- Event Logging (Windows Installer)
- How To Know Who Logged Into Windows 10?
- How To Know If Someone Logged Into Your Windows 10?
- How To See Who Logged Into Windows 10 Using Event Viewer
- How To Set A Custom Filter In Event Viewer
- Video Showing How To See Who Logged Into Your Windows 10:
- Where Are The Windows Logs Stored?
- Accessing The Event Viewer
- Using The Event Viewer
- Log Categories
- Get Started Today!
- How to get Security Log with non-administrative user
- SHOWTIME
- Manage auditing and security log
- Get-WinEvent VS Get-EventLog
- Non-administrator access to DC Event logs
Event Logging (Windows Installer)
Windows Events provides a standard, centralized way for applications (and the operating system) to record important software and hardware events. The event-logging service stores events from various sources in a single collection called an event log. Prior to WindowsВ Vista, you would use either Event Tracing for Windows (ETW) or Event Logging to log events. WindowsВ Vista introduced a new eventing model that unifies both ETW and the Windows Event Log API.
The installer also writes entries into the event log. These record events such as following:
- Success or failure of the installation; removal or repair of a product.
- Errors that occur during product configuration.
- Detection of corrupted configuration data.
If a large amount of information is written, the Event Log file can become full and the installer displays the message, «The Application log file is full.»
The installer may write the following entries in the event log. All event log messages have a unique event ID. All general errors authored in the Error table that are returned for an installation that fails are logged in the Application Event Log with a message ID equal to the Error + 10,000. For example, the error number in the Error table for an installation completed successfully is 1707. The successful installation is logged in the Application Event Log with a message ID of 11707 (1707 + 10,000).
For information about how to enable verbose logging on a user’s computer when troubleshooting deployment, see Windows Installer Best Practices.
How To Know Who Logged Into Windows 10?
How To Know If Someone Logged Into Your Windows 10?
Windows 10 enables you to see which users are logged into your PC using Event Viewer (and when they logged in). Event viewer is a component of Microsoft Windows that enables administrators and regular users to view event logs on a local or remote machine. It uses event IDs to define uniquely-identifiable events that a Windows computer might encounter. Event Viewer displays a log of application and system information messages, including warnings and errors (these are displayed even if your system is running correctly).
This feature is helpful if you are troubleshooting a specific problem and require more information about the cause. You can look for events in different categories such as «Application», «System» and «Security». In the Application event log, you can find events relating to Windows system components such as drivers and built-in interface elements. The System event log provides event logs relating to programs installed on your Windows operating system. The Security event log also provides events relating to security such as login attempts and resource access. In this article, we discuss the Security category in more detail, since it enables you to see who and when users logged into your computer.
NOTE: If you are running Windows 10 Home, you will only be able to see successful login attempts (this log is enabled by default in this edition). To enable full login auditing, you must use Windows Pro edition with the Local Group Policy Editor included. This article is only useful for Home edition users specifically interested in Windows auditing for successful attempts.
Table of Contents:
It is recommended to run a free scan with Malwarebytes — a tool to detect malware and fix computer errors. You will need to purchase the full version to remove infections and eliminate computer errors. Free trial available.
How To See Who Logged Into Windows 10 Using Event Viewer
First, open Event Viewer by typing «event viewer» in Search and clicking the «Event Viewer» result.
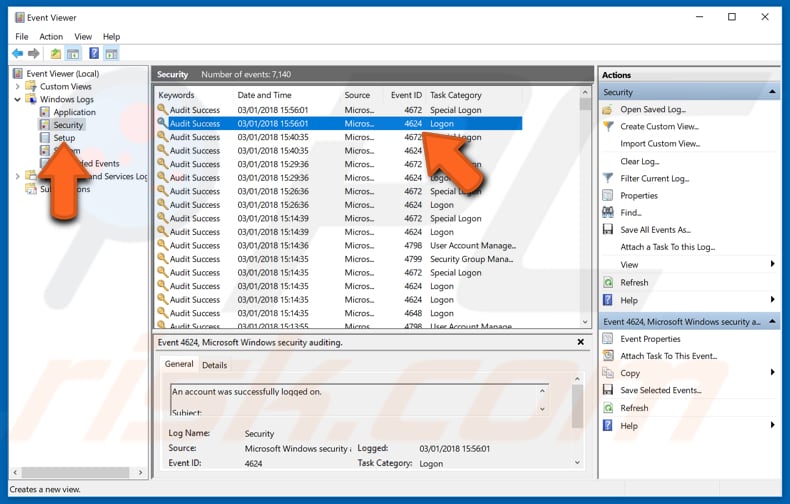
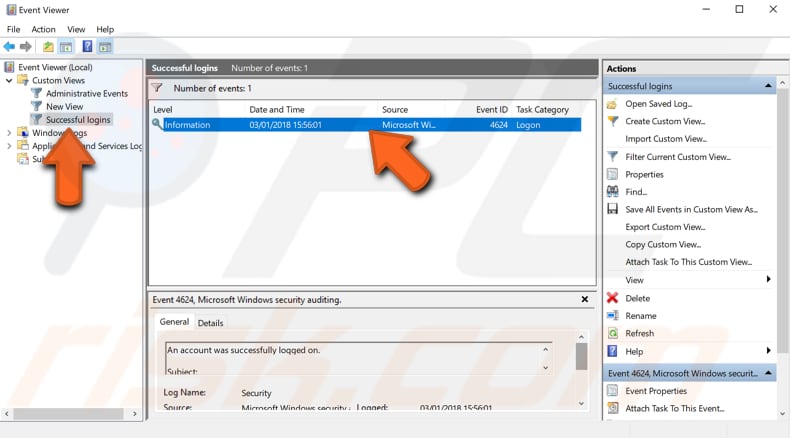
In the Event Viewer, expand the «Windows Logs» category and select «Security». You will see a list of events. Events with ID number 4624 indicate successful sign-ins.
