- Stay protected with Windows Security
- Important security info
- Understand and customize Windows Security features
- Status icons indicate your level of safety:
- Run a malware scan manually
- Run a quick scan in Windows Security
- Run an advanced scan in Windows Security
- Schedule your own scan
- Schedule a scan
- Turn Microsoft Defender Antivirus real-time protection on or off
- Turn real-time protection off temporarily
- Device protection in Windows Security
- Core isolation
- Memory integrity
- Security processor
- Security processor details
- Secure boot
- Hardware security capability
- Your device meets the requirements for standard hardware security
- Your device meets the requirements for enhanced hardware security
- Your device exceeds the requirements for enhanced hardware security ( Note: In Windows 20H2 this message will say «Your device has all Secured-core PC features enabled»)
- Standard hardware security not supported
- Модель шифрования .NET .NET cryptography model
- Наследование объектов Object inheritance
- Реализация алгоритмов в .NET How algorithms are implemented in .NET
- Конфигурация шифрования Cryptographic configuration
- Выбор алгоритма Choose an algorithm
Stay protected with Windows Security
Windows 10 includes Windows Security, which provides the latest antivirus protection. Your device will be actively protected from the moment you start Windows 10. Windows Security continually scans for malware (malicious software), viruses, and security threats. In addition to this real-time protection, updates are downloaded automatically to help keep your device safe and protect it from threats.
Windows 10 in S mode
Some features will be a little different if you’re running Windows 10 in S mode. Because this mode is streamlined for tighter security, the Virus & threat protection area has fewer options. But don’t worry—the built-in security of this mode automatically prevents viruses and other threats from running on your device, and you’ll receive security updates automatically. For more info, see Windows 10 in S mode FAQ.
Important security info
Windows Security is built-in to Windows 10 and includes an antirvirus program called Microsoft Defender Antivirus. (In previous versions of Windows 10, Windows Security is called Windows Defender Security Center).
If you have another antivirus app installed and turned on, Microsoft Defender Antivirus will turn off automatically. If you uninstall the other app, Microsoft Defender Antivirus will turn back on automatically.
If you’re having problems receiving Windows Security updates, see Fix Windows Update errors and the Windows Update FAQ.
For info on how to uninstall an app, see Repair or remove an app in Windows 10.
To change your user account to an admin account, see Create a local user or administrator account in Windows 10.
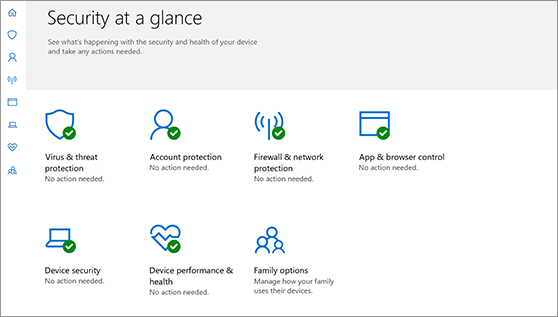
Understand and customize Windows Security features
Windows Security is your home to manage the tools that protect your device and your data:
Virus & threat protection. Monitor threats to your device, run scans, and get updates to help detect the latest threats. (Some of these options are unavailable if you’re running Windows 10 in S mode.)
Account protection. Access sign-in options and account settings, including Windows Hello and dynamic lock.
Firewall & network protection. Manage firewall settings and monitor what’s happening with your networks and internet connections.
App & browser control. Update settings for Microsoft Defender SmartScreen to help protect your device against potentially dangerous apps, files, sites, and downloads. You’ll have exploit protection and you can customize protection settings for your devices.
Device security. Review built-in security options to help protect your device from attacks by malicious software.
Device performance & health. View status info about your device’s performance health, and keep your device clean and up to date with the latest version of Windows 10.
Family options. Keep track of your kids’ online activity and the devices in your household.
You can customize how your device is protected with these Windows Security features. To access them, select Start > Settings > Update & Security > Windows Security . Then select the feature you want to explore.
Open Windows Security settings
Status icons indicate your level of safety:
Green means your device is sufficiently protected and there aren’t any recommended actions.
Yellow means there is a safety recommendation for you.
Red is a warning that something needs your immediate attention.
Run a malware scan manually
When you’re concerned about risks to a specific file or folder, you can right-click the file or folder in File Explorer, then select Scan with Microsoft Defender.
