- Getting started
- Installation
- Creating your first certificate
- Validation problems
- Testing
- General validation issues
- DNSSEC
- CAA records
- Protocols and cipher suites
- Let’s Encrypt limitations
- Domain count limit
- Non-public domains
- HTTP validation issues
- Firewall
- IPv6 configuration
- FileSystem plugin IIS issues
- win-acme
- Sponsors
- Getting started
- Getting help
- Settings.json
- Client
- ClientName
- ConfigurationPath
- LogPath
- VersionCheck
- DateFormat
- PageSize
- TextEncoding
- DefaultBaseUri
- DefaultBaseUriTest
- DefaultBaseUriImport
- PostAsGet
- RetryCount
- RetryInterval
- PreferredIssuer
- Proxy
- Username
- Password
- Cache
- ReuseDays
- DeleteStaleFiles
- Scheduled task
- RenewalDays
- StartBoundary
- ExecutionTimeLimit
- RandomDelay
- Notifications
- SmtpServer
- SmtpPort
- SmtpUser
- SmtpPassword
- SmtpSecure
- SmtpSecureMode
- SmtpSenderName
- SenderAddress
- ReceiverAddresses
- EmailOnSuccess
- ComputerName
- Security
- RSAKeyBits
- ECCurve
- PrivateKeyExportable
- EncryptConfig
- Script
- Timeout
- Target
- DefaultTarget
- Validation
- DefaultValidation
- DefaultValidationMode
- DisableMultiThreading
- CleanupFolders
- PreValidateDns
- PreValidateDnsRetryCount
- PreValidateDnsRetryInterval
- AllowDnsSubstition
- DnsServers
- Order
- DefaultOrder
- DefaultCsr
- Store
- DefaultStore
- CertificateStore.DefaultStore
- CentralSsl.DefaultPath
- CentralSsl.DefaultPassword
- Pemfiles.DefaultPath
- Pemfiles.DefaultPassword
- PfxFile.DefaultPath
- PfxFile.DefaultPassword
- Installation
- DefaultInstallation
Getting started
Installation
- Download the latest version of the program from this website. For most users the file called win-acme.v2.x.x.xx.x64.trimmed.zip is recommended, but if you want to run on a 32 bit system you should get the x86 version instead of the x64 one, or if you want to download or develop extra plugins, you should get the pluggable version instead of the trimmed one.
- Unzip files to a non-temporary folder, so that the scheduled task will be able to run. We recommend using %programfiles%\win-acme .
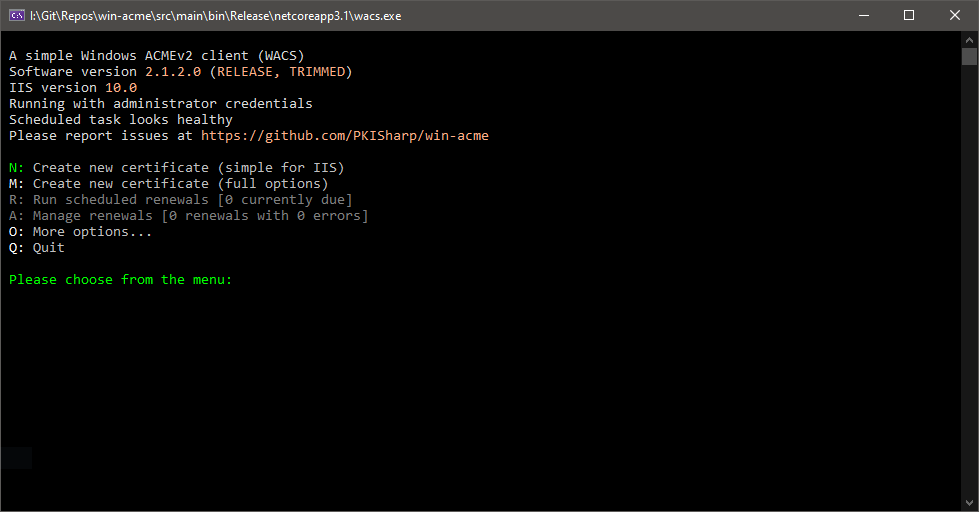
- Run wacs.exe (this requires administrator privileges).
- Follow the instructions on the screen to configure your first renewal.
Creating your first certificate
Note: the default settings are for users looking to install a regular (non-wildcard) certificate on their local IIS instance. For any other scenario you should skip straight to the section on advanced use.
- Choose N in the main menu to create a new certificate with default settings.
- Choose how you want to determine the domain name(s) that you want to include in the certificate. This can be derived from the bindings of an IIS site, or you can input them manually.
- A registration is created with the ACME server, if no existing one can be found. You will be asked to agree to its terms of service and to provide an email address that the administrators can use to contact you.
- The program negotiates with ACME server to try and prove your ownership of the domain(s) that you want to create the certificate for. By default the http validation mode is picked, handled by our self-hosting plugin. Getting validation right is often the most tricky part of getting an ACME certificate. If there are problems please check out some common issues.
- After the proof has been provided, the program gets the new certificate from the ACME server and updates or creates IIS bindings as required, according to the logic documented here.
- The program remembers all choices that you made while creating the certificate and applies them for each subsequent renewal.
Validation problems
Validation is an important aspect of the ACME and Let’s Encrypt, but there are many subtle ways that it can fail. This page is meant for people who run into problems to help figure out what the issue might be.
Testing
Run wacs.exe with the —test and —verbose parameters to watch your validation unfold in ‘slow motion’. This will run against the Let’s Encrypt staging server so you don’t risk running into any rate limits. If you want to test against the production endpoint, include the parameter —baseuri https://acme-v02.api.letsencrypt.org/ as well.
General validation issues
DNSSEC
ACME providers will typically validate your DNSSEC configuration. If there is anything suspicious about it, your browser might not complain, but you will not be able to get a certificate. A useful tool to check your (provider’s) DNSSEC configuration from the perspective of a strict external observer is the Unbound DNS checker.
CAA records
ACME providers will check for the existence and validity of a CAA record for your domain. You may have to add a record like `example.com. CAA 0 issue “letsencrypt.org” to your DNS server in order to allow the provider to issue certificates for your domain. This can be checked using Let’s Debug.
Protocols and cipher suites
Tools like IISCrypto are often used configure the cipher suites of Windows systems according to the latest best practices. Changing these settings always brings some risk of breaking compatibility between two parties though. Too restrictive cipher suites have been known to hamper the ability to communicate with the ACME API endpoint and its validation servers. If that happens try more conservative settings. Test if the API endpoint is accessible from a web browser on your server.
Let’s Encrypt limitations
The following limitations apply to Let’s Encrypt and may not be true for every ACME service provider.
Domain count limit
Let’s Encrypt does not support more than 100 domain names per certificate.
Non-public domains
Let’s Encrypt can only be used to issue certificates for domains living on the public internet. Interal domains or Active Directory host names are therefor not possible to use.
HTTP validation issues
Firewall
HTTP validation happens on port 80, so it will have to open on your firewall(s). Let’s Encrypt doesn’t disclose IP address range(s) for their validation servers, meaning port 80 will have to be accessible from any origin, at least for the duration of the validation.
IPv6 configuration
Let’s Encrypt will check IPv6 access to your site if AAAA records are configured. Many browsers and networks don’t use IPv6 yet or automatically fallback to IPv4 when an error occurs, so it might not be immediately obvious that your site is unreachable on IPv6. You can test it here.
FileSystem plugin IIS issues
Note that it’s recommended to use the default SelfHosting validation plugin in combination with IIS. The FileSystem validation is great of other web servers such as Apache, but using it in combination with IIS leads to many potentials issues, described in the following sections.
CMS modules
Your CMS might intercept the request and redirect the user to an (error) page. The solution is to configure your CMS to allow unlimited access to the /.well-known/acme-challenge/ path.
Problems with httpHanders
IIS might not be configured to serve static extensionless files.