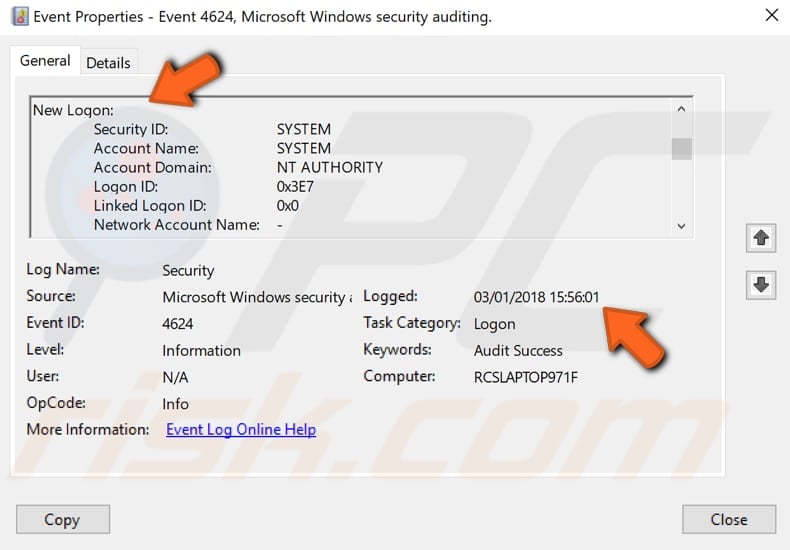
Double click an event with this ID number (4264) to see details. If you are using Windows 10 Pro, you will also see events with ID 4625 (unsuccessful attempts) and 4634 (user log-off) — double-click these to see details.
In the «Logged» section, you can see when someone is logged into your PC (including you). In the «General» tab, look for «New Logon», and you will see the account that is logged in.
How To Set A Custom Filter In Event Viewer
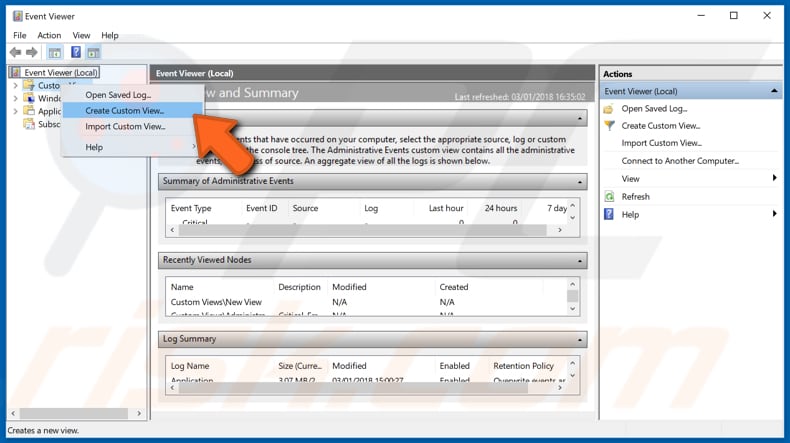
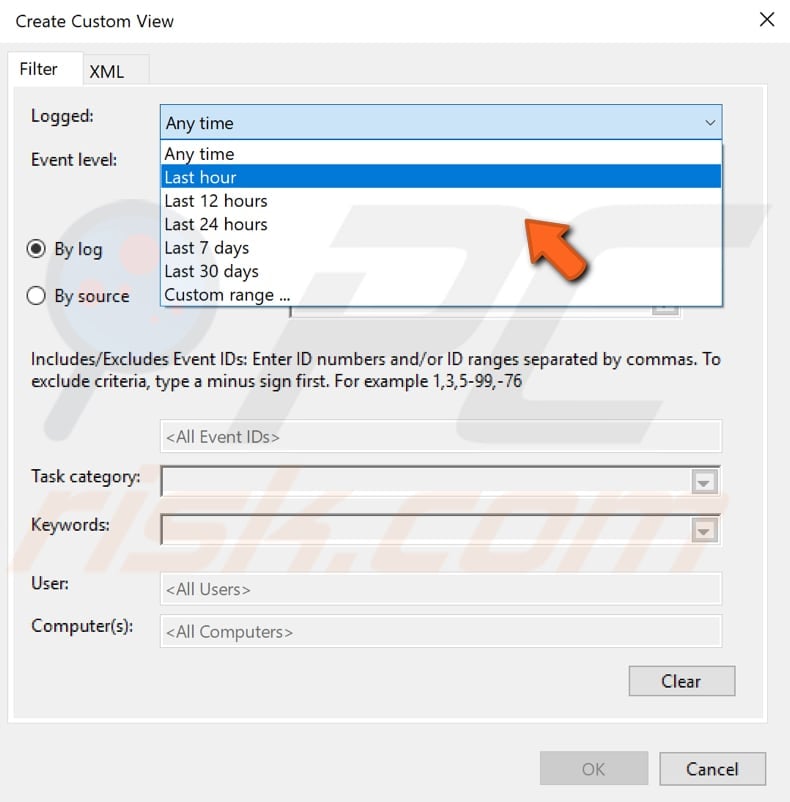
