- Configuring Windows Firewall Settings and Rules with Group Policy
- Group Policy Settings to Manage Windows Defender Firewall Rules
- How to Enable Windows Firewall Using GPO?
- How to Create a Firewall Rule Using GPO?
- Testing Windows Firewall Policies on Clients
- How to Import/Export Windows Firewall Rules to/from GPO?
- Domain and Local Windows Defender Firewall Rules
- Tips: Managing Windows Firewall with GPOs
- Управление групповой политикой Защитник Windows брандмауэра Group Policy Management of Windows Defender Firewall
- Windows server gpo firewall
- Answered by:
- Question
- Answers
- All replies
Configuring Windows Firewall Settings and Rules with Group Policy
Windows Firewall allows to restrict inbound/outbound network traffic for a certain application, protocol or a TCP/IP port. This is an easy way to restrict network access to/from user workstations or servers. You can configure Windows Firewall rules individually on each computer or, if a user computer is joined to an Active Directory domain, an administrator can manage Windows Defender Firewall settings and rules using GPO.
In large enterprises, the port filtering rules are usually set at the level of routers, L3 switches or dedicated firewall devices. However, nothing prevents you from deploying your Windows Firewall network access restriction rules to workstations or Windows servers.
Group Policy Settings to Manage Windows Defender Firewall Rules
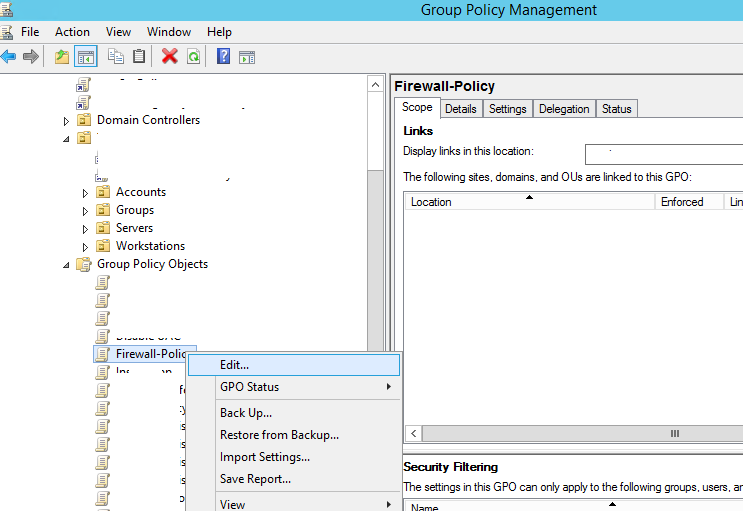
Using the domain group policy editor (Group Policy Management console – gpmc.msc), create a new GPO object (policy) with the name Firewall-Policy and switch to the edit mode.
There are two sections in the Group Policy Management console that allow you to manage firewall settings:
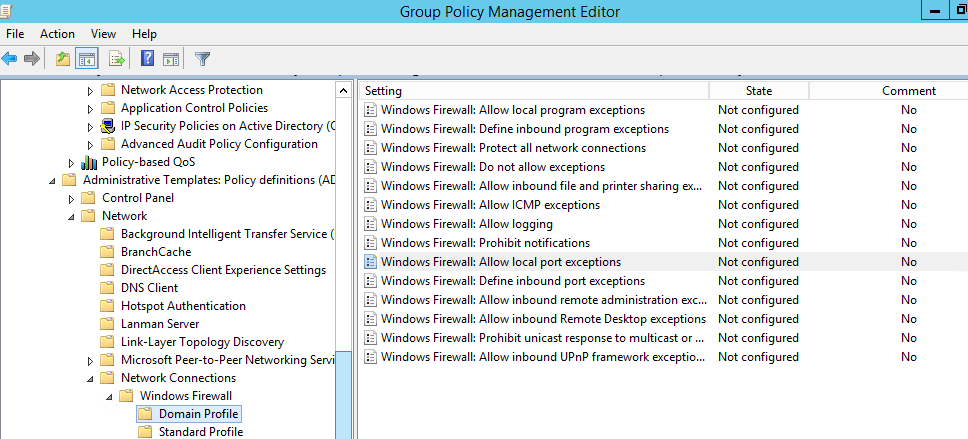
- Computer Configuration -> Administrative Templates -> Network -> Network Connections -> Windows Firewall – this GPO section was used to configure firewall rules in OS Vista/Windows Server 2008 or earlier. If you don’t have any computers with these old OS versions, use the next policy section to configure your firewall;
- Computer Configuration -> Windows Settings -> Security Settings -> Windows Firewall with Advanced Security – is the actual section to configure Windows Firewall in modern Windows OS versions, and its interface is similar to that of the local Defender Firewall management console.
How to Enable Windows Firewall Using GPO?
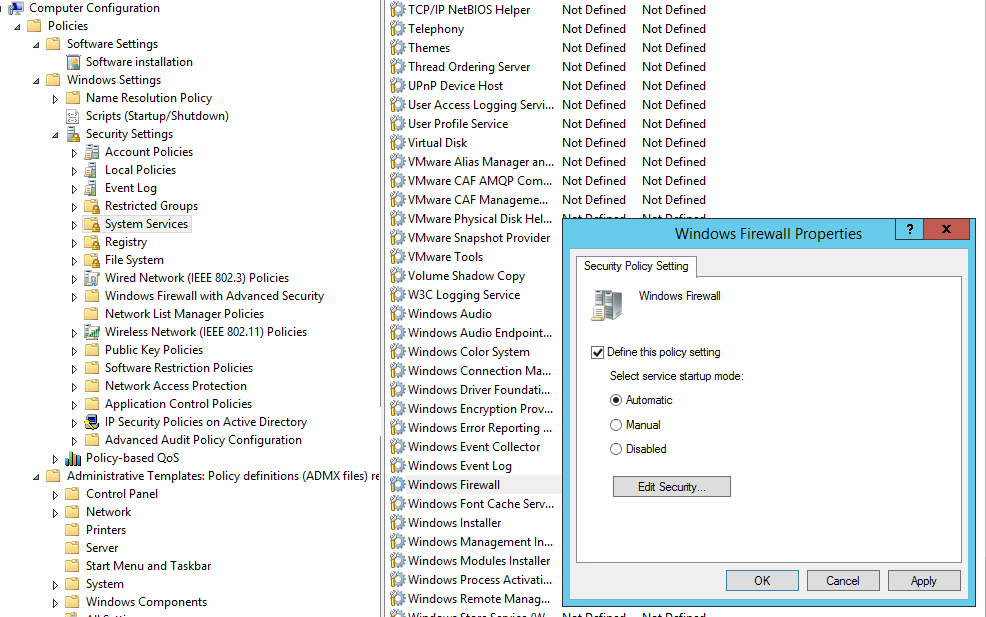
In order users (even having local admin permissions) cannot stop the firewall service, it is recommended to configure the automatic startup of Windows Firewall using GPO. To do it, go to Computer Configuration- > Windows Settings -> Security Settings -> System Services. Find Windows Firewall in the list of services and change the startup mode to automatic (Define this policy setting -> Service startup mode Automatic). Make sure that your users don’t have the permissions to stop the service.
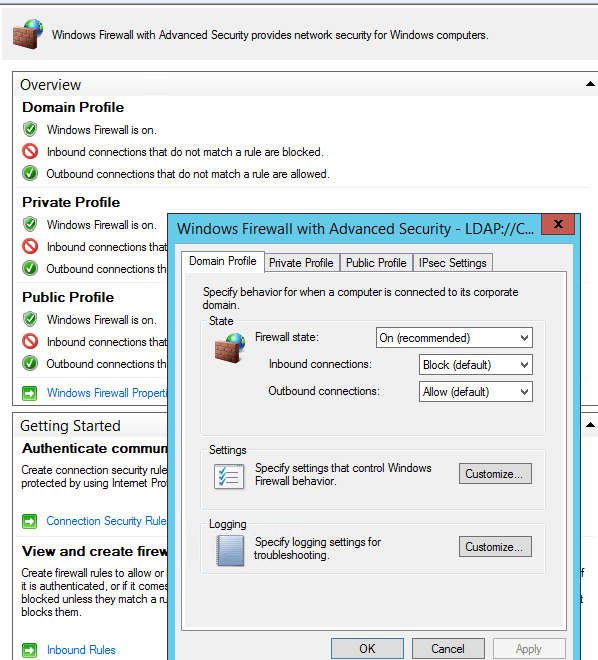
Go to the Computer Configuration -> Windows Settings -> Security Settings section in the GPO console. Right-click Windows Firewall with Advanced Security and open the properties.
Change the Firewall state to On (recommended) in all three tabs: Domain Profile, Private Profile and Public Profile (What are network locations in Windows?). Depending on the security policies in your company, you can specify that all inbound connections are blocked by default (Inbound connections -> Block), and outbound connections are allowed (Outbound connections -> Allow). Save the changes.
How to Create a Firewall Rule Using GPO?
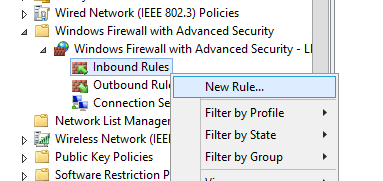
Let’s try to create an allowing inbound Windows Firewall rule. For example, we want to allow the incoming RDP connection to all computers (TCP 3389 port). Right-click the Inbound Rules section and select New Rule.
The firewall rule wizard has an interface similar to that of local Windows Firewall on the user’s desktop computer.
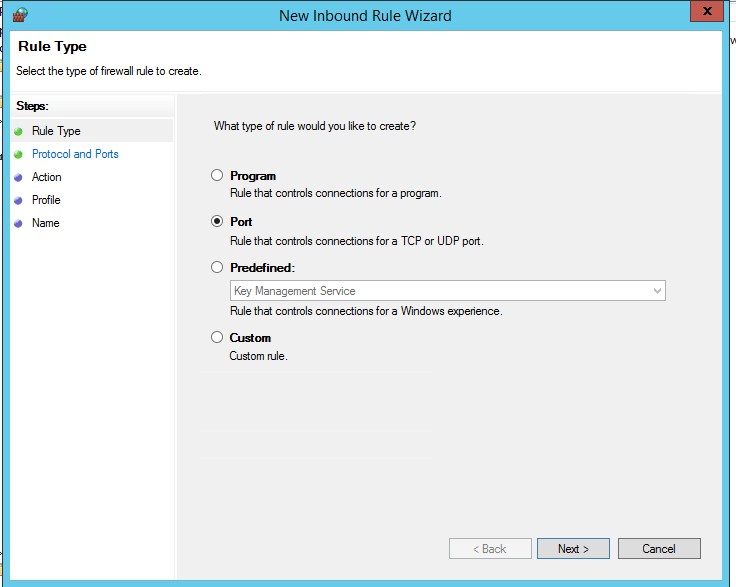
Select the rule type. You can allow access to:
- Program – you can select a program executable (.exe);
- Port – you can select a TCP/UDP port or a port range;
- Predefined – you can select one of the standard Windows rules, which already contain access rules (both executable files and ports are described) to typical services (e. g., AD, HTTP(s), DFS, BranchCache, remote restart, SNMP, KMS, etc.);
- Custom – here you can specify a program, a protocol (protocols other than TCP or UDP, like ICMP, GRE, L2TP, IGMP, etc.), client IP addresses or entire IP subnets.
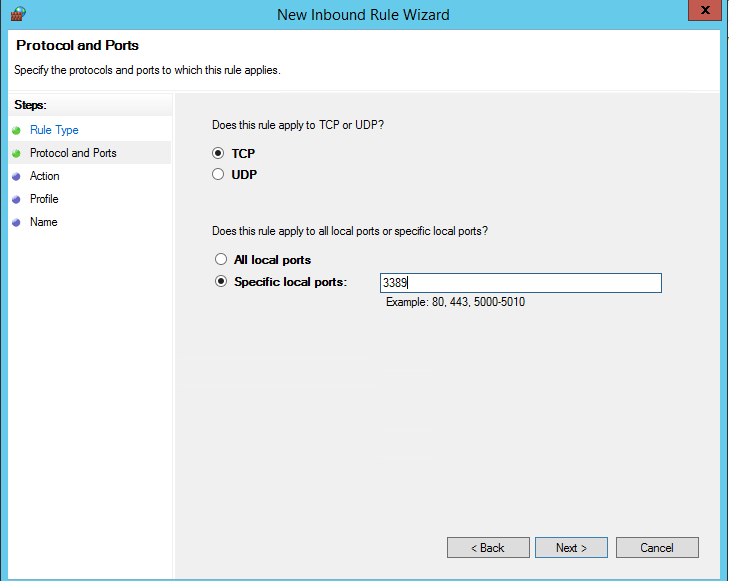
In our case, we’ll select the Port rule. Let’s specify TCP as the protocol, and Port 3389 as the port (it is the default RDP port, but you can change it via the registry).
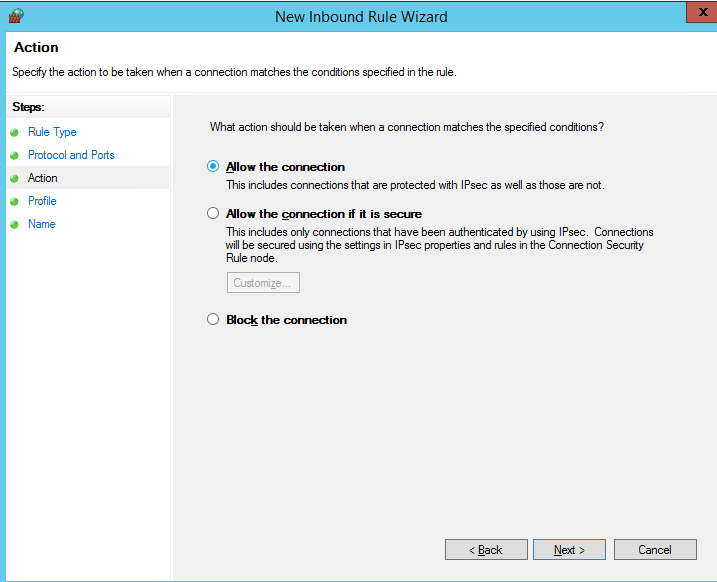
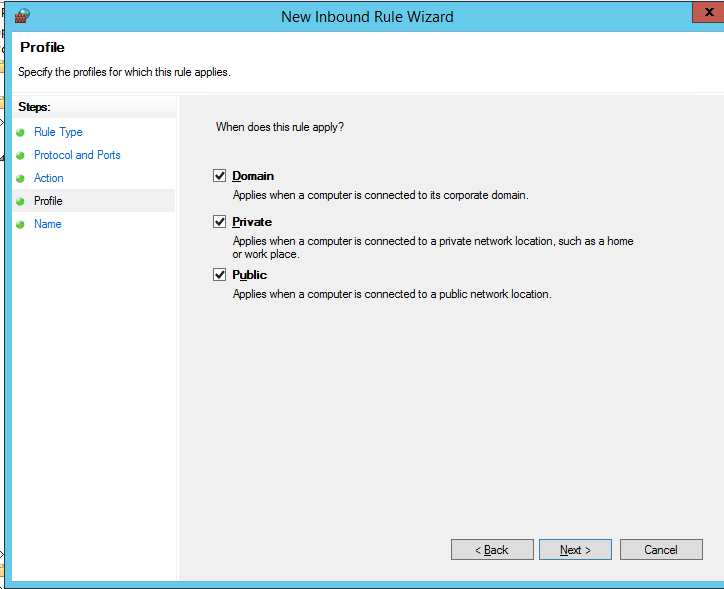
Then you must select what to do with such a network connection: Allow the connection, allow if it is secure or Block the connection.
Then select the firewall profiles to apply the rule to. You can leave all profiles enabled (Domain, Private and Public).
On the last step, specify the name and description of the rule. Click Finish, and it will appear in the list of firewall rules.
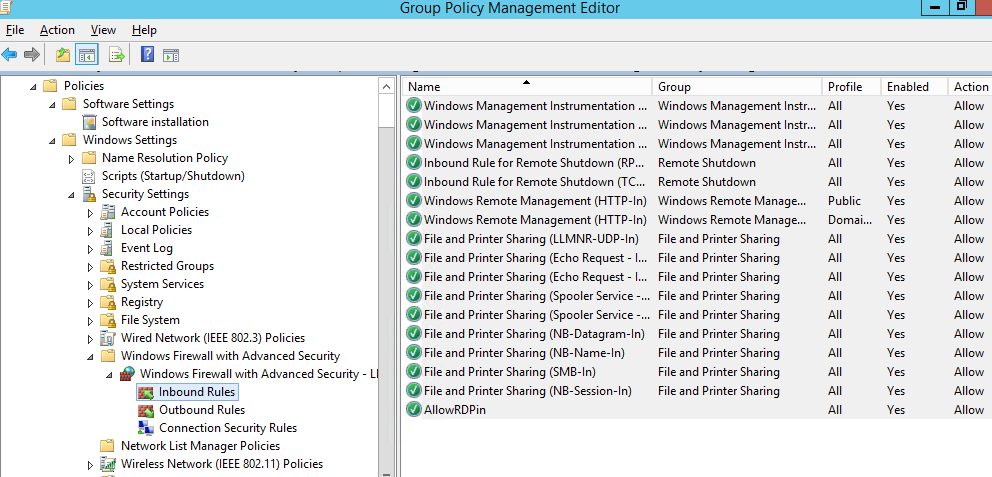
In the same way you can configure other rules for the inbound traffic to be applied to your Windows clients.Don’t forget to create rules for the inbound and outbound traffic.
Now just assign the Firewall Policy to the OU with user computers.
Testing Windows Firewall Policies on Clients
Update the group policy settings on your clients (gpupdate /force). Make sure that the ports you have specified are available on user computers (you can use Test-NetConnection cmdlet or Portqry tool).
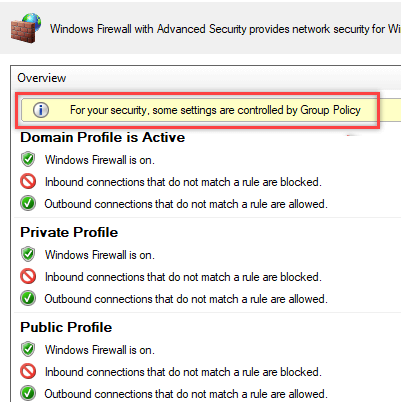
On a user PC, open the Control Panel -> System&Security -> Windows Defender Firewall and make sure that there is the message For your security, some settings are controlled by Group Policy and your firewall settings are used.
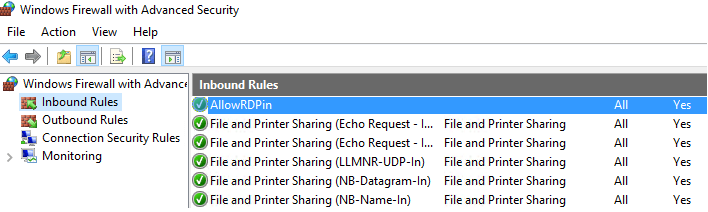
Now a user cannot change firewall settings, and all rules that you have created must appear in the Inbound Rules list.
You can also display the firewall settings using this command:
netsh firewall show state
How to Import/Export Windows Firewall Rules to/from GPO?
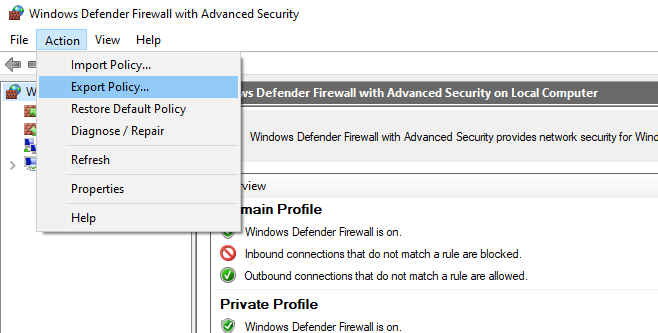
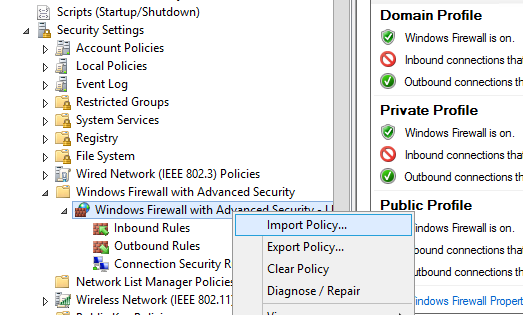
Of course, the process of creating Windows Firewall rules is a painstaking and time consuming task (however, it is worth the effort). To make it easier, you can import/export Windows Firewall settings. To do it, it’s enough to configure local firewall settings on a reference workstation as you need. Then go to the root of Windows Firewall snap-in (Windows Firewall with Advanced Security) and select Action -> Export Policy.
The policy will be exported into a WFW file, which can be imported to the Group Policy Management Editor by selecting Import Policy option and specifying the path to the .wfw file (the current policy settings will be overwritten).
Domain and Local Windows Defender Firewall Rules
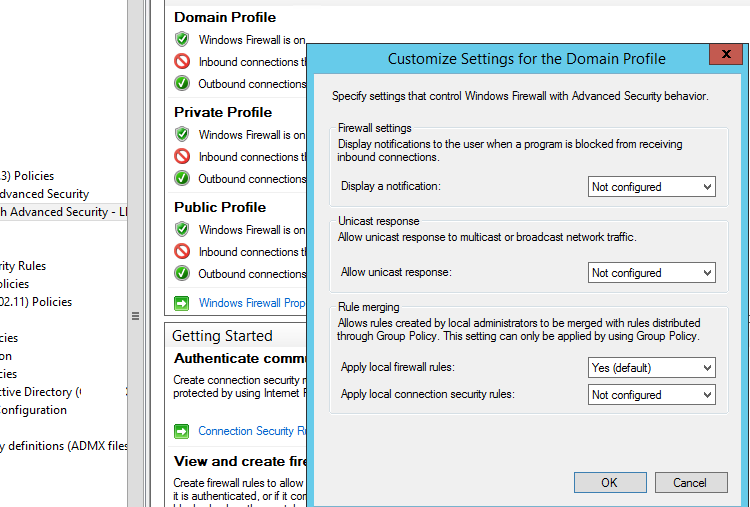
Depending on whether you want that local administrators can create their own firewall rules on their computers to be combined with the rules obtained from the group policy, you can select the rule merging option. Open the policy properties and view the settings in the Rule merging section. By default rule merging is enabled. You can force that a local administrator can create their own firewall rules: select Yes (default) in the Apply local firewall rules option.
Tips: Managing Windows Firewall with GPOs
Of course, you should create separate policies to manage Windows Firewall rules for servers and workstations (you may have to create separate policies for each group of similar servers depending on their role). It means that firewall rules for the domain controller, an Exchange mail server and an SQL server will differ.
You can find what ports must be opened for each service on the vendor’s website. The process is quite painstaking and complicated at the first glance. However, you can finally get a working Windows Firewall configuration that allows only approved network connections and blocks other ones. From my experience, I’d like to note that you can quickly find the list of used TCP/UDP ports for Microsoft software.
Управление групповой политикой Защитник Windows брандмауэра Group Policy Management of Windows Defender Firewall
Область применения Applies to
- Windows 10 Windows 10
- Windows Server 2016 Windows Server 2016
Чтобы открыть GPO для Защитник Windows брандмауэра: To open a GPO to Windows Defender Firewall:
Откройте консоль управления групповыми политиками. Open the Group Policy Management console.
В области навигации разместите «Лес: имя»,«Домены», «Имя домена», «Объекты групповой политики», щелкните правой кнопкой мыши объект групповой политики, который нужно изменить, и выберите ****»Изменить». **** ** **** In the navigation pane, expand Forest: YourForestName, expand Domains, expand YourDomainName, expand Group Policy Objects, right-click the GPO you want to modify, and then click Edit.
В области навигации редактора объектов групповой **** политики перейдите к сетевому подключению конфигурации компьютера административных шаблонов сети Защитник Windows > **** > **** > **** > брандмауэра. In the navigation pane of the Group Policy Object Editor, navigate to Computer Configuration > Administrative Templates > Network > Network Connections > Windows Defender Firewall.
Windows server gpo firewall
This forum has migrated to Microsoft Q&A. Visit Microsoft Q&A to post new questions.
Answered by:
Question
I am using server 2008 Standard Edition as a Domain controller. I want to Disable firewall on clients and prevent users from changing firewall settings. I have checked the Policy in computer configuration but I did not understand how to fulfill my requirement. Please, help me in this matter so I can disable firewall on client machines using group policies.
Thank You
Abdul Shakoor
Answers
Follow the patch that i gave you
Computer Config > Administrative Templates > Network > Network connections > Windows Firewall > Domain Profile > Windows Firewall: Protect all network connections = Disabled
After that go to client machine;
Start > Run > CMD > Gpupdate /force
Check the Firewall in Control Panel should be disable Thiago Pereira | http://thiagoinfrat.spaces.live.com | http://www.winsec.org
All replies
Create a GPO and set under Computer Config > Administrative Templates > Network > Network connections > Windows Firewall > Domain Profile . Here is where you can set firewall stuff.
After that, start the client machine.
Hope it Helps Thiago Pereira | http://thiagoinfrat.spaces.live.com | http://www.winsec.org
Thanks I have checked all of these policies but I can’t find which policy I have to implement for these requirements:
1. Disable firewall on clients
2. Prevent users from changing firewall settings.
Hope you help me
Follow the patch that i gave you
Computer Config > Administrative Templates > Network > Network connections > Windows Firewall > Domain Profile > Windows Firewall: Protect all network connections = Disabled
After that go to client machine;
Start > Run > CMD > Gpupdate /force
Check the Firewall in Control Panel should be disable Thiago Pereira | http://thiagoinfrat.spaces.live.com | http://www.winsec.org
The same problem, pls help
i am curious about something in this; you guys keep saying the domain firewall. theres also a section for local firewall.
well i have TMG on my network and isnt playing with the domain going to disable the firewall completely? why not the local firewall setting?
COmputer COnfiguration > Windows Settings > Security Settings > Windows Firewall with Advanced Security.
This will allow you to enable or disable the FW policy.
Sorry for digging this subject again after a while.
I am curious about the reason why we need to disable the firewall of machines on our local network. Isn’t this causing a security risk of an internal breach ? and can’t we select the local domain setting of the firewall ?
I tried to search for a reason but couldn’t.
I manage a windows domain and am curious about this.
Thanks in advance.
Well, if they’re like me. they run McAfee’s firewall and it’s ‘no bueno’ to have more than one firewall.
This GPO links to the Firewall Settings, it can’t be applied via GPO Pack because you can’t export these settings.
Computer Configuration > Windows Settings > Security Settings > Windows Firewall with Advanced Security.
It seems thiugh everyone is providing steps to setting up the policy but I think the user needs to know how and where.
Before you can edit a gpo you need to create and link a gpo to an AD containiner/OU or link it to the entire Domain by editing the Default Domain Policy. Once you have decided where you would like to apply the new gpo, then you can right click the container/OU and «Edit and Link a GPO here» or right click an exisitng gpo and choose Edit. This will put you in to gpo edit mode where yo can follow the instruction provided in the previous answers. I hope this helps.