- Hardening Windows 10 with zero-day exploit mitigations
- CVE-2016-7255 exploit: Win32k elevation of privilege
- Abusing the tagWND.strName kernel structure
- Mitigating tagWND exploits with stronger validation
- CVE-2016-7256 exploit: Open type font elevation of privilege
- Function table corruption for initial code execution
- Shellcode and privilege escalation
- Mitigating font exploits with AppContainer
- Conclusion: Fighting the good fight with exploit mitigation and layered detection
- Windows 10 Hardening: 10+ Step Checklist
- Windows 10 Hardening: What should you do?
- Operating System: Regular Updates
- Motherboard: Secure Boot
- How to confirm if I am running Secure Boot?
- System Protection: Create a Restore Point
- Account Settings: Prefer Non-Admin User
- Encrypt Drives with BitLocker
- Review Windows 10 Privacy Settings
- Cleanup: Uninstall Unnecessary Software
- Scan Non-Microsoft Products for vulnerability
- Windows 10 Hardening: Never disable User Account Control
- Strong Passwords: Tough to Guess
- Active Protection: Use Antivirus
- Update Windows Device Drivers
- Frequently Asked Questions(FAQ)
- Do I still need an Anti-Malware?
- How do I protect myself from risky Websites?
- Does Windows 10 Hardening protect my Online Privacy?
- Conclusion
- 3 thoughts on “Windows 10 Hardening: 10+ Step Checklist”
Hardening Windows 10 with zero-day exploit mitigations
Cyberattacks involving zero-day exploits happen from time to time, affecting different platforms and applications. Over the years, Microsoft security teams have been working extremely hard to address these attacks. While delivering innovative solutions like Windows Defender Application Guard, which provides a safe virtualized layer for the Microsoft Edge browser, and Windows Defender Advanced Threat Protection, a cloud-based service that identifies breaches using data from built-in Windows 10 sensors, we are hardening the Windows platform with mitigation techniques that can stop exploits of newly discovered and even undisclosed vulnerabilities. As Terry Myerson reiterated in his blog post, we take our commitment to security innovation very seriously.
A key takeaway from the detonation of zero-day exploits is that each instance represents a valuable opportunity to assess how resilient a platform can be—how mitigation techniques and additional defensive layers can keep cyberattacks at bay while vulnerabilities are being fixed and patches are being deployed. Because it takes time to hunt for vulnerabilities and it is virtually impossible to find all of them, such security enhancements can be critical in preventing attacks based on zero-day exploits.
In this blog, we look at two recent kernel-level zero-day exploits used by multiple activity groups. These kernel-level exploits, based on CVE-2016-7255 and CVE-2016-7256 vulnerabilities, both result in elevation of privileges. Microsoft has promptly fixed the mentioned vulnerabilities in November 2016. However, we are testing the exploits against mitigation techniques delivered in August 2016 with Windows 10 Anniversary Update, hoping to see how these techniques might fare against future zero-day exploits with similar characteristics.
| CVE | Microsoft Update | Exploit Type | Mitigation in Anniversary Update |
| CVE-2016-7255 | MS16-135 (Nov, 2016) | Win32k Elevation of Privilege Exploit | Strong validation of tagWND structure |
| CVE-2016-7256 | MS16-132 (Nov, 2016) | Open Type Font Exploit | Isolated Font Parsing (AppContainer) Stronger validation in font parsing |
CVE-2016-7255 exploit: Win32k elevation of privilege
In October 2016, the STRONTIUM attack group launched a spear-phishing campaign targeting a small number of think tanks and nongovernmental organizations in the United States. The campaign, also discussed in the previously mentioned blog post, involved the use of the exploit for CVE-2016-7255 in tandem with an exploit for the Adobe Flash Player vulnerability CVE-2016-7855.
The attack group used the Flash exploit to take advantage of a use-after-free vulnerability and access targeted computers. They then leveraged the type-confusion vulnerability in win32k.sys (CVE-2016-7255) to gain elevated privileges.
Abusing the tagWND.strName kernel structure
In this section, we’ll go through the internals of the specific exploit for CVE-2016-7255 crafted by the attacker. We will show how mitigation techniques provided customers with preemptive protection from the exploit, even before the release of the specific update fixing the vulnerability.
Figure 1. Exploit and shellcode phases of this attack
Modern exploits often rely on read-write (RW) primitives to achieve code execution or gain additional privileges. For this exploit, attackers acquire RW primitives by corrupting tagWND.strName kernel structure. This exploit method is a trend discussed in security conferences and visible to those who investigated actual attacks. For example, we detailed similar findings in a presentation about the Duqu 2.0 exploit at Virus Bulletin 2015.
