- Access Control Entries
- How to Fix ‘Access Control Entry is Corrupt’ Error on Windows?
- What is causing the ‘Access Control Entry is Corrupt’ error?
- Method 1: Closing all Windows UWP apps
- Method 2: Changing the owner to Users
- Method 3: Perform DISM and SFC scans
- Access Control Lists
- Access Control Overview
- Feature description
Access Control Entries
An access control entry (ACE) is an element in an access control list (ACL). An ACL can have zero or more ACEs. Each ACE controls or monitors access to an object by a specified trustee. For information about adding, removing, or changing the ACEs in an object’s ACLs, see Modifying the ACLs of an Object in C++.
There are six types of ACEs, three of which are supported by all securable objects. The other three types are Object-specific ACEs supported by directory service objects.
All types of ACEs contain the following access control information:
- A security identifier (SID) that identifies the trustee to which the ACE applies.
- An access mask that specifies the access rights controlled by the ACE.
- A flag that indicates the type of ACE.
- A set of bit flags that determine whether child containers or objects can inherit the ACE from the primary object to which the ACL is attached.
The following table lists the three ACE types supported by all securable objects.
| Type | Description |
|---|---|
| Access-denied ACE | Used in a discretionary access control list (DACL) to deny access rights to a trustee. |
| Access-allowed ACE | Used in a DACL to allow access rights to a trustee. |
| System-audit ACE | Used in a system access control list (SACL) to generate an audit record when the trustee attempts to exercise the specified access rights. |
For a table of object-specific ACEs, see Object-specific ACEs.
System-alarm object ACEs are not currently supported.
How to Fix ‘Access Control Entry is Corrupt’ Error on Windows?
Several Windows users have been reaching us with questions after being unable to change the ‘owner’ in the Advanced Security Settings. Upon clicking Ok to save the changes, affected users are reporting that they see the ‘Access Control Entry is Corrupt‘ error popping up in a yellow box and the change never gets saved. The issue doesn’t seem to be exclusive to a certain Windows version as it’s confirmed to occur on Windows 7, Windows 8.1 and Windows 10.
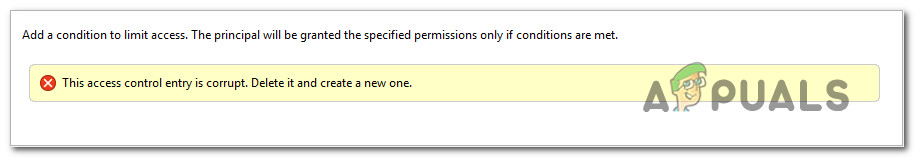
What is causing the ‘Access Control Entry is Corrupt’ error?
We analyzed this issue by looking into various user reports and trying out different fixes that are recommended by other users after they we’re able to fix this problem. Based on our investigations, several different culprits might be responsible for this issue. Here’s a shortlist with potential scenarios that might lead to this issue:
- UWP application is interfering with permission editing – Universal Windows Platform applications are known to cause errors in instances where the user tries to edit the permissions of a Windows App folder. In this case, you can resolve the error message by closing the UWP apps that are interfering with this process.
- Folder or file has a generic owner – As it turns out, this issue can also occur in instances where the file or folder in question doesn’t have an owner. If this scenario is applicable, you will be able to resolve the issue by changing the owner to the Users group.
- System File corruption – In some rare cases, this problem can occur due to one or more system files that have become corrupted and are preventing the change from getting enforced. In this case, eliminating the logical errors and corruption issues with utilities such as DISM and SFC should allow you to fix the issue entirely.
If you’re currently looking fox fixes capable of resolving this error message, this article will provide you with several different troubleshooting steps. Down below, you’ll find a collection of repair strategies that other users in a similar scenario have used to get the problem resolved.
If you want to do things as efficiently as possible, we advise you to follow the methods below in the same order that we arranged them (by efficiency and severity). Eventually, you should stumble upon a fix that will resolve the issue regardless of the culprit that’s causing the problem.
Method 1: Closing all Windows UWP apps
As it turns out, in some cases, the issue might occur due to some UWP (Universal Windows Platform) applications or games that are running in the background and preventing the permissions from being edited.
Even if you aren’t aware of any UWP application that might be running, it’s still worth it to investigate, since Microsoft is notoriously known for automatically partnership games such as ‘Candy Crush Saga’ and the likes. Some of this will include background services that will open at every startup, without ever noticing you.
