- How to See Which Group Policies are Applied to Your PC and User Account
- Using a GUI
- Using The Command Line
- Check users in a security group in SQL Server
- 6 Answers 6
- Check if a user is in a group
- 13 Answers 13
- Check whether the user name is in the administrator group
- 3 Answers 3
- How to check if a user account is an Administrator in Windows 10
- How to check if you have Admin rights on Windows 10
- 1] Using the Settings app
- 2] Using PowerShell
- 3] Using Control Panel
- 4] using Local Users and Groups
- Related Posts
- You must have Read permissions to view the properties of this object
- You require permission from TrustedInstaller to make changes to this folder
- How to remove deleted User Account from login screen in Windows 10
- [email protected]
How to See Which Group Policies are Applied to Your PC and User Account
If you’re running a Professional (or higher) version of Windows, then you may have run into the Group Policy Editor before. Basically, it is a hidden control panel that lets you set computer-level or user-level settings. If you’re a Systems Administrator, then you can set group policies at your domain level, then push them out to the clients on your network.
If you ever wanted to know what group policies are enabled on your computer, you have a few ways of finding out.
Using a GUI
The easiest way to see which Group Policy settings have been applied to your machine or user account is to use the Resultant Set of Policy Management Console. To open it, press the Win + R keyboard combination to bring up a run box.
Type rsop.msc into the run box and then hit enter.
You will see a pop-up dialog for the small period of time it take Windows to query your system.
Once the console opens you will be able to see which settings have been applied to your PC.
Note: Only settings that have been applied to your machine and user account will show up.
Using The Command Line
You could also use the command line if you prefer it. When using the command line, it should be noted that you have to specify the scope of the results. To find all the policies that are applied to your user account, you would use the following command:
gpresult /Scope User /v
Then if you scroll down, you will see the the Resultant Set Of Policies for User section.
If you are looking for all policies applied to your Computer, all you need to do is change the scope:
Check users in a security group in SQL Server
In the Security/Users folder in my database, I have a bunch of security groups, include «MyApplication Users». I need to check if I am (or another user is) in this group, but I have no idea how to query for it or where I could see this information. I tried looking in the properties, but couldn’t find anything. Any ideas?
6 Answers 6
Checking yourself or the current user:
A result of 1 = yes,0 = no, and null = the group or role queried is not valid.
To get a list of the users, try xp_logininfo if extended procs are enabled and the group in question is a windows group :
For a quick view of which groups / roles the current user is a member of;
Accepted answer from DeanG is the preferred solution for getting this info within SQL Server
You can use Active Directory tools for this. I like Active Directory Users and Computers that is part of the Remote Server Administration Tools. Follow the link to download and install the tools on Windows 7.
Once installed, you can search for a specific group name:
Then you can see group membership using the Members tab:
If you don’t want to use the AD browser packaged with RSA tools, there are several others available.
To find the AD Group members in the Instance, we can use below query:
By using this query, we can find the below states.
Instead you use the users and groups to grant/deny privileges, and let the engine enforce them appropiately. Attempting to roll your own security will get you nowhere fast. A banal example is when you will fail to honor the ‘one deny trumps all grants’ rule. And you will fail to navigate the intricacies of EXECUTE AS. Not to mention security based on module signatures.
For the record: users, roles and groups are exposed in the sys.database_principals catalog view. sys.fn_my_permissions will return the current context permissions on a specific securable.
The code that is provided on the Microsoft page here works for me, every time.
Check if a user is in a group
I have a server running where I use php to run a bash script to verify certain information of a user. For example, I have a webhosting server set up, and in order to be able to add another domain to their account I want to verify if the user is actually a member of the ‘customers’ group. What would be the best way to do this?
I have searched google, but all it comes up with is ways to check whether a user or a group exists, so google is not being a big help right now.
13 Answers 13
- id -nG $USER shows the group names a user belongs to.
- grep -qw $GROUP checks silently if $GROUP as a whole word is present in the input.
I know this is probably old thread but just in case this also works well:
if any number > 0 is returned then user is a member of that group.
A slightly more error-proof method to check for group membership using zero char delimited fixed string grep.
or using long opts
You could use groups $username_here | grep -q ‘\busergroup\b’
The exitcode will be 0 if a match was found, 1 if no match was found.
you could use this function as user_in_group userfoo groupbar
Using the zero delimiter to split by lines:
A while ago, I wrote a shell function to check if a user is a member of a group. To maximise portability, I wanted it be POSIX-compatible (while this question is tagged as bash , this function will still work). For performance, I wanted to use builtin shell features as much as possible: the only external command it uses is id , the POSIX-standardised utility for getting data about a user’s identity.
Example usage to test both positive and negative cases – and ensure it handles a non-existent username gracefully:
Running the above command prints the following output:
It hasn’t been tested for the case where a group or user has a space or other unusual characters in their name but some research shows that such names are not legal: the POSIX Base Definition for Group Name states that
To be portable across conforming systems, the value is composed of characters from the portable filename character set.
The Portable Filename Character Set is specified as the alphanumeric characters, A-Z, a-z, 0-9 along with the period, underscore, and hyphen-minus characters.
Check whether the user name is in the administrator group
In an InstallShield basic MSI project: how can I check whether a user name is in the administrator group?
(Not the current user with which I know it’s possible to do so.)
3 Answers 3
You could run «net localgroup administrators» and parse the output. I suspect there is a better way, but if not.
Users can belong to the ‘Administrators’ group on the local server or could be part of the ‘Domain Admins’ or ‘Enterprise Admins’ groups defined inside your AD. Ideal solution would be to create a DLL with a method called IsUserAdmin(user_name) that takes in a user name parameter and returns either true or false.
Internally, the method will call the IADsUser::Groups method to determine the groups the supplied user belongs to and will return true if the groups enumerated belongs to one of those administrator groups above. If not it will return false. You may invoke this DLL inside your InstallShield projects. Be wary of nested groups.
I can think of two approaches, however each would involve writing code over-and-above your install script, I’m not familiar with Installshield any more, but presumably just like Visual Studio setup projects you have the concept of custom actions. I suspect that’s what you’ll need.
I’ll only outline the first because the second is quite complex (i.e. even more complex than the first!). The obvious approach is AD. The following snippet of code will tell you whether a a username/password combination exists. Having obtained the user I’m sure you could work out what groups they’re in.
Now, there is a potential problem here if the account which runs this code does not have privileges to access AD. I won’t go into detail in this post because hopefully the code above will be enough to help you, but the basic principle of the alternative approach is to shell out directly to advapi32.dll to functions like LogonUser. (Bear in mind that again, my problem was validating credentials not checking for admin rights, but there’s probably a link there if you’re prepared to dig).
How to check if a user account is an Administrator in Windows 10
There is a Standard, Work & School, Child, Guest, and Administrator account feature in Windows 10 which is pretty good. You can easily create a new user account in Windows 10 and add other accounts anytime. But we need an administrator account to run things that need elevated privileges. In that case, we have to check which account is an administrator. This tutorial will help you easily check your administrator account in Windows 10 so that you can access it and use it.
How to check if you have Admin rights on Windows 10
We have covered four different and built-in ways to find out which account is an administrator account:
- Using Settings app
- Windows PowerShell
- Control Panel
- Local User and Groups.
Let’s check all these options.
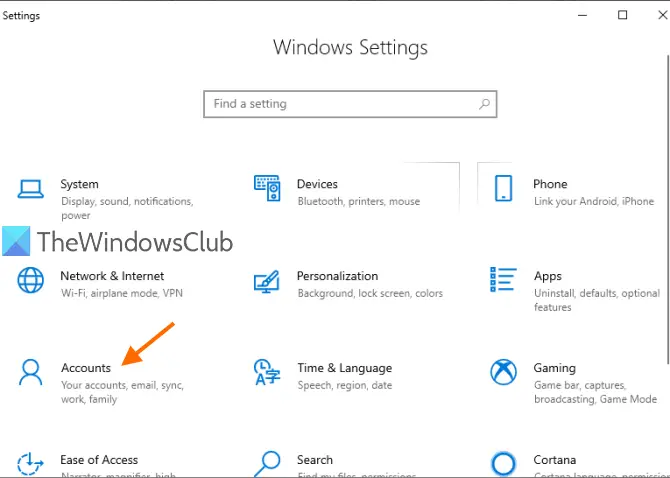
1] Using the Settings app
The modern Settings app of Windows 10 lets you access and use numerous options related to Personalization, Devices, System, Update & Security, Cortana, etc. You can also use this app to check if your user account is administrative or not.
For this, open Settings app of Windows 10. The quickest way to open this app is using the hotkey/shortcut key ‘Windows key + I’. After opening the app, click on the Accounts section.
Under Accounts section, you will see Your Info on the right part. There you can easily check if you’re logged in with an administrator account or not.
If the account is not an Administrator, you can log out from that account and log in with another account and repeat the same steps.
2] Using PowerShell
PowerShell is an easier way to find out administrator accounts including the built-in Administrator account of Windows 10. Just a simple command will provide the output.
First of all, open PowerShell using the Search box. Just type powershell and press the Enter key.
Or else, you can use Run Command box (Windows key + R), write powershell, and hit the Enter key.
When PowerShell window is opened, enter and execute the following command:
This will show the list of administrator accounts as highlighted in the image above.
3] Using Control Panel
Type control panel in the Search box and press Enter.
When Control Panel is opened, select User Accounts. After that, again click on the User Accounts option.
Now, on the right-hand part of the Control Panel window, you can see the information related to your account.
It will show if the account is standard or Administrator, local or Microsoft account, and password protected or not.
4] using Local Users and Groups
This option also shows a built-in Administrator account and other Administrator account created by you.
When the window is opened, click on the Groups folder. You will see the list of different accounts and members on the right part. Double-click on the Administrators option.
It will open the Administrators Properties window. There you will see all the administrators’ accounts under the Members section.
The next time whenever you have to check for an administrator account in your Windows 10 PC, hope these options will be helpful.
Related Posts
You must have Read permissions to view the properties of this object
You require permission from TrustedInstaller to make changes to this folder
How to remove deleted User Account from login screen in Windows 10
[email protected]
Laxman enjoys writing about Windows 10 OS and the free software and services that are available for the Windows ecosystem.