Windows explorer source code
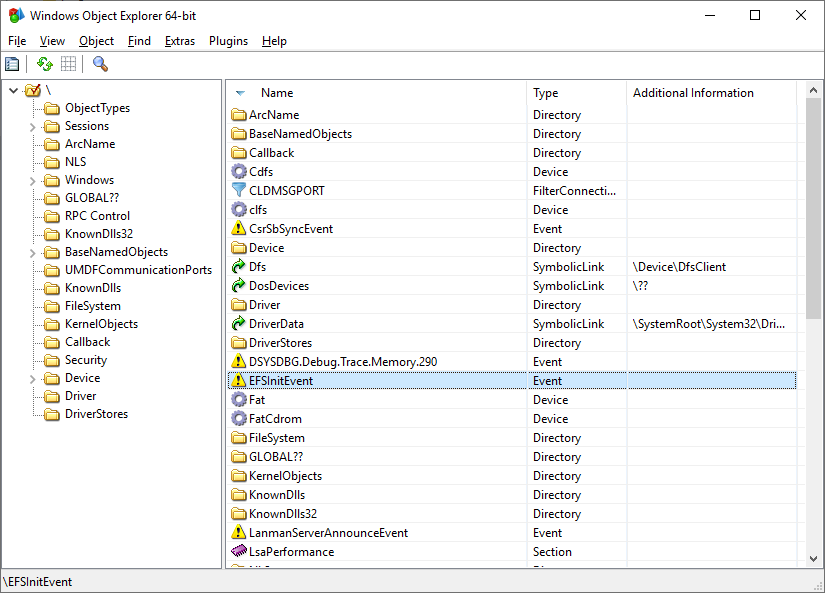
Windows Object Explorer 64-bit
WinObjEx64 is an advanced utility that lets you explore the Windows Object Manager namespace. For certain object types, you can double-click on it or use the «Properties. » toolbar button to get more information, such as description, attributes, resource usage etc. WinObjEx64 let you view and edit object-related security information if you have required access rights.
WinObjEx64 does not require administrative privileges. However administrative privilege is required to view much of the namespace and to edit object-related security information.
WinObjEx64 works only on the following x64 Windows: Windows 7, Windows 8, Windows 8.1 and Windows 10, including Server variants.
Explore all of Windows Object Manager namespace
Hierarchical objects tree
Symbolic links resolving
Version information for Section type objects that are backed by an image file
Additional information for WindowStation type objects
View objects details
- Descriptions
- Flags
- Invalid attributes
- Memory pool type
- Object type specific information
- Object-related structure memory dumps 1
- ALPC_PORT
- CALLBACK_OBJECT
- DEVICE_OBJECT
- DRIVER_OBJECT
- DIRECTORY_OBJECT
- FLT_SERVER_PORT_OBJECT
- KEVENT
- KMUTANT
- KSEMAPHORE
- KTIMER
- KQUEUE (IoCompletion)
- OBJECT_SYMBOLIC_LINK
- OBJECT_TYPE
- Opened handles
- Statistics
- Supported access rights
- Process Trust label
- And more.