- In IIS manager go to the /.well-known/acme-challenge/ folder of the site (you may have to create it). Don’t do this at the root of the server or the website, because it might break your application(s).
- Choose Handler Mappings -> View Ordered List.
- Move the StaticFile mapping above the ExtensionlessUrlHandler mappings.
Anonymous authentication
Your website might require Windows authentication, client certificates or other authentication methods. Enable anonymous authentication to the /.well-known/acme-challenge/ path to allow access from the ACME server.
Require SSL
Your website might be configured to exclusively accept SSL traffic, while the validation request comes in on port 80. Disable the “Require SSL” setting for the /.well-known/acme-challenge/ path to fix that.
IP Address and Domain Restrictions
Your website might use IP Address and Domain Restrictions to provide extra security. The ACME server will have to bypass though. Let’s Encrypt does not publicize a list of IP addresses that they can use for validation, so this features needs to be disabled for the /.well-known/acme-challenge/ path.
URL Rewrite
If you are using URL Rewrite the validation request might get caught up in that, so you have to make exceptions for the /.well-known/acme-challenge/ path. For example like so:
win-acme
This is a ACMEv2 client for Windows that aims to be very simple to start with, but powerful enough to grow into almost every scenario.
- A very simple interface to create and install certificates on a local IIS server
- A more advanced interface for many other use cases, including Apache and Exchange
- Automatically creates a scheduled task to renew certificates when needed
- Get certificates with wildcards ( *.example.com ), international names ( 证书.example.com ), OCSP Must Staple extension (optional).
- Re-use private keys for DANE, use EC crypto or bring your own CSR
- Advanced toolkit for DNS, HTTP and TLS validation: SFTP/FTPS, acme-dns, Azure, Route53, Cloudflare and many more…
- Store your certificates where and how you want them: Windows, IIS Central Store, .pem files, .pfx file or KeyVault
- Compatible with all popular ACME services, including Let’s Encrypt, ZeroSSL, DigiCert, Sectigo, Buypass, Keyon and others…
- Completely unattended operation from the command line
- Other forms of automation through manipulation of .json files
- Write your own Powershell .ps1 scripts to handle installation and validation
- Build your own plugins with C#
Sponsors
eGov Strategies
Insurance Technology Services
- e-shop LTD
- The Proof Group @proofgroup
- imagenia.fr
Getting started
Download the .zip file from the download menu, unpack it to a location on your hard disk and run wacs.exe .
Alternatively install .NET Core, run dotnet tool install win-acme —global and then wacs.exe .
Getting help
If you require assistance please check the manual first before looking for support.
Settings.json
Some of the applications’ settings can be modified in a file called settings.json . If this file is not present when the program starts it will be automatically created on first run, copied from settings_default.json . This allows you to xcopy new releases without worrying about overwriting your previously customized settings.
Client
ClientName
The name of the client, which comes back in the scheduled task and the ConfigurationPath .
ConfigurationPath
Change the location where the program stores its (temporary) files. If not specified this resolves to %programdata%\
LogPath
The path where log files for the past 31 days are stored. If not specified or invalid, this defaults to
VersionCheck
Automatically check for new versions at startup.
DateFormat
Default: «yyyy/M/d H:mm:ss»
A string that is used to format the date of the certificates friendly name. Documentation for possibilities is available from Microsoft.
PageSize
The number of items to display per page in list views.
TextEncoding
Encoding to use for the console output. A list of possible values can be found here. For certain languages «unicode» might give better results displaying the characters, but note that this reduces compatibility with other programs processing the output.
DefaultBaseUri
Default ACMEv2 endpoint to use when none is specified with the command line.
DefaultBaseUriTest
Default ACMEv2 endpoint to use when none is specified with the command line and the —test switch is activated.
DefaultBaseUriImport
Default ACMEv1 endpoint to import renewal settings from.
PostAsGet
Use [POST-as-GET] mode as defined in RFC8555, will be required by Let’s Encrypt in production from November 2020, and in test from November 2019.
RetryCount
Maximum numbers of times to refresh validation and order status, while waiting for the ACME server to complete its tasks.
