and disk space is very low, regardless if the PC is actively in use or not. |
| AccountManagement: DiskLevelCaching | If you set DeletionPolicy to Delete at disk space threshold, set the percent of total disk space to be used as the disk space threshold for account caching. |
| AccountManagement: DiskLevelDeletion | If you set DeletionPolicy to Delete at disk space threshold, set the percent of total disk space to be used as the disk space threshold for account deletion. |
| AccountManagement: InactiveThreshold | If you set DeletionPolicy to Delete at disk space threshold and inactive threshold, set the number of days after which an account that has not signed in will be deleted. |
| AccountManagement: EnableAccountManager | Set as True to enable automatic account management. If this is not set to true, no automatic account management will be done. |
| AccountManagement: KioskModeAUMID | Set an Application User Model ID (AUMID) to enable the kiosk account on the sign-in screen. A new account will be created and will use assigned access to only run the app specified by the AUMID. Note that the app must be installed on the PC. Set the name of the account using KioskModeUserTileDisplayText, or a default name will be used. Find the Application User Model ID of an installed app |
| AccountManagement: KioskModeUserTileDisplayText | Sets the display text on the kiosk account if KioskModeAUMID has been set. |
| Customization: MaintenanceStartTime | By default, the maintenance start time (which is when automatic maintenance tasks run, such as Windows Update) is midnight. You can adjust the start time in this setting by entering a new start time in minutes from midnight. For example, if you want maintenance to begin at 2 AM, enter 120 as the value. |
| Customization: MaxPageFileSizeMB | Adjusts the maximum page file size in MB. This can be used to fine-tune page file behavior, especially on low end PCs. |
| Customization: RestrictLocalStorage | Set as True to restrict the user from saving or viewing local storage when using File Explorer. This setting controls this API: ShouldAvoidLocalStorage |
| Customization: SetEduPolicies | Set to True for PCs that will be used in a school. For more information, see Windows 10 configuration recommendations for education customers. This setting controls this API: IsEducationEnvironment |
| Customization: SetPowerPolicies | When set as True: — Prevents users from changing power settings — Turns off hibernate — Overrides all power state transitions to sleep (e.g. lid close) |
| Customization: SignInOnResume | This setting specifies if the user is required to sign in with a password when the PC wakes from sleep. |
| Customization: SleepTimeout | Specifies all timeouts for when the PC should sleep. Enter the amount of idle time in seconds. If you don’t set sleep timeout, the default of 1 hour applies. |
| Policies: Authentication (optional related setting) | Enables a quick first sign-in experience for a user by automatically connecting new non-admin Azure AD accounts to the pre-configured candidate local accounts. |
Configuring Shared PC mode for Windows
You can configure Windows to be in shared PC mode in a couple different ways:
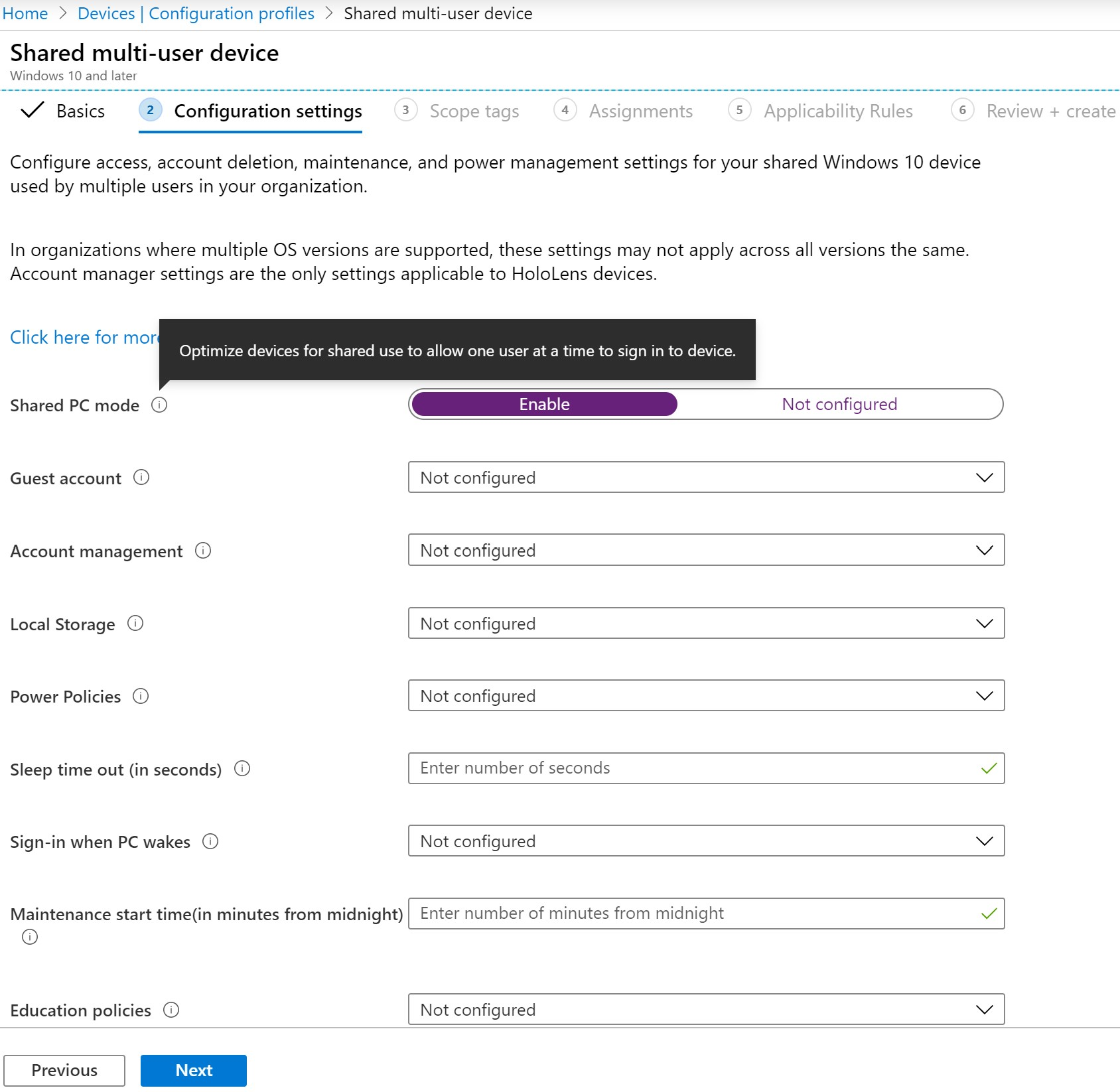
Mobile device management (MDM): Shared PC mode is enabled by the SharedPC configuration service provider (CSP). To setup a shared device policy for Windows 10 in Intune, complete the following steps:
Select Devices > Windows > Configuration profiles > Create profile.
Enter the following properties:
- Platform: Select Windows 10 and later.
- Profile: Select Templates >Shared multi-user device.
Select Create.
In Basics, enter the following properties:
- Name: Enter a descriptive name for the new profile.
- Description: Enter a description for the profile. This setting is optional, but recommended.
Select Next.
In Configuration settings, depending on the platform you chose, the settings you can configure are different. Choose your platform for detailed settings:
On the Configuration settings page, set the вЂShared PC Mode’ value to Enabled.
From this point on, you can configure any additional settings you’d like to be part of this policy, and then follow the rest of the set-up flow to its completion by selecting Create after Step 6.
A provisioning package created with the Windows Configuration Designer: You can apply a provisioning package when you initially set up the PC (also known as the out-of-box-experience or OOBE), or you can apply the provisioning package to a Windows 10 PC that is already in use. The provisioning package is created in Windows Configuration Designer. Shared PC mode is enabled by the SharedPC configuration service provider (CSP), exposed in Windows Configuration Designer as SharedPC.
WMI bridge: Environments that use Group Policy can use the MDM Bridge WMI Provider to configure the MDM_SharedPC class. For all device settings, the WMI Bridge client must be executed under local system user; for more information, see Using PowerShell scripting with the WMI Bridge Provider. For example, open PowerShell as an administrator and enter the following:
Create a provisioning package for shared use
Open Windows Configuration Designer.
On the Start page, select Advanced provisioning.
Enter a name and (optionally) a description for the project, and click Next.
Select All Windows desktop editions, and click Next.
Click Finish. Your project opens in Windows Configuration Designer.
Go to Runtime settings > SharedPC. Select the desired settings for shared PC mode.
On the File menu, select Save.
On the Export menu, select Provisioning package.
Change Owner to IT Admin, which will set the precedence of this provisioning package higher than provisioning packages applied to this device from other sources, and then select Next.
Set a value for Package Version.
You can make changes to existing packages and change the version number to update previously applied packages.
(Optional) In the Provisioning package security window, you can choose to encrypt the package and enable package signing.
Enable package encryption — If you select this option, an auto-generated password will be shown on the screen.
Enable package signing — If you select this option, you must select a valid certificate to use for signing the package. You can specify the certificate by clicking Select. and choosing the certificate you want to use to sign the package.
We recommend that you include a trusted provisioning certificate in your provisioning package. When the package is applied to a device, the certificate is added to the system store and any package signed with that certificate thereafter can be applied silently.
Click Next to specify the output location where you want the provisioning package to go once it’s built. By default, Windows Configuration Designer uses the project folder as the output location. Optionally, you can click Browse to change the default output location.
Click Next.
Click Build to start building the package. The project information is displayed in the build page and the progress bar indicates the build status. If you need to cancel the build, click Cancel. This cancels the current build process, closes the wizard, and takes you back to the Customizations Page.
If your build fails, an error message will show up that includes a link to the project folder. You can scan the logs to determine what caused the error. Once you fix the issue, try building the package again. If your build is successful, the name of the provisioning package, output directory, and project directory will be shown.
- If you choose, you can build the provisioning package again and pick a different path for the output package. To do this, click Back to change the output package name and path, and then click Next to start another build.
- If you are done, click Finish to close the wizard and go back to the Customizations Page.
Select the output location link to go to the location of the package. You can provide that .ppkg to others through any of the following methods:
Shared network folder
Removable media (USB/SD) (select this option to apply to a PC during initial setup)
Apply the provisioning package
You can apply the provisioning package to a PC during initial setup or to a PC that has already been set up.
During initial setup
Start with a PC on the setup screen.
Insert the USB drive. If nothing happens when you insert the USB drive, press the Windows key five times.
If there is only one provisioning package on the USB drive, the provisioning package is applied.
If there is more than one provisioning package on the USB drive, the Set up device? message displays. Click Set up, and select the provisioning package that you want to install.
Complete the setup process.
After setup
On a desktop computer, navigate to Settings > Accounts > Work access > Add or remove a management package > Add a package, and selects the package to install.
If you apply the setup file to a computer that has already been set up, existing accounts and data might be lost.
Guidance for accounts on shared PCs
We recommend no local admin accounts on the PC to improve the reliability and security of the PC.
When a PC is set up in shared PC mode with the default deletion policy, accounts will be cached automatically until disk space is low. Then, accounts will be deleted to reclaim disk space. This account management happens automatically. Both Azure AD and Active Directory domain accounts are managed in this way. Any accounts created through Guest and Kiosk will be deleted automatically at sign out.
On a Windows PC joined to Azure Active Directory:
- By default, the account that joined the PC to Azure AD will have an admin account on that PC. Global administrators for the Azure AD domain will also have admin accounts on the PC.
- With Azure AD Premium, you can specify which accounts have admin accounts on a PC using the Additional administrators on Azure AD Joined devices setting on the Azure portal.
Local accounts that already exist on a PC won’t be deleted when turning on shared PC mode. New local accounts that are created using Settings > Accounts > Other people > Add someone else to this PC after shared PC mode is turned on won’t be deleted. However, any new local accounts created by the Guest and Kiosk options on the sign-in screen (if enabled) will automatically be deleted at sign-out.
If admin accounts are necessary on the PC
- Ensure the PC is joined to a domain that enables accounts to be signed on as admin, or
- Create admin accounts before setting up shared PC mode, or
- Create exempt accounts before signing out when turning shared pc mode on.
The account management service supports accounts that are exempt from deletion.
An account can be marked exempt from deletion by adding the account SID to the registry key: HKEY_LOCAL_MACHINE\SOFTARE\Microsoft\Windows\CurrentVersion\SharedPC\Exemptions\ .
To add the account SID to the registry key using PowerShell:
Policies set by shared PC mode
Shared PC mode sets local group policies to configure the device. Some of these are configurable using the shared pc mode options.
It is not recommended to set additional policies on PCs configured for Shared PC Mode. The shared PC mode has been optimized to be fast and reliable over time with minimal to no manual maintenance required.
Admin Templates > Control Panel > Personalization
Prevent enabling lock screen slide show
Prevent changing lock screen and logon image
Admin Templates > System > Power Management > Button Settings
Select the Power button action (plugged in)
Select the Power button action (on battery)
Select the Sleep button action (plugged in)
Select the lid switch action (plugged in)
Select the lid switch action (on battery)
Admin Templates > System > Power Management > Sleep Settings
Require a password when a computer wakes (plugged in)
Require a password when a computer wakes (on battery)
Specify the system sleep timeout (plugged in)
Specify the system sleep timeout (on battery)
Turn off hybrid sleep (plugged in)
Turn off hybrid sleep (on battery)
Specify the unattended sleep timeout (plugged in)
Specify the unattended sleep timeout (on battery)
Allow standby states (S1-S3) when sleeping (plugged in)
Allow standby states (S1-S3) when sleeping (on battery)
Specify the system hibernate timeout (plugged in)
Specify the system hibernate timeout (on battery)
Admin Templates>System>Power Management>Video and Display Settings
Turn off the display (plugged in)
Turn off the display (on battery
Admin Templates>System>Power Management>Energy Saver Settings
Admin Templates>System>Logon
Show first sign-in animation
Hide entry points for Fast User Switching
Turn on convenience PIN sign-in
Turn off picture password sign-in
Turn off app notification on the lock screen
Allow users to select when a password is required when resuming from connected standby
Block user from showing account details on sign-in
Admin Templates>System>User Profiles
Turn off the advertising ID
Admin Templates>Windows Components
Do not show Windows Tips
Turn off Microsoft consumer experiences
Microsoft Passport for Work
Prevent the usage of OneDrive for file storage
Admin Templates>Windows Components>Biometrics
Allow the use of biometrics
Allow users to log on using biometrics
Allow domain users to log on using biometrics
Admin Templates>Windows Components>Data Collection and Preview Builds
Toggle user control over Insider builds
Disable pre-release features or settings
Do not show feedback notifications
Admin Templates>Windows Components>File Explorer
Show lock in the user tile menu
Admin Templates>Windows Components>Maintenance Scheduler
Automatic Maintenance Activation Boundary
Automatic Maintenance Random Delay
Enabled, 2 hours
Automatic Maintenance WakeUp Policy
Admin Templates>Windows Components>Windows Hello for Business
Use phone sign-in
Use Windows Hello for Business
Admin Templates>Windows Components>OneDrive
Prevent the usage of OneDrive for file storage
Windows Settings>Security Settings>Local Policies>Security Options
Interactive logon: Do not display last user name
Enabled, Disabled when account model is only guest
Interactive logon: Sign-in last interactive user automatically after a system-initiated restart
Shutdown: Allow system to be shut down without having to log on
User Account Control: Behavior of the elevation prompt for standard users