Display in dump sub-structures such as 1 :
- ALPC_PORT_ATTRIBUTES
- DEVICE_MAP
- LDR_DATA_TABLE_ENTRY
- OBJECT_TYPE_INITIALIZER
- UNICODE_STRING
- and many others
Edit object-related security information 2
Detect driver object IRP modifications (as part of structure dump) 1
Detect kernel object hooking (as part of structure dump) 1
Search for objects by name and/or type
System information viewer
- Boot state and type
- Code Integrity options
- Mitigation flags
- Windows version and build
Loaded drivers list viewer
- Ability to dump selected driver 1
- Export driver list to file in CSV format
- Jump to driver file location
- Recognize Kernel Shim Engine «shimmed» drivers 1
- View driver file properties
Mailslots/Named pipes viewer
- Display list of all registered mailslots/named pipes
- Named pipes security information editor 4
- Object statistics
Hierarchical process tree viewer 2
- Show process id, user name, EPROCESS addresses
- Highlight processes by type similar to default Process Explorer highlighting
- Show thread list for selected process
- Show ETHREAD addresses
- Show common properties for Process/Thread objects
- Basic properties as for any other object type
- Start time
- Process type
- Image file name
- Command line
- Current directory
- Applied mitigation’s
- Protection
- State of «Critical Process» flag
- Security edit
- Jump to process file location
- Process/Thread token information
- User name
- User SID
- AppContainer SID
- Session
- UIAccess
- Elevation state
- Integrity level
- Privileges and groups
- Show additional token properties for Process/Thread
- Basic properties as for any other object type
- List of security attributes
- Security edit
Software Licensing Cache viewer
- Display list of registered licenses
- Display license data
- Dump license data of type SL_DATA_BINARY to file
User Shared Data viewer
- Display structured dump of most important parts of KUSER_SHARED_DATA
System callbacks viewer 1
- Display address, module and callback specific information for callbacks registered with:
- PsSetCreateProcessNotifyRoutine
- PsSetCreateProcessNotifyRoutineEx
- PsSetCreateProcessNotifyRoutineEx2
- PsSetCreateThreadNotifyRoutine
- PsSetCreateThreadNotifyRoutineEx
- PsSetLoadImageNotifyRoutine
- PsSetLoadImageNotifyRoutineEx
- KeRegisterBugCheckCallback
- KeRegisterBugCheckReasonCallback
- CmRegisterCallback
- CmRegisterCallbackEx
- IoRegisterShutdownNotification
- IoRegisterLastChanceShutdownNotification
- PoRegisterPowerSettingCallback
- SeRegisterLogonSessionTerminatedRoutine
- SeRegisterLogonSessionTerminatedRoutineEx
- IoRegisterFsRegistrationChange
- IopFsListsCallbacks
- ObRegisterCallbacks
- DbgSetDebugPrintCallback
- DbgkLkmdRegisterCallback
- PsRegisterAltSystemCallHandler
- CodeIntegrity SeCiCallbacks
- ExRegisterExtension
Windows Object Manager private namespace viewer 1
- View basic namespace entry information
- View boundary descriptor information
- Show common properties for objects
KiServiceTable viewer 1
- Show dump of Ntoskrnl-managed KiServiceTable (sometimes referenced as SSDT)
- Jump to service entry module
- Export list to file in CSV format
W32pServiceTable viewer 1
- Show dump of Win32k-managed W32pServiceTable (sometimes referenced as Shadow SSDT)
- Support Win32k import forwarding
- Support Win32k ApiSets resolving
- Jump to service entry module
- Export list to file in CSV format
Most of list/trees allows to copy object address and/or name to the clipboard
Running on Wine/Wine-Staging is supported 3
Plugins subsystem for extending basic features
- Available plugins that shipped with WinObjEx64 release:
- ApiSetView — viewer for Windows ApiSetSchema internals, support loading ApiSet schema from file
- Example plugin — example plugin for developers
- Sonar — NDIS protocols viewer, display registered NDIS protocols and dumps some information about them
- ImageScope — context plugin allowing to view more details in WinObjEx64 for Section type objects that are backed by image file (available through popup menu on object of Section type in WinObjEx64 main list)
- Windows Callbacks
- Plugins subsystem
- This feature require driver support enabled, see «Driver support» part below.
- This may require administrator privileges.
- Most of additional Windows internals-specific features however will be unavailable due to obvious reasons.
- Some named pipes may require administrator privileges to access.
WinObjEx64 supports two types of driver helpers:
- Helper for read-only access to the kernel memory. Default version uses Kernel Local Debugging Driver (KLDBGDRV) from WinDbg. In order to use it (and thus enable all the above features) Windows must be booted in the debug mode (bcdedit -debug on) and WinObjEx64 must be run with administrator privileges. If you are using WinObjEx64 version with custom helper driver — Windows debug mode is not required. There are exist several drivers that can be used as helpers for WinObjEx64, by default it has only WinDbg type built-in.
- Helper to access object handles. WinObjEx64 (any variant) support Process Explorer driver of version 1.5.2 to open process/threads. To enable this just load Process Explorer with administrator privileges simultaneously with WinObjEx64.
All driver helpers require WinObjEx64 to be run with administrative privileges.
WinObjEx64 comes with full source code. In order to build from source you need Microsoft Visual Studio 2015/2017/2019 and later versions.
Windows explorer source code
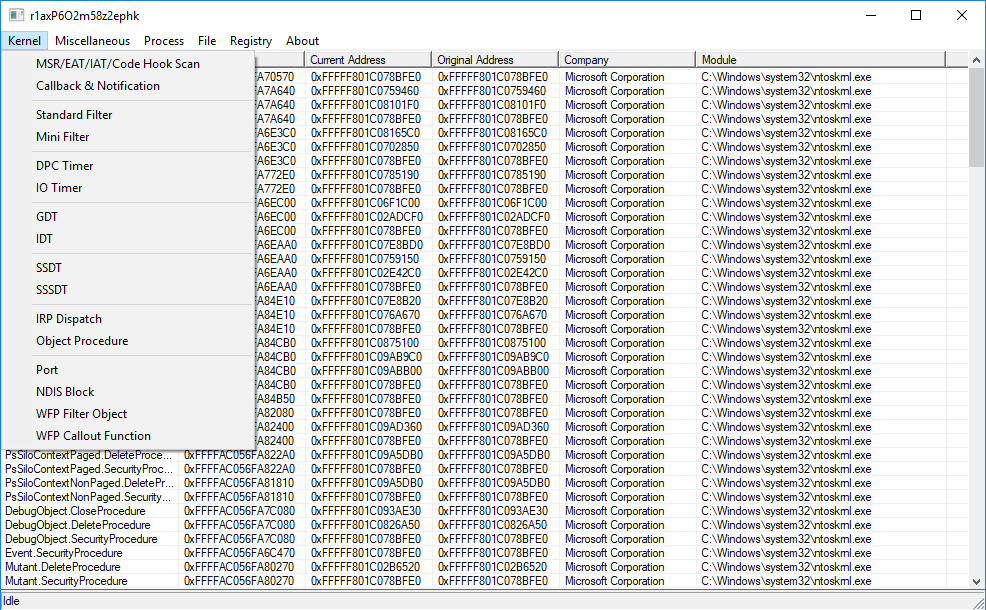
Windows Kernel Explorer (you can simply call it as «WKE») is a free but powerful kernel research tool. It supports from Windows XP to Windows 10 (32-bit and 64-bit). Compared with WIN64AST and PCHunter, WKE can run on the latest Windows 10 without updating binary files.
How WKE works on the latest Windows 10
WKE will automatically download required symbol files if the current system is not supported natively, 90% of the features will work after this step. For some needed data that doesn’t exist in symbol files, WKE will try to retrieve them from the DAT file (when new Windows 10 releases, I will upload a new DAT file to GitHub). If WKE cannot access the internet, 50% of the features will still work. Currently, native support is available from Windows XP to Windows 10 RS3; Windows 10 from RS4 to the lastest version are fully supported by parsing symbol files and DAT file.
How to customize WKE
You can customize WKE by editing the configuration file. Currently, you can specify the device name and symbolic link name of driver, and altitude of filter. You can also enable kernel-mode and user-mode characteristics randomization to avoid being detected by malware. If you rename the EXE file of WKE, you must synchronously rename SYS/DAT/INI files with the same name as the EXE file.
About digital signature and negative comment from Anti-Virus software
Because I don’t have a digital certificate, I have to use the leaked digital certificate from HT SRL to sign drivers of WKE. Signing files with the HT SRL digital certificate has a side effect: almost all Anti-Virus software infer files with HT SRL digital signature are malware, because many hackers use it to sign malwares since 2015. Only idiots implant malicious code into a tool for experienced programmers and reverse engineers, because most users only use WKE in test environments, this kind of behavior is meaningless.
About loading driver unsuccessfully
If WKE prompts «unable to load driver», there may be the following reasons:
- HVCI is enabled.
- Anti-Virus software prevents the driver from loading.
- Disable HVCI or Secure Boot.
- Add the files of WKE to the white list of Anti-Virus software.
About open source
It is a bit awkward, so I say straightforwardly: I don’t plan to share the source code of this tool, but I may share some source code of test programs that associated with this tool.
About WKE can be detected by Anti-Cheat solutions
I received too many SPAM of this issue. I must declare: WKE is not designed to bypass any Anti-Cheat solution. If you need to use WKE in a specfic environment, please order «binary customization» service.
- Process management (Module, Thread, Handle, Memory, Window, Windows Hook, etc.)
- File management (NTFS partition analysis, low-level disk access, etc.)
- Registry management and HIVE file operation
- Kernel-mode callback, filter, timer, NDIS blocks and WFP callout functions management
- Kernel-mode hook scanning (MSR, EAT, IAT, CODE PATCH, SSDT, SSSDT, IDT, IRP, OBJECT)
- User-mode hook scanning (Kernel Callback Table, EAT, IAT, CODE PATCH)
- Memory editor and symbol parser (it looks like a simplified version of WINDBG)
- Hide driver, hide/protect process, hide/protect/redirect file or directory, protect registry and falsify registry data
- Path modification for driver, process and process module
- Enable/disable some obnoxious Windows components
In order to optimize the page load speed in low quality network environments, I only placed one picture on this page.
- Team of WIN64AST: I referenced the UI design and many features of this software.
- Team of PCHunter: I referenced some features of this software.
- Team of ProcessHacker: I studied the source code of this software, but I didn’t use it in my project.
- Donald John Trump: Ich hoffe sehr, dass er noch vier Jahre Präsident sein kann.
E-MAIL: AxtMueller#gmx.de (Replace # with @)
- If you find bugs, have constructive suggestions or would like to purchase a paid service, please let me know.
- You’d better write E-MAIL in English or German, I only reply to E-MAILs that I am interested in.
- In order to disclose as little personal information as possible (IP address, online time, etc.), I do not use instant messaging. Just write what you want in the E-MAIL.
- In order to reduce the impact of the Internet on real life, I also do not use Facebook, Twitter, etc. Please don’t ask me for such information via E-MAIL.
- Binary customization: Modify obvious characteristics of WKE and remove all of my personal information in WKE.
- Implant link: Implant link in WKE on «About» page, all users will see it when main dialog appears.
- Specific feature separation: Copy source code of specific feature to a separate project.
- Driver static library: It contains most of main features of WKE. WBD also uses this static library.
- Driver source code: Entire driver source code of WKE.
- Software customization: Write the user-mode program or kernel-mode driver according to your needs. This service is only available to customers who have purchased any of the above services.
Current Version: 20201111
Bug fix: Enhanced stability.
Revoked Versions: 00000000
These versions have serious security issues and should not be used anymore.
About
A free but powerful Windows kernel research tool.
Windows explorer source code

The Windows File Manager lives again and runs as a native x86 and x64 desktop app on all currently supported version of Windows, including Windows 10. I welcome your thoughts, comments and suggestions.
There are two primary versions of the source code in the master branch:
original_plus tag: refers to the source for WinFile as of Windows NT4 with minimal changes so that it compiles with Visual Studio and runs on current Windows.
current master: contains my personal changes / additions to WinFile.
I will consider bugs fixes and suggestions for minor changes to the master branch. Feel free to create a pull request or post issues as you see fit.
I will not be changing the original_plus sources nor creating other branches for other purposes. You are welcome to do that on your own.
Download The App
If you are running Windows 10, you can download the app from the store
If you just want to download the WinFile application without worrying about compiling from the source code, we have a number of precompiled versions available.
Please select the version which you would like to download.
Latest build from master (located on Azure): Win32 (x86), x64, ARM.
To see more release binaries, including of older versions, see the releases page.
The Windows File manager was originally released with Windows 3.0 in the early 1990s. You can read more about the history at https://en.wikipedia.org/wiki/File_Manager_(Windows).
What it looks like
Thanks to @Speps for the link; not sure who uploaded the image to Wikimedia.
Changes in original_plus
The source code provided here (in the src directory) was copied from the Windows NT 4 source tree in November 2007. The tag named original_plus contains a very limited set of modifications from the original sources to enable WinFile.exe to run on current Windows. The most significant changes are:
- converted to Visual Studio solution; works on VS 2015 and 2017
- compiles and runs on 64-bit Windows (e.g., GetWindowLong -> GetWindowLongPtr, LONG -> LPARAM)
- added a few header files which were stored elsewhere in the NT source tree (e.g., wfext.h)
- deleted some unused files (e.g., winfile.def)
- converted 64-bit arithmetic from internal libraries to C
- converted internal shell APIs to public APIs (the primary reason the old version would not run)
The help directory contains both winfile.hlp and winfile.chm. Winfile.hlp was in the NT4 source tree, but does not work on Windows 10 any more. Winfile.chm was copied from a regular installation of Windows 98 and works on Windows 10. As is, WinFile.exe tries to launch winfile.hlp which fails.
To create your own local branch referring to this release, run git checkout -b original_plus .
Changes in master v10.0 after original_plus
The master branch contains changes I have made since 2007. The changes have been solely determined by my needs and personal use. Some of the changes have limitations that fit the way I use the tool. For example, the path index which supports the new goto command only contains information for the c: drive.
I have also not redesigned or restructured WinFile in any major way.
Version v10.0 represents the entire set of changes from Nov. 2007 until this OSS project was created. For changes post v10.0, see the commit and release history.
In summary v10.0 has the following changes/new features compared to original_plus:
- OLE drag/drop support
- control characters (e.g., ctrl+C) map to current short cut (e.g., ctrl+c -> copy ) instead of changing drives
- cut ( ctrl+X ) followed by paste ( ctrl+V ) translates into a file move as one would expect
- left and right arrows in the tree view expand and collapse folders like in the Explorer
- added context menus in both panes
- improved the means by which icons are displayed for files
- F12 runs notepad or notepad++ on the selected file
- moved the ini file location to %AppData%\Roaming\Microsoft\WinFile
- File.Search can include a date which limits the files returned to those after the date provided; the output is also sorted by the date instead of by the name
- File.Search includes an option as to whether to include sub-directories
- ctrl+K starts a command shell (ConEmu if installed) in the current directory; shift+ctrl+K starts an elevated command shell ( cmd.exe only)
- File.Goto ( ctrl+G ) enables one to type a few words of a path and get a list of directories; selecting one changes to that directory. Only drive c: is indexed.
- UI shows reparse points (e.g., Junction points) as such
- added simple forward / back navigation (probably needs to be improved)
- View command has a new option to sort by date forward (oldest on top); normal date sorting is newest on top
You can read the code for more details.
Contributor License Agreement
As mentioned above, this project welcomes contributions and suggestions. Most contributions require you to agree to a Contributor License Agreement (CLA) declaring that you have the right to, and actually do, grant us the rights to use your contribution. For details, visit https://cla.microsoft.com.
When you submit a pull request, a CLA-bot will automatically determine whether you need to provide a CLA and decorate the PR appropriately (e.g., label, comment). Simply follow the instructions provided by the bot. You will only need to do this once across all repos using our CLA.
This project has adopted the Microsoft Open Source Code of Conduct. For more information see the Code of Conduct FAQ or contact opencode@microsoft.com with any additional questions or comments.
What Makes a Good Pull Request for WinFile?
If you are interested in contributing and/or suggesting changes to the actual application, you might find it helpful to read this post first.
Copyright (c) Microsoft Corporation. All rights reserved.
Licensed under the MIT License.
About
Original Windows File Manager (winfile) with enhancements