RetryInterval
Amount of time in seconds to wait for each retry.
PreferredIssuer
In some exceptional cases an ACME service will offer multiple certificates signed by different root authorities. This setting can be used to give a preference. I.e. «ISRG Root X1» can be used to prefer Let’s Encrypt first fully self-signed root before it becomes the default on January 11th, 2021, and «DST Root CA X3» can be set for backwards compatibility with old Android releases (until September 30th, 2021).
Proxy
Configures a proxy server to use for communication with the ACME server and other HTTP requests done by the program. The default setting uses the system proxy. Passing an empty string will try to bypass the system proxy.
Username
Username used to access the proxy server.
Password
Password used to access the proxy server.
Cache
The path where certificates and request files are cached. If not specified or invalid, this defaults to
ReuseDays
When renewing or re-creating a previously requested certificate that has the exact same set of domain names, the program will used a cached version for this many days, to prevent users from running into rate limits while experimenting. Set this to a high value if you regularly re-request the same certificates, e.g. for a Continuous Deployment scenario.
DeleteStaleFiles
Automatically delete files older than 120 days from the CertificatePath folder. Running with default settings, these should only be long-expired certificates, generated for abandoned renewals. However we do advise caution.
Scheduled task
RenewalDays
The number of days to renew a certificate after. Let’s Encrypt certificates are currently for a max of 90 days so it is advised to not increase the days much. If you increase the days, please note that you will have less time to fix any issues if the certificate doesn’t renew correctly.
StartBoundary
Default: «09:00:00» (9:00 am)
Configures start time for the scheduled task.
ExecutionTimeLimit
Default: «02:00:00» (2 hours)
Configures time after which the scheduled task will be terminated if it hangs for whatever reason.
RandomDelay
Configures random time to wait for starting the scheduled task.
Notifications
SmtpServer
SMTP server to use for sending email notifications. Required to receive renewal failure notifications.
SmtpPort
SMTP server port number.
SmtpUser
User name for the SMTP server, in case of authenticated SMTP.
SmtpPassword
Password for the SMTP server, in case of authenticated SMTP.
SmtpSecure
Change to true to enable secure SMTP.
SmtpSecureMode
| Value | Meaning |
|---|---|
| 1 | Automatic (based on port number) |
| 2 | Implicit TLS |
| 3 | Explicit TLS (required) |
| 4 | Explicit TLS (when available) |
SmtpSenderName
Display name to use as the sender of notification emails. Defaults to the ClientName setting when empty.
SenderAddress
Email address to use as the sender of notification emails. Required to receive renewal failure notifications.
ReceiverAddresses
Email address to receive notification emails. Required to receive renewal failure notifications. The correct format for the receiver is [«example@example.com»] for a single address and [«example1@example.com», «example2@example.com»] for multiple addresses.
EmailOnSuccess
Send an email notification when a certificate has been successfully created or renewed, as opposed to the default behavior that only send failure notifications. Only works if at least SmtpServer , SmtpSenderAddress and SmtpReceiverAddress have been configured.
ComputerName
This value replaces the Windows machine name reported in emails.
Security
RSAKeyBits
The key size to sign the certificate with. Minimum is 2048.
ECCurve
The curve to use for EC certificates.
PrivateKeyExportable
If set to true , it will be possible to export the generated certificates from the certificate store, for example to move them to another server.
EncryptConfig
Uses Microsoft Data Protection API to encrypt sensitive parts of the configuration, e.g. passwords. This may be disabled to share the configuration across a cluster of machines.
Script
Timeout
Time in seconds to allow installation and DNS scripts to run before terminating them forcefully.
Target
DefaultTarget
Default target plugin. This only affects the menu in the UI. null equivalent to «iis» with «manual» as backup for non-administrators or systems without IIS.
Validation
DefaultValidation
Default validation plugin, null currently equivalent to «selfhosting» with «filesystem» as backup for non-administrators.
DefaultValidationMode
Default validation method, null currently equivalent to «http-01» .
DisableMultiThreading
Disable multithreading features for validation. Inceases runtime but may help to fix bugs caused by race conditions.
CleanupFolders
If set to true , it will cleanup the folder structure and files it creates under the site for authorization.
PreValidateDns
If set to true , it will wait until it can verify that the validation record has been created and is available before beginning DNS validation.
PreValidateDnsRetryCount
Maximum numbers of times to retry DNS pre-validation, while waiting for the name servers to start providing the expected answer.
PreValidateDnsRetryInterval
Amount of time in seconds to wait between each retry.
AllowDnsSubstition
If your goal is to get a certificate for example.com using DNS validation, but the DNS provider for that domain does not support automation and/or your security policy doesn’t allow third party tools like win-acme to access the DNS configuration, then you can set up a CNAME from _acme-challenge.example.com to another (sub)domain under your control that doesn’t have these limitations. acme-dns is based on this principle, but the same trick can be applied to any of the DNS plugins. Set this value to false to disable the feature.
DnsServers
Default: [ «8.8.8.8», «1.1.1.1», «8.8.4.4» ]
A list of servers to query during DNS prevalidation checks to verify whether or not the validation record has been properly created and is visible for the world. These servers will be used to located the actual authoritative name servers for the domain. You can use the string [System] to have the program query your servers default, but note that this can lead to prevalidation failures when your Active Directory is hosting a private version of the DNS zone for internal use.
Order
DefaultOrder
Default order plugin, null currently equivalent to «single»
DefaultCsr
Default order plugin, null currently equivalent to «rsa»
Store
DefaultStore
Default store plugin(s), null currently equivalent to «certificatestore» . This may be a comma seperated value for multiple default store plugins.
CertificateStore.DefaultStore
The certificate store to save the certificates in. If left empty, certificates will be installed either in the WebHosting store, or if that is not available, the My store (better known as Personal ).
CentralSsl.DefaultPath
When using —store centralssl this path is used by default, saving you the effort from providing it manually. Filling this out makes the —centralsslstore parameter unnecessary in most cases. Renewals created with the default path will automatically change to any future default value, meaning this is also a good practice for maintainability. Values should be JSON-encoded, e.g. «C:\\» (note the double backslash).
CentralSsl.DefaultPassword
When using —store centralssl this password is used by default for the pfx files, saving you the effort from providing it manually. Filling this out makes the —pfxpassword parameter unnecessary in most cases. Renewals created with the default password will automatically change to any future default value, meaning this is also a good practice for maintainability.
Pemfiles.DefaultPath
When using —store pemfiles this path is used by default, saving you the effort from providing it manually. Filling this out makes the —pemfilespath parameter unnecessary in most cases. Renewals created with the default path will automatically change to any future default value, meaning this is also a good practice for maintainability. Values should be JSON-encoded, e.g. «C:\\» (note the double backslash).
Pemfiles.DefaultPassword
When using —store pemfiles this password is used by default for the pfx files, saving you the effort from providing it manually. Filling this out makes the —pempassword parameter unnecessary in most cases. Renewals created with the default password will automatically change to any future default value, meaning this is also a good practice for maintainability.
PfxFile.DefaultPath
When using —store pfxfile this path is used by default, saving you the effort from providing it manually. Filling this out makes the —pfxfilepath parameter unnecessary in most cases. Renewals created with the default path will automatically change to any future default value, meaning this is also a good practice for maintainability. Values should be JSON-encoded, e.g. «C:\\» (note the double backslash).
PfxFile.DefaultPassword
When using —store pfxfile this password is used by default for the pfx files, saving you the effort from providing it manually. Filling this out makes the —pfxpassword parameter unnecessary in most cases. Renewals created with the default password will automatically change to any future default value, meaning this is also a good practice for maintainability.
Installation
DefaultInstallation
Default installation plugin(s), null currently equivalent to «none» for unattended usage and «iis» for interactive mode. This may be a comma seperated value for multiple default installation plugins.

 eGov Strategies
eGov Strategies Insurance Technology Services
Insurance Technology Services


