- RDS Shadow – подключаемся к сессии пользователя в Windows 2012 R2
- Remote Desktop Shadow — работа в GUI
- RDS Shadow из Powershell
- Shadowing RDS connections in Windows 2012 R2
- Shadowing RDS 2012 Sessions
- RDS GUI Shadowing:
- PowerShell RDS Shadowing:
- Share This Article :
- Like this:
- Related
- Published by Ryan Mangan
- 3 thoughts on “ Shadowing RDS 2012 Sessions ”
- Add yours
- Leave a Reply Cancel reply
RDS Shadow – подключаемся к сессии пользователя в Windows 2012 R2
Спешим поделиться хорошей новостью: Microsoft вернула функционал Remote Desktop Shadowing в Windows Server 2012 R2 и Windows 8.1! Напомним, что режим Shadow (теневой сеанс) – может использовать администратором для просмотра и управления активной терминальной сессией любого пользователя. Этот режим работы поддерживается практически с первых версий терминального сервера Microsoft и неожиданно был убран в релизе Windows Server 2012 (связано с переносом стека rdp из режима ядра в пользовательский режим).
Кроме того, у режима RD Shadow и rdp клиента появился ряд новых интересных возможностей. Полный список опций rdp клиента mstsc.exe, определяющих возможность удаленного подключения к сессии конечного пользователя:
Mstsc.exe [/shadow:sessionID [/v:Servername] [/control] [/noConsentPrompt]]
/shadow:ID – подключится к терминальной сессии с указанным ID
/v:servername – имя терминального сервера (если не задано, используется текущий)
/control – возможность взаимодействия с сеансом пользователя (если не указано, используется режим просмотра сессии пользователя).
/noConsentPrompt – не запрашивать у пользователя подтверждение на подключение к сессии
Ограничения теневых сеансов RDS в Windows 2012 R2
- Подключаться к чужим сессиям может только администратор сервера. Делегировать эти права обычным пользователем нельзя
- RDS Shadow не будет работать в сетях на базе рабочих групп
Remote Desktop Shadow — работа в GUI
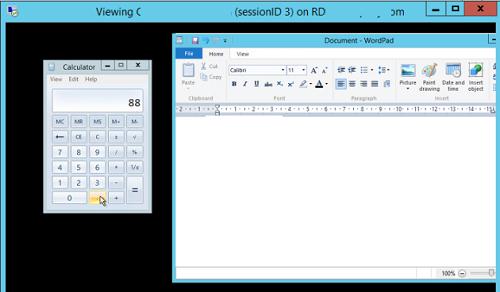
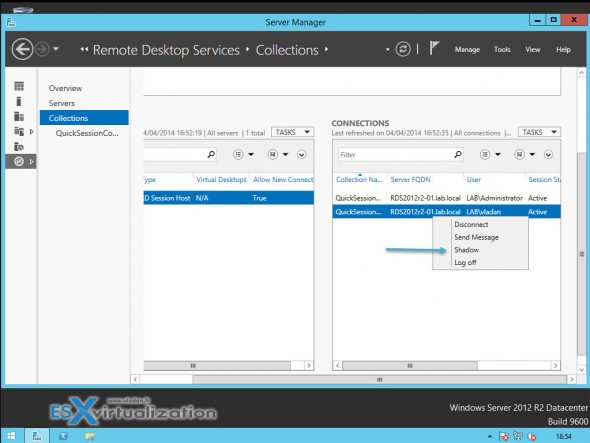
Подключиться к сессии пользователя можно с помощью утилиты mstsc.exe или непосредственно из консоли Server Manager. Для этого в консоли Server Manager откройте коллекцию QuickSessionCollection.
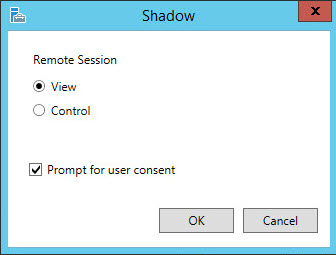
Появится окно параметров теневого подключения. Возможен просмотр (View) и управление (Control) сессией. Кроме того можно включить опцию Prompt for user consent (запросить согласие на подключение у пользователя).
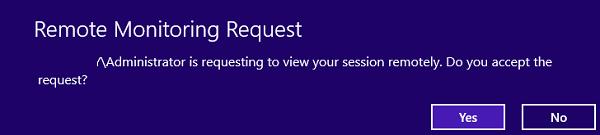
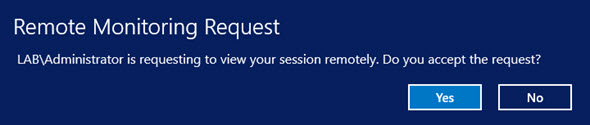
Если выбрана опция «Запросить подтверждение», в сессии у пользователя появится запрос:
Winitpro\administrator is requesting to view your session remotely. Do you accept the request?
Если пользователь подтвердит, подключение, администратор увидит его рабочий стол и сможет взаимодействовать с ним.
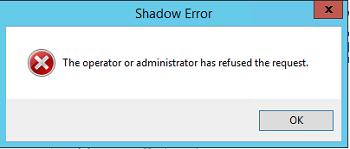
Если же пользователь отклонит подключение, появится окно:
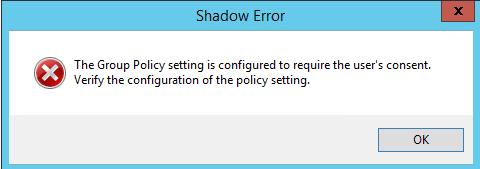
Если же попытаться подключится к сессии пользователя без запроса подтверждения, появится ошибка, сообщающая что такое поведение настроено групповой политикой:
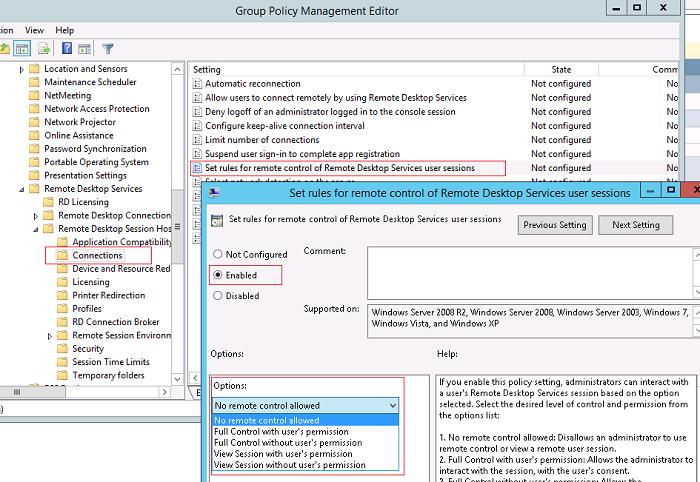
Параметры удаленного управлениями терминальными сессиями пользователя настраиваются политиками Set rules for remote control of Remote Desktop Services user sessions, которые находится в разделе Policies -> Administrative Templates -> Windows components -> Remote Desktop Services -> Remote Session Host -> Connections в пользовательской и «компьютерной» секциях GPO.
Этой политикой можно настроить следующие варианты подключения по RD Shadow:
- No remote contol allowed — удаленное управление запрещено
- Full Control with users’s permission — полный контроль с разрешения пользователя
- Full Control without users’s permission — полный контроль без разрешения пользователя
- View Session with users’s permission – наблюдение за сеансом с подтверждением
- View Session without users’s permission – наблюдение за сеансом без подтверждения
RDS Shadow из Powershell
Воспользоваться функционалом Remote Desktop Services Shadow можно и из Powershell.
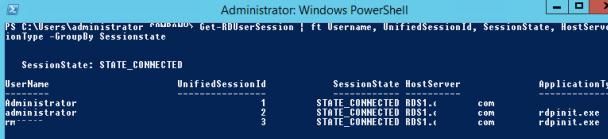
В первую очередь покажем, как получить список сессий на терминальном сервере (сесии пользователей будут сгруппированы в группы в зависимости от их статуса):
На данном сервере мы обнаружили три активных терминальных сессии. Подключимся к сессии пользователя с ID сессии 3:
Shadowing RDS connections in Windows 2012 R2
By Vladan SEGET | Last Updated: April 9, 2014
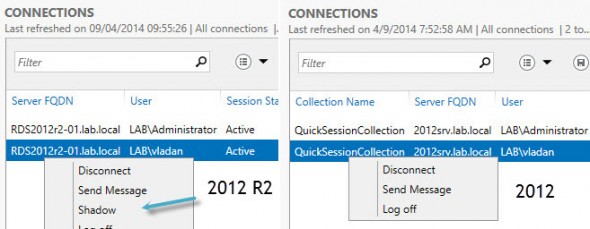
Some sources reported that Microsoft has removed the possibility to shadow RDS connections in Windows 2012, but then put it back in the Windows 2012 R2 release. I quickly checked in my lab on two VMs, but saw that both versions of Windows Server 2012 allows that .
I double checked that and unfortunately the statement was true. Check out the image below showing Windows 2012 R2 on the left and 2012 on the right. Clearly we can see the shadow menu option in the R2 release.
I thought that it might interest someone, that’s why this post. Shadowing RDS connections was here since ages. the feature was present in previous releases of Windows servers, like 2003 or 2008. This Shadowing feature allows the help desk personnel follow a remote user in shadow session (view or control mode).
In simple all-in-one server deployments, for testing or smaller site deployments, the RDS deployment options are very simple. It’s actually a two step process. I’ll show you where to find the options, but basically as being said for simple deployments you’ll need first:
- Join the server to the domain if it has not been joined already.
- Go to Server Manager > Add roles and features > RDS Installation > Quick start > Session-based desktop deployment > finish wizard.
You have then 180 days to worry about licensing.
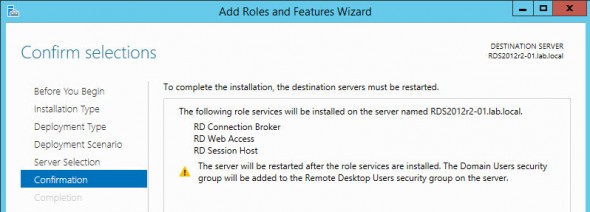
Here is a confirmation screen:
You’ll need to reboot the server to complete the installation…
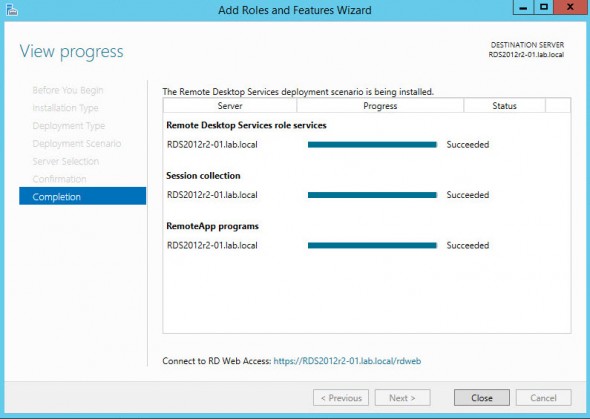
In my situation, after the reboot the installation continues.
Then the RDS > collections > you’ll see the option …
There is still the option (can be unchecked) to ask user for a permission. This is usually necessity…
When doing a right click you’ll see the Shadow option there.
Easy and built-in.
The Quick start option is quite useful and handy for quick prototyping in lab environment or for smaller one-server deployments. Quick Start is an option in RDS deployment during the process of adding roles and features with Windows Server 2012 Service Manager. You can still add add additional RDS servers as needed.
You can be up and running in minutes.
Good to know that as an administrator you can also override the behaviour through the GPO. The group policy in this case must be set to allow shadowing without user permission.
You’ll find the shadow group policies in the following path (gpedit.msc):
[ |
\Administrative Templates\Windows Components\Remote Desktop Services
\Remote Desktop Session Host\Connections
\Set rules for remote control of Remote Desktop Services user sessions
Shadowing RDS 2012 Sessions
Server 2012 R2 Remote Desktop Services brings a new feature called shadowing, which allows administrators to view sessions.
This can be done through the GUI or through the use of Command Line.
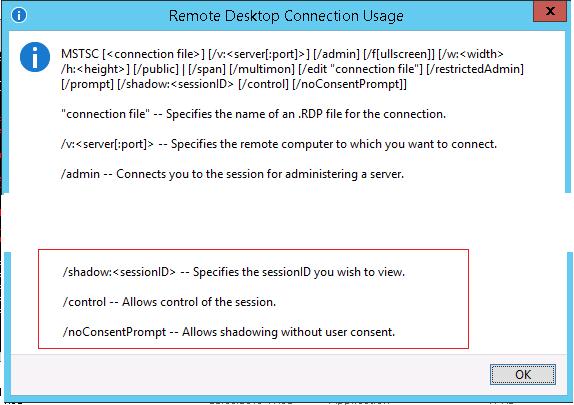
As you can see from the MSTSC Connection Usage help Window, there are three new commands that we can use for connecting to end user sessions. There are two types of Shadowing ( view & control) and the option to select “No Consent” which means you don’t need the end user’s approval/permission before connecting to their session.
Here is the command line for Shadowing:
Mstsc.exe [/shadow:sessionID [/v:Servername] [/u:[Username]] [/control] [/noConsentPrompt]]
/shadow:ID Starts shadow with the specified sessionID.
/v:servername If not specified, will use the current server as the default.
/u:username If not specified, the currently logged on user is used.
/control If not specified, will only view the session.
/noConsentPrompt Attempts to shadow without prompting the shadowee to grant permission.
RDS GUI Shadowing:
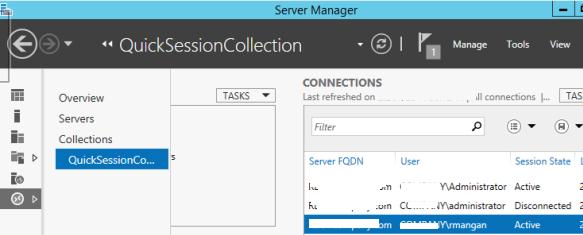
As you can see from the screenshot provided above, there are three users showing in the connections task pane. By right clicking on the user, you will be presented with the following options:
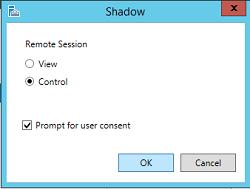
Select Shadow and you will be presented with a Shadowing options box.
As mentioned earlier, you have the option of viewing , controlling and prompting for user consent. For this example we are going view and request the users permission to shadow their screen.
Once the request has been sent, you will see the Remote Desktop Connection loading box.
The requester will see this box until the end user actions the request.
If the end user refuses the connection, you will see the above error.
When the user selects yes, you will then be able to view their screen.
As you can see from the screenshot, we are now viewing the user’s screen.
If we try and access the User’s session with out their permission, we are presented with the following error message.
This is an out of the box feature and to disable it, you will need to apply a Group policy.
The Group Policy that needs to be changed is located under Administrative Templates>Windows components>Remote Desktop Services>Remote Session Host>Connections. “Set rules for remote control of Remote Desktop Services user sessions”
This can be applied as a user or computer policy.
PowerShell RDS Shadowing:
To shadow User sessions using PowerShell, we first need to Find the session ID’s of our users.
For this I will use the following:
The following Cmd organises User Active and Disconnected RDS sessions. This is also useful for reporting.
Once you have obtained the Session ID’s , you can then connect to that session.
If you don’t want to request the user’s permission add the /noconsentprompt
Share This Article :
Like this:
Related
Published by Ryan Mangan
Ryan Mangan works as the CTO at AppCURE based in the UK. AppCURE specialises in Application packaging, App migration and Application packaging/delivery automation. Ryan is an end-user computing specialist with a great passion for Technology with a specific focus on Virtualisation and Cloud. A speaker and presenter, he has helped customers and technical communities with end-user computing solutions, ranging from small to global 30,000-user deployments. He is the owner and author of ryanmangansitblog.com, where he posts articles about remote desktop services, VMware, Microsoft Azure, Parallels RAS, KEMP, Application Packaging and other products and technologies. Ryan has been awarded VMware vExpert since 2014, has been a member of the NetApp United program since 2017, Parallels VIPP, and was awarded Technical Person of the Year in 2017 by KEMP Technologies. Subject Matter Expert with Remote Desktop Services and Windows Virtual Desktop. Ryan is the author of the Microsoft Ebook «Quickstart Guide to Windows Virtual Desktop» and the Ebook «A introduction to MSIX app attach» View all posts by Ryan Mangan
3 thoughts on “ Shadowing RDS 2012 Sessions ”
Add yours
Whenever I setup the shadowing via Group policy the shadowing feature is reset after each use. For instance when an administrator logs on and connects with another user using the shadowing feature it works. As soon as the shadowing session ends the shadowing feature is no longer available for use unless the server is restarted. How can I keep the shadowing feature turned on? What is making it disconnect after each session?
it sounds like a issue with the server. Have you reviewed the logs, is the server patched up to date ?
Ryan, we have an issue where some of our RDSH servers never get a UnifiedSessionID for the user who logged on. This just started happening in the past few months. Servers that work seem to always work, but especially new servers (built from the same image) never get a UnifiedSessionID for the user registered in the database. I have looked online and seen others with this problem but nobody with a resolution.
Leave a Reply Cancel reply
This site uses Akismet to reduce spam. Learn how your comment data is processed.