Here’s a quick guide on identifying and closing any UWP apps that might be preventing you from editing the permissions:
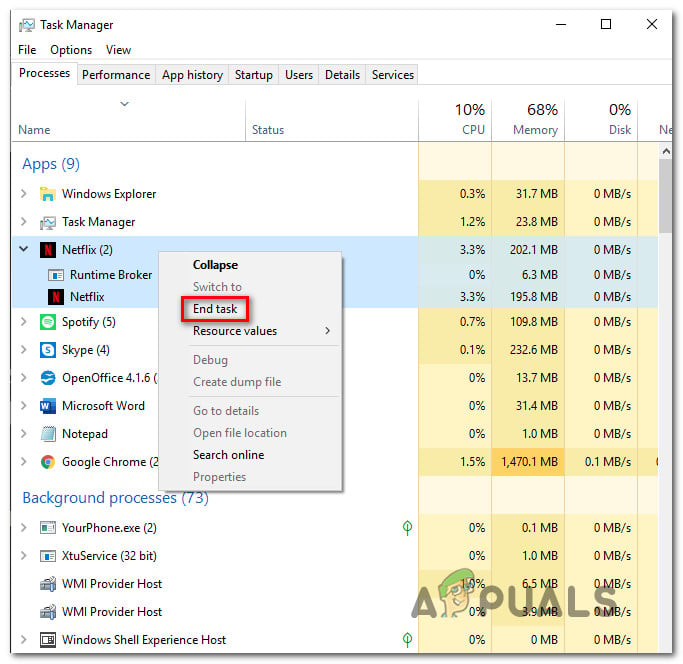
- Press Ctrl + Shift + Esc to open up the Task Manager.
- Inside Task Manager, select the Processes tab, then scroll down through the list of Apps and Background processes and right-click >End Task anything that is not essential to the functioning of your PC.
Ending every unnecessary task
Note: Ignore the Windows Processes category.
If you’re still encountering the ‘Access Control Entry is Corrupt‘ error, move down to the next method below.
Method 2: Changing the owner to Users
Perhaps the most effective fix for this particular issue is to change the Owner of the folder/file and to take full ownership of it. After doing this, you should be able to edit the permissions without encountering the ‘Access Control Entry is Corrupt‘ error.
