- Сетевой доступ: удаленно доступные пути реестра Network access: Remotely accessible registry paths
- Справочные материалы Reference
- Возможные значения Possible values
- Рекомендации Best practices
- Расположение Location
- Значения по умолчанию Default values
- Управление политикой Policy management
- Необходимость перезапуска Restart requirement
- Вопросы безопасности Security considerations
- Уязвимость Vulnerability
- Противодействие Countermeasure
- Возможное влияние Potential impact
- We answer: What are Network locations in Windows 10 and how to use them?
- What are network locations and how do they work in Windows 10?
- Where are the Windows Registry files located in Windows 10?
- Location of Windows Registry files
Сетевой доступ: удаленно доступные пути реестра Network access: Remotely accessible registry paths
Область применения Applies to
В этой статье описываются лучшие методики, расположение, значения, управление политиками и вопросы безопасности для сетевого доступа: параметр политики безопасности путей реестра с удаленным доступом. Describes the best practices, location, values, policy management and security considerations for the Network access: Remotely accessible registry paths security policy setting.
Справочные материалы Reference
Этот параметр политики определяет, какие пути реестра доступны, когда приложение или процесс ссылаются на ключ WinReg для определения разрешений доступа. This policy setting determines which registry paths are accessible when an application or process references the WinReg key to determine access permissions.
Реестр — это база данных для сведений о конфигурации устройств, большая часть которых является конфиденциальной. The registry is a database for device configuration information, much of which is sensitive. Злоумышленник может использовать реестр для упрощения несанкционированных действий. A malicious user can use the registry to facilitate unauthorized activities. Чтобы снизить риск этого, во всем реестре назначены подходящие списки управления доступом (ALS), которые помогут защитить его от доступа неавторизованного пользователя. To reduce the risk of this happening, suitable access control lists (ACLs) are assigned throughout the registry to help protect it from access by unauthorized users.
Чтобы разрешить удаленный доступ, необходимо также включить службу удаленного реестра. To allow remote access, you must also enable the Remote Registry service.
Возможные значения Possible values
- Пользовательский список путей User-defined list of paths
- Не определено Not Defined
Рекомендации Best practices
- Установите для этой политики значение null; то есть введите параметр политики, но не вводите пути в текстовом поле. Set this policy to a null value; that is, enable the policy setting but do not enter any paths in the text box. Для средств удаленного управления, таких как Microsoft Baseline Security Analyzer и Configuration Manager, требуется удаленный доступ к реестру. Remote management tools, such as the Microsoft Baseline Security Analyzer and Configuration Manager, require remote access to the registry. Удаление путей реестра по умолчанию из списка доступных путей может привести к сбойу этих и других средств управления. Removing the default registry paths from the list of accessible paths might cause these and other management tools to fail.
Расположение Location
Конфигурация компьютера\Параметры Windows\Параметры безопасности\Локальные политики\Параметры безопасности Computer Configuration\Windows Settings\Security Settings\Local Policies\Security Options
Значения по умолчанию Default values
В следующей таблице перечислены фактические и эффективные значения по умолчанию для этой политики. The following table lists the actual and effective default values for this policy. Значения по умолчанию также можно найти на странице свойств политики. Default values are also listed on the policy’s property page.
| Тип сервера или объект групповой политики Server type or GPO | Значение по умолчанию Default value |
|---|---|
| Default Domain Policy Default Domain Policy | Не определено Not defined |
| Политика контроллера домена по умолчанию Default Domain Controller Policy | Не определено Not defined |
| Параметры по умолчанию для автономного сервера Stand-Alone Server Default Settings | См. следующее сочетание ключей реестра See the following registry key combination |
| Эффективные параметры по умолчанию для DC DC Effective Default Settings | См. следующее сочетание ключей реестра See the following registry key combination |
| Действующие параметры по умолчанию для рядового сервера Member Server Effective Default Settings | См. следующее сочетание ключей реестра See the following registry key combination |
| Действующие параметры по умолчанию для клиентского компьютера Client Computer Effective Default Settings | См. следующее сочетание ключей реестра See the following registry key combination |
Сочетание всех следующих параметров реестра применяется к предыдущим настройкам: The combination of all the following registry keys apply to the previous settings:
- System\CurrentControlSet\Control\ProductOptions System\CurrentControlSet\Control\ProductOptions
- System\CurrentControlSet\Control\Server Applications System\CurrentControlSet\Control\Server Applications
- Software\Microsoft\Windows NT\CurrentVersion Software\Microsoft\Windows NT\CurrentVersion
Управление политикой Policy management
В этом разделе описываются функции и средства, которые помогут вам управлять этой политикой. This section describes features and tools that are available to help you manage this policy.
Необходимость перезапуска Restart requirement
Нет. None. Изменения этой политики становятся эффективными без перезапуска устройства, если они сохраняются локально или распространяются посредством групповой политики. Changes to this policy become effective without a device restart when they are saved locally or distributed through Group Policy.
Вопросы безопасности Security considerations
В этом разделе описывается, каким образом злоумышленник может использовать компонент или его конфигурацию, как реализовать меры противодействия, а также рассматриваются возможные отрицательные последствия их реализации. This section describes how an attacker might exploit a feature or its configuration, how to implement the countermeasure, and the possible negative consequences of countermeasure implementation.
Уязвимость Vulnerability
Злоумышленник может использовать сведения в реестре для упрощения несанкционированных действий. An attacker could use information in the registry to facilitate unauthorized activities. Чтобы снизить риск такой атаки, во всем реестре назначены подходящие ALS для защиты от доступа неавторизованного пользователя. To reduce the risk of such an attack, suitable ACLs are assigned throughout the registry to help protect it from access by unauthorized users.
Противодействие Countermeasure
Настройте сетевой доступ: параметр путей реестра с удаленным доступом имеет значение NULL (введите параметр, но не вводите пути в текстовом поле). Configure the Network access: Remotely accessible registry paths setting to a null value (enable the setting, but do not enter any paths in the text box).
Возможное влияние Potential impact
Средства удаленного управления, такие как microsoft Baseline Security Analyzer (MBSA) и Configuration Manager, требуют удаленного доступа к реестру для надлежащего мониторинга и управления этими компьютерами. Remote management tools such as the Microsoft Baseline Security Analyzer (MBSA) and Configuration Manager require remote access to the registry to properly monitor and manage those computers. Если удалить пути реестра по умолчанию из списка доступных, такие средства удаленного управления могут не работать. If you remove the default registry paths from the list of accessible ones, such remote management tools could fail.
Примечание. Чтобы разрешить удаленный доступ, необходимо также включить службу удаленного реестра. Note: If you want to allow remote access, you must also enable the Remote Registry service.
We answer: What are Network locations in Windows 10 and how to use them?
Online safety is quite important, therefore Microsoft created several features designed to protect Windows 10 users. Network locations is one of these features, and today we’re going to explain you what are network locations and how do they work.
What are network locations and how do they work in Windows 10?
As previously mentioned, network locations are designed to protect your PC while connecting to different networks. We wrote briefly about network locations in our how to protect your Windows 10 device on public Wi-Fi network article, so you might want to check that article for some extra security tips.
Network locations were introduced in Windows Vista, and over the years Microsoft improved and streamlined that feature. This feature made its way to Windows 10, and it works almost the same like in previous versions of Windows.
Network location is basically a profile with certain settings related to network discovery and file sharing. When you access a certain network for the first time Windows 10 will ask you to choose one of the three profiles: Home network, Work network and Public network. Each of these profiles comes with different settings optimized for certain conditions.
For example, Home network option is designed for networks that you fully trust. This option comes with most settings enabled, so you can easily see other computers that are connected to this network. In addition to being able to see other devices on this network, you can also create or join Homegroup and share files easily with other devices on your network.
Work network profile comes with the same settings that allow you to see other devices on your network, but unlike with Home network profile, by using the Work profile you won’t be able to create or join Homegroups.
Last profile is Public network, and this profile doesn’t allow you to see other computers connected to the same network. At the same time other computers won’t be able to see your PC as well, therefore you should be relatively protected from malicious users. Since file sharing is disabled for this profile, malicious users on the same network won’t be able to share any potentially harmful files with you. As you can see, this profile is especially useful if you’re in a internet cafe or if you’re using Wi-Fi network at any public location along with many other unknown users.
We should mention that you can easily change your Network locations settings by following these steps:
- Press Windows Key + S and enter network. Select Network and Sharing Center from the list of results.
- Once Network and Sharing Center opens, click the Change advanced sharing settings.
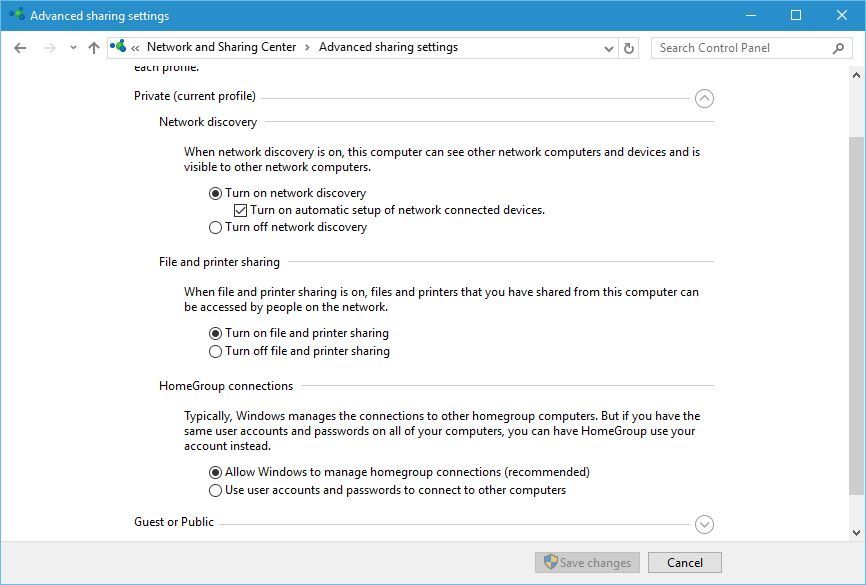
Now you should see network settings for all available profiles. You’ll notice that there are two groups of profiles, Private that include Work and Home network profiles and Guest or Public group.
In Private group first option is Network discovery. By turning on this feature you allow your computer to be seen by other network devices on your network. If you’re on a home network and you recognize all the devices on your network, you can freely turn this feature on.
Next on our list is File and printer sharing. This feature allows you to turn on file and printer sharing with other network devices. Again, if you recognize all the devices on your local network, you can turn on this feature.
Last option is HomeGroup connections, and this feature allows you to manage your Homegroup connections. By default, Windows manages the Homegroup connections for you, but if you want you can use user accounts and passwords to connect to other computers.
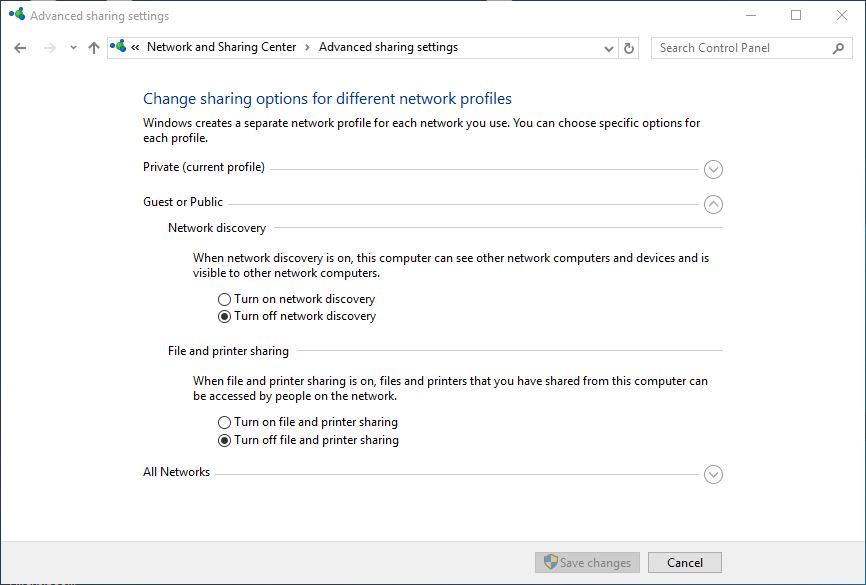
Guest or Public group has only two options and those options are Network discovery and File and printer sharing. Since we already explained how both of these options work there’s no need to explain again.
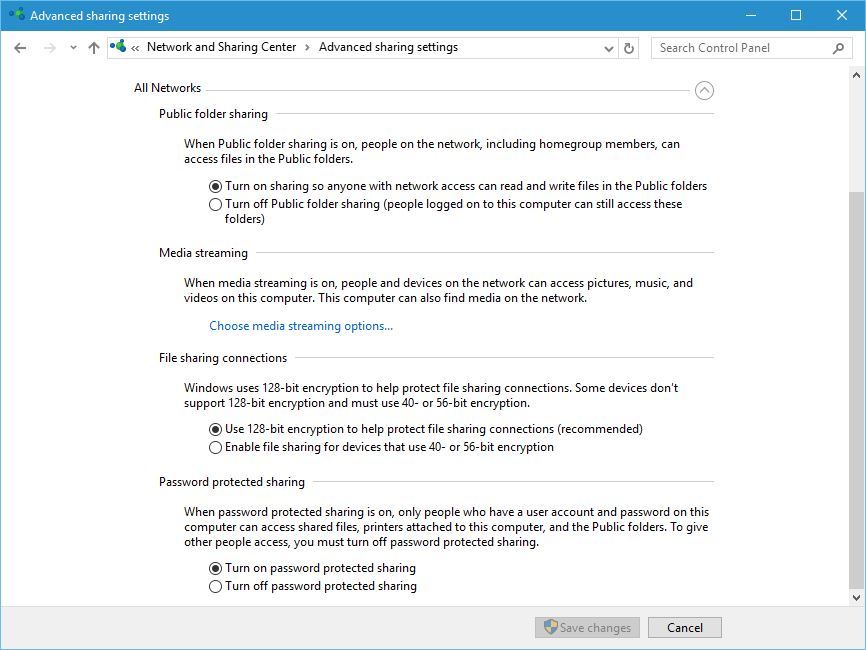
Last on our list is All Networks group, and the first option available is Public folder sharing. By turning this option on you allow other people on this network to access files stored in the Public folder. By default this option is turned on.
Next option is media streaming and you can enable this option to allow other people and devices to access pictures, music and videos on your PC. In addition, by using this option you allow your computer to find media on the network.
File sharing connections allow you to choose the method of encryption for file sharing. By default 128-bit encryption is used, but you can switch to 40 or 56-bit encryption if your devices don’t support 128-bit encryption.
Last option is password protected sharing. This is one of the most important options because it allows only users that know your computer password to access your files or printer. If the user doesn’t have your password, it won’t be able to see your Public files or any of your shared files.
Network locations are important feature of Windows 10, and we hope you understand a bit better how network locations work and how to use them to protect your PC.
Where are the Windows Registry files located in Windows 10?
The Windows Registry is the centralized configuration database for Windows NT and Windows 2000, as well as for applications. The Registry in Windows 10/8/7 stores information about tuning parameters, device configuration, and user preferences.
On disk, the Windows Registry isn’t simply one large file, but a set of discrete files called hives. Each hive contains a Registry tree, which has a key that serves as the root (i.e., starting point) of the tree. Subkeys and their values reside beneath the root.
Location of Windows Registry files
The location of these registry hives are as follows:
- HKEY_LOCAL_MACHINE \SYSTEM : \system32\config\system
- HKEY_LOCAL_MACHINE \SAM : \system32\config\sam
- HKEY_LOCAL_MACHINE \SECURITY : \system32\config\security
- HKEY_LOCAL_MACHINE \SOFTWARE : \system32\config\software
- HKEY_USERS \UserProfile : \winnt\profiles\username
- HKEY_USERS.DEFAULT : \system32\config\default
The supporting files are as follows:
Some hives are volatile and don’t have associated files. The system creates and manages these hives entirely in memory; the hives are therefore temporary. The system creates volatile hives every time the system boots. Examples are:
- HKEY_LOCAL_MACHINE \ HARDWARE : Volatile hive
- HKEY_LOCAL_MACHINE \ SYSTEM \ Clone : Volatile hive
These files are database files, and only RegEdit, Regedit32, and Kernel32 can read them. The primary tool in Windows 10/8/7 for working directly with the registry is Registry Editor.
To access it, simply type Regedit in Start Menu Search Bar and hit Enter.
If you need to read more on this, head over to TechNet.
UPDATE: AccidentalADMIN has made a useful comment. He says:
Every Windows has a Registry Key which lists every hive in the system. Run regedit to open the Registry Editor and navigate to the following key to get a complete list: