- View the Windows application log (Windows 10)
- View the Windows application log
- Создаем собственный журнал событий в Windows
- Просмотр журнала приложений Windows (Windows 10) View the Windows application log (Windows 10)
- Просмотр журнала приложений Windows View the Windows application log
- Windows Event Logs — Event Log FAQ
- What is Windows event log?
- How to view event logs?
- What is Windows Event Log Service?
- What are Windows event log files?
- What is Windows Application event log?
- What is Windows System event log?
- Eventlog Key
View the Windows application log (Windows 10)
Applies to: SQL Server (all supported versions)
SQL Server is configured to use the Windows application log, each SQL Server session writes new events to that log. Unlike the SQL Server error log, a new application log is not created each time you start an instance of SQL Server.
View the Windows application log
On the Search bar, type Event Viewer, and then select the Event Viewer desktop app.
In Event Viewer, open the Applications and Services Logs.
SQL Server events are identified by the entry MSSQLSERVER (named instances are identified with MSSQL$ ) in the Source column. SQL Server Agent events are identified by the entry SQLSERVERAGENT (for named instances of SQL Server, SQL Server Agent events are identified with SQLAgent$ ). Microsoft Search service events are identified by the entry Microsoft Search.
To view the log of a different computer, right-click Event Viewer (local). Select Connect to another computer, and fill in the fields to complete the Select Computer dialog box.
Optionally, to display only SQL Server events, on the View menu, select Filter. In the Event source list, select MSSQLSERVER. To view only SQL Server Agent events, instead select SQLSERVERAGENT in the Event source list.
To view more information about an event, double-click the event.
Создаем собственный журнал событий в Windows
Как вы знаете, большинство «нормальных» приложений записывают свои события в журнал событий Windows (Application Event Log). Это отличное место для централизованного хранения и просмотра событий приложений, однако зачастую при возникновении необходимости журналировать события от определенного приложения в данном журнале, мы можем столкнуться с тем, что из-за большого количества и чрезмерной подробности событий, работать со стандартным журналом приложений Windows становится очень неудобно. В данном случае было бы удобно создать собственный журнал событий для данного приложения, и для него настраивать различные параметры, такие как размер журнала, фильтры и т.д., а стандартный журнал Application можно использовать как обычно, не засоряя его ненужной информацией. В ОС семейства Windows присутствует функция, позволяющая создать собственный журнал событий.
Сначала создадим новый файл журнала. Сделать это можно при помощи реестра. Запустите редактор реестра regedit и перейдите в ветку:
Щелкните правой кнопкой по узлу Eventlog и создайте новый ключ (New > Key)
Имя ключа в этом случае будет являться и именем нового журнала. По умолчанию новый журнал (файл .evt) создается тут:
Его можно переименовать, изменив строковый параметр в реестре по своему усмотрению.
Далее нужно добавить источники (Sources) событий для нового журнала. Создайте новый ключ типа Multi-String с именем “Sources”, в качестве параметров укажите имена всех приложений, который будут использовать данный журнал (каждое приложение с новой строки).
Затем нужно перенести ассоциации ваших приложений из стандартного журнала Application в ваш новый журнал. Разверните ветку “Application”, находящуюся по адресу:
И скопируйте все ветки, которые относятся к интересуемым Вами приложениям в новый ветку реестра нового журналa:
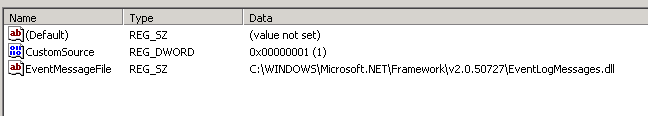
Т.к. команда скопировать/вставить в редакторе реестра не работает, их можно пересоздать вручную (если их немного), или же можно осуществить перенос при помощи процедуры экспорта/импорта веток реестра с ручным редактирование .reg файла. Убедитесь, что после переноса вы удалили ключи реестра ваших приложений из ветки Application, иначе Windows не поймет, что нужно писать события в новый журнал. В том случае, если вы используете новый источник событий для журнала, нужно будет создать параметр типа DWORD с именем CustomSource и значением равным 1:
В моем примере, я создал собственное приложение .NET 2.0, причем я хочу, чтобы оно записывало события в созданный нами журнал. Для этого я создам новый ключ реестра EventMessageFile и укажу в нем путь к библиотеке журналирования.NET 2.0:
Затем нужно перезагрузить Windows, а после загрузки системы вы увидите новый журнал событий в разделе Event Viewer-а. В том случае, если ваше приложение по какой-либо причине не пишет событий в новый журнал, можно протестировать его работу вручную, откройте командую строку и перейдите в каталог:
В том случае, если вы все сделали правильно должно появиться окно, сообщающее о том, что событие было успешно записан в журнал, либо сообщение об ошибки и причины ее появления.
Update:
Небольшое обновление статьи по письмам читателей:
Вышеприведенная инструкция по созданию собственного журнала ориентирована на серверные ОС семейства Microsoft. Более общий способ, который должен работать в большинстве Windows следующий (отличаются пути в реестре и ключи):
Создаем новый раздел в реестре (имя раздела — имя создаваемого журнала), путь к созданному будет таким:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Eventlog\NewEventLog , в котором нужно создать следующие ключи:
- «AutoBackupLogFiles» — тип DWORD, создавать или нет резервные копии журнала (0 — не создавать)
- «MaxSize» -тип DWORD, максимальны размер журнала в байтах, значение должно быть кратным 64Кб
- «Retention» — тип DWORD, время хранения записей в случае переполнения журнала.
- «File» — тип REG_EXPAND_SZ, строка, в которой содержится путь к логу журнала на жестком диске, например %SystemRoot%\System32\config\NewEventLog.evt)
- «Sources»- тип REG_MULTI_SZ, здесь указан список источников событий, чьи логи должны попадать в этот журнал, каждый источник с новой строки
Просмотр журнала приложений Windows (Windows 10) View the Windows application log (Windows 10)
Применимо к: Applies to: SQL Server SQL Server (все поддерживаемые версии) SQL Server SQL Server (all supported versions) Применимо к: Applies to: SQL Server SQL Server (все поддерживаемые версии) SQL Server SQL Server (all supported versions)
Когда для SQL Server SQL Server настроено использование журнала приложений Windows, каждый сеанс SQL Server SQL Server записывает новые события в этот журнал. SQL Server SQL Server is configured to use the Windows application log, each SQL Server SQL Server session writes new events to that log. В отличие от журнала ошибок SQL Server SQL Server , новый журнал приложений не создается заново каждый раз при запуске экземпляра SQL Server SQL Server . Unlike the SQL Server SQL Server error log, a new application log is not created each time you start an instance of SQL Server SQL Server .
Просмотр журнала приложений Windows View the Windows application log
На панели поиска введите средство просмотра событий, а затем выберите классическое приложение Просмотр событий. On the Search bar, type Event Viewer, and then select the Event Viewer desktop app.
В средстве просмотра событий откройте журналы приложений и служб. In Event Viewer, open the Applications and Services Logs.
События SQL Server SQL Server идентифицируются записью MSSQLSERVER в столбце Источник (именованные экземпляры обозначаются как MSSQL$ ). SQL Server SQL Server events are identified by the entry MSSQLSERVER (named instances are identified with MSSQL$ ) in the Source column. События агента SQL Server идентифицируются записью SQLSERVERAGENT (для именованных экземпляров сервера SQL Server SQL Server события агента SQL Server SQL Server идентифицируются при помощи SQLAgent$ ). SQL Server Agent events are identified by the entry SQLSERVERAGENT (for named instances of SQL Server SQL Server , SQL Server SQL Server Agent events are identified with SQLAgent$ ). События службы Microsoft Search идентифицируются записью Microsoft Search. Microsoft Search service events are identified by the entry Microsoft Search.
Чтобы просмотреть журнал с другого компьютера, щелкните правой кнопкой мыши элемент Просмотр событий (локальных) . To view the log of a different computer, right-click Event Viewer (local). Выберите пункт Подключение к другому компьютеру и заполните поля в диалоговом окне Выбор компьютера. Select Connect to another computer, and fill in the fields to complete the Select Computer dialog box.
Чтобы отображались только события SQL Server SQL Server , в меню Вид выберите пункт Фильтр. Optionally, to display only SQL Server SQL Server events, on the View menu, select Filter. В списке Источник событий выберите MSSQLSERVER. In the Event source list, select MSSQLSERVER. Чтобы просмотреть только события агента SQL Server SQL Server , в списке Источник события вместо этого выберите SQLSERVERAGENT . To view only SQL Server SQL Server Agent events, instead select SQLSERVERAGENT in the Event source list.
Чтобы просмотреть дополнительные сведения о событии, дважды щелкните событие. To view more information about an event, double-click the event.
Windows Event Logs — Event Log FAQ
What is Windows event log?
Event logs are special files that record significant events on your computer, such as when a user logs on to the computer or when a program encounters an error. Whenever these types of events occur, Windows records the event in an event log. Users might find the details in event logs helpful when troubleshooting problems with Windows and other programs.
