- Enabling debug logging for the Netlogon service
- More information
- For Windows Server 2019, Windows Server 2016, Windows Server 2012 R2
- Alternative methods to enable Netlogon logging
- Turn on debug logging in the Windows Time Service
- Turn on debug logging for Windows Time Service
- How to get rid of auto-generated debug.log file in Windows 10
- What is the debug.log file and is it harmful?
- How do I get rid of the debug file?
- What is The file «Debug.log»
- Replies (6)
Enabling debug logging for the Netlogon service
This article describes the steps to enable logging of the Netlogon service in Windows to monitor or troubleshoot authentication, DC locator, account lockout, or other domain communication-related issues.
Original product version: В Windows 10 — all editions, Windows Server 2016, Windows Server 2019, Windows Server 2012 R2
Original KB number: В 109626
More information
This section, method, or task contains steps that tell you how to modify the registry. However, serious problems might occur if you modify the registry incorrectly. Therefore, make sure that you follow these steps carefully. For added protection, back up the registry before you modify it. Then, you can restore the registry if a problem occurs. For more information about how to back up and restore the registry, click the following article number to view the article in the Microsoft Knowledge Base:
322756 How to back up and restore the registry in Windows
The version of Netlogon.dll that has tracing included is installed by default on all currently supported versions of Windows. To enable debug logging, set the debug flag that you want by using Nltest.exe, the registry, or Group Policy. To do it, follow these steps:
For Windows Server 2019, Windows Server 2016, Windows Server 2012 R2
These steps also apply to Windows 10.
To enable Netlogon logging:
Open a Command Prompt window (administrative Command Prompt window for Windows Server 2012 R2 and later versions).
Type the following command, and then press Enter:
It’s typically unnecessary to stop and restart the Netlogon service for Windows Server 2012 R2 or later to enable Netlogon logging. Netlogon-related activity is logged to %windir%\debug\netlogon.log. Verify new writes to this log to determine whether a restart of the Netlogon service is necessary. If you have to restart the service, open a Command Prompt window (administrative Command Prompt window for Windows 10, and Windows Server 2012 R2 and later versions). Then run the following commands:
- In some circumstances, you may have to perform an authentication against the system in order to obtain a new entry in the log to verify that logging is enabled.
- Using the computer name may cause no new test authentication entry to be logged.
To disable Netlogon logging, follow these steps:
Open a Command Prompt window (administrative Command Prompt window for Windows Server 2012 R2 and higher).
Type the following command, and then press Enter:
It’s typically unnecessary to stop and restart the Netlogon service for Windows Server 2012 R2 or later versions to disable Netlogon logging. Netlogon-related activity is logged to %windir%\debug\netlogon.log. Verify that no new information is being written to this log to determine whether a restart of the Netlogon service is necessary. If you have to restart the service, open a Command Prompt window (administrative Command Prompt window for Windows 10, and Windows Server 2012 R2 and later versions). Then run the following commands:
Alternative methods to enable Netlogon logging
In all versions of Windows, you can use the registry method that’s provided in the Enable/Disable logging by using registry method section.
On computers that are running Windows Server 2012 R2 and later versions of the operating system, you can also use the following policy setting to enable verbose Netlogon logging (value is set in bytes):
\Computer Configuration\Administrative Templates\System\Net Logon\Specify log file debug output level
A value of decimal 545325055 is equivalent to 0x2080FFFF (which enables verbose Netlogon logging). This Group Policy setting is specified in bytes.
The Group Policy method can be used to enable Netlogon logging on a larger number of systems more efficiently. We don’t recommend that you enable Netlogon logging in policies that apply to all systems, such as the Default Domain Policy. Instead, consider narrowing the scope to systems that may be causing problems by using one of the following methods:
- Create a new policy by using this Group Policy setting, and then provide the Read and Apply Group Policy rights to a group that contains only the required computer accounts.
- Move computer objects into a different OU, and then apply the policy settings at that OU level.
Enable/Disable logging by using registry method
To enable logging, you may have to obtain a checked build of Netlogon.dll.
Start Registry Editor.
If it exists, delete the Reg_SZ value of the following registry entry, create a REG_DWORD value with the same name, and then add the 2080FFFF hexadecimal value:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Netlogon\Parameters\DBFlag
It’s typically unnecessary to stop and restart the Netlogon service for Windows Server 2012 R2 and later versions to enable Netlogon logging. Netlogon-related activity is logged to %windir%\debug\netlogon.log. Verify the new writes to this log to determine whether a restart of the Netlogon service is necessary. If you have to restart the service, open a Command Prompt window (administrative Command Prompt window for Windows Server 2012 R2/Windows 10 and above). Then run the following commands:
- In some circumstances, you may have to do an authentication against the system to obtain a new entry in the log to verify that logging is enabled.
- Using the computer name may cause no new test authentication entry to be logged.
To disable Netlogon logging, follow these steps:
In Registry Editor, change the data value to 0x0 in the following registry key:
Exit Registry Editor.
It’s typically unnecessary to stop and restart the Netlogon service for Windows Server 2012 R2, Windows 10, or later versions to disable Netlogon logging. Netlogon-related activity is logged to %windir%\debug\netlogon.log. Verify that no new information is being written to this log to determine whether a restart of the Netlogon service is necessary. If you have to restart the service, open a Command Prompt window (administrative Command Prompt window for Windows Server 2012 R2/Windows 10 and later versions of the operating system). Then run the following commands:
Set the maximum log file size for Netlogon logs:
The MaximumLogFileSize registry entry can be used to specify the maximum size of the Netlogon.log file. By default, this registry entry doesn’t exist, and the default maximum size of the Netlogon.log file is 20 MB. When the file reaches 20 MB, it’s renamed to Netlogon.bak, and a new Netlogon.log file is created. This registry entry has the following parameters:
- Path: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Netlogon\Parameters
- Value Name: MaximumLogFileSize
- Value Type: REG_DWORD
- Value Data:
Remember that the total disk space that’s used by Netlogon logging is the size that’s specified in the maximum log file size times two (2). It’s required to accommodate space for the Netlogon.log and Netlogon.bak file. For example, a setting of 50 MB can require 100 MB of disk space, which provides 50 MB for Netlogon.log and 50 MB for Netlogon.bak.
As mentioned earlier, on Windows Server 2012 R2 and later versions of the operating system, you can use the following policy setting to configure the log file size (value is set in bytes):
\Computer Configuration\Administrative Templates\System\Net Logon\Maximum Log File Size
For more information, click the following article numbers to view the articles in the Microsoft Knowledge Base:
247811 How domain controllers are located in Windows
Turn on debug logging in the Windows Time Service
This article describes how to turn on debug logging for the Windows Time service (also known as W32time). If you are an administrator, you can use the debug logging feature of the Windows Time service to help troubleshoot issues.
Original product version:  Windows Server 2019, Windows Server 2016, Windows Server 2012 R2, Window 10 – all editions, Windows 7 Service Pack 1
Original KB number: В 816043
Microsoft recommends that you use debug logging after you have performed all other troubleshooting steps. Because of the nature of the detailed information in the debug log, you may have to contact a Microsoft Support Professional.
Turn on debug logging for Windows Time Service
This section, method, or task contains steps that tell you how to modify the registry. However, serious problems might occur if you modify the registry incorrectly. Therefore, make sure that you follow these steps carefully. For added protection, back up the registry before you modify it. Then, you can restore the registry if a problem occurs. For more information about how to back up and restore the registry, see How to back up and restore the registry in Windows.
To turn on debug logging in the Windows Time service:
Start Registry Editor.
Locate and then click the registry key: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\W32Time\Config .
On the Edit menu, click New Value, and then add the following registry values:
- Value Name: FileLogSize
- Data Type: DWORD
- Value data: 10000000
This registry value specifies the size of the log file in bytes. A value of 10000000 bytes will limit the log file to approximately 10 MB.
- Value name: FileLogName
- Data Type: String
- Value data: C:\Windows\Temp\w32time.log
This registry value specifies the location of the log file. The path is not fixed. You can use a different path.
- Value name: FileLogEntries
- Data Type: String
- Value: 0-116
This registry value specifies the level of detail of the information in the debug log. If you must have more detailed logging information, contact a Microsoft Support Professional.
The Data Type value must be of type REG_SZ (String). You must type the value exactly as shown (that is, type 0-116 ). The highest possible value is 0-300 for most detailed logging. The meaning of this value is: Log all entries within the range of 0 and 116.
How to get rid of auto-generated debug.log file in Windows 10
- Many users noticed recently a debug.log file on their desktops containing error keywords.
- This type of file is generated every once in a while and is a bug that can be removed.
- Whenever you’re in doubt about certain software errors, you’ll surely find the right answers in our Troubleshooting Hub.
- Visit our large collection of articles on Browsers, to find everything there’s to know on this topic.
With certain updates, Chromium-based browsers such as Chrome, Edge, Opera, Vivaldi randomly generate a debug.log file that lands on the users’ desktops, generating confusion.
The same happened last week, with the latest Google Chrome update. Shortly afterward, questions started to pop up on forums asking for clarifications regarding a debug Notepad file containing some errors codes and the following text:
FindFirstFile: The system cannot find the path specified. (0x3)
As noticed by many, they could delete the file, but it would reappear on their desktop each time their device connected to the Internet or each time they opened certain files or apps in their browsers.
What is the debug.log file and is it harmful?
The file is generated by Chromium 68x based browsers (as mentioned above) and it doesn’t point out toward a system issue.
Initially, it was advised on Microsoft’s forums to delete the file, as it didn’t pose any security threat.
Actually, upon a system scan with a third-party antivirus, no malware can be found (at least not one related to the file in question).
However, the file would be re-generated on the desktop, only containing another error code.
How do I get rid of the debug file?
It seems there is only one fix for these situations, as suggested by a moderator of the Microsoft community.
Namely, users noticing the file have to delete a Crashpad folder contained in their browser folder.
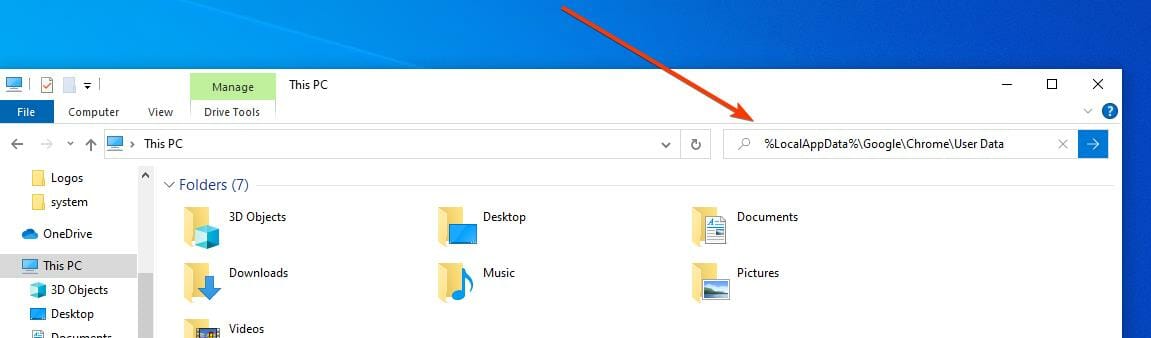
- Open File Explorer.
- In the search bar, paste the following: %LocalAppData%\Google\Chrome\User Data
- Note: Replace Chrome with the browser generating the debug.log file.
- You should see a Crashpad folder that you have to delete.
Many users mentioned that this solution helped them.
On the other hand, the developers team at Chromium has taken notice of the issue and opened a bug tracker and they are likely to release a fix soon..