As mentioned, Event Viewer keeps many logs with a great deal of information, so it may be not easy to find a particular event ID (there could be hundreds of events logged throughout the day). There is a filter feature in the Event Viewer enabling you to create a custom view to see only particular event IDs. In this example, we filter use a filter to see only the IDs of logged events pertaining to login attempts. To create this filter, right-click on «Custom Views» and select the «Create Custom View. « option.
In the Create Custom View window, look for the «Logged» section and select a time range.
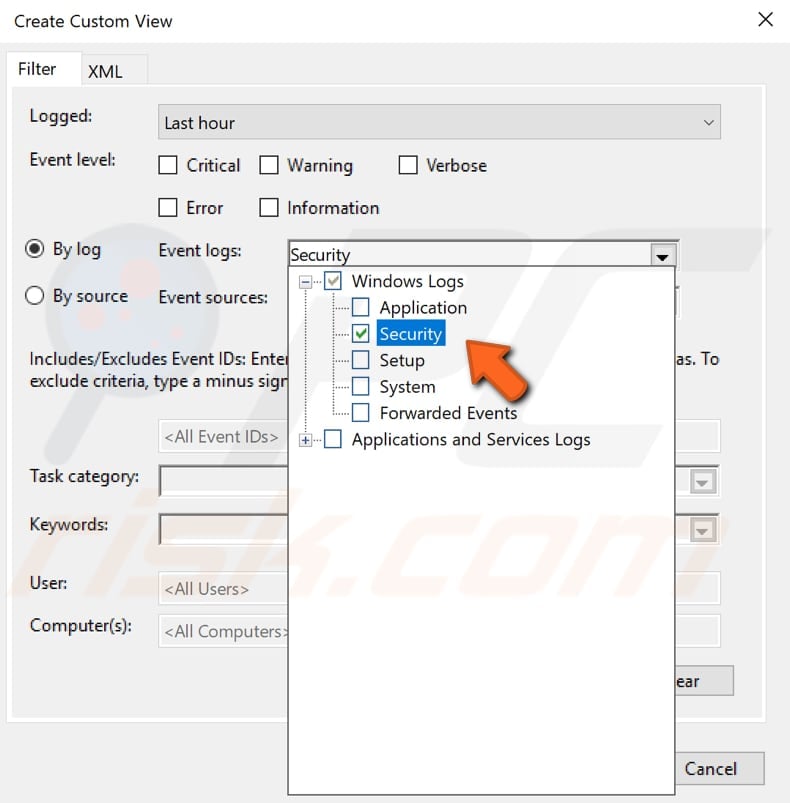
Then choose to view «By log» and select «Security» from the «Windows Logs» drop-down menu.
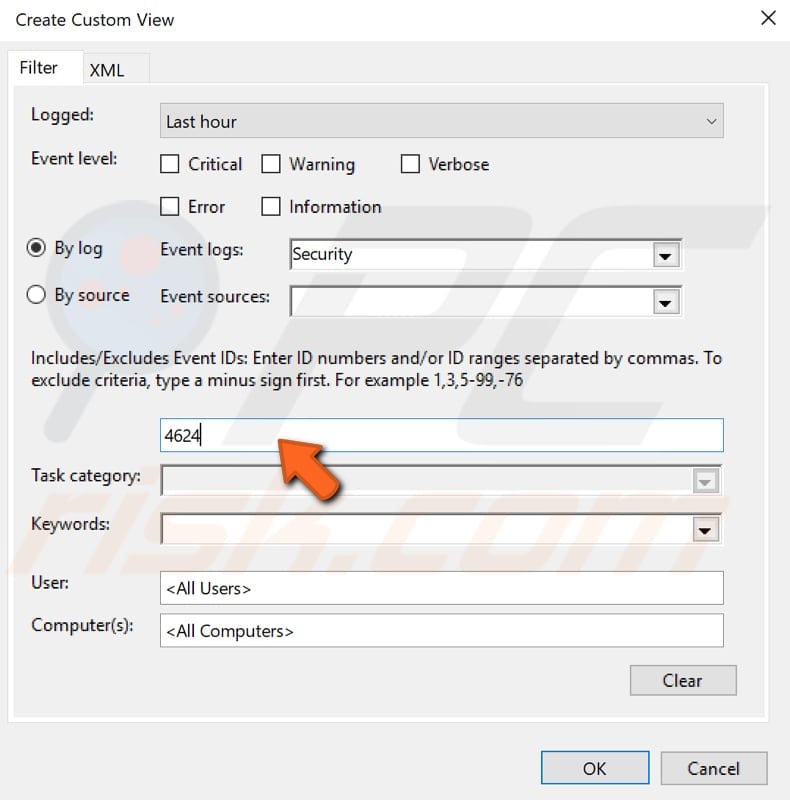
In the Event ID field, type the ID number ‘4624’ and click OK.
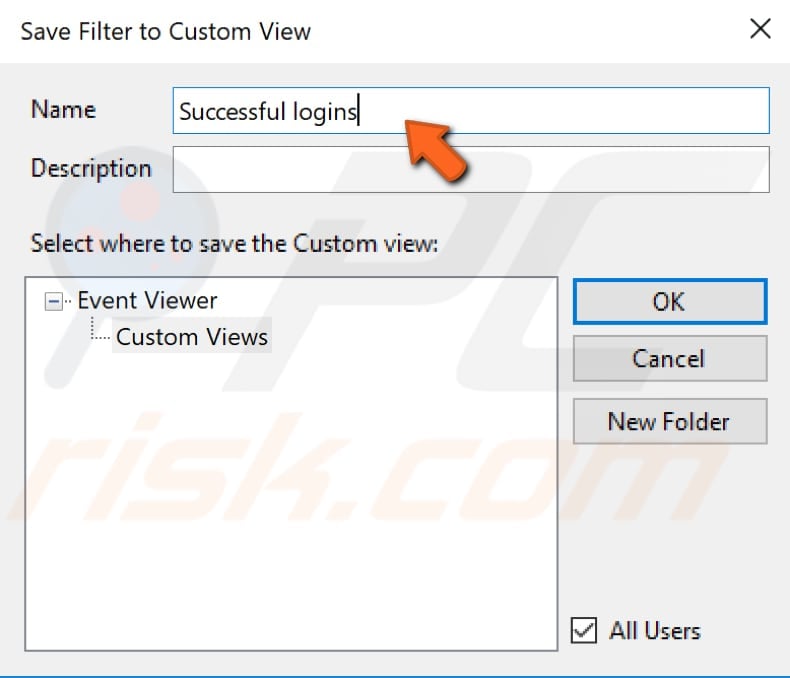
Name your Custom View filter and click OK.
Your Custom View filter is now created and you can see all events logged that match your criteria. Double click the event to see details.
You will now be able to find out who and when users successfully logged in to your PC. This guide works on earlier versions of Windows such as Windows 7 & 8.1. Hope this helped!
Video Showing How To See Who Logged Into Your Windows 10:
Where Are The Windows Logs Stored?
In this article, we discuss Windows logging, using the event viewer, and the windows log storage locations.
Windows VPS server options include a robust logging and management system for logs. These logs record events as they happen on your server via a user process, or a running process. This information is very helpful in troubleshooting services and other issues, or to investigate a security problem.В
Windows references logs as events, while Plesk and most other systems call them logs. For standardization, they call them logs in this article. Follow below to see how you can use the event viewer to review your logs and investigate issues.В
Accessing The Event Viewer
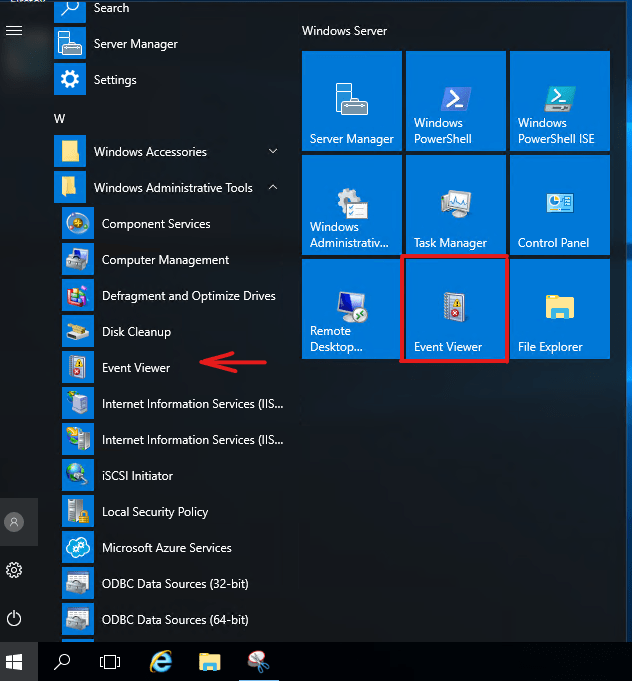
The first step in accessing the Event Viewer is to connect to your server. Gaining access to the server is accomplished through the Console button in Manage, or through a manual RDP connection.
Once you have connected to your Windows server, you will need to log in to your administrator account. Once logged in, click the Start menu, then Event Viewer.
Using The Event Viewer
The event viewer is a system application included on all versions of Windows servers. This program allows you to view logs recorded to it by applications and the system. The event viewer has four main views you will see when you first launch the application:
- Custom Views
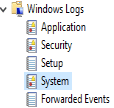
- Windows Logs
- Application and Services logs
- Subscriptions
For this article, we will focus mainly on the Windows Logs. The project you are hosting may have you reference the application logs for programs you use, which may be outside the scope of this article.В
All logs are assigned an event level. This event level denotes the severity or seriousness of any issues noted in the logs. The default view of the list below is by acuity.
- Audit Success — (Security category only)
- Audit Failure — (Security category only)
- Critical
- Error
- Warning
- Information
- Verbose
Log Categories
You will also notice that Windows logs are broken down into categories. These classifications are listed below, along with some quick info about each section.В В
Application — Logs related to drivers and other system components
Security — Logs pertaining to successful and failed logins, and other authentication requestsВ
Setup — Logs associated with Windows install and updates
System — Logs linked to uptime, service status changes, and other messages generated by the operating system
Forward Events — Logs from a remote server, forwarded to this server
Clicking on any of the categories above will load all of the saved logs for that category. The logs will, by default, be arranged in chronological order. You can also modify how the logs are arranged by clicking on any of the column headers.В
Clicking on any specific record will bring up some general information about the log, like the time of the log entry, the log entry level, it’s ID and source, as well as a variety of other information that can be used to identify an issue.В
Clicking on details will provide you with the raw log data, which can present a more considerable amount of detail that can be used to investigate and solve problems.В
Lastly, the default location of these logs can be found in the following folder on the server:В
Get Started Today!
Are you have issues tracking down where problems are occurring on your windows server? Need help deciphering the information in a log file, or trying to locate ways to improve the responsiveness of your server?
Our Level 3 Windows administrators are tough, smart, and experienced techs who can help with any issue. Reach out today if you are running out of options and need to hear from a professional regarding any of our Windows servers or platforms using either our Managed Cloud or Private Cloud Powered by VMware and NetApp!
If you are on a Fully Managed VPS server, Cloud Dedicated, Private Parent server, or a Dedicated server owner and want to make a change, give us a call at 800.580.4985, or open aВ chatВ orВ ticketВ with us to find out how!
How to get Security Log with non-administrative user
Привет Хабр! Читайте под катом как получить доступ к логу безопасности Windows без прав администратора. Эта будет не первая статья на Хабре связанная с логами Windows и наверно не самая оригинальная, но на мой взгляд я потратил слишком много времени на поиск простого решения для чтения логов обычным пользователем, вот я и решил поделиться «историей своего успеха».
Также пришлось сравнить скорость работы Powershell командлетов Get-WinEvent и Get-EventLog.
Все что находится под катом актуально для Windows Server 2008R2/2012R2, Windows 10 Pro (1809), на других версиях я не проверял, думаю что с продуктами 2016 и 2019 годов ситуация аналогичная.
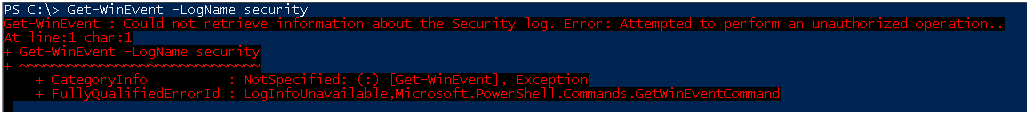
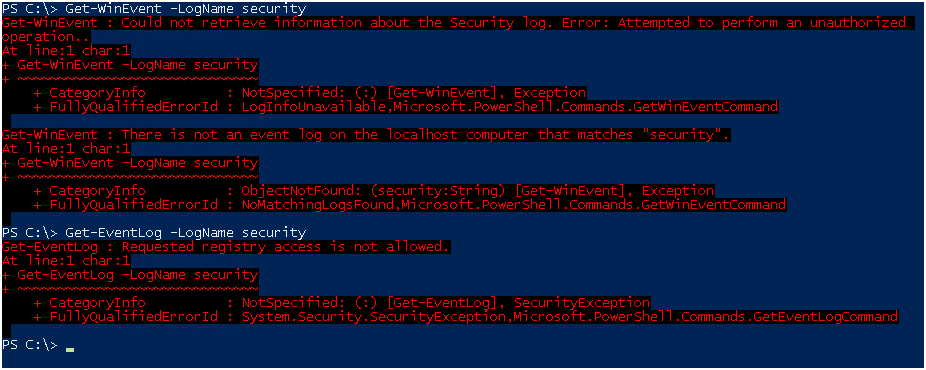
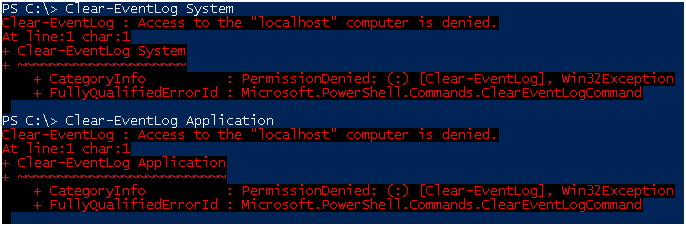
И так, по умолчанию у рядового пользователя прав на чтение логов безопасности нет.
При попытке получить логи вы получите ошибку.
И через Event Viewer в доступе также будет отказано.
SHOWTIME
Добавим пользователя в локальную группу Event Log Readers.
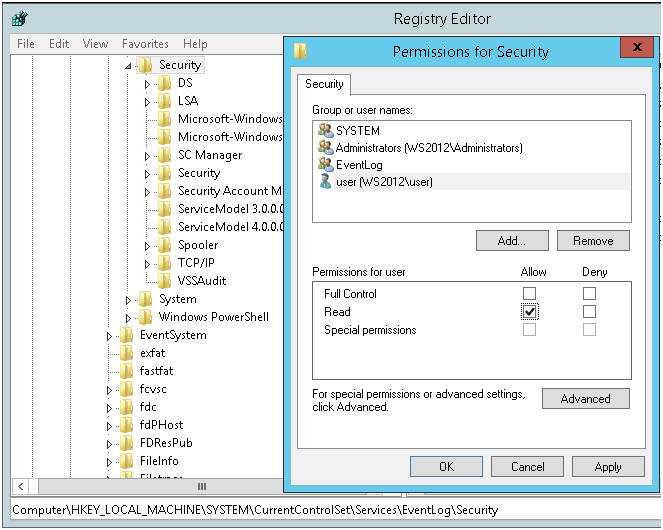
Далее предоставляем права на чтение ветки реестра MACHINE\System\CurrentControlSet\Services\Eventlog\Security.
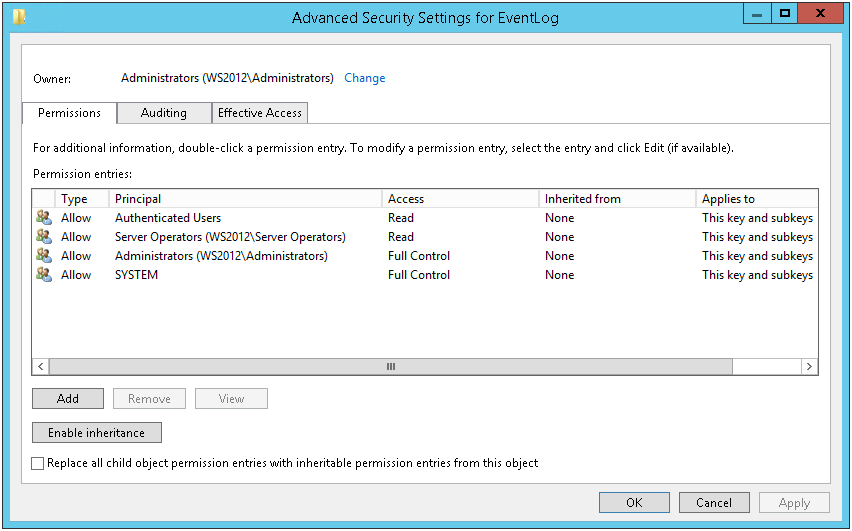
Без изменения прав на эту ветку реестра, прочитать параметры лога безопасности не получится, соответственно не получится узнать место расположение и имя файла с логами. Security, это единственный раздел сервиса Eventlog который не наследует права доступа от корня.
Вот как выглядят права для MACHINE\System\CurrentControlSet\Services\Eventlog.
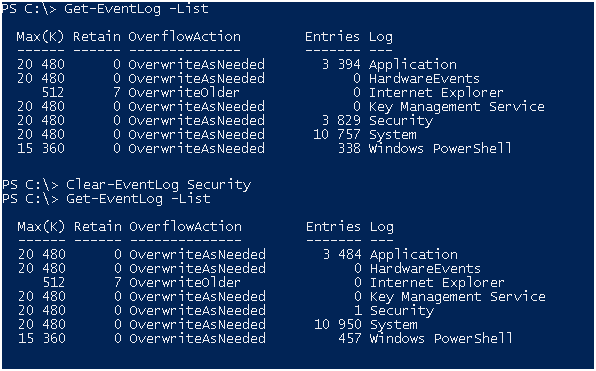
Проверяем, оба командлета Get-WinEvent и Get-EventLog работают!
Позже вернусь к сравнению этих командлетов…
Manage auditing and security log
Если пользователю необходимо предоставить права на отчистку лога, вам придется отредактировать групповую политику. Пользователю или группе пользователей необходимо добавить права Manage auditing and security log.
Находится данная группа тут Computer Configuration\Windows Settings\Security Settings\Local Policies\User Rights Assignment.
Более подробно про Manage auditing and security log можно прочитать тут
This policy setting determines which users can specify object access audit options for individual resources such as files, Active Directory objects, and registry keys. These objects specify their system access control lists (SACL). A user who is assigned this user right can also view and clear the Security log in Event Viewer. For more info about the Object Access audit policy, see Audit object access.
Проверяем, все работает как и было обещано, логи были отчищены…
Другие логии отчистить прав нету.
Честно говоря, не могу придумать сценарий где пользователю нужно выдать права на отчистку логов безопасности, но такая возможность присутствует.
Get-WinEvent VS Get-EventLog
Пришло время сравнить эти два командлета
The Get-EventLog cmdlet gets events and event logs on the local and remote computers.
You can use the cmdlet’s parameters and property values to search for events. This cmdlet gets events that match the specified property values.
The cmdlets that contain the EventLog noun work only on classic event logs. To get events from logs that use the Windows Event Log technology in Windows Vista and later Windows versions, use Get-WinEvent.
The Get-WinEvent cmdlet gets events from event logs, including classic logs, such as the System and Application logs, and the event logs that are generated by the Windows Event Log technology introduced in Windows Vista. It also gets events in log files generated by Event Tracing for Windows (ETW).
Without parameters, a Get-WinEvent command gets all the events from all the event logs on the computer. To interrupt the command, press CTRL + C.
Get-WinEvent also lists event logs and event log providers. You can get events from selected logs or from logs generated by selected event providers. And, you can combine events from multiple sources in a single command. This cmdlet allows you to filter events by using XPath queries, structured XML queries, and simplified hash-table queries
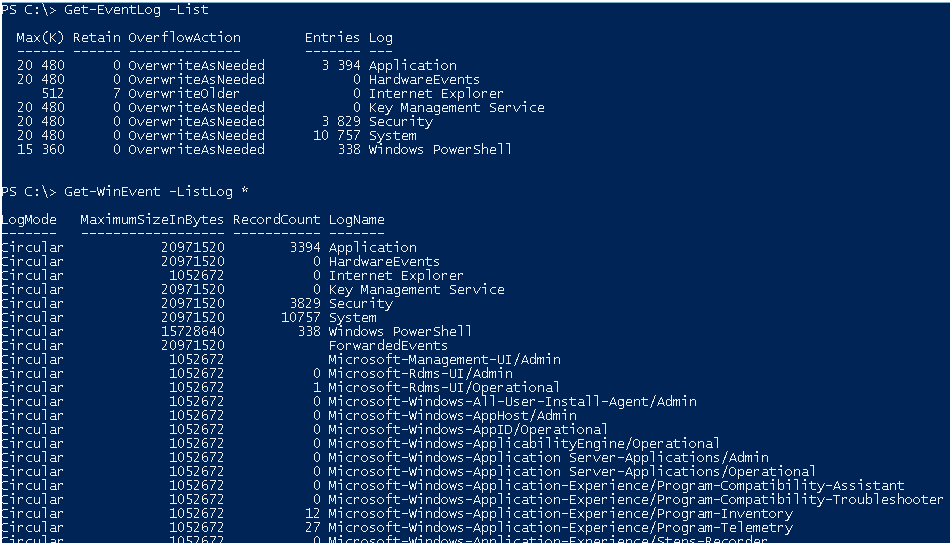
Согласно описания, Get-WinEvent умеет работать с большим количеством журналов которые появились в WIndows Vista.
Для наглядности вот списки с которыми работают эти командлеты, вывод для Get-WinEvent я остановил.