Several affected users have confirmed that this fixes allowed them to resolve the issue indefinitely and they were able to modify the permissions without any errors after following the steps below:
- Right-click on the folder or file that you’re having issues with and choose Properties from the context menu.
- Once you’re inside the Properties screen, select the Security tab, click on the Advanced button associated with Permissions.
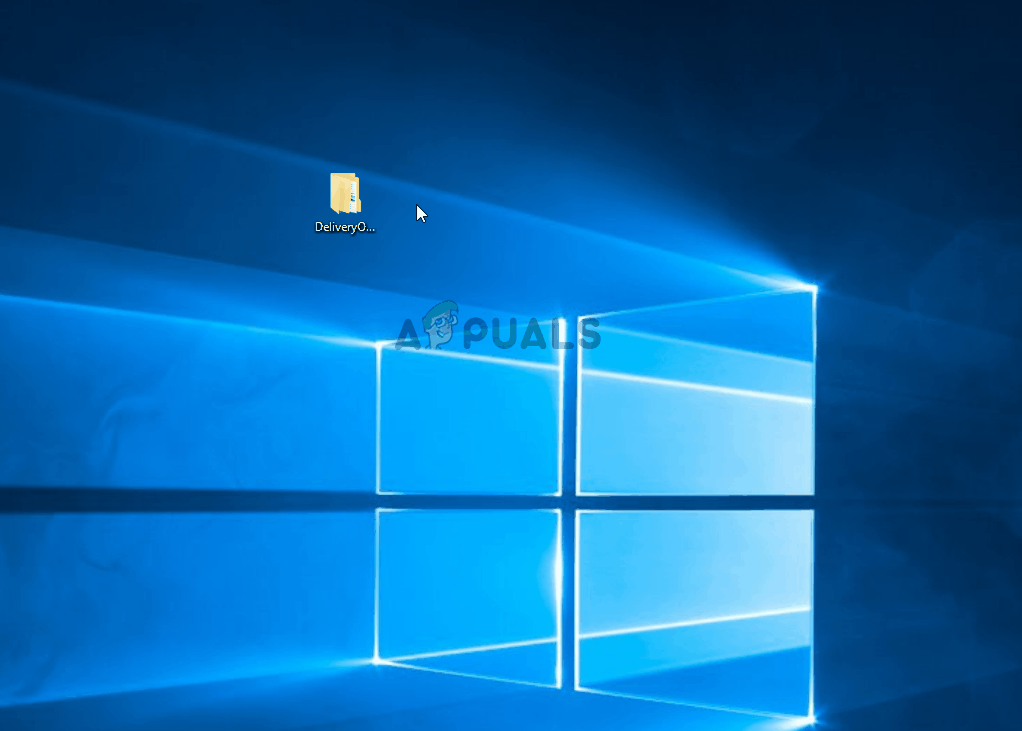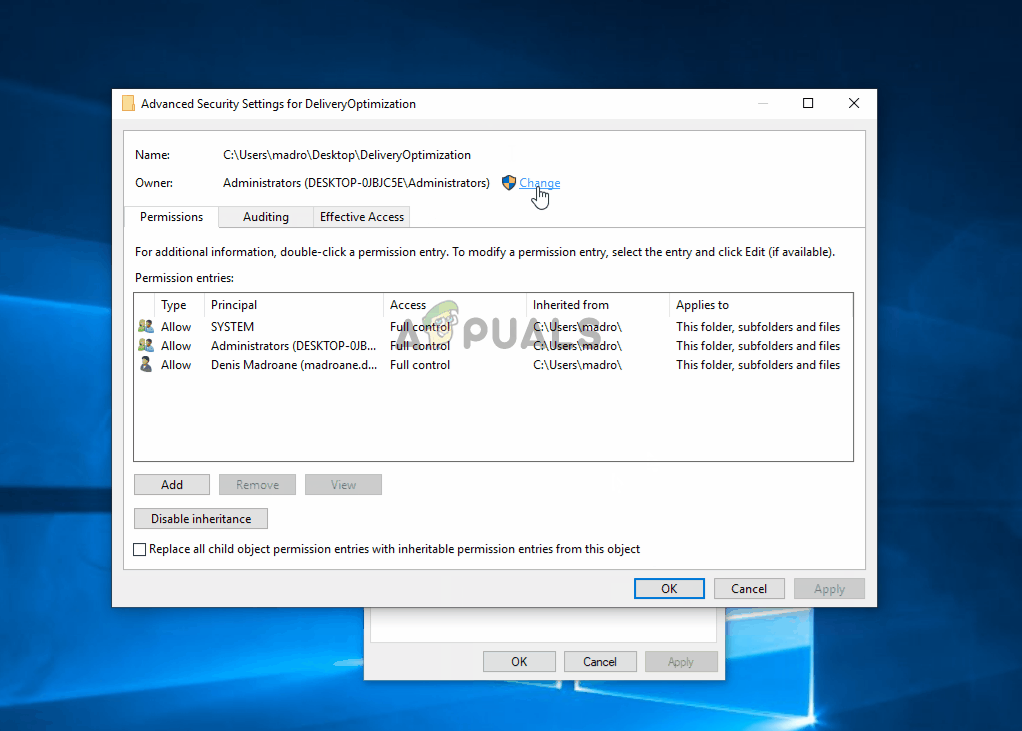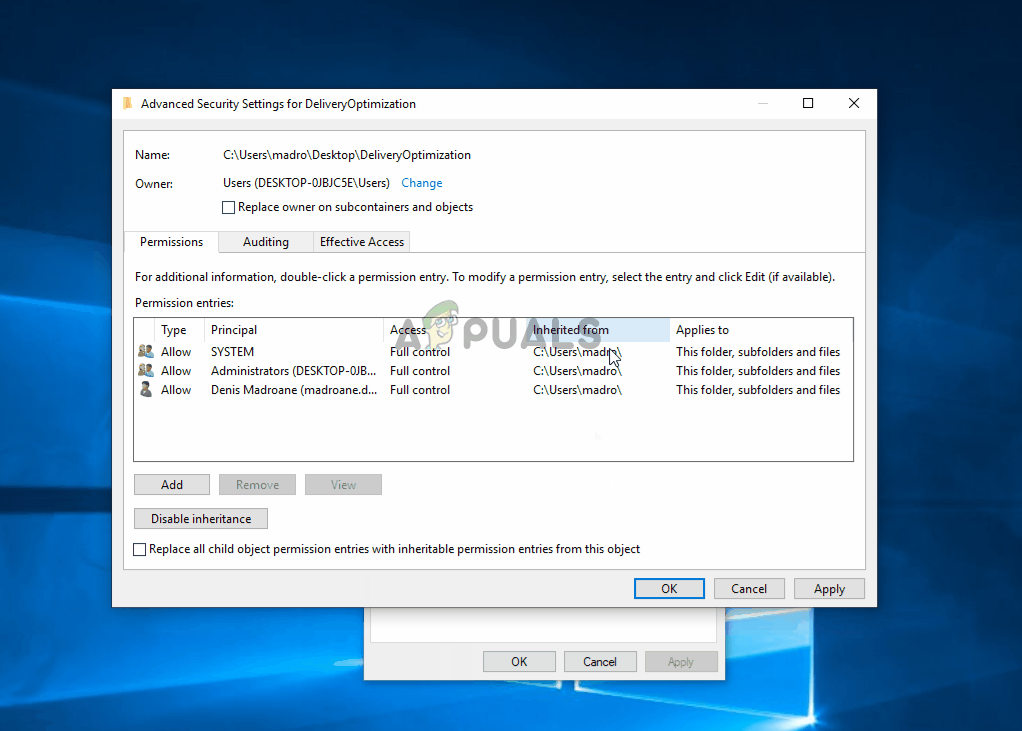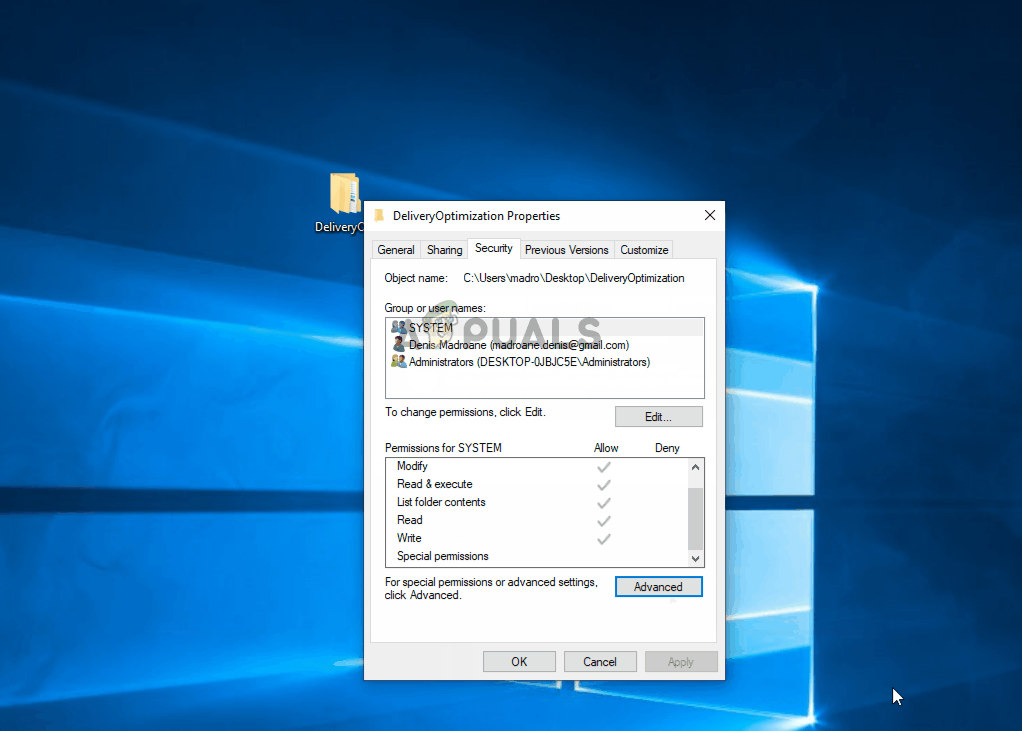
- Inside the Advanced Security Settings, click on the Change button associated with the Owner.
- Inside the Select User or Group, type Users inside the text box, then click on Check Names to verify. If the syntax is replaced correctly, click Ok to save the changes. Then click Apply at the previous window to make the change permanent.
- Try to modify the permissions accordingly and see if you still see the error message.
If you’re still encountering the ‘Access Control Entry is Corrupt‘ error, move down to the final method below.
Method 3: Perform DISM and SFC scans
It’s also possible that the ‘Access Control Entry is Corrupt‘ error is facilitated by a system file corruption issue. As it’s been reported by several different users, you should be able to fix this problem by using a couple of built-in utilities that are equipped to resolve logical errors and system file corruption that might be responsible for the error.
SFC (System File Checker) and DISM (Deployment Image Servicing and Management) are built-in utilities capable of dealing with this particular issue. The only difference is they do things in different ways – DISM relies on WU (Windows Update) to download healthy copies to replace corrupted files while SFC uses a locally stored archive to fetch healthy copies for the same purpose.
Since the two utilities are designed to complement each other, we advise you to run both to fix any logical errors or corruption issues that might trigger the ‘Access Control Entry is Corrupt‘ error. Here’s a quick guide on doing this:
- Open a Run dialog box by pressing Windows key + R. Next, type “cmd” inside the text box and press Ctrl + Shift + Enter to open up an elevated Command Prompt window. When you’re prompted by the User Account Control window, click Yes to grant admin access.
Running Command Prompt as an administrator
- Once you’re inside the elevated Command Prompt, type the following command and hit Enter to initiate an SFC scan:
Note: Keep in mind that once this process is started, stopping it forcibly (by a restart or by closing the CMD window) exposes your machine to the risk of causing even more logical errors. So make sure you leave the machine running without interrupting through the entire scanning process.
Note: Before you initialize the DISM scan, make sure that your Internet connection is stable. It will be needed to download healthy files in case corruption is identified.
Access Control Lists
An access control list (ACL) is a list of access control entries (ACE). Each ACE in an ACL identifies a trustee and specifies the access rights allowed, denied, or audited for that trustee. The security descriptor for a securable object can contain two types of ACLs: a DACL and a SACL.
A discretionary access control list (DACL) identifies the trustees that are allowed or denied access to a securable object. When a process tries to access a securable object, the system checks the ACEs in the object’s DACL to determine whether to grant access to it. If the object does not have a DACL, the system grants full access to everyone. If the object’s DACL has no ACEs, the system denies all attempts to access the object because the DACL does not allow any access rights. The system checks the ACEs in sequence until it finds one or more ACEs that allow all the requested access rights, or until any of the requested access rights are denied. For more information, see How DACLs Control Access to an Object. For information about how to properly create a DACL, see Creating a DACL.
A system access control list (SACL) enables administrators to log attempts to access a secured object. Each ACE specifies the types of access attempts by a specified trustee that cause the system to generate a record in the security event log. An ACE in a SACL can generate audit records when an access attempt fails, when it succeeds, or both. For more information about SACLs, see Audit Generation and SACL Access Right.
Do not try to work directly with the contents of an ACL. To ensure that ACLs are semantically correct, use the appropriate functions to create and manipulate ACLs. For more information, see Getting Information from an ACL and Creating or Modifying an ACL.
ACLs also provide access control to Microsoft Active Directory directory service objects. Active Directory Service Interfaces (ADSI) include routines to create and modify the contents of these ACLs. For more information, see Controlling Access to Active Directory Objects.
Access Control Overview
Applies to
- Windows 10
- Windows Server 2016
This topic for the IT professional describes access control in Windows, which is the process of authorizing users, groups, and computers to access objects on the network or computer. Key concepts that make up access control are permissions, ownership of objects, inheritance of permissions, user rights, and object auditing.
Feature description
Computers that are running a supported version of Windows can control the use of system and network resources through the interrelated mechanisms of authentication and authorization. After a user is authenticated, the Windows operating system uses built-in authorization and access control technologies to implement the second phase of protecting resources: determining if an authenticated user has the correct permissions to access a resource.
Shared resources are available to users and groups other than the resource’s owner, and they need to be protected from unauthorized use. In the access control model, users and groups (also referred to as security principals) are represented by unique security identifiers (SIDs). They are assigned rights and permissions that inform the operating system what each user and group can do. Each resource has an owner who grants permissions to security principals. During the access control check, these permissions are examined to determine which security principals can access the resource and how they can access it.
Security principals perform actions (which include Read, Write, Modify, or Full control) on objects. Objects include files, folders, printers, registry keys, and Active Directory Domain Services (AD DS) objects. Shared resources use access control lists (ACLs) to assign permissions. This enables resource managers to enforce access control in the following ways:
Deny access to unauthorized users and groups
Set well-defined limits on the access that is provided to authorized users and groups
Object owners generally grant permissions to security groups rather than to individual users. Users and computers that are added to existing groups assume the permissions of that group. If an object (such as a folder) can hold other objects (such as subfolders and files), it is called a container. In a hierarchy of objects, the relationship between a container and its content is expressed by referring to the container as the parent. An object in the container is referred to as the child, and the child inherits the access control settings of the parent. Object owners often define permissions for container objects, rather than individual child objects, to ease access control management.
 Ending every unnecessary task
Ending every unnecessary task 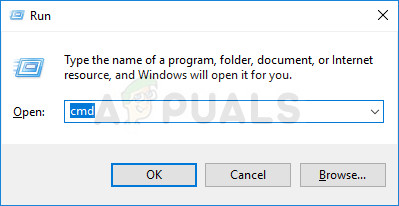 Running Command Prompt as an administrator
Running Command Prompt as an administrator