Unlike UNIX syslog, Microsoft event log is not a text file and it is impossible to view it with simple text editors. Microsoft Windows event log is a binary file that consists of special records – Windows events.
Microsoft Windows runs Event Log Service to manage event logs, configure event publishing, and perform operations on the logs. Windows Event Log service exposes a special API, which allows applications to maintain and manage event logs.
Windows event logging was introduced in Windows NT operating system (version 3.1) in 1993. This Windows edition came with three Windows logs: Application event log, System event log and Security event log. Modern versions of Windows come with more than a hundred of Windows eventlogs, and third party applications can create and integrate into Windows logging their own event logs.
How to view event logs?
You can view eventlogs using Event Viewer (comes with Windows operating system) or third-party Windows event viewers. We recommend using our Event Log Explorer software – it provides a lot of advanced features for event log management.
What is Windows Event Log Service?
Windows Event Log Service is a Windows service that manages events and event logs. It supports logging events, querying events, subscribing to events, archiving event logs, and managing event metadata. It helps to display events in both XML and plain text format. This service is enabled and starts automatically by default. You should not stop or disable this service. Stopping Windows Event Log service may compromise security and reliability of the system.
What are Windows event log files?
Windows Event Log Service lets users to save (backup) event logs to files. Windows NT, 2000 and XP/2003 save event logs to EVT format. Windows Vista/2008 and better save logs to EVTX format. Having backup event files are essential for incident investigation.
Windows event logs are also files, but they are commonly locked by Windows (Event Log Service) and it is impossible to open these files on «live» system. But if the computer is started from another disk or the system drive from the analyzed machine is connected to another computer, you can read event logs as files. The default location of event logs on Vista/2008 and better is «C:\Windows\System32\winevt\Logs\». Windows Event Viewer allows you to open event file as follows:
Click Open Saved Log in Actions pane of Event Viewer.
Select your event log file and it will appear in Windows Event Viewer as a log.
Our Event Log Explorer software also works with event files and does it even better than Event Viewer, e.g. it lets you read even damaged event files.
What is Windows Application event log?
The Application log contains events logged by applications or programs. For example, a database program might record a file error in the application log. Program developers decide which events should be logged. E.g. Microsoft SQL Server logs details about important events linked with SQL server, e.g. «out of memory», «backup failure» etc. One application log commonly contains events logged from different sources (applications), so it is incorrect to rely solely on event ID when analyzing the Application log. You should always rely on event ID along with event source. Some applications, such as Internet Explorer, Power Shell create own event log instead of using Windows application event log. Such logs look exactly like standard Windows event logs and Event Viewer (as well as Event Log Explorer) can read these event logs. Application logs are commonly useful for application support teams.
What is Windows System event log?
The System log contains events logged by Windows system components. For example, the failure of a driver or other system component to load during startup is recorded in the system log. The event types logged by system components are predetermined by Windows. Similarly to Application log, System event log lists events from different sources (system components) so you should not rely only on event ID when analyzing System log, instead you should rely on event ID along with event source. System logs are essential for system administrators and technicians.
Eventlog Key
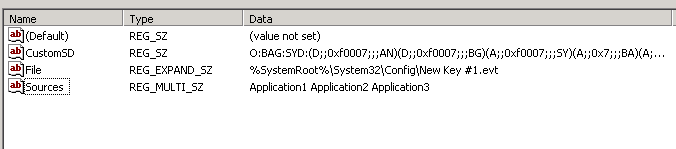
The event log contains the following standard logs as well as custom logs:
| Log | Description |
|---|---|
| Application | Contains events logged by applications. For example, a database application might record a file error. The application developer decides which events to record. |
| Security | Contains events such as valid and invalid logon attempts, as well as events related to resource use such as creating, opening, or deleting files or other objects. An administrator can start auditing to record events in the security log. |
| System | Contains events logged by system components, such as the failure of a driver or other system component to load during startup. |
| CustomLog | Contains events logged by applications that create a custom log. Using a custom log enables an application to control the size of the log or attach ACLs for security purposes without affecting other applications. |
The event logging service uses the information stored in the Eventlog registry key. The Eventlog key contains several subkeys, called logs. Each log contains information that the event logging service uses to locate resources when an application writes to and reads from the event log.
The structure of the Eventlog key is as follows:
Note that domain controllers record events in the Directory service and File Replication service logs and DNS servers record events in the DNS server.
Each log can contain the following registry values.
| Registry value | Description |
|---|---|
| CustomSD | Restricts access to the event log. This value is of type REG_SZ. The format used is Security Descriptor Definition Language (SDDL). Construct an ACL that grants one or more of the following rights: Clear (0x0004) Read (0x0001) Write (0x0002) To be a syntactically valid SDDL, the CustomSD value must specify an owner and a group owner (for example, O:BAG:SY), but the owner and group owner are not used. If CustomSD is set to a wrong value, an event is fired in the System event log when the event log service starts, and the event log gets a default security descriptor which is identical to the original CustomSD value for the Application log. SACLs are not supported. For more information, see Event Logging Security. Windows Server 2003: SACLs are supported. Windows XP/2000: This value is not supported. |
| DisplayNameFile | This value is not used. Windows Server 2003 and Windows XP/2000: Name of the file that stores the localized name of the event log. The name stored in this file appears as the log name in Event Viewer. If this entry does not appear in the registry for an event log, Event Viewer displays the name of the registry subkey as the log name. This value is of type REG_EXPAND_SZ. The default value is %SystemRoot%\system32\els.dll. |
| DisplayNameID | This value is not used. Windows Server 2003 and Windows XP/2000: Message identification number of the log name string. This number indicates the message in which the localized display name appears. The message is stored in the file specified by the DisplayNameFile value. This value is of type REG_DWORD. |
| File | Fully qualified path to the file where each event log is stored. This enables Event Viewer and other applications to find the log files. This value is of type REG_SZ or REG_EXPAND_SZ. This value is optional. If the value is not specified, it defaults to %SystemRoot%\system32\winevt\logs\ followed by a file name that is based on the event log registry key name.The specific event log file path should be set using the command line utility wevtutil.exe or by using the EvtSetChannelConfigProperty function with EvtChannelLoggingConfigLogFilePath passed into the PropertyId parameter. If a specific file is set, make sure that the event log service has full permissions on the file. This value needs to be a valid file name for a file that is located on a local directory (not a remote computer, not a DOS device, not a floppy, and not a pipe). If the file setting is wrong, an event is fired in the System event log when the event log service starts. Do not use environment variables, in the path to the file, that cannot be expanded in the context of the event log service. Windows Server 2003 and Windows XP/2000: This value defaults to %SystemRoot%\system32\config\ followed by a file name that is based on the event log registry key name. If the File setting is set to an invalid value, the log will either not be initialized properly, or all requests will silently go to the default log (Application). |
| MaxSize | Maximum size, in bytes, of the log file. This value is of type REG_DWORD. The value must be set to a multiple of 64K for a System, Application, or Security log. The default value is 1MB.Windows Server 2003 and Windows XP/2000: The value is limited to 0xFFFFFFFF, and the default value is 512K. |
| PrimaryModule | This value is not used.Windows Server 2003 and Windows XP/2000: This value is the name of the subkey that contains the default values for the entries in the subkey for the event source. This value is of type REG_SZ. |
| Retention | This value is of type REG_DWORD. The default value is 0. If this value is 0, the records of events are always overwritten. If this value is 0xFFFFFFFF or any nonzero value, records are never overwritten. When the log file reaches its maximum size, you must clear the log manually; otherwise, new events are discarded. You must also clear the log before you can change its size.Windows Server 2003 and Windows XP/2000: This value is the time interval, in seconds, that records of events are protected from being overwritten. When the age of an event reaches or exceeds this value, it can be overwritten. |
| Sources | This value is not used. Windows Server 2003 and Windows XP/2000: Names of the applications, services, or groups of applications that write events to this log. This value should only be read and not altered. The event log service maintains the list based on each program listed in a subkey under the log. This value is of type REG_MULTI_SZ. |
| AutoBackupLogFiles | This value is of type REG_DWORD, and is used by the event log service to determine whether an event log should be automatically saved. The default value is 0, which disables auto-backup. The service will back up the log file only if the retention value is -1 (0xFFFFFFFF). Other values will be ignored.Windows Server 2003: Retention can be set to -1 (0xFFFFFFFF) or 1 (0x00000001) for AutoBackupLogFiles to work. Other values will be ignored. |
| RestrictGuestAccess | This value is not used. Windows XP/2000: This value is of type REG_DWORD, and the default value is 1. When the value is set to 1, it restricts the Guest and Anonymous account access to the event log, and when this value is 0, it allows Guest account access to the event log. |
| Isolation | Defines the default access permissions for the log. This value is of type REG_SZ. You can specify one of the following values:
The default isolation is Application. The default permissions for Application are (shown using SDDL): |
Each log also contains event sources. For more information, see Event Sources.