If you suspect there’s malware or a virus on your device, you should immediately run a quick scan. This is much faster than running a full scan on all your files and folders.
Run a quick scan in Windows Security
Select Start > Settings > Update & Security > Windows Security and then Virus & threat protection.
Open Windows Security settings
Under Current threats, select Quick scan (or in previous versions of Windows 10, under Threat history, select Scan now).
If the scan doesn’t find any issues, but you’re still concerned, you may want to check your device more thoroughly.
Run an advanced scan in Windows Security
Select Start > Settings > Update & Security > Windows Security and then Virus & threat protection.
Under Current threats, select Scan options (or in previous versions of Windows 10, under Threat history, select Run a new advanced scan).
Select one of the scan options:
Full scan (check files and programs currently running on your device)
Custom scan (scan specific files or folders)
Microsoft Defender Offline scan (run this scan if your device has been, or could potentially be, infected by a virus or malware). Learn more about Microsoft Defender Offline
Select Scan now.
Note: Because of streamlined security, this process isn’t available if you’re running Windows 10 in S mode.
Schedule your own scan
Even though Windows Security is regularly scanning your device to keep it safe, you can also set when and how often the scans occur.
Schedule a scan
Select the Start button, type schedule tasks in the Search box, and in the list of results, select Task Scheduler.
In the left pane, select the arrow (>) next to Task Scheduler Library to expand it, do the same with Microsoft > Windows, and then scroll down and select the Windows Defender folder.
In the top-center pane, select Windows Defender Scheduled Scan. (Point to the choices to see the full names.)
In the Actions pane on the right, scroll down and then select Properties.
In the window that opens, select the Triggers tab, and then select New.
Set your preferred time and frequency, and then select OK.
Review the schedule and select OK.
Note: Because of streamlined security, this process isn’t available if you’re running Windows 10 in S mode.
Turn Microsoft Defender Antivirus real-time protection on or off
Sometimes you may need to briefly stop running real-time protection. While real-time protection is off, files you open or download won’t be scanned for threats. However, real-time protection will soon turn on automatically again to protect your device.
Turn real-time protection off temporarily
Select Start > Settings > Update & Security > Windows Security and then Virus & threat protection > Manage settings. (In previous versions of Windows 10, select Virus & threat protection > Virus & threat protection settings.)
Open Windows Security settings
Switch the Real-time protection setting to Off and choose Yes to verify.
Note: Because of streamlined security, this process isn’t available if you’re running Windows 10 in S mode.
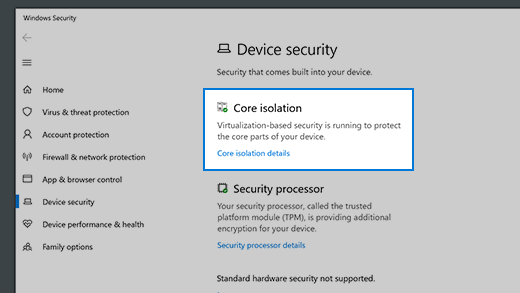
Device protection in Windows Security
Windows Security provides the following built-in security options to help protect your device from malicious software attacks.
To access the features described below, in the search box on the taskbar, type windows security, select it from the results, and then select Device security.
Notes: What you actually see on the Device security page may vary depending upon what your hardware supports.
For more info about Windows Security, see Stay protected with Windows Security.
For more info about Microsoft Defender Firewall, see Turn Microsoft Defender Firewall on or off.
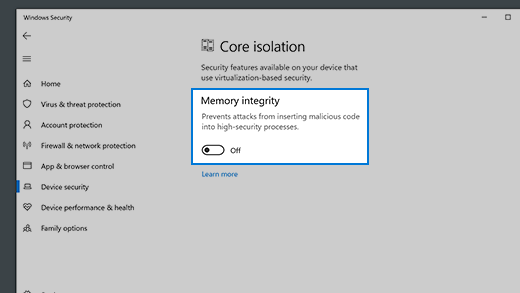
Core isolation
Core isolation provides added protection against malware and other attacks by isolating computer processes from your operating system and device. Select Core isolation details to enable, disable, and change the settings for core isolation features.
Memory integrity
Memory integrity is a feature of core isolation. By turning on the Memory integrity setting, you can help prevent malicious code from accessing high-security processes in the event of an attack.
Security processor
Your security processor provides additional encryption for your device.
Security processor details
This is where you’ll find info about the security processor manufacturer and version numbers, as well as about the security processor’s status. Select Security processor details for additional info and options.
Note: If you don’t see a Security processor entry on this screen then it’s likely that your device doesn’t have the TPM (Trusted Platform Module) hardware necessary for this feature.
If your security processor isn’t working properly you’ll see a link on the Security processor details page that says Security processor troubleshooting. Select it to see any error messages and advanced options. For more information see: Security Processor troubleshooting.
Secure boot
Secure boot prevents a sophisticated and dangerous type of malware—a rootkit—from loading when you start your device. Rootkits use the same permissions as the operating system and start before it, which means they can completely hide themselves. Rootkits are often part of an entire suite of malware that can bypass local logins, record passwords and keystrokes, transfer private files, and capture cryptographic data.
You may have to disable secure boot to run some PC graphics cards, hardware, or operating systems such as Linux or earlier versions of Windows. For more info, see How to disable and re-enable secure boot.
Hardware security capability
At the bottom of the Device security screen, one of the following messages appears, indicating the security capability of your device.
Your device meets the requirements for standard hardware security
This means your device supports memory integrity and core isolation and also has:
TPM 2.0 (also referred to as your security processor)
Secure boot enabled
Your device meets the requirements for enhanced hardware security
This means that in addition to meeting all the requirements of standard hardware security, your device also has memory integrity turned on.
Your device exceeds the requirements for enhanced hardware security ( Note: In Windows 20H2 this message will say «Your device has all Secured-core PC features enabled»)
This means that in addition to meeting all the requirements of enhanced hardware security, your device also has System Management Mode (SMM) protection turned on.
Standard hardware security not supported
This means that your device does not meet at least one of the requirements of standard hardware security.
Improving hardware security
If the security capability of your device isn’t what you’d like it to be, you might need to turn on certain hardware features (such as secure boot, if supported) or change the settings in your system’s BIOS. Contact your hardware manufacturer to see what features are supported by your hardware and how to activate them.
Модель шифрования .NET .NET cryptography model
.NET предоставляет реализации многих стандартных криптографических алгоритмов, и модель шифрования .NET является расширяемой. .NET provides implementations of many standard cryptographic algorithms, and the .NET cryptography model is extensible.
Наследование объектов Object inheritance
Система криптографии .NET реализует расширяемый шаблон наследования производного класса. The .NET cryptography system implements an extensible pattern of derived class inheritance. Иерархия имеет представленный ниже вид. The hierarchy is as follows:
Класс типа алгоритма, например SymmetricAlgorithm , AsymmetricAlgorithm или HashAlgorithm . Algorithm type class, such as SymmetricAlgorithm, AsymmetricAlgorithm, or HashAlgorithm. Этот уровень является абстрактным. This level is abstract.
Класс алгоритма, наследующий от класса типа алгоритма, например Aes, RSA или ECDiffieHellman. Algorithm class that inherits from an algorithm type class; for example, Aes, RSA, or ECDiffieHellman. Этот уровень является абстрактным. This level is abstract.
Реализация класса алгоритма, наследующего от класса алгоритма, например AesManaged, RC2CryptoServiceProvider или ECDiffieHellmanCng. Implementation of an algorithm class that inherits from an algorithm class; for example, AesManaged, RC2CryptoServiceProvider, or ECDiffieHellmanCng. Этот уровень полностью реализован. This level is fully implemented.
Этот шаблон производных классов позволяет добавить новый алгоритм или новую реализацию существующего алгоритма. This pattern of derived classes lets you add a new algorithm or a new implementation of an existing algorithm. Например, чтобы создать новый алгоритм открытого ключа, можно наследовать от класса AsymmetricAlgorithm. For example, to create a new public-key algorithm, you would inherit from the AsymmetricAlgorithm class. Чтобы создать новую реализацию определенного алгоритма, можно создать неабстрактный производный класс этого алгоритма. To create a new implementation of a specific algorithm, you would create a non-abstract derived class of that algorithm.
Реализация алгоритмов в .NET How algorithms are implemented in .NET
В качестве примера различных реализаций, доступных для алгоритма, рассмотрим симметричные алгоритмы. As an example of the different implementations available for an algorithm, consider symmetric algorithms. Основой для всех симметричных алгоритмов является SymmetricAlgorithm , которая наследуется Aes , TripleDES и другие, которые больше не рекомендуются. The base for all symmetric algorithms is SymmetricAlgorithm, which is inherited by Aes, TripleDES, and others that are no longer recommended.
В платформа .NET Framework в Windows: In .NET Framework on Windows:
- *CryptoServiceProvider классы алгоритмов, такие как AesCryptoServiceProvider , являются оболочками для реализации алгоритма с помощью API шифрования Windows (CAPI). *CryptoServiceProvider algorithm classes, such as AesCryptoServiceProvider, are wrappers around the Windows Cryptography API (CAPI) implementation of an algorithm.
- *Cng классы алгоритмов, такие как ECDiffieHellmanCng , являются оболочками для реализации Windows криптографии следующего поколения (CNG). *Cng algorithm classes, such as ECDiffieHellmanCng, are wrappers around the Windows Cryptography Next Generation (CNG) implementation.
- *Managed классы, такие как AesManaged , полностью записываются в управляемом коде. *Managed classes, such as AesManaged, are written entirely in managed code. *Managed реализации не сертифицированы Федеральным стандартом обработки информации (FIPS) и могут быть медленнее, чем *CryptoServiceProvider классы- *Cng оболочки. *Managed implementations are not certified by the Federal Information Processing Standards (FIPS), and may be slower than the *CryptoServiceProvider and *Cng wrapper classes.
В .NET Core и .NET 5 и более поздних версиях все классы реализации ( *CryptoServiceProvider , *Managed и *Cng ) являются оболочками для алгоритмов операционной системы (ОС). In .NET Core and .NET 5 and later versions, all implementation classes ( *CryptoServiceProvider , *Managed , and *Cng ) are wrappers for the operating system (OS) algorithms. Если алгоритмы ОС сертифицированы по стандарту FIPS, .NET использует алгоритмы, сертифицированные FIPS. If the OS algorithms are FIPS-certified, then .NET uses FIPS-certified algorithms. Дополнительные сведения см. в статье кросс-платформенное шифрование. For more information, see Cross-Platform Cryptography.
В большинстве случаев нет необходимости напрямую ссылаться на класс реализации алгоритма, например AesCryptoServiceProvider . In most cases, you don’t need to directly reference an algorithm implementation class, such as AesCryptoServiceProvider . Обычно нужные методы и свойства находятся в классе базового алгоритма, например Aes . The methods and properties you typically need are on the base algorithm class, such as Aes . Создайте экземпляр класса реализации по умолчанию, используя фабричный метод в классе базового алгоритма и обратитесь к классу базового алгоритма. Create an instance of a default implementation class by using a factory method on the base algorithm class, and refer to the base algorithm class. Например, см. выделенную строку кода в следующем примере: For example, see the highlighted line of code in the following example:
Конфигурация шифрования Cryptographic configuration
Конфигурация криптографии позволяет разрешать определенную реализацию алгоритма в имя алгоритма, обеспечивая расширяемость классов шифрования .NET. Cryptographic configuration lets you resolve a specific implementation of an algorithm to an algorithm name, allowing extensibility of the .NET cryptography classes. Вы можете добавить свою собственную аппаратную или программную реализацию алгоритма и сопоставить ее с необходимым именем алгоритма. You can add your own hardware or software implementation of an algorithm and map the implementation to the algorithm name of your choice. Если алгоритм не задан в файле конфигурации, используются параметры по умолчанию. If an algorithm is not specified in the configuration file, the default settings are used.
Выбор алгоритма Choose an algorithm
Алгоритм можно выбирать, исходя из различных причин, например для обеспечения целостности данных, для обеспечения конфиденциальности данных или для создания ключа. You can select an algorithm for different reasons: for example, for data integrity, for data privacy, or to generate a key. Симметричные и хэш-алгоритмы предназначены для защиты данных от нарушения целостности (защита от изменения) или конфиденциальности (защита от просмотра). Symmetric and hash algorithms are intended for protecting data for either integrity reasons (protect from change) or privacy reasons (protect from viewing). Хэш-алгоритмы используются в основном для обеспечения целостности данных. Hash algorithms are used primarily for data integrity.
Ниже приведен список рекомендуемых алгоритмов в зависимости от приложения. Here is a list of recommended algorithms by application: