- How to Check for Ports in Use in Windows 10
- Use Nirsoft CurrPorts
- Command Prompt Method
- TCPView
- Use Netstat to See Listening Ports and PID in Windows
- What Is Netstat?
- Using Netstat To See Listening Ports & PID
- What’s Using That Port?
- How To Get Port, PID, & Process Name In PowerShell
- Go Get Them
- How to check if a port is blocked on a Windows machine?
- 4 Answers 4
- Command line for looking at specific port
- 14 Answers 14
How to Check for Ports in Use in Windows 10
At any one time, there’s a whole bunch of information being sent between your Windows 10 PC and the endless void of the Internet. This is done using a process whereby network-dependent processes seek out TCP and UDP ports, which they use to communicate with the Internet. First, your data gets sent to remote ports at the destination or website your processes are trying to connect to, then it gets received at local ports back on your PC.
Most of the time, Windows 10 knows how to manage ports and ensure that traffic is being directed through the right ports so that those processes can connect with what they need to. But sometimes two processes may be assigned to one port, or maybe you just want to get a better picture of your network traffic and what’s going in and out.
That’s why wrote this guide that shows you how to get an overview of your ports and see which applications are using which ports.
Use Nirsoft CurrPorts
NirSoft is one of the best indie software developers, giving us great utilities, like PassView and WirelessKeyView. While some people will prefer checking their ports without installing third-party software (in which case, scroll down to the CMD method), CurrPorts is easily the fastest and most convenient way to view your ports.
Once you’ve installed CurrPorts, just open it to see a list of all your ports currently in use. If you’re looking for local ports in use, just click the “Local Port” column at the top to order the list by port number (handy if you’re looking for a specific one). You can do the same thing with remote ports, too.
If you want to really find specific ports, click the “Advanced Filters” icon at the top and enter your string in the format they suggest. It should look something like the below image.
Hit OK when you’re ready, and the list will filter down to your queries.
Command Prompt Method
The integrated – though not necessarily the simplest – way to check open ports is to use the trusty command prompt.
Click the Start button, type cmd , then right-click “Command Prompt” when it shows up in the search results. Click “Run as administrator.”
Once you’re in the elevated command prompt, enter the following command:
This will steadily bring up a list of ports that is probably quite long, along with the Windows processes that are using them. (You can press Ctrl + A , then Ctrl + C to copy all information to the clipboard.) On the average PC, there will be two main local IP addresses that contain ports on your PC.
The first, in our case, is “127.0.0.1.” This IP address is otherwise known as “localhost” or a “loopback address,” and any process listening to ports here is communicating internally on your local network without using any network interface. The actual port is the number you see after the colon. (See image below.)
The bulk of your processes will probably be listening to ports prefixed with “192.168.xxx.xxx,” which is your IP address. This means the processes you see listed here are listening for communications from remote Internet locations (such as websites). Again, the port number is the number after the colon.
TCPView
If you don’t mind installing a third-party app and want to have more control over what’s going on with all your ports, you can use a lightweight app called TCPView. This immediately brings up a list of processes and their associated ports.
What make this better than the command prompt is that you can actively see the ports opening, closing and sending packets. Just look for the green, red and yellow highlights. You can also reorder the list by clicking the column headings, making it easier to find the process you want or two separate processes vying for the same port.
If you do find a process or connection you want to close, just right-click that process. You can then select “End process,” which is exactly the same function as the one in Windows task manager. Or you can click “Close Connection” to leave the process open but stop it from listening on a given port.
If you’re having some trouble in Windows 10, then see whether a Windows update may be causing it. We also have a handy guide for managing the health of your hard drive in Windows 10.
Related:
Content Manager at Make Tech Easier. Enjoys Android, Windows, and tinkering with retro console emulation to breaking point.
Use Netstat to See Listening Ports and PID in Windows
You never know when this will come in handy
In another article, we explained computer ports and what they’re used for. Other than that, what can we do with port information? Since all traffic in and out of the computer goes through ports, we can check on them to see what they’re doing. Maybe the port isn’t listening for traffic? Maybe something is using a port that shouldn’t be?
We’re going to use the Windows command netstat to see our listening ports and PID (Process ID). We’re also going to see what we can do with that information.
What Is Netstat?
The netstat command is a combination of the words ‘network’ and ‘statistics’. The netstat command works in all versions of Windows from Windows XP right up to Windows 10. It’s also used in other operating systems (OS) like Unix and Linux, but we’ll stick to Windows here.
Netstat can provide us with:
- The name of the protocol the port is using (TCP or UDP).
- The local IP address and name of the computer and the port number being used.
- The IP address and port number to which we’re connecting.
- The state of a TCP connection. For details on what these states are, read the Event Processing section of RFC 793.
Using Netstat To See Listening Ports & PID
- Use the key combination Win Key + X. In the menu that opens, select Command Prompt.
- Enter the command . The parameters for netstat are preceded with a hyphen, not a forward slash like many other commands. The -a tells it to show us all active connections and the ports on which the computer is listening.
The -n tells netstat to show the IP addresses and ports as numbers only. We’re telling it to not try to resolve the names. This makes for a quicker and neater display. The -o tells netstat to include the PID. We’ll use the PID later to find out what process is using a specific port.
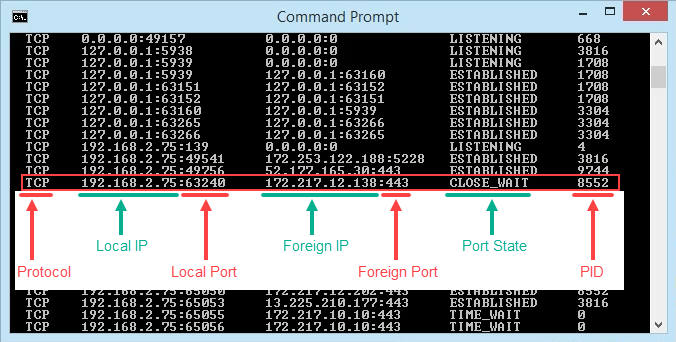
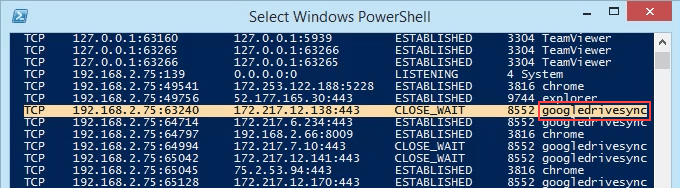
- View the results and take note of the addresses, port numbers, state, and PID. Let’s say we want to know what’s using port 63240. Note that its PID is 8552 and it’s connecting to the IP address 172.217.12.138 on port 443.
What’s Using That Port?
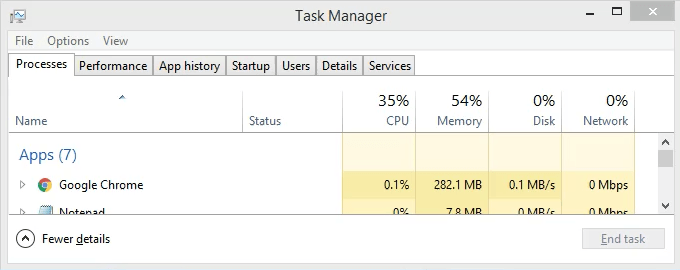
- Open Task Manager. That’s most easily done by using the key combination Ctrl + Shift + Esc.
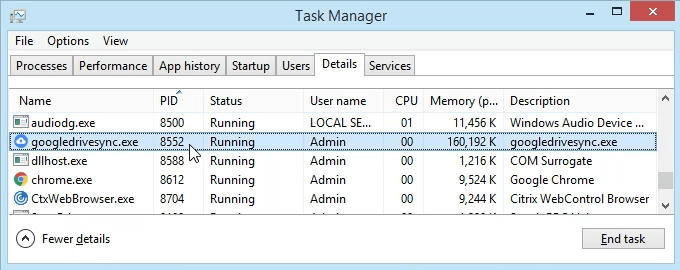
- Click on the Details tab. To make this easier to find, click on the PID column header to sort the PIDs numerically.
- Scroll down to PID 8552 and see what process it is. In this case, it’s googledrivesync.exe. But is it really? Sometimes viruses can make themselves look like legitimate processes.
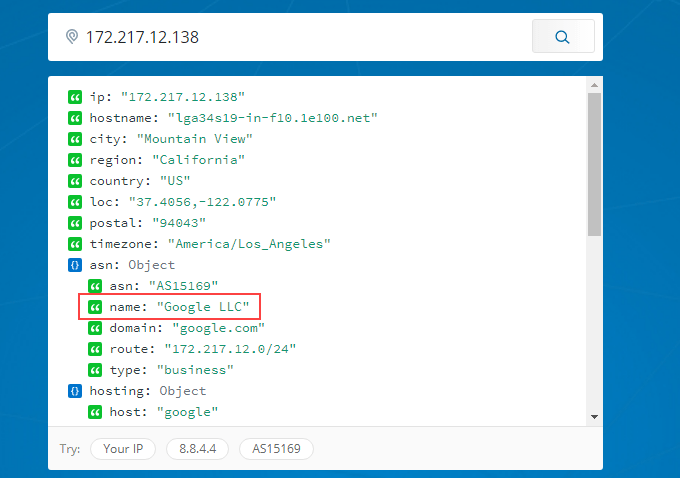
- In a web browser, go to ipinfo.io. Enter the IP address 172.217.12.138. As we can see, the IP address is registered to Google. So this googledrivesync.exe is a legitimate one.
How To Get Port, PID, & Process Name In PowerShell
PowerShell is Microsoft’s newer way to use a command-line interface with Windows. We say newer, but it’s been around for several versions. You should learn PowerShell even if you’re a home user.
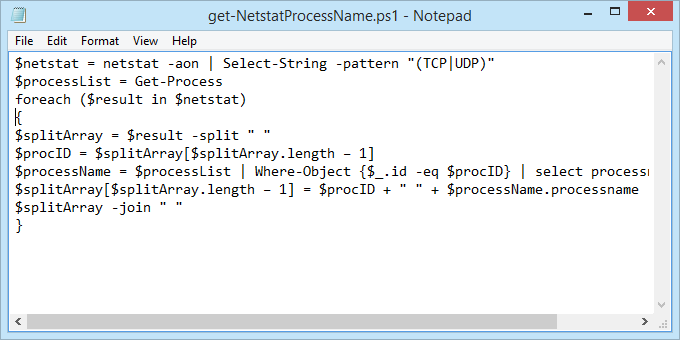
Most Windows commands also work in PowerShell, plus we can combine them with PowerShell’s cmdlets – pronounced command-lets. Joe at Winteltools.com provides the script for this method.
- Open Notepad and enter the following code:
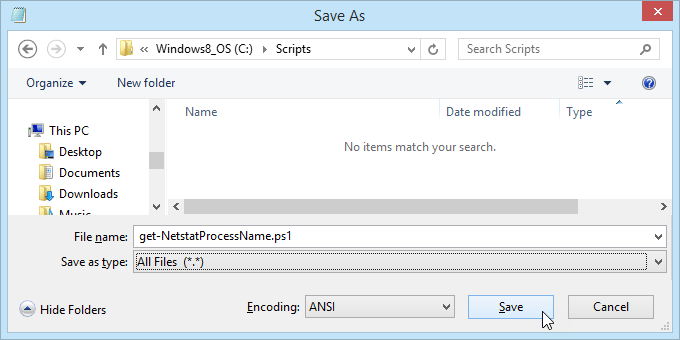
- Save the file as get-NetstatProcessName.ps1. Make sure to note where it’s being saved. It’s important to change the Save as type: to All Files (*.*) or it will get saved as get-NetstatProcessName.ps1.txt and it won’t work for us.
- Open PowerShell and navigate to the location in which the script was saved. In this case, it’s . Hit Enter to run the command.
- Run the script using dot-sourcing to make it work. That means use ./ before the name of the file. The command will be
- Now we can see all the traditional netstat info plus the process name. No need to open Task Manager anymore.
Go Get Them
We’ve covered two ways to use the netstat command to see listening ports. It can be used either in the old Command Prompt or within a PowerShell script. With the information it can give us, we’ve looked at how it can help us figure out what our computer is doing.
If you thought netstat is a great utility, take a look at some other Windows TCP/IP utilities like tracert, ipconfig, and nslookup. Or use Resource Monitor to get a better look into hidden website and Internet connections. There is a lot you can do to see exactly what your computer is doing.
Have you used netstat to solve a problem? Please tell us what you did. Any questions about how to use netstat? Please ask us in the comments below.
Guy has been published online and in print newspapers, nominated for writing awards, and cited in scholarly papers due to his ability to speak tech to anyone, but still prefers analog watches. Read Guy’s Full Bio
How to check if a port is blocked on a Windows machine?
On the Windows platform, what native options to I have to check if a port (3306, for example) on my local machine (as in localhost ), is being blocked?
4 Answers 4
Since you are on a Windows machine, these things can be done:
Execute the following command and look for a «:3306» listener (you did not mention UDP/TCP). This will confirm there is something running on the port.
After this, if you are expecting incoming connections on this port and feel that the firewall may be blocking them, you could use start windows firewall logging and check the logs for dropped connections
- Go to Windows Firewall, Advanced settings
- Click on the Settings button next to «Local Area Connection»
- Select «Log dropped packets»
- Look at the log file location (if not present, define one)
- Click OK
- Now, when the connection attempt is made (assuming you know when this is done), look at the log file for a drop on port 3306.
- If this is seen, you will want to add an exception for this port.
There is one more command to check the firewall state
(Updated for Windows 7 users — as referred by Nick below — use netsh advfirewall firewall)
netsh firewall show state
- this will list the blocked ports as well as active listening ports with application associations
This command will dump the Windows firewall configuration detail
netsh firewall show config
If you have an active block (incoming connections are being dropped by firewall) after you start logging, you should see that in the log.
If you are running an application/service that is listening on 3306, the firewall config should show it to be Enabled. If this is not seen, you have probably missed adding an exception with the firewall to allow this app/service.
Finally, port 3306 is typically used for MySQL. So, I presume you are running MySQL server on this windows machine. You should therefore see a listener for 3306 accepting incoming connections. If you do not see that, you need to work with your application (MySQL) to get that started first.
Command line for looking at specific port
Is there a way to examine the status of a specific port from the Windows command line? I know I can use netstat to examine all ports but netstat is slow and looking at a specific port probably isn’t.
14 Answers 14
Here is the easy solution of port finding.
You can use the netstat combined with the -np flags and a pipe to the find or findstr commands.
Basic Usage is as such:
So for example to check port 80 on TCP, you can do this: netstat -np TCP | find «80» Which ends up giving the following kind of output:
As you can see, this only shows the connections on port 80 for the TCP protocol.
here o represents process ID. now you can do whatever with the process ID. To terminate the process, for e.g., use:
when I have problem with WAMP apache , I use this code for find which program is using port 80.
3068 is PID, so I can find it from task manager and stop that process.
As noted elsewhere: use netstat, with appropriate switches, and then filter the results with find[str]
To find a foreign port you could use:
To find a local port you might use:
Where N is the port number you are interested in.
-n ensures all ports will be numerical, i.e. not returned as translated to service names.
-a will ensure you search all connections (TCP, UDP, listening. )
In the find string you must include the colon, as the port qualifier, otherwise the number may match either local or foreign addresses.
You can further narrow narrow the search using other netstat switches as necessary.
Further reading (^0^)
it will give you number of sockets active on a specific IP and port(Server port number)
For Windows 8 User : Open Command Prompt, type netstat -an | find «your port number» , enter .
If reply comes like LISTENING then the port is in use, else it is free .
To find a foreign port (IPv4 or IPv6) you can use:
To find a local port (IPv4 or IPv6) you can use:
Where N is the port number you are interested in. The «/r» switch tells it to process it as regexp. The «/c» switch allows findstr to include spaces within search strings instead of treating a space as a search string delimiter. This added space prevents longer ports being mistreated — for example, «:80» vs «:8080» and other port munging issues.
To list remote connections to the local RDP server, for example:
Or to see who is touching your DNS:
If you want to exclude local-only ports you can use a series of exceptions with «/v» and escape characters with a backslash: