- Collect Windows event log data sources with Log Analytics agent
- Configuring Windows Event logs
- Data collection
- Windows event records properties
- Log queries with Windows Events
- Consuming Events (Windows Event Log)
- XPath 1.0 limitations
- WMI Tasks: Event Logs
- Windows Event Logs — Event Log FAQ
- What is Windows event log?
- How to view event logs?
- What is Windows Event Log Service?
- What are Windows event log files?
- What is Windows Application event log?
- What is Windows System event log?
Collect Windows event log data sources with Log Analytics agent
Windows Event logs are one of the most common data sources for Log Analytics agents on Windows virtual machines since many applications write to the Windows event log. You can collect events from standard logs such as System and Application in addition to specifying any custom logs created by applications you need to monitor.
This article covers collecting Windows events with the Log Analytics agent which is one of the agents used by Azure Monitor. Other agents collect different data and are configured differently. See Overview of Azure Monitor agents for a list of the available agents and the data they can collect.
Configuring Windows Event logs
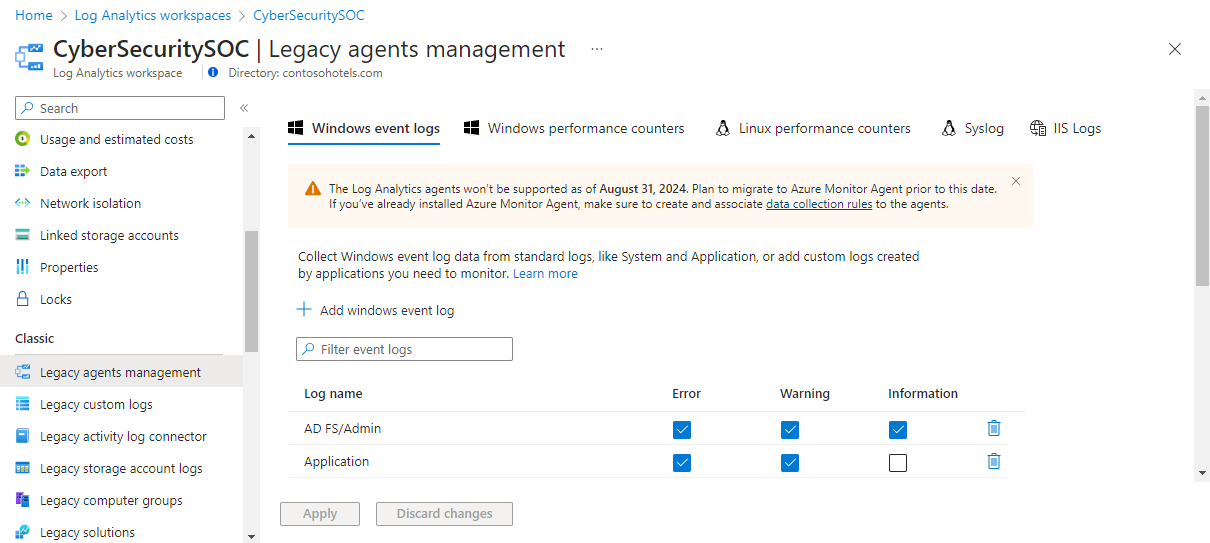
Configure Windows Event logs from the Agents configuration menu for the Log Analytics workspace.
Azure Monitor only collects events from the Windows event logs that are specified in the settings. You can add an event log by typing in the name of the log and clicking +. For each log, only the events with the selected severities are collected. Check the severities for the particular log that you want to collect. You cannot provide any additional criteria to filter events.
As you type the name of an event log, Azure Monitor provides suggestions of common event log names. If the log you want to add does not appear in the list, you can still add it by typing in the full name of the log. You can find the full name of the log by using event viewer. In event viewer, open the Properties page for the log and copy the string from the Full Name field.
You can’t configure collection of security events from the workspace. You must used Azure Security Center or Azure Sentinel to collect security events.
Critical events from the Windows event log will have a severity of «Error» in Azure Monitor Logs.
Data collection
Azure Monitor collects each event that matches a selected severity from a monitored event log as the event is created. The agent records its place in each event log that it collects from. If the agent goes offline for a period of time, then it collects events from where it last left off, even if those events were created while the agent was offline. There is a potential for these events to not be collected if the event log wraps with uncollected events being overwritten while the agent is offline.
Azure Monitor does not collect audit events created by SQL Server from source MSSQLSERVER with event ID 18453 that contains keywords — Classic or Audit Success and keyword 0xa0000000000000.
Windows event records properties
Windows event records have a type of Event and have the properties in the following table:
| Property | Description |
|---|---|
| Computer | Name of the computer that the event was collected from. |
| EventCategory | Category of the event. |
| EventData | All event data in raw format. |
| EventID | Number of the event. |
| EventLevel | Severity of the event in numeric form. |
| EventLevelName | Severity of the event in text form. |
| EventLog | Name of the event log that the event was collected from. |
| ParameterXml | Event parameter values in XML format. |
| ManagementGroupName | Name of the management group for System Center Operations Manager agents. For other agents, this value is AOI- |
| RenderedDescription | Event description with parameter values |
| Source | Source of the event. |
| SourceSystem | Type of agent the event was collected from. OpsManager – Windows agent, either direct connect or Operations Manager managed Linux – All Linux agents AzureStorage – Azure Diagnostics |
| TimeGenerated | Date and time the event was created in Windows. |
| UserName | User name of the account that logged the event. |
Log queries with Windows Events
The following table provides different examples of log queries that retrieve Windows Event records.
Consuming Events (Windows Event Log)
You can consume events from channels or from log files. To consume events, you can consume all events or you can specify an XPath expression that identifies the events that you want to consume. To determine the elements and attributes of an event that you can use in your XPath expression, see Event Schema.
Windows Event Log supports a subset of XPath 1.0. For details on the limitations, see XPath 1.0 limitations.
The following examples show simple XPath expressions.
You can use the XPath expressions directly when calling the EvtQuery or EvtSubscribe functions or you can use a structured XML query that contains the XPath expression. For simple queries that query events from a single source, using an XPath expression is fine. If the XPath expression is a compound expression that contains more than 20 expressions or you are querying for events from multiple sources, then you must use a structured XML query. For details on the elements of a structured XML query, see Query Schema.
A structured query identifies the source of the events and one or more selectors or suppressors. A selector contains an XPath expressions that selects events from the source and a suppressor contains an XPath expression that prevents events from being selected. You can select events from more than one source. If a selector and suppressor identify the same event, the event is not included in the result.
The following shows a structured XML query that specifies a set of selectors and suppressors.
The result set from the query does not contain a snapshot of the events at the time of the query. Instead, the result set includes the events at the time of the query and will also contain all new events that are raised that match the query criteria while you are enumerating the results.
The order of the events is preserved for events that are written by the same thread. However, it is possible for events written by separate threads on different processors of a multiple processor computer to appear out of order.
For details on consuming events, see the following topics:
The standard end user tools for consuming event are:
XPath 1.0 limitations
Windows Event Log supports a subset of XPath 1.0. The primary restriction is that only XML elements that represent events can be selected by an event selector. An XPath query that does not select an event is not valid. All valid selector paths start with * or «Event». All location paths operate on the event nodes and are composed of a series of steps. Each step is a structure of three parts: the axis, node test, and predicate. For more information about these parts and about XPath 1.0, see XML Path Language (XPath). Windows Event Log places the following restrictions on the expression:
- Axis: Only the Child (default) and Attribute (and its shorthand «@») axis are supported.
- Node Tests: Only node names and NCName tests are supported. The «*» character, which selects any character, is supported.
- Predicates: Any valid XPath expression is acceptable if the location paths conform to the following restrictions:
- Standard operators OR, AND, =, !=, =, >, and parentheses are supported.
- Generating a string value for a node name is not supported.
- Evaluation in reverse order is not supported.
- Node sets are not supported.
- Namespace scoping is not supported.
- Namespace, processing, and comment nodes are not supported.
- Context size is not supported.
- Variable bindings are not supported.
- The position function, and its shorthand array reference, is supported (on leaf nodes only).
- The Band function is supported. The function performs a bitwise AND for two integer number arguments. If the result of the bitwise AND is nonzero, the function evaluates to true; otherwise, the function evaluates to false.
- The timediff function is supported. The function computes the difference between the second argument and the first argument. One of the arguments must be a literal number. The arguments must use FILETIME representation. The result is the number of milliseconds between the two times. The result is positive if the second argument represents a later time; otherwise, it is negative. When the second argument is not provided, the current system time is used.
WMI Tasks: Event Logs
WMI tasks for event logs obtain event data from event log files and perform operations like backing up or clearing log files. For other examples, see the TechNet ScriptCenter at https://www.microsoft.com/technet.
The script examples shown in this topic obtain data only from the local computer. For more information about how to use the script to obtain data from remote computers, see Connecting to WMI on a Remote Computer.
The following procedure describes how to run a script.
To run a script
- Copy the code and save it in a file with a .vbs extension, such as filename.vbs. Ensure that your text editor does not add a .txt extension to the file.
- Open a command prompt window and navigate to the directory where you saved the file.
- Type cscript filename.vbs at the command prompt.
- If you cannot access an event log, check to see if you are running from an Elevated command prompt. Some Event Log, such as the Security Event Log, may be protected by User Access Controls (UAC).
By default, cscript displays the output of a script in the command prompt window. Because WMI scripts can produce large amounts of output, you might want to redirect the output to a file. Type cscript filename.vbs > outfile.txt at the command prompt to redirect the output of the filename.vbs script to outfile.txt.
The following table lists script examples that can be used to obtain various types of data from the local computer.
| How do I. | WMI classes or methods | ||
|---|---|---|---|
| . retrieve information about the Security event log? | Include the Security privilege when connecting to the Win32_NTEventlogFile class. For more information, see Executing Privileged Operations Using VBScript.
| ||
| . back up an event log? | |||
| . back up an event log more than once? | Ensure that the backup file has a unique name before using the Win32_NTEventlogFile and the BackupEventLog method. The operating system does not allow you to overwrite an existing backup file; you must either move the backup file or rename it before you can run the script again. You may need to include the Backup privilege when connecting to WMI. For more information, see Executing Privileged Operations Using VBScript. | ||
| . determine the number of records in an event log? | Use the Win32_NTEventlogFile class and check the value of the NumberOfRecords property. Windows Event Logs — Event Log FAQWhat is Windows event log?Event logs are special files that record significant events on your computer, such as when a user logs on to the computer or when a program encounters an error. Whenever these types of events occur, Windows records the event in an event log. Users might find the details in event logs helpful when troubleshooting problems with Windows and other programs. Unlike UNIX syslog, Microsoft event log is not a text file and it is impossible to view it with simple text editors. Microsoft Windows event log is a binary file that consists of special records – Windows events. Microsoft Windows runs Event Log Service to manage event logs, configure event publishing, and perform operations on the logs. Windows Event Log service exposes a special API, which allows applications to maintain and manage event logs. Windows event logging was introduced in Windows NT operating system (version 3.1) in 1993. This Windows edition came with three Windows logs: Application event log, System event log and Security event log. Modern versions of Windows come with more than a hundred of Windows eventlogs, and third party applications can create and integrate into Windows logging their own event logs. How to view event logs?You can view eventlogs using Event Viewer (comes with Windows operating system) or third-party Windows event viewers. We recommend using our Event Log Explorer software – it provides a lot of advanced features for event log management. What is Windows Event Log Service?Windows Event Log Service is a Windows service that manages events and event logs. It supports logging events, querying events, subscribing to events, archiving event logs, and managing event metadata. It helps to display events in both XML and plain text format. This service is enabled and starts automatically by default. You should not stop or disable this service. Stopping Windows Event Log service may compromise security and reliability of the system. What are Windows event log files?Windows Event Log Service lets users to save (backup) event logs to files. Windows NT, 2000 and XP/2003 save event logs to EVT format. Windows Vista/2008 and better save logs to EVTX format. Having backup event files are essential for incident investigation. Windows event logs are also files, but they are commonly locked by Windows (Event Log Service) and it is impossible to open these files on «live» system. But if the computer is started from another disk or the system drive from the analyzed machine is connected to another computer, you can read event logs as files. The default location of event logs on Vista/2008 and better is «C:\Windows\System32\winevt\Logs\». Windows Event Viewer allows you to open event file as follows: Click Open Saved Log in Actions pane of Event Viewer. Select your event log file and it will appear in Windows Event Viewer as a log. Our Event Log Explorer software also works with event files and does it even better than Event Viewer, e.g. it lets you read even damaged event files. What is Windows Application event log?The Application log contains events logged by applications or programs. For example, a database program might record a file error in the application log. Program developers decide which events should be logged. E.g. Microsoft SQL Server logs details about important events linked with SQL server, e.g. «out of memory», «backup failure» etc. One application log commonly contains events logged from different sources (applications), so it is incorrect to rely solely on event ID when analyzing the Application log. You should always rely on event ID along with event source. Some applications, such as Internet Explorer, Power Shell create own event log instead of using Windows application event log. Such logs look exactly like standard Windows event logs and Event Viewer (as well as Event Log Explorer) can read these event logs. Application logs are commonly useful for application support teams. What is Windows System event log?The System log contains events logged by Windows system components. For example, the failure of a driver or other system component to load during startup is recorded in the system log. The event types logged by system components are predetermined by Windows. Similarly to Application log, System event log lists events from different sources (system components) so you should not rely only on event ID when analyzing System log, instead you should rely on event ID along with event source. System logs are essential for system administrators and technicians. |