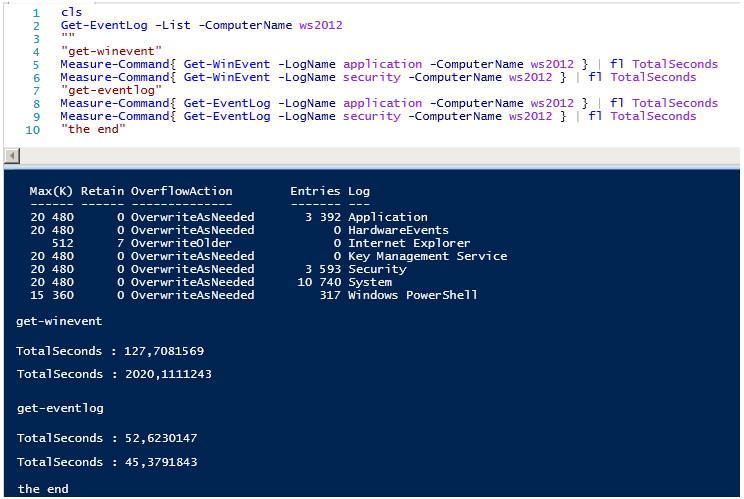
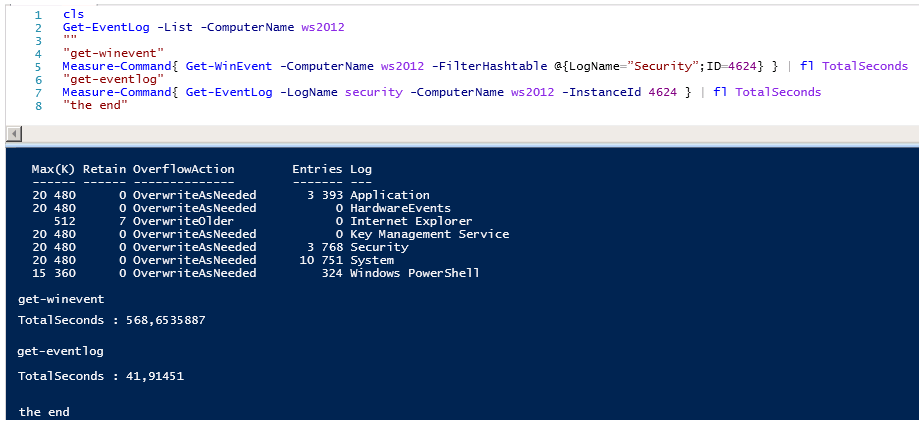
Но есть одно но, производительность имеет значение, сравните время выполнения запросов.
Время работы Get-WinEvent просто поражает, обратите внимание на количество записей в логах Applocation и Security, количество событий примерно одинаковое 3400-3600, но при этом разница по времени выполнения почти 20 раз…
Get-WinEvent тратит 127 секунд против 52 секунд Get-EventLog для чтения событий Application.
И шах и мат, Get-WinEvent тратит 2020 секунд против 45 секунд Get-EventLog для чтения событий Security.
Если выполнить те же команды локально все выглядит не так уж и плохо, но даже локально Get-EventLog работает с логами безопасности в 50 раз быстрее чем Get-WinEvent.
И еще один пример, уже чуть более осмысленный, получения событий с кодом 4624 An account was successfully logged on.
Что тут сказать, цифры не врут…
Non-administrator access to DC Event logs
И на заключение я оставил тему получения доступа к логам безопасности на домен контроллере.
Все выше написанное актуально и для домен контроллера с некоторыми поправками.
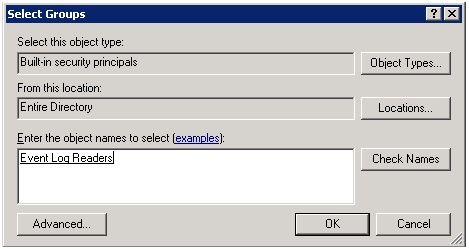
1 — Группу Event Log Readers вы найдете в объектах Built-in security principals.
Добавляя пользователя в данную группу вы даете права только на чтение логов на домен контроллерах.
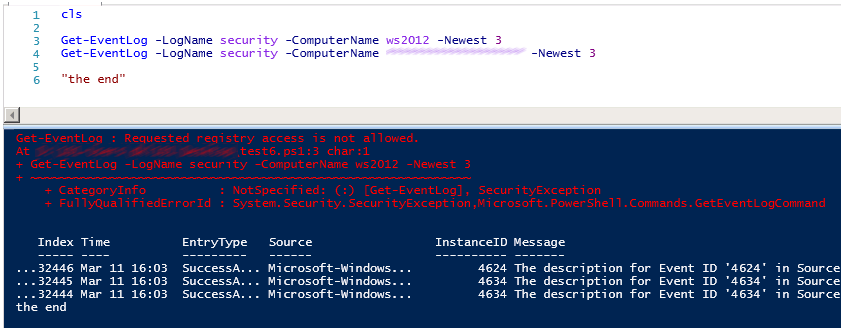
И не забывайте что на каждом из домен контроллеров необходимо дать права на чтение ветки реестра MACHINE\System\CurrentControlSet\Services\Eventlog\Security.
Вот пример, прочитать лог рядового сервера разрешений нет, если вам нужно читать логи с других машин домена, используйте групповые политики, для добавления пользователей или групп пользователей в локальные группы Event Log Readers.
2 – Для добавления прав на отчистку логов необходимо редактировать политику Default Domain Controllers Policy.
3 – Для разрешения запуска заданий от имени пользователя на домен контроллере необходимо также редактировать Default Domain Controllers Policy и дать пользователю права Log on as a batch job.
4 — Будьте предельно внимательными при редактировании дефолтных политик домена!
Краткий список ресурсов, которые мне помогли: