- Use Netstat to See Listening Ports and PID in Windows
- What Is Netstat?
- Using Netstat To See Listening Ports & PID
- What’s Using That Port?
- How To Get Port, PID, & Process Name In PowerShell
- Go Get Them
- PID Как узнать открытые порты TCP/IP приложений в Windows
- PID Как узнать в разных ОС Windows
- Как по PID узнать используемые порт TCP/IP
- PID:4 using Port 80
- 6 Answers 6
- Windows Process from PID
- 4 Answers 4
- Find the PID of a process that uses a port on Windows
- 7 Answers 7
Use Netstat to See Listening Ports and PID in Windows
You never know when this will come in handy
In another article, we explained computer ports and what they’re used for. Other than that, what can we do with port information? Since all traffic in and out of the computer goes through ports, we can check on them to see what they’re doing. Maybe the port isn’t listening for traffic? Maybe something is using a port that shouldn’t be?
We’re going to use the Windows command netstat to see our listening ports and PID (Process ID). We’re also going to see what we can do with that information.
What Is Netstat?
The netstat command is a combination of the words ‘network’ and ‘statistics’. The netstat command works in all versions of Windows from Windows XP right up to Windows 10. It’s also used in other operating systems (OS) like Unix and Linux, but we’ll stick to Windows here.
Netstat can provide us with:
- The name of the protocol the port is using (TCP or UDP).
- The local IP address and name of the computer and the port number being used.
- The IP address and port number to which we’re connecting.
- The state of a TCP connection. For details on what these states are, read the Event Processing section of RFC 793.
Using Netstat To See Listening Ports & PID
- Use the key combination Win Key + X. In the menu that opens, select Command Prompt.
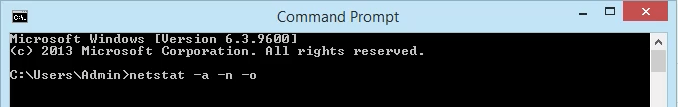
- Enter the command . The parameters for netstat are preceded with a hyphen, not a forward slash like many other commands. The -a tells it to show us all active connections and the ports on which the computer is listening.
The -n tells netstat to show the IP addresses and ports as numbers only. We’re telling it to not try to resolve the names. This makes for a quicker and neater display. The -o tells netstat to include the PID. We’ll use the PID later to find out what process is using a specific port.
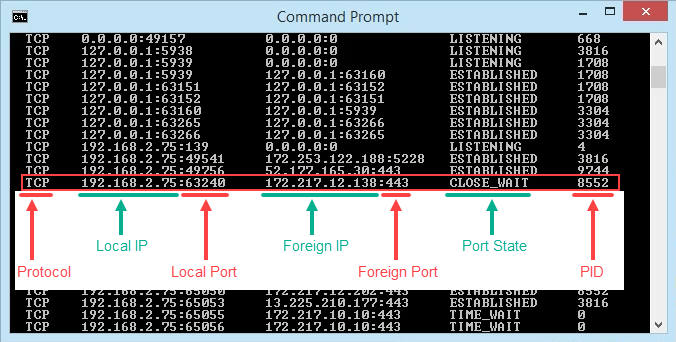
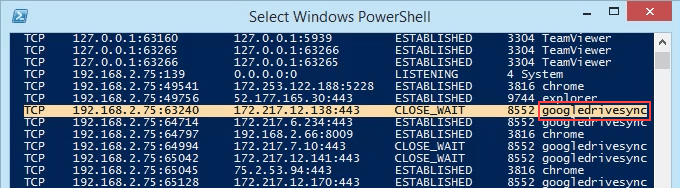
- View the results and take note of the addresses, port numbers, state, and PID. Let’s say we want to know what’s using port 63240. Note that its PID is 8552 and it’s connecting to the IP address 172.217.12.138 on port 443.
What’s Using That Port?
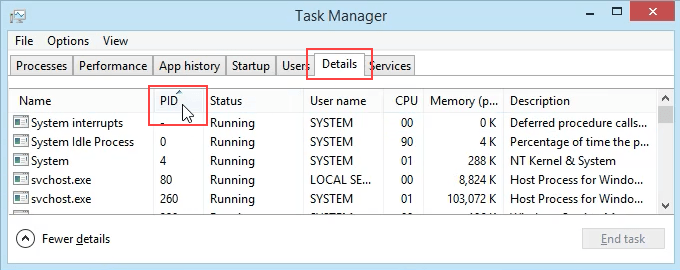
- Open Task Manager. That’s most easily done by using the key combination Ctrl + Shift + Esc.
- Click on the Details tab. To make this easier to find, click on the PID column header to sort the PIDs numerically.
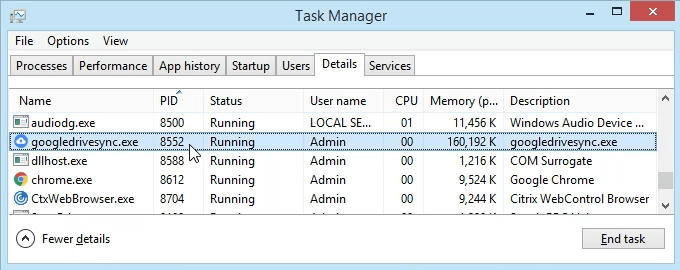
- Scroll down to PID 8552 and see what process it is. In this case, it’s googledrivesync.exe. But is it really? Sometimes viruses can make themselves look like legitimate processes.
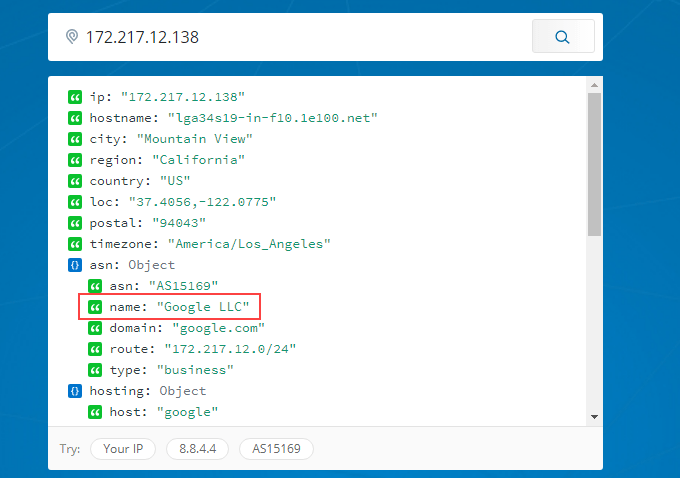
- In a web browser, go to ipinfo.io. Enter the IP address 172.217.12.138. As we can see, the IP address is registered to Google. So this googledrivesync.exe is a legitimate one.
How To Get Port, PID, & Process Name In PowerShell
PowerShell is Microsoft’s newer way to use a command-line interface with Windows. We say newer, but it’s been around for several versions. You should learn PowerShell even if you’re a home user.
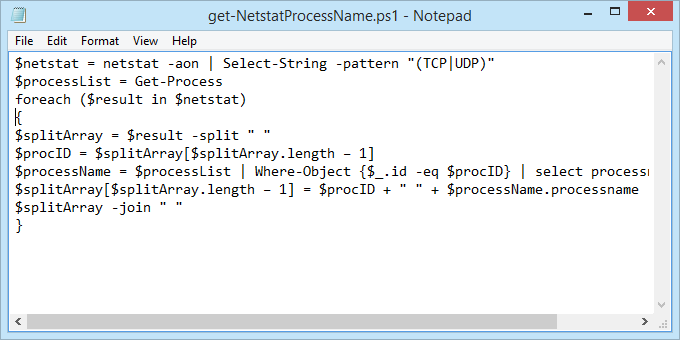
Most Windows commands also work in PowerShell, plus we can combine them with PowerShell’s cmdlets – pronounced command-lets. Joe at Winteltools.com provides the script for this method.
- Open Notepad and enter the following code:
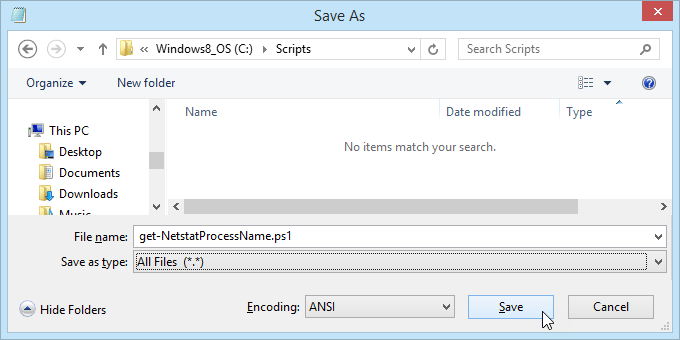
- Save the file as get-NetstatProcessName.ps1. Make sure to note where it’s being saved. It’s important to change the Save as type: to All Files (*.*) or it will get saved as get-NetstatProcessName.ps1.txt and it won’t work for us.
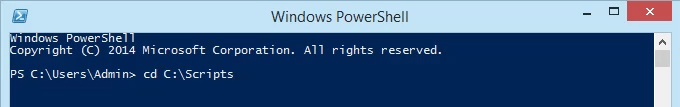
- Open PowerShell and navigate to the location in which the script was saved. In this case, it’s . Hit Enter to run the command.
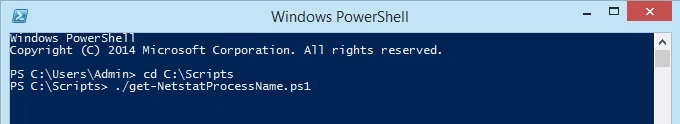
- Run the script using dot-sourcing to make it work. That means use ./ before the name of the file. The command will be
- Now we can see all the traditional netstat info plus the process name. No need to open Task Manager anymore.
Go Get Them
We’ve covered two ways to use the netstat command to see listening ports. It can be used either in the old Command Prompt or within a PowerShell script. With the information it can give us, we’ve looked at how it can help us figure out what our computer is doing.
If you thought netstat is a great utility, take a look at some other Windows TCP/IP utilities like tracert, ipconfig, and nslookup. Or use Resource Monitor to get a better look into hidden website and Internet connections. There is a lot you can do to see exactly what your computer is doing.
Have you used netstat to solve a problem? Please tell us what you did. Any questions about how to use netstat? Please ask us in the comments below.
Guy has been published online and in print newspapers, nominated for writing awards, and cited in scholarly papers due to his ability to speak tech to anyone, but still prefers analog watches. Read Guy’s Full Bio
PID Как узнать открытые порты TCP/IP приложений в Windows
Идентификатор процесса (англ. process identifier , PID ) — уникальный номер (идентификатор) процесса в многозадачной операционной системе (ОС)
wikipedia.org
Иногда в работе сталкиваемся с необходимостью узнать/проверить открытый порт у приложения.Не всегда все зависит от заданных параметров в конфигурации, да и как часто бывает проблема не в нем, а в сетевых настройках фаервола.
При помощью командной строки можно узнать всю эту информацию. Конечно есть и более простые варианты с помощью специализированного программного обеспечения от разных производителей, в некоторых случаях это даже на много удобнее и быстрее. Но не всегда есть то заветное приложение на компьютере, а командная строка есть всегда в наличии у Windows.
Рассмотрим случай когда нам надо узнать по запущенному приложению открытые порты.
PID Как узнать в разных ОС Windows
- Владельцев ОС Windows 7 или более поздней версии, PID можно узнать с помощью диспетчера задач.
- Нажмите на клавиатуре одновременно на клавиши Ctrl, Shift и Esc.
- В окне Диспетчер задач перейдите на вкладку Процессы.
- Выберите пункт Вид → Выбрать столбцы.
- В окне Выбор столбцов страницы процессов установите флажок ИД процесса (PID).
- Нажмите OK.
- На вкладке Процессы найдите нужный процесс и в колонке ИД процесса (PID) идентификатор процесса.
- Владельцам ОС Windows 10 или 8.1 для вас есть два варианта узнать
- Первый быстрый вариант запустить CMD от имени администратора и ввести команду tasklist и найти PID интересующего приложения, скопировать данные для дальнейшей работы.
- Второй быстрый вариант открыть диспетчер задач сочетанием клавиш Ctrl, Shift и Esc и
посмотреть ИД процесса в закладках «Подробности» или «Службы«.
Как по PID узнать используемые порт TCP/IP
Обратимся к командной строке за поиском портов с командой netstat
О возможностях netstat и findstr
PID:4 using Port 80
I was trying to install Zend Server CE on my computer but when I got to the point were I need to choose the port for my Web Server it says: «Web Server Port: 80 Occupied». So I decided to check what is using Port 80 with CMD by typing: «netstat -o -n -a | findstr 0.0:80»:
I check for PID:4 in Task Manager’s Processes and Services. Seems PID 4 is «System».
So, what I want to know is how can I stop «System» (PID:4) from using Port 80?
INFO: I am using: Windows 7 64bit; Zend Server CE 5.5.0
6 Answers 6
Ok, after searching the web for a while I found a solution to my problem.
Just follow these steps to diagnose and resolve your issue:
Get pid that is listening port 80: netstat -nao | find «:80»
Open task manager, go to processes tab and check “PID” in Menu/View/Select Columns… , then look for the process using the PID found in last step.
If it is a normal application or IIS, disable it or uninstall. Some programs (such as Skype) have the option to disable its use of port 80.
If it is a System Process—PID 4—you need to disable the HTTP.sys driver which is started on demand by another service, such as Windows Remote Management or Print Spooler on Windows 7 or 2008.
There is two ways to disable it but the first one is safer:
Go to device manager, select “show hidden devices” from menu/view, go to “Non-Plug and Play Driver”/HTTP, double click it to disable it (or set it to manual, some services depended on it).
Reboot and use netstat -nao | find «:80» to check if 80 is still used.
Go to HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\HTTP
Change the value of «start» to 4, which means disabled.
Windows Process from PID
I’m trying to determine which application or system program is using a particular port on a Windows 2008 R2 machine.
And have determined that PID is holding open port 445, which I’m interested in.
But when I run tasklist or Microsoft’s pslist program, it tells me that the process holding the port open is simply named ‘Sys’.
Is there another tool or approach I can use to find which is the real process holding it open?
4 Answers 4
PID 4 is the system process — if PID 4 is holding a port open, it means that some device driver has opened the port. Given that it’s port 445, my guess is that it’s the CIFS network filesystem or server. Try doing a «net stop srv» and «net stop rdr» from an elevated command prompt — that should shut down the service using the port.
The sysinternals tool procexp (process explorer) shows both processes and if the process is a service — it can show which services are running in the same process. (Windows service processes can contain a number of service threads).
Port 445 is normally the SMB port for Windows domain activities and file sharing and so on.
Have you looked at TCPView http://technet.microsoft.com/en-us/sysinternals/bb897437? It’s another tool from sysinternals.
There is a free tool on Nirsoft’s website called «CPORTS» with both 32 and 64 bit versions that might help you. Port 445 is used by Server 2008 R2 and later for communicating with other systens using SAMBA /TCP. I got the list below from «cyberciti.biz»
■netbios-ns — 137/tcp # NETBIOS Name Service ■netbios-dgm — 138/tcp # NETBIOS Datagram Service ■netbios-ssn — 139/tcp # NETBIOS session service ■microsoft-ds — 445/tcp # if you are using Active Directory ■Port 389 (TCP) — for LDAP (Active Directory Mode) ■Port 445 (TCP) — NetBIOS was moved to 445 after 2000 and beyond, (CIFS) ■Port 901 (TCP) — for SWAT service (not related to client communication
If you can run «grep» this is their recommended format: «$ grep -i NETBIOS /etc/services». If not, «AstroGrep» is a little more «user-friendly» Both can be gotten from SourceForge. My own interest lies in a solution to why some systems are unable to map network drives to a server 2008 R2 box yet they have no problem making a VPN connection and running the SQL software on the same server. Port 445 is the one I am most closely looking at due to NETBIOS needs but I really don’t have a clue. One person can be unable to map a drive letter from their laptop on their home internet, but then use their cellphone as a tethered modem and map it with no problem. Same system same everything else.
I hope one of these helps you, as my problem is still ongoing but the Nirsoft tool is the easiest to use by far and the listed use of grep did give me other information that may be of use to you. The tool from Nirsoft provides an excellent map of all ports in use and plenty of other information. Requires no installation and small enough to keep handy on a flashdrive. Grep or Astrogrep from SourceForge.
Find the PID of a process that uses a port on Windows
My service crash on startup with the classic:
How can I find the process for killing it?
7 Answers 7
Just open a command shell and type (saying your port is 123456):
You will see everything you need.
The headers are:
Find the PID of a process that uses a port on Windows (e.g. port: «9999»)
-a Displays all connections and listening ports.
-o Displays the owning process ID associated with each connection.
-n Displays addresses and port numbers in numerical form.
Then kill the process by PID
/F — Specifies to forcefully terminate the process(es).
Note: You may need an extra permission (run from administrator) to kill some certain processes
Command:
Output:
Now cut the process ID, «10396», using the for command in Windows.
Command:
Output:
If you want to cut the 4th number of the value means «LISTENING» then command in Windows.
Command:
Output:
If you want to do this programmatically you can use some of the options given to you as follows in a PowerShell script:
However; be aware that the more accurate you can be the more precise your PID result will be. If you know which host the port is supposed to be on you can narrow it down a lot. netstat -aon | findstr «0.0.0.0:9999» will only return one application and most llikely the correct one. Only searching on the port number may cause you to return processes that only happens to have 9999 in it, like this:
The most likely candidate usually ends up first, but if the process has ended before you run your script you may end up with PID 12331 instead and killing the wrong process.