- Access Control Editor
- Обзор управления доступом Access Control Overview
- Описание функции Feature description
- Access Control Software
- Basic Access Control Software / Software download
- Additional Options Access Control Software / Software download
- How RFID Access control works
- Why you need this software?
- Feature and Benefit Of Fresh Access Control ?
- Temperature Access Control Face Recognition
- Did You Know That Temperature Access Control Face Recognition Can Help In Finding Body Temperature During The Global Panic Of Any Disease?
- Functions and features of the device access control download here.
- Temperature Access Control Face Recognition – What You Need To Know.
- The magic of Biometrics Access Control
- Different Types of Biometrics Access Control
- Get a simple RFID access control!
- Access RFID
- How To Make Boat Club Access Control By Doing Less
- Access RFID Access Control
- Access RFID
- Access Control Software
- RFID Access Control Software
Access Control Editor
The access control editor is a set of property sheets and property pages that enable the user to view and modify the components of an object’s security descriptor. The editor consists of two main parts:
- A basic security property page that provides a simple interface for editing the access control entries (ACEs) in an object’s discretionary access control list (DACL). This page can include an optional Advanced button that displays the advanced security property sheet.
- An advanced security property sheet with property pages that enable the user to edit the object’s system access control list (SACL), change the object’s owner, or perform advanced editing of the object’s DACL.
The CreateSecurityPage function creates the basic security property page. You can then use the PropertySheet function or the PSM_ADDPAGE message to add this page to a property sheet.
Alternatively, you can use the EditSecurity function to display a property sheet that contains the basic security property page.
For both CreateSecurityPage and EditSecurity, the caller must pass a pointer to an implementation of the ISecurityInformation interface. The access control editor calls the methods of this interface to retrieve access control information about the object being edited and to pass the user’s input back to your application. The ISecurityInformation methods have the following purposes:
To initialize the property pages.
Your implementation of the GetObjectInformation method passes an SI_OBJECT_INFO structure to the editor. This structure specifies the property pages that you want the editor to display and other information that determines the editing options available to the user.
To provide security information about the object being edited.
Your GetSecurity implementation passes the object’s initial security descriptor to the editor. The GetAccessRights and MapGeneric methods provide information about the object’s access rights. The GetInheritTypes method provides information about how the object’s ACEs can be inherited by child objects.
To pass the user’s input back to your application.
When the user clicks Okay or Apply, the editor calls your SetSecurity method to pass back a security descriptor containing the user’s changes.
Обзор управления доступом Access Control Overview
Относится к: Applies to
- Windows 10 Windows 10
- Windows Server 2016 Windows Server 2016
В этом разделе для ИТ-специалистов описывается управление доступом в Windows, которое является процессом авторизации пользователей, групп и компьютеров для доступа к объектам в сети или на компьютере. This topic for the IT professional describes access control in Windows, which is the process of authorizing users, groups, and computers to access objects on the network or computer. Ключевыми понятиями, которые составляют управление доступом, являются разрешения, владение объектами, наследование разрешений, права пользователей и аудит объектов. Key concepts that make up access control are permissions, ownership of objects, inheritance of permissions, user rights, and object auditing.
Описание функции Feature description
Компьютеры с поддерживаемой версией Windows могут управлять использованием системных и сетевых ресурсов с помощью взаимосвязанных механизмов проверки подлинности и авторизации. Computers that are running a supported version of Windows can control the use of system and network resources through the interrelated mechanisms of authentication and authorization. После проверки подлинности пользователя операционная система Windows использует встроенные технологии авторизации и управления доступом для реализации второго этапа защиты ресурсов: определения, имеет ли пользователь с проверкой подлинности правильные разрешения на доступ к ресурсу. After a user is authenticated, the Windows operating system uses built-in authorization and access control technologies to implement the second phase of protecting resources: determining if an authenticated user has the correct permissions to access a resource.
Общие ресурсы доступны пользователям и группам, кроме владельца ресурса, и они должны быть защищены от несанкционированного использования. Shared resources are available to users and groups other than the resource’s owner, and they need to be protected from unauthorized use. В модели управления доступом пользователи и группы (также именуемые директорами безопасности) представлены уникальными идентификаторами безопасности (SID). In the access control model, users and groups (also referred to as security principals) are represented by unique security identifiers (SIDs). Им назначены права и разрешения, которые информируют операционную систему о том, что может сделать каждый пользователь и группа. They are assigned rights and permissions that inform the operating system what each user and group can do. У каждого ресурса есть владелец, который предоставляет разрешения директорам безопасности. Each resource has an owner who grants permissions to security principals. Во время проверки контроля доступа эти разрешения проверяются, чтобы определить, какие принципы безопасности могут получить доступ к ресурсу и каким образом они могут получить к нему доступ. During the access control check, these permissions are examined to determine which security principals can access the resource and how they can access it.
Принципы безопасности выполняют действия (в том числе чтение, записи, изменение или полный контроль) на объектах. Security principals perform actions (which include Read, Write, Modify, or Full control) on objects. Объекты включают файлы, папки, принтеры, ключи реестра и объекты служб домена Active Directory (AD DS). Objects include files, folders, printers, registry keys, and Active Directory Domain Services (AD DS) objects. Общие ресурсы используют списки управления доступом (ACLs) для назначения разрешений. Shared resources use access control lists (ACLs) to assign permissions. Это позволяет руководителям ресурсов применять управление доступом следующими способами: This enables resource managers to enforce access control in the following ways:
Отказ в доступе к несанкционированным пользователям и группам Deny access to unauthorized users and groups
Установите четко определенные ограничения доступа, предоставляемого уполномоченным пользователям и группам Set well-defined limits on the access that is provided to authorized users and groups
Владельцы объектов обычно выдают разрешения группам безопасности, а не отдельным пользователям. Object owners generally grant permissions to security groups rather than to individual users. Пользователи и компьютеры, добавленные в существующие группы, принимают разрешения этой группы. Users and computers that are added to existing groups assume the permissions of that group. Если объект (например, папка) может удерживать другие объекты (например, подмостки и файлы), он называется контейнером. If an object (such as a folder) can hold other objects (such as subfolders and files), it is called a container. В иерархии объектов связь между контейнером и его контентом выражается, ссылаясь на контейнер в качестве родительского. In a hierarchy of objects, the relationship between a container and its content is expressed by referring to the container as the parent. Объект в контейнере называется ребенком, и ребенок наследует параметры управления доступом родителя. An object in the container is referred to as the child, and the child inherits the access control settings of the parent. Владельцы объектов часто определяют разрешения для контейнерных объектов, а не отдельных детских объектов, чтобы облегчить управление управлением доступом. Object owners often define permissions for container objects, rather than individual child objects, to ease access control management.
Этот набор контента содержит: This content set contains:
Access Control Software
This integrated solution access control software is usually used to gain control over the entry point of buildings or places where it is used. This unique software allows the use of different mechanical components such as BOOM barriers, door barriers, and electronic locks among others.
Access Control Software helps restrict access to anyone whose identity couldn’t be verified by biometrics, RFID access card, wristband, keychain or other type of chip. Having a good access control to your company systems includes not only preventing unauthorized access to a high-security environment but also ensuring that both visitors and employees are able to get an access to the needed areas at the right time with very minimal barriers.
Radio-Frequency Identification RFID and access control software involve utilizing small electric gadget to track items. This unique device consists of an antenna and a tiny chip; it can also be used for the same purpose as the magnetic strip on the bar code on the product packaging or the magnetic strip on all credit cards.
With RFID solutions, you will be able to track vehicles, inventories and successfully perform an access control.
Basic Access Control Software / Software download
Additional Options Access Control Software / Software download
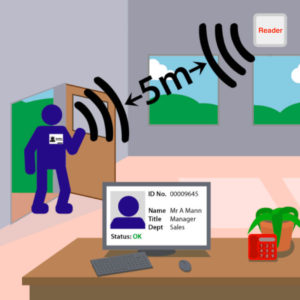
How RFID Access control works
The Radio-Frequency Identification RFID chips are first integrated into devices such as cards, labels, and tags. To retrieve identifying information from the chips, the Radio-Frequency Identification RFID device has to be scanned by a compatible reader. The received information is transmitted to the access control software. For instance, a moving car that is equipped with Radio-Frequency Identification RFID tag will easily activate the parking gate arms when the car is close to the area, making the arms quickly rise so that the car can enter the lot.
Why you need this software?