By reverse engineering its code, we found that the Win32k exploit used by STRONTIUM in October 2016 reused the exact same method. The exploit, after the initial Win32k vulnerability, corrupts tagWND.strName structure and uses SetWindowTextW to write arbitrary content anywhere in kernel memory.
Figure 2. SetWindowTextW as a write primitive
The exploit abuses this API call to overwrite data of current processes and copy token privileges of the SYSTEM. If successful, the exploit enables the victim process—iexplore.exe, in this example—to execute with elevated privileges.
Figure 3. Internet Explorer with SYSTEM privileges
Mitigating tagWND exploits with stronger validation
To mitigate the Win32k exploit and similar exploits, the Windows Offensive Security Research Team (OSR) introduced techniques in the Windows 10 Anniversary Update that prevent abusive use of tagWND.strName. This mitigation performs additional checks for the base and length fields, making sure that they are in the expected virtual address ranges and are not usable for RW primitives. In our tests on Anniversary Update, exploits using this method to create an RW primitive in the kernel are ineffective. These exploits instead cause exceptions and subsequent blue screen errors.
Figure 4. Windows 10 Anniversary Update mitigation on a common kernel write primitive
With the upcoming Windows 10 Creators Update, Windows Defender ATP introduces numerous forms of generic kernel exploit detection for deeper visibility into targeted attacks leveraging zero-day exploits. Technical details about the enhanced sensor will be shared in a forthcoming blog post.
CVE-2016-7256 exploit: Open type font elevation of privilege
As early as June 2016, unidentified actors began to use an implant detected as “Henkray” in low-volume attacks primarily focused on targets in South Korea. Later, in November 2016, these attackers were detected exploiting a flaw in the Windows font library (CVE-2016-7256) to elevate privileges and install the Henkray backdoor on targeted computers with older versions of Windows.
The font samples found on affected computers were specifically manipulated with hardcoded addresses and data to reflect actual kernel memory layouts. This indicates the likelihood that a secondary tool dynamically generated the exploit code at the time of infiltration.
Figure 5. Auto-generation of font file with exploit
This secondary executable or script tool, which has not been recovered, appears to prepare and drop the font exploit, calculating and preparing the hardcoded offsets needed to exploit the kernel API and the kernel structures on the targeted system. Through deep forensic inspection of the binary data found in samples, we extracted all the hardcoded offsets and ascertained the kernel version targeted by this exploit: Windows 8 64-bit.
Function table corruption for initial code execution
The font exploit uses fa_Callbacks to corrupt the function table and achieve initial code execution. The callback is called from the CFF parsing function. The following snippet shows a corrupted ftell pointer to a nt!qsort+0x39 location in kernel code.
Figure 6. fa_Callbacks table corruption
The following snippet shows the code that calls the corrupt function pointer leading to a kernel ROP chain.
Figure 7. fa_Callbacks.ftell function call code
When the corrupted function is called, the control jumps to the first ROP gadget at nt!qsort+0x39, which adjusts stack pointer and initializes some register values from stack values.
Figure 8. First ROP gadget
After the first gadget, the stack points to a kernel ROP chain which calls to ExAllocatePoolWithTag call to reserve shellcode memory. Another ROP gadget will copy the first 8 bytes of the stage 1 shellcode to the allocated memory.
Figure 9. Copying the stage 1 shellcode
Shellcode and privilege escalation
The stage 1 shellcode is very small. Its main function is to copy the main body of the shellcode to newly allocated memory and run them with a JMP RAX control transfer.
Figure 10. Stage 1 shellcode
The main shellcode runs after the copy instructions. The main shellcode—also a small piece of code—performs a well-known token-stealing technique. It then copies the token pointer from a SYSTEM process to the target process, achieving privilege escalation. Both the SYSTEM process and target process PIDs, as well as certain offsets for the kernel APIs needed by the shellcode, are hardcoded in the font sample.
Figure 11. Token replacement technique
Mitigating font exploits with AppContainer
When opening the malicious font sample on Windows 10 Anniversary Update, font parsing happens completely in AppContainer instead of the kernel. AppContainer provides an isolated sandbox that effectively prevents font exploits (among other types of exploits) from gaining escalated privileges. The isolated sandbox considerably reduces font parsing as an attack surface.
Figure 12. AppContainer protects against untrusted fonts in Windows 10 Anniversary Update
Windows 10 Anniversary Update also includes additional validation for font file parsing. In our tests, the specific exploit code for CVE-2016-7256 simply fails these checks and is unable to reach vulnerable code.