What is The file «Debug.log»
unknown Notepad file icon is on my disk top «Debug»
02-17-2018 12:14:49.2094 GetHDSerialProcessor driveNumber 0
02-17-2018 12:14:49.6594 GetHDSerialProcessor result xxxxxxxxx
02-17-2018 12:14:49.7524 GetHDSerialProcessor driveNumber 0
02-17-2018 12:14:50.0024 GetHDSerialProcessor result xxxxxxxxx
02-17-2018 12:14:50.7925 GetHDSerialProcessor driveNumber 0
02-17-2018 12:14:51.0225 GetHDSerialProcessor result xxxxxxxxx
02-17-2018 12:14:52.2320 GetHDSerialProcessor driveNumber 0
02-17-2018 12:14:52.5022 GetHDSerialProcessor result xxxxxxxxx
02-17-2018 12:35:14.9307 GetHDSerialProcessor driveNumber 0
02-17-2018 12:35:15.2426 GetHDSerialProcessor result xxxxxxxxx
02-17-2018 12:35:15.4124 GetHDSerialProcessor driveNumber 0
02-17-2018 12:35:15.6632 GetHDSerialProcessor result xxxxxxxxx
I replaced the numbers with xxxxxxxxx
Replies (6)
The Debug.log file can record database operations, system processes, and errors that occur when executing a transaction or running unit tests. To help us identify the cause why this files suddenly appeared on your desktop, we would need to know the following information:
- Which build, version and edition of Windows is installed on your computer?
- What changes were made to the device before this file appeared?
- Is your device connected to a domain network?
- Is your device being managed by a Windows Server?
We are looking forward to your response.
18 people found this reply helpful
Was this reply helpful?
Sorry this didn’t help.
Great! Thanks for your feedback.
How satisfied are you with this reply?
Thanks for your feedback, it helps us improve the site.
How satisfied are you with this reply?
Thanks for your feedback.
I just reinstalled my Windows 10 Home OS on a new hard drive as I was having major issues. Now, I am methodically setting up my system again.
I, too, just noted a Debug .txt file on my desktop after the reinstall and all of the updates completed. I am on my own home network which has a printer and three other computers linked together over Ethernet and Wifi. My log file reads:
03-10-2018 08:21:53.1551 GetHDSerialProcessor driveNumber 0
03-10-2018 08:21:53.2958 GetHDSerialProcessor result W761Y3ZP
03-10-2018 08:21:53.4051 GetHDSerialProcessor driveNumber 0
03-10-2018 08:21:53.5302 GetHDSerialProcessor result W761Y3ZP
03-10-2018 08:21:53.9677 GetHDSerialProcessor driveNumber 0
03-10-2018 08:21:54.1083 GetHDSerialProcessor result W761Y3ZP
03-10-2018 08:21:55.3909 GetHDSerialProcessor driveNumber 0
03-10-2018 08:21:55.5709 GetHDSerialProcessor result W761Y3ZP
03-10-2018 08:27:52.4231 GetHDSerialProcessor driveNumber 0
03-10-2018 08:27:52.5638 GetHDSerialProcessor result W761Y3ZP
03-10-2018 08:27:53.1732 GetHDSerialProcessor driveNumber 0
03-10-2018 08:27:53.3451 GetHDSerialProcessor result W761Y3ZP
03-10-2018 08:27:53.5169 GetHDSerialProcessor driveNumber 0
03-10-2018 08:27:53.6732 GetHDSerialProcessor result W761Y3ZP
03-10-2018 08:27:55.0508 GetHDSerialProcessor driveNumber 0
03-10-2018 08:27:55.1908 GetHDSerialProcessor result W761Y3ZP
03-10-2018 08:34:15.1717 GetHDSerialProcessor driveNumber 0
03-10-2018 08:34:15.3378 GetHDSerialProcessor result W761Y3ZP
03-10-2018 08:34:15.4396 GetHDSerialProcessor driveNumber 0
03-10-2018 08:34:15.5797 GetHDSerialProcessor result W761Y3ZP