Businesses may assume that having a security guard in place would suffice. It could be so, however the security can only be effective when they see people who enter the building. This requires full guards’ attention and a number of guards that drive your labor costs up. Yet, unlike this RFID access control software, guards may allow mistakes. The RFID access control software will better help business streamline their work, and make their work more organized and efficient. This reliable automation will also allow the guards focus on other important aspects ensuring that the building remains secure. This system is not only good for securing buildings, but can also be utilized for many other purposes, for example, for tracking of object motions inside the controlled area working as Local Positioning System.
Feature and Benefit Of Fresh Access Control ?
This amazing RFID access control software provides full real-time visibility of all visitors and employees at the facility.
The locks can be enable and disabled automatically depending on access privileges.
Our software enables automatic exit and entry tracking.
Access control software provides reports and cloud-based dashboards based on locations, groups, times and other parameters. With the help of this software, you get automatic alerts on unauthorized access or attempt to access.
Another significant benefit of this software is the reduction in human error and labor. You will also get increased security and efficiency. It could be utilized to find or locate people in the case of an emergency. Also, multiple tenant control is guaranteed.
It could be used for attendance and time tracking.
Why choose fresh access control software and RFID system?
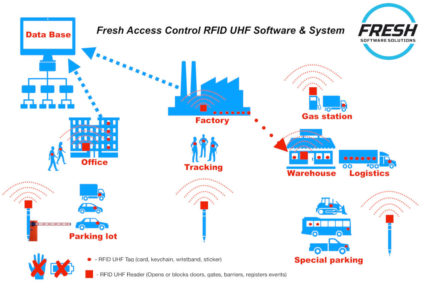
This unique Access Control System by Fresh Software Solution is suitable for various types of RFID access control applications. RFID can effectively handle the control access and personnel to an entire building; it also provides 24hours unmanned operation. This system can be adequately managed remotely with a web interface. The tag and tag holder could be edited, removed and added by the staff in charge without the needing to have them move to the site. The system is also compatible with Fresh Software solution and works as passive RFID tag, RFID hardware, UHF longe range distance. Also, this system also offers group management and customizable reporting.
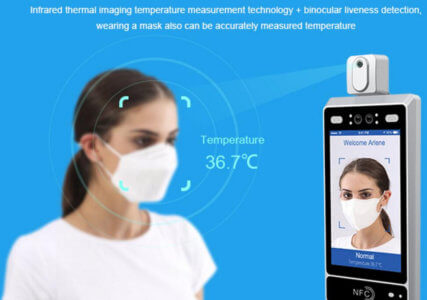
Temperature Access Control Face Recognition
Did You Know That Temperature Access Control Face Recognition Can Help In Finding Body Temperature During The Global Panic Of Any Disease?
The world is experiencing the consistent frenzy of diseases and other types of flues, and building security is a basic worry for the greater part of the business these days. Under the pandemic circumstances, contactless temperature estimating access control terminals have become ventures’ vital hardware to prop the workup. Ordinarily, building security is a typical worry for organizations. Still, numerous entrepreneurs are ignoring the significance of the Temperature Access Control Face Recognition framework without understanding that it can help in discovering the body temperature of an individual in your work spot or living space. An ever-increasing number of spots and nations are getting in the web of communicable diseases in light of the contamination hazard in the work environment. You would be shocked to realize that around 45% of laborers have a chance to be tainted if they don’t take temperature estimations, wash hands, or wear a veil in the up and coming days. How amazing is that?
Functions and features of the device access control download here.
Presently find out what face recognition is. Face recognition is a two-factor authentication framework that is getting sought after because of its well-known alternative for securing access-controlled environments. We have mapped down the best information around a couple of reasons that will make you imagine that you should go for the temperature access control face recognition frameworks for your business. From the benefits to how facial recognition functions in an access control framework, adhere to this article since it will inform you regarding how you can go for the splendid technology in your environment. Much appreciated us later!
Temperature Access Control Face Recognition – What You Need To Know.
The working of facial recognition in an access control environment is stunning to comprehend. At the point when utilized for access control, facial recognition programming looks at the face introduced at the purpose of access to a database of approved people to decide if there is a match. If there is a match, access is in all actuality, and if there is no match, access is denied, and a security caution can be activated. To chop down the contamination way, numerous organizations around the globe are taking this epidemic anticipation principle of early identification. The reason behind why temperature access face control recognition framework is getting astounding reaction since its an ideal substitution of unique card participation and unique finger impression identification participation, which ultimately brings about reduced contact transmission.
Detailed Technical Description Temperature Access Control System download here.