Figure 13. Windows 10 font viewer error
Conclusion: Fighting the good fight with exploit mitigation and layered detection
While fixing a single-point vulnerability helps neutralize a specific bug, Microsoft security teams continue to look into opportunities to introduce more and more mitigation techniques. Such mitigation techniques can break exploit methods, providing a medium-term tactical benefit, or close entire classes of vulnerabilities for long-term strategic impact.
In this article, we looked into recent attack campaigns involving two zero-day kernel exploits. We saw how exploit mitigation techniques in Windows 10 Anniversary Update, which was released months before these zero-day attacks, managed to neutralize not only the specific exploits but also their exploit methods. As a result, these mitigation techniques are significantly reducing attack surfaces that would have been available to future zero-day exploits.
By delivering these mitigation techniques, we are increasing the cost of exploit development, forcing attackers to find ways around new defense layers. Even the simple tactical mitigation against popular RW primitives forces the exploit authors to spend more time and resources in finding new attack routes. By moving font parsing code to an isolated container, we significantly reduce the likelihood that font bugs are used as vectors for privilege escalation.
In addition to the techniques mentioned in this article, Windows 10 Anniversary Update introduced many other mitigation techniques in core Windows components and the Microsoft Edge browser, helping protect customers from entire classes of exploits for very recent and even undisclosed vulnerabilities.
For effective post-breach detection, including cover for the multiple stages of attacks described in this blog post, sign up for Window Defender ATP. The service leverages built-in sensors to raise alerts for exploits and other attack activity, providing corresponding threat intelligence. Customers interested in the Windows Defender ATP post-breach detection solution can find more information here.
To test how Windows Defender ATP can help your organization detect, investigate, and respond to advanced attacks, sign up for a free trial.
Microsoft would like to thank KrCERT for their collaboration in protecting customers and for providing the sample for CVE-2016-7256.
Matt Oh and Elia Florio, Windows Defender ATP Research Team
Jan 18, 2017 – Corrected the spelling of Henkray backdoor.
Windows 10 Hardening: 10+ Step Checklist
It’s 2020, and malware today is socially engineered. Just installing antivirus software on the PC is not sufficient. Hence, you have to take additional steps to ensure the complete Windows 10 hardening. Having security software is only one of the ways, but there are other levels of hardening that you probably don’t know.
So, here is a complete Windows 10 hardening checklist to protect your PC.
Windows 10 Hardening: What should you do?
Are you still using Windows XP or Windows 7? In that case, it will be a good idea to upgrade to Windows 10. I understand that it may appear to be a bit difficult to operate at the beginning. However, once you get used to the interface, it will be a part of your life as any other operating system. So moving forward, this guide will focus on Windows 10.
Operating System: Regular Updates
Microsoft has officially stopped support for Windows XP on April 8th, 2014. Also, Windows 7 met with the same fate on January 14th, 2020. Hence, you will not receive any updates from Microsoft on these two operating systems. Due to the lack of regular updates and security patches, these operating systems are at higher risk with the view of recent attacks.
Considering the security point of view, Windows 10 should be your choice.
Motherboard: Secure Boot
Bootkit type of malware can infect the master boot record of the system. Also, it executes automatically when the computer starts up. As it runs outside the file system, an operating system level protection isn’t enough. Hence, if you are assembling a PC, g o for a Motherboard that supports Secure Boot and set the boot menu to UEFI only. All modern laptops already have motherboards with Secure boot support.
Here is a list of Intel Motherboards which support SecureBoot. For other brands, check the description or their release notes.
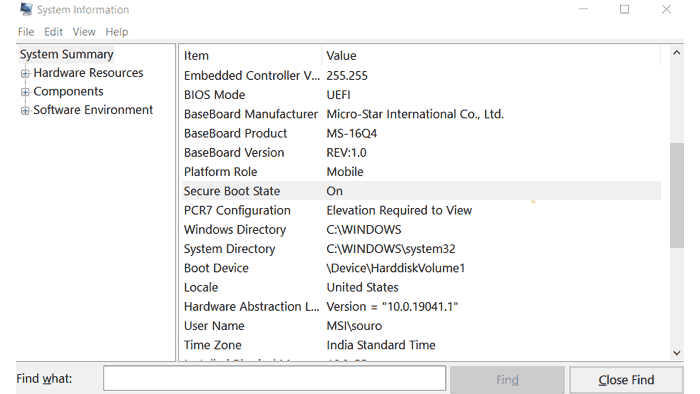
How to confirm if I am running Secure Boot?
You can quickly check if Secure Boot is enabled or not.
- Open the «Run console,» press Windows key + R
- On the Run Console type msinfo32 and hit enter
- Under System Summary search for Secure Boot State.
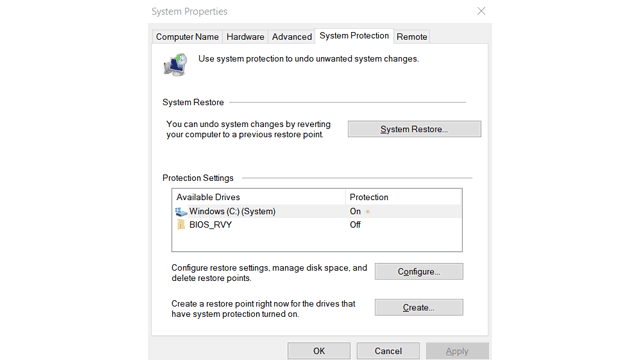
System Protection: Create a Restore Point
It’s always a good practice to have a restore point. When system protection is on, Windows automatically keeps and updates a restore point to which you can revert if you face any issues.
You can also create a manual restore point. Doing so gives you control over the state of Windows where you want to return. I usually create a restore point manually after a fresh installation with a basic set of applications. However, you can also do so as per your choice. A restore point is not helping you directly in Windows 10 hardening, but it provides a flag point where you can always return.
Account Settings: Prefer Non-Admin User
By default, we get the access and privileges of administrators on the first account creation of Windows. You should create another user with standard privileges and use it for daily work. It lowers the risk of infection as a standard user account doesn’t have all access to the system. For escalated privileges (if necessary), you can use the Admin account.
Encrypt Drives with BitLocker
Drive encryption protects your data from unauthorized access. Since Windows 10 includes BitLocker by default, you do not have to spend anything. Also, you can use it to encrypt local and removable storage devices. Learn more about BitLocker and implement the same.
Review Windows 10 Privacy Settings
In this section, you can tweak how Windows 10 collects your data or apps accesses system resources. In Privacy settings, visit all the sections and disable the options accordingly. I recommend you to disable all the data settings you do not want Microsoft to use. In case you wish to be a part of the Windows Insider Program, you need to enable Full Diagnostics & Feedback.
App permissions are very useful in case you only want to allow certain apps to use your File system. Hence, it will protect you from ransomware attacks. To ensure Windows 10 hardening, you should review and limit the apps that can access your Camera and Microphone. There are many more settings that you can tweak in this section.
Note: If you have an antivirus with ransomware protection, you will not have access to change File System as your antivirus actively manages it.
Cleanup: Uninstall Unnecessary Software
The less you have, is better. Avoid the risk by uninstalling software products you don’t use. Intruders exploit many popular programs to gain access to your system and infect it. Some prominently exploited software programs are Adobe Flash and Java, so get rid of them unless extremely necessary.
CCleaner , Revo Uninstaller , and Uninstaller Pro are reliable solutions to uninstall unnecessary applications and clean up garbage. Also, apps like CCleaner can optimize PC Speed automatically. It is an essential step in Windows 10 Hardening. Hence, do not miss it.
Scan Non-Microsoft Products for vulnerability
In Windows 10, Microsoft automatically updates the apps that you get from Microsoft Store. Also, you need to update 3rd party software regularly. While updating the software, you also reduce the chances of existing software vulnerabilities. In case you have a lot of applications on your system and find it difficult to update them manually, check the IObit Software Updater . It helps you by automatically updating any software to the latest version.
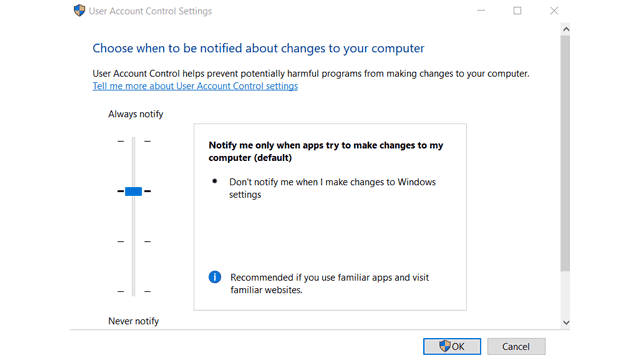
Windows 10 Hardening: Never disable User Account Control
Yes, UAC prompts are annoying, but by disabling it, you lose more than just a pop-up. Disabling UAC also disables file-system & Registry virtualization and Protected Mode. When an application wants to make a system change like modifications that affect other users, modifications of system files and folders, and installation of new software, a UAC prompt shows up, asking for permission.
User Account Control makes sure that these changes are made only with approval from the administrator. Read more about UAC .
Strong Passwords: Tough to Guess
It is a grave mistake, but it isn’t your fault. Hard-to-guess passwords are difficult to remember. Why not use a sophisticated tool to manage and remember all your passwords in a safe Vault? I have been using LastPass for a long time for this purpose. It generates secure passwords as well as stores them in encrypted form. You can get passwords on demand and auto-fill whenever required.
Active Protection: Use Antivirus
It is indeed necessary even after following everything stated above. No matter how many manual actions you take, there should be a program that continuously monitors every activity. It is possible only if you have an Antivirus program. Windows 10 includes Windows Defender, and it can protect you from primary threats. Also, the latest additions include ransomware protection by default. However, you should solely depend on it only if you are fully aware of your internet browsing habits.
I recommend more than just a plain antivirus like an Internet Security program that has an inbuilt firewall and spam protection. Bitdefender Total Security is a perfect choice with advanced antivirus protection, two-way Firewall protection, and Cloud-Antispam.
Update Windows Device Drivers
Updating device drivers is essential. Not only it keeps your devices at optimal performance level but also prevents any exploits that may exist in older versions. Windows 10 automatically updates the device drivers for you. However, if you feel that you are not receiving proper driver updates, you can check a 3rd party driver updater like Driver Booster Pro.
Frequently Asked Questions(FAQ)
Do I still need an Anti-Malware?
If you have followed everything till now, you probably won’t need one. Also, if you are using a primary antivirus, it is not recommended to use another real-time protection. However, if you want to have an additional layer of security, you can use an anti-malware with real-time protection off. Hence, you have to perform another scan manually. The good idea is to perform a full system scan weekly manually. If you wish, you can give a try to Zemana or Malwarebytes.
How do I protect myself from risky Websites?
If you use Bitdefender Total Security , it comes with a real-time URL checker which notifies you about malicious website. You can avoid visiting them or go ahead by adding them as an exception. In any case, you will not accidentally land on malicious websites. Apps like Advanced SystemCare Pro also implements features like Host file and browser Homepage protection.
Does Windows 10 Hardening protect my Online Privacy?
Unfortunately, the answer is NO. The tweaks in this guide only allow you to protect the Windows 10 environment. However, if your concern is with online privacy, then you should use a VPN. With the increase of ISP monitoring, a VPN is a must-use service. A misconception among many people is that a VPN is only needed to access geo-restricted content. Well, it is not precisely correct.
Apart from letting you access streaming content and services, a VPN also encrypts all your connections using various Tunneling protocols. Also, many new VPN services like Surfshark provide advanced features like ads, Malware, and tracker blocker. Hence, you should use a VPN regularly and especially when you are using public Wi-Fi.
Conclusion
So this concludes the Windows 10 Hardening checklist. This article includes all the tricks that will make your Windows 10 safer. However, always remember that you have to be careful with every Windows update and check for the changes in the new version. If there is any change in the privacy sections, you will have to change the particulars accordingly.
Comment below and let me know if you have any more questions.
The three attributes that define me- Tech lover, Blogger, and Dog lover. I primarily cover Cyber Security, online privacy, and also have keen interest in exploring new software that make daily computing easier for home users. I do love to spend quality time away from the internet, so when I am not online, I either cook or bike.
3 thoughts on “Windows 10 Hardening: 10+ Step Checklist”
Excellent checklist to make sure the windows is secure from viruses and malwares. Between i prefer windows 7 to do better tweaks and take control of the security area of the PC. Windows 8 has all the features but they are not easily accessible and less ways to tweak them.
Good article you have here to protect our data from internet attacks (Y). Cheers.
Hi Rohit,
Many believe that after installing antivirus, the computer is totally secured, Hell No! there are still some security measure to apply to secure the computer, installing antivirus is just among the list
if u have some virus/mailware, and doesnt noticed this, what problem u have at this time really ?
i have no UAC
i haver bitdefender total sec,
i have the UP- DOWN load rate show at task. to see it nonstop, because i can down with 200Mbit and up with 12mbit…
soooo, if i have any virus/mailware onboard, and ingame my ping doesnt goes over 20, dont notice some CPU RAM or NET load, there i dont have make at myselfe, wtf does some “viruses/mailware” ? i doesnt scarred, and all people get spend monney 4 this scarry thing who are at the end doesnt make u pain, u dont noticed u only scarred 4 this ? if i get paranoid, i can shut down the pc, and choose some backup thats me doesnt let get paranoid freaky.
sometimes i think, all people are think ” OMMMMGGG have MAILWARE, one day longer, and the police comes, brake my dore and fuc*s me in the ass 24/7 365 ,….