Moreover, if you don’t need individuals to access the structure without your insight, then your business unquestionably needs an access control framework. It’s a very strong security framework through which you can boycott specific individuals who you would prefer not to enter your premises. A portion of the facial recognition temperature access control terminal can identify the body temperature of the person from 0.5 to 0.7 meters, which helps in close contact. Is it true that you are considering how Temperature Access Control Face Recognition functions? Try to keep your hat on! At the point when your body temperature isn’t ordinary and is irregular, there is a shift in the tonality of the voice, which this astonishing security programming detects.
You can install Temperature Access Control Face Recognition System at the entrance of the school, commercial structures, building destinations, hospitals, workplaces, and even in your private space also to make sure about public wellbeing. You can introduce it helpfully as Temperature Access Control Face Recognition framework bolsters correspondence mediums like WIFI, Bluetooth. From applying it to worker attendance in your working environment to utilizing for the participation of the visiting guests, FACIAL RECOGNITION TEMPERATURE ACCESS CONTROL TERMINAL aides in recognizing the tainted individual in advance by estimating their body temperature.
Because of the global frenzy of the infections around the globe, the world is going through an upsetting time. For those of you perusing this article, you should consider picking a temperature access face recognition framework in your workplace or local location because, as indicated by the reports, this terminal can recognize around 10 staff who might be tainted. Increasingly more businesses are going insane for the Temperature Access Control System with Face Recognition frameworks because it helps in recognizing the epidemic spread by China across the globe.
If you introduce temperature access to face recognition in your working space, it can change your client loyalty. YESS!! You heard it right! If you are in a retail business, you can analyze the realities that around 45 % of clients spend more at retail marks that they’re faithful to, and a full 70% of retailers’ business originates from existing clients. Since it is so significant for retailers to win their clients’ loyalty, sagacious retailers are continually searching for approaches to improve loyalty programs. More retailers have been going to mechanical developments to improve loyalty.
You would be flabbergasted to realize that even organizations, as Starbucks, effectively executed loyalty programs into their versatile application. But maybe the most significant retail loyalty innovation is facial recognition. Facial recognition programming offers some amazing favorable circumstances over existing retail loyalty innovation. You should think around a couple benefits of facial recognition if you need to transform your client loyalty. “Saying Good To The Phone Numbers” is the prime explanation you have to choose this innovation.
There are times when you have to give your phone numbers at the supermarket, which is a time expending task. But with Temperature Access Control System with Face Recognition, you can forestall the epidemic illnesses, and it can perceive clients who select into your loyalty program during the checkout of the store without giving the telephone numbers to any more bizarre. How astounding is this? For the more targeted limits and client reward focuses. With the facial recognition client experience stage, retailers can monitor clients’ purchasing inclinations and offer better rewards.
We imagine that Temperature Access Control Face Recognition is an enchantment projectile answer for attracting client loyalty in your business. What’s more, most importantly, this security arrangement is an encouraging sign right now of infection. If you are looking where to request the installation of the Temperature Access Control System with Face Recognition, at that point where you can tell us in the remarks segment, and we will disclose to you where to get the best arrangement, which is upheld by the top specialized care staff.
The magic of Biometrics Access Control
Different Types of Biometrics Access Control
Making sure your facilities and buildings are protected against unwanted intruders is essential for the safety of your employees as well as your property. The right access control security solutions can provide added peace of mind for you and your workers and increased protection for your valuable data and other items. Biometrics technologies can be an integral part of your Houston access control system. Here are some of the most popular ways in which biometrics can be used to protect your people as well as your property.
Access Control Fingerprint Scanning
One of the earliest ways in which biometrics were used to assist criminal investigations, fingerprints have been around in use since the late 1800s as a way to identify criminals. Today, thumbprint and fingerprint recognition technologies are a key feature for many Chicago business security systems. These systems are among the most commonly used in our area because of their ease of installation and their proven effectiveness for access control.
Vascular Biometrics
For areas in which absolute security is critical, vascular biometrics can offer an added layer of protection above that offered by fingerprint scanning. These systems use near-infrared light to scan the pattern of veins in the fingers. This can provide positive confirmation of identity for access purposes and to track movements within your facility.
Access Control Facial Recognition
Facial recognition software has advanced significantly since it was invented in 1964. Today, these biometric technologies can work hand-in-hand with Houston industrial security camera systems to provide a clear record of the activities of employees and guests at your facilities. Even minor differences to look at can be identified by facial recognition scanners, reducing the chance of unwanted access to your facilities.
Iris Scanning
Iris recognition technologies use the unique patterns found in the eye to provide accurate identification for employees. This can provide you with detailed information about the movements and access points used by various individuals in your employ, allowing you to maintain a record of activities throughout your facilities.
Access Control Voice Authentication
Voice-activated access control systems can eliminate the need for badges and passwords while allowing tiered access to various areas of your facility. These systems can sometimes generate false rejections, however , and must be installed and monitored by a qualified security company to achieve the best and most reliable results.
The Fresh Software Solution can provide you Access Control Software installations for your facility. We design, sell and install commercial access control systems designed to keep your people, your property and your premises safe from unwanted intruders.
Get a simple RFID access control!
Maintaining the right physical security measures and access control is of critical importance for data centers. These arrangements should go far beyond the locks on your outside doors. Creating integrated business security systems for your facilities can added peace of mind in safeguarding your equipment and protecting the data of your clients. Here are some key elements that should be part of your general data center physical security plan.
Monitoring Activities
One of the most effective ways to protect your data, people and property is to identify your weak points and monitor your facilities on a continuous basis. Access control software & systems are ideal for tracking the arrivals and departures of employees, vendors and guests to your facilities. They might also provide a valuable record of activities in and around your data center if an unauthorized intrusion or theft should occur.
Maintaining Access Control
Modern access control systems are a key element in your overall security plan. Card entry systems are specifically useful and provide tracking capabilities for your data center. They can also be customized to allow tiered entry to high-security areas, ensuring that only your most trusted employees have access to all parts of your facility. This can limit the risk of unwanted activities while ensuring that a record exists of access to restricted areas of your details center.
Planning for Access Control Software
Making sure that you have a back-up source for power can ensure your office security systems always operate even during an outage. This can also prevent criminals and intruders from taking advantage of these unplanned events to enter your facility. Working together with a company that specializes in providing security services can help you identify the most practical solutions for keeping your power on and your premises secure even during a prolonged electrical outage.
Expanding the Access Perimeter
Making sure that your surveillance and access systems extend to the outer perimeter of your property can provide you with added lead time and energy to respond to threats and contact the authorities. Industrial security cameras can allow you to keep a watchful eye on all entrances and exits from your building and property to make certain greater safety for people and property on your premises.
Fresh Software Solution, we focus on providing customized security systems for industrial and commercial area. We can deliver the comprehensive access control necessary to ensure the safety of your staff members and the security of the data you manage on behalf of your clients.
Access RFID
How To Make Boat Club Access Control By Doing Less
Historic Boat Club Discovers Benefits of Transitioning from Outdated Access System to VIZpin
The Customer
The Vesper Boat Club, located on the Schuylkill River in Philadelphia, PA, is one of the most celebrated rowing clubs in the nation. Founded in 1865, Vesper is a small , not-for-profit run solely by volunteers whose mission is to perpetuate its legacy of developing highly skilled and competitive rowers at all levels by providing its diverse community of members with premier rowing programs and first-class facilities and equipment.
The Challenge
On a day, there are many people arriving and out of the historic boat house, and Vesper must protect them and the club’s boats and
other equipment. At the begining of 2016, Tom Simon, an associate of Vesper Boat Club’s House Committee, inherited access control responsibility
for the club and a traditional and often troublesome card/fob access control solution.
Tom quickly discovered that both the access control system’s manufacturer and installer had gone out of business, so there were no helpful service calls or troubleshooting. What’s more, when any access changes needed to be made, Tom had to use an outdated, unsupported version of Windows, and the club had only a
single, aging laptop that fit the criteria. He comments, “It was an unacceptable situation. If something would be to happen to that old laptop, I would have had no way at all regarding
controlling access᾿
Vesper clearly needed to update their access control solution, but did not want to invest in hardware or technology that
would quickly be out-of-date or cumbersome to manage.
The Solution
A club member introduced Tom to VIZpin’s smartphone access control system. He says, “As soon as I saw it, it was a no-brainer. I immediately knew we could benefit from it. ᾿
VIZpin’s VP1 bluetooth access control reader was attached to Vesper Boat Club’s main entrance door to support smartphone access control, and the organization immediately began realizing the benefits of transitioning to VIZpin’s cloud-based system.
Even though VIZpin’s keyless access control is simple to use, Vesper realized a transition period was necessary, so VIZpin arranged for the new bluetooth enabled door lock system to run in parallel with the old system until a total transition can be completed. Tom notes that not needing to purchase fobs and keep physical inventory of them makes cost savings an additional benefit of the new keyless access control system.
Currently Vesper Boat Club has 142 users with the VIZpin smartphone app and has 140 physical fobs that still need to be converted. Tom concludes, “VIZpin did us a massive favor, allowing us to offer members the smartphone option. The system has already solved numerous challenges for us᾿
Highlights
More secure access ᾿ Because people don’t tend to share phones, the club is now more confident that only those who are granted access get into the building. Tom notes, for example , that in the past, parents tended to share fobs with their children, resulting in the club having unsupervised minors inside the boat house.
More access control ᾿ While Vesper has members who need regular, on-going access to the boat house, the club also has tenants (for example, schools apply the club’s facilities and services) and event participants, where access is needed for limited hours during a particular time frame. With VIZpin, Vesper no longer must issue fobs and then get them back when a plan or event ends. Tom explains, “It’s really no muss, no fuss.
We are able to manage phone-based fobs so they really basically self-destruct when will no longer needed᾿
Better data plus more transparency ᾿ Previously data was often inaccurate and incomplete. Tom explains, “Often, you couldn’t actually tell who fobs belonged to, but now ownership is well-defined. With VIZpin, users set up their own profiles, so it is much less likely that a name will be spelled incorrectly, and there is a phone number to identify the user with, as well᾿ He continues, “The database is really self-maintaining and it will be very easy to turn it over to the next person who will manage it᾿
In addition , with Vesper’s legacy system, the club has not been able to tell who entered and when, but the access data provided by VIZpin is detailed and transparent.
Ease of use ᾿ While the benefits of the VIZpin technology were immediately
apparent, Tom knew that to understand them, it would need to be simple to teach members
how to use it. He explains that more than half of Vesper’s constituents are “of a certain age, ᾿
and using a smartphone app is not intuitive to them, however , “With VIZpin, it’s quite simple to show
users how to use the machine – even members who are not used to working with their phones or tech᾿ In addition , Tom notes that it is easy to learn and teach the system admin.
Access RFID Access Control
Radio-Frequency Identification RFID and access control software involve utilizing small electric gadget to track items. This unique device consists of an antenna and a tiny chip; it can also be used for the same purpose as the magnetic strip on the bar code on the presentation or the magnetic strip on all credit cards. ᾿ With RFID solutions, you will be able to vehicles, inventories and successfully perform an access control.
Access control video management software (VMS) is now able to support Paxton Net2 and COLDSTORE video storage solutions.
Users of Paxton Net2, a browser-based access control solution, can view event-driven video captured by network cameras connected to Wisenet WAVE VMS. Achievable through the free Paxton Net2 plugin, the integration means operators can visually verify the identity of anyone wanting to access a site or sensitive areas of a building, in addition to provide video verification of alarm incidents. Veracity’s COLDSTORE, a ‘direct to disk’ storage system that circumvents the need for network video recorders (NVRs), supports audio and metadata as well as video.
It also offers camera-level fail-over, resilience to network interruptions and optional fully-redundant recording.
” Wisenet IP network video surveillance cameras are now regularly being specified alongside Net2 and COLDSTORE. Bob (HY) Hwang PhD, MD, Hanwha Techwin Europe
“These integrations are important to system integrators because Wisenet IP network video surveillance cameras are now regularly being specified alongside Net2 and COLDSTORE as part of integrated electronic security solutions, ” said Bob (HY) Hwang PhD, MD of Hanwha Techwin Europe. “We are very pleased to experienced the opportunity to work closely with the Paxton and Veracity technical teams to experience the integrations. These are further examples of how WE MOVE with trust’ with technology partners to deliver added value to our mutual customers. “
View the full list of integrations with WiseNet WAVE, which include AI Tech analytics and NCR point of sale systems, here. Launched in January 2018, Wisenet WAVE gets the following features:
Monitoring of up to 64 high-definition video streams
Auto-discover feature ensures connected cameras and a wide range of third-party IP network devices can be addressed and set up in only minutes.
‘Drag & drop’ tool to set up display of live and recorded images on a single screen or video wall, with customisable layouts and sizes.
Virtual PTZ – zoom in to see close-up detail of suspicious activity with a single click
Motion detection and video analytics support can be configured to generate alerts when user-defined incidents occur
Access RFID
sourced from: securityblogs.co.uk
Radio-Frequency Identification RFID and access control software involve utilizing small electric gadget to track items. This unique device consists of an antenna and a tiny chip; it can also be used for the same purpose as the magnetic strip around the bar code on the presentation or the magnetic strip on all credit cards. ᾿ With RFID solutions, you will be able in order to vehicles, inventories and successfully perform an access control. ᾿ You can order customized software by contacting us. ᾿
A former employee stole data on 1.5 million customers, Atlanta-based SunTrust Banks announced on Friday.
The employee appears to have stolen data from some of the company’s contact lists, the company says. SunTrust is already informing impacted clients and is working with outside experts and coordinating with law enforcement on investigations.
The stolen information includes names, addresses, and phone numbers, along with certain account balances, as this was the data included in the contact lists, the company confirmed.
Personally identifying information such as social security numbers, account numbers, PINs, User IDs, passwords, or driver’s license information wasn’t included in the lists.
“We apologize to clients who may have been affected by this. We have heightened our monitoring of accounts and increased other security measures.
While we have not identified significant fraudulent activity…..
How RFID Access control works The Radio-Frequency Identification RFID chips are first integrated into devices like cards, labels, and tags. To retrieve identifying information from the chips, the Radio-Frequency Identification RFID device must be scanned by a compatible reader. The received information is transmitted to the access control software. For instance, a moving car that is equipped with Radio-Frequency Identification RFID tag will easily activate the parking gate arms when the car is close to the area, making the arms quickly rise so the car can enter the lot. Why you need this software? Businesses may assume that using a security guard in place would suffice. It could be so , however the security can only be effective when they see people who enter the building. This requires full guards’ attention and also a number of guards that drive your labor costs up. Yet, unlike this RFID access control software, guards may allow mistakes. The RFID access control software will better help business streamline their work, and make their work more organized and efficient. This reliable automation will also allow the guards focus on other important aspects ensuring that the building remains secure. This system is not only good for securing buildings, but can also be utilized for many other purposes, for example , for tracking of object motions inside the controlled area working as Local Positioning System. Feature and Benefit Of Fresh Access Control This amazing RFID access control software provides full real-time visibility of most visitors and employees in the facility. ᾿ The locks can be enable and disabled automatically depending on access privileges. ᾿ Our software enables automatic exit and entry tracking. Access control software provides reports and cloud-based dashboards based on locations, groups, times and other parameters. ᾿ With the aid of this software, you get automatic alerts on unauthorized access or attempt to access. ᾿ Another significant benefit of this software is the reduction in human error and labor. You will also get increased security and efficiency. It might be utilized to find or locate people in the case of an emergency. ᾿ Also, multiple tenant control is guaranteed. It could possibly be used for attendance and time tracking. Why choose fresh access control software and RFID system? This unique Access Control System by Fresh Software Solution is suitable for various types of RFID access control applications. RFID can effectively handle the control access and personnel to an entire building; it also provides 24hours unmanned operation. This system can be adequately managed remotely with a web interface. The tag and tag holder could be edited, removed and added from the staff in charge without the the need to have them move to the site. The system is also compatible with Fresh Software solution and works as passive RFID tag, RFID hardware, UHF longe range distance. Also, this system also offers group management and customizable reporting.
Access Control Software
sourced from: vizpin.com
Radio-Frequency Identification RFID and access control software involve utilizing small electric gadget to track items. This unique device consists of an antenna and a tiny chip; it can also be used for the same purpose as the magnetic strip around the bar code on the packaging or the magnetic strip on all credit cards. ᾿ With RFID solutions, you will be able to vehicles, inventories and successfully perform an access control. ᾿ You can order customized software by contacting us. ᾿
Paul Bodell, VIZpin CEO
I recently had an interesting discussion with a school administrator at an expensive, private K-12 school in Florida. Like most schools, they needed access control, but were challenged by the balancing act of creating a welcoming, open environment for students, parents, and visitors, while keeping out those with potentially ill-intentions. Striking the right balance was made especially difficult because some very specific needs had to be accommodated.
The system must keep each classroom door locked until a teacher came in, and then remain open until the teacher locked it. Administrators must be able to easily grant/revoke access to teachers based on schedules, eliminating a loc…
How RFID Access control works The Radio-Frequency Identification RFID chips are first integrated into devices such as cards, labels, and tags. To retrieve identifying information from the chips, the Radio-Frequency Identification RFID device needs to be scanned by a compatible reader. The received information is transmitted to the access control software. For instance, a moving car that is equipped with Radio-Frequency Identification RFID tag will easily activate the parking gate arms when the car is close to the area, the arms quickly rise in order that the car can enter the lot. Why you need this software? Businesses may assume that using a security guard in place would suffice. It could be so , however the security can only be effective when they see people who enter the building. This requires full guards’ attention and a number of guards that drive your labor costs up. Yet, unlike this RFID access control software, guards may allow mistakes. The RFID access control software will better help business streamline their work, and make their work more organized and efficient. This reliable automation will also allow the guards focus on other important aspects ensuring that the building remains secure. This system is not only good for securing buildings, but can also be employed for many other purposes, for example , for tracking of object motions inside the controlled area working as Local Positioning System. Feature and Benefit Of Fresh Access Control This amazing RFID access control software provides full real-time visibility of visitors and employees at the facility. ᾿ The locks can be enable and disabled automatically depending on access privileges. ᾿ Our software enables automatic exit and entry tracking. Access control software provides reports and cloud-based dashboards based on locations, groups, times and other parameters. ᾿ With the help of this software, you get automatic alerts on unauthorized access or attempt to access. ᾿ Another significant benefit of this software is the reduction in human error and labor. You will also get increased security and efficiency. It could be utilized to find or locate people in the case of an emergency. ᾿ Also, multiple tenant control is guaranteed. It could possibly be used for attendance and time tracking. Why choose fresh access control software and RFID system? This unique Access Control System by Fresh Software Solution is suitable for a number of00 RFID access control applications. RFID can effectively handle the control access and personnel to an entire building; it also provides 24hours unmanned operation. This system can be adequately managed remotely with a web interface. The tag and tag holder could be edited, removed and added from the staff in charge without the the need to have them move to the site. The machine is also compatible with Fresh Software solution and works as passive RFID tag, RFID hardware, UHF longe range distance. Also, this system also offers group management and customizable reporting.
RFID Access Control Software
Fresh Software Solutions Launches Access Control Software Long Range RFID capabilities save time and money for customers in numerous industries .
Chicago, April, 2018 ᾿ Fresh Software Solutions, a leader in integrated RFID software and hardware products, announced a new long-range RFID solution that will bring convenience and speed to customers᾿ access control. The new long-range RFID eliminates the need for the access control chip to become next to or against the reader, which can streamline operations across industries.
The new software permits the chip to be programmed for scanning anywhere from several inches to 80 feet from the reader.
This long-range solution is a game changer for those businesses that already use RFID technology. RFID (radio frequency identification) is used to automatically identify and track tags or chips attached to objects, products or people. The scanner accumulates information from the tags or chips and the information about the object or person is being transmitted to the access control software, which enables access to doors, gates, machinery and more.
“While RFID has many applications and has been the standard for access control, we knew our customers needed even more convenience, ᾿ says Leri Tomin CEO of Fresh Software Solutions (Fresh USA, Inc. ). “This product will make a big difference for many companies in speed and effectiveness. ᾿
The technology is completely scalable, and can be used for large and small businesses or facilities. One of these of a customer reaping big benefits is at the Geely automobile plant, where the long range RFID helps makes operations more efficient. The technology enables parts and equipment to get easily moved throughout the facility by automatically opening gates as needed. Chip is hard-wired into a product, machinery or car itself and opens the gate or door automatically once the object is within the reachable distance from the reader,. This eliminates the need for an employee to stop operations to open the gate or door and allows the process to continue uninterruptedly.
Not only can objects move more freely throughout the plant but also people can do so. The chip can be stored in someone’s pocket and when the person is within the reachable range from the chip, she can gain entry through locked barriers as needed. This hands-free solution speeds up work on the factory floor.
Factories aren’t the only places where the long range RFID solution can be useful. The technology is beneficial in warehouses for packing and shipping, in retail environments to prevent theft and for employee access in a variety of businesses, offering both convenience and safety.
The Fresh Software Solutions hardware can be found from various distributors , and the software can be downloaded for free from the Fresh Software Solutions website.