- Deploy Access-Denied Assistance (Demonstration Steps)
- Step 1: Configure access-denied assistance
- To configure access-denied assistance by using Group Policy
- To configure access-denied assistance by using File Server Resource Manager
- To configure access-denied assistance for all file types by using Group Policy
- To specify a separate access-denied message for a shared folder by using File Server Resource Manager
- Step 2: Configure the email notification settings
- Step 3: Verify that access-denied assistance is configured correctly
- Access Denied when running Windows Service
- How to troubleshoot Active Directory replication error 5 in Windows Server: Access is denied
- Symptoms
- Symptom 1
- Symptom 2
- Symptom 3
- Symptom 4
- Symptom 5
- Workaround
- Causes and solutions
- Cause 1: The RestrictRemoteClients setting in the registry has a value of 2
- Cause 2: The CrashOnAuditFail setting in the registry of the destination domain controller has a value of 2
- Cause 3: Invalid trust
- Cause 4: Excessive time skew
- Cause 6: The «Access this computer from network» user right isn’t granted to a user who triggers replication
- Cause 7: There’s an SMB signing mismatch between the source and destination domain controllers
- Cause 8: UDP-formatted Kerberos packet fragmentation
- Cause 9: Network adapters have the Large Send Offload feature enabled
- Cause 10: Invalid Kerberos realm
- Solution for the incorrect KDCNames registry entry
- Solution for mismatching PolAcDmN and PolPrDmN registry keys
- Cause 11: There’s a LAN Manager Compatibility (LM Compatibility) mismatch between the source and destination domain controllers
- Cause 12: Service principal names are either not registered or not present because of simple replication latency or a replication failure
- Cause 13: Antivirus software uses a mini-firewall network adapter filter driver on the source or destination domain controller
- Status
- More information
- Sample output from DCDIAG /TEST:CheckSecurityError
Deploy Access-Denied Assistance (Demonstration Steps)
Applies To: Windows Server 2016, Windows Server 2012 R2, Windows Server 2012
This topic explains how to configure access-denied assistance, and verify that it is working properly.
In this document
This topic includes sample Windows PowerShell cmdlets that you can use to automate some of the procedures described. For more information, see Using Cmdlets.
Step 1: Configure access-denied assistance
You can configure access-denied assistance within a domain by using Group Policy, or you can configure the assistance individually on each file server by using the File Server Resource Manager console. You can also change the access-denied message for a specific shared folder on a file server.
You can configure access-denied assistance for the domain by using Group Policy as follows:
To configure access-denied assistance by using Group Policy
Open Group Policy Management. In Server Manager, click Tools, and then click Group Policy Management.
Right-click the appropriate Group Policy, and then click Edit.
Click Computer Configuration, click Policies, click Administrative Templates, click System, and then click Access-Denied Assistance.
Right-click Customize message for Access Denied errors, and then click Edit.
Select the Enabled option.
Configure the following options:
In the Display the following message to users who are denied access box, type a message that users will see when they are denied access to a file or folder.
You can add macros to the message that will insert customized text. The macros include:
[Original File Path] The original file path that was accessed by the user.
[Original File Path Folder] The parent folder of the original file path that was accessed by the user.
[Admin Email] The administrator email recipient list.
[Data Owner Email] The data owner email recipient list.
Select the Enable users to request assistance check box.
Leave the remaining default settings.
Windows PowerShell equivalent commands
The following Windows PowerShell cmdlet or cmdlets perform the same function as the preceding procedure. Enter each cmdlet on a single line, even though they may appear word-wrapped across several lines here because of formatting constraints.
Alternatively, you can configure access-denied assistance individually on each file server by using the File Server Resource Manager console.
To configure access-denied assistance by using File Server Resource Manager
Open File Server Resource Manager. In Server Manager, click Tools, and then click File Server Resource Manager.
Right-click File Server Resource Manager (Local), and then click Configure Options.
Click the Access-Denied Assistance tab.
Select the Enable access-denied assistance check box.
In the Display the following message to users who are denied access to a folder or file box, type a message that users will see when they are denied access to a file or folder.
You can add macros to the message that will insert customized text. The macros include:
[Original File Path] The original file path that was accessed by the user.
[Original File Path Folder] The parent folder of the original file path that was accessed by the user.
[Admin Email] The administrator email recipient list.
[Data Owner Email] The data owner email recipient list.
Click Configure email requests, select the Enable users to request assistance check box, and then click OK.
Click Preview if you want to see how the error message will look to the user.
Click OK.
Windows PowerShell equivalent commands
The following Windows PowerShell cmdlet or cmdlets perform the same function as the preceding procedure. Enter each cmdlet on a single line, even though they may appear word-wrapped across several lines here because of formatting constraints.
After you configure the access-denied assistance, you must enable it for all file types by using Group Policy.
To configure access-denied assistance for all file types by using Group Policy
Open Group Policy Management. In Server Manager, click Tools, and then click Group Policy Management.
Right-click the appropriate Group Policy, and then click Edit.
Click Computer Configuration, click Policies, click Administrative Templates, click System, and then click Access-Denied Assistance.
Right-click Enable access-denied assistance on client for all file types, and then click Edit.
Click Enabled, and then click OK.
Windows PowerShell equivalent commands
The following Windows PowerShell cmdlet or cmdlets perform the same function as the preceding procedure. Enter each cmdlet on a single line, even though they may appear word-wrapped across several lines here because of formatting constraints.
You can also specify a separate access-denied message for each shared folder on a file server by using the File Server Resource Manager console.
To specify a separate access-denied message for a shared folder by using File Server Resource Manager
Open File Server Resource Manager. In Server Manager, click Tools, and then click File Server Resource Manager.
Expand File Server Resource Manager (Local), and then click Classification Management.
Right-click Classification Properties, and then click Set Folder Management Properties.
In the Property box, click Access-Denied Assistance Message, and then click Add.
Click Browse, and then choose the folder that should have the custom access-denied message.
In the Value box, type the message that should be presented to the users when they cannot access a resource within that folder.
You can add macros to the message that will insert customized text. The macros include:
[Original File Path] The original file path that was accessed by the user.
[Original File Path Folder] The parent folder of the original file path that was accessed by the user.
[Admin Email] The administrator email recipient list.
[Data Owner Email] The data owner email recipient list.
Click OK, and then click Close.
Windows PowerShell equivalent commands
The following Windows PowerShell cmdlet or cmdlets perform the same function as the preceding procedure. Enter each cmdlet on a single line, even though they may appear word-wrapped across several lines here because of formatting constraints.
Step 2: Configure the email notification settings
You must configure the email notification settings on each file server that will send the access-denied assistance messages.
Open File Server Resource Manager. In Server Manager, click Tools, and then click File Server Resource Manager.
Right-click File Server Resource Manager (Local), and then click Configure Options.
Click the Email Notifications tab.
Configure the following settings:
In the SMTP server name or IP address box, type the name of IP address of the SMTP server in your organization.
In the Default administrator recipients and Default ‘From’ e-mail address boxes, type the email address of the file server administrator.
Click Send Test E-mail to ensure that the email notifications are configured correctly.
Click OK.
Windows PowerShell equivalent commands
The following Windows PowerShell cmdlet or cmdlets perform the same function as the preceding procedure. Enter each cmdlet on a single line, even though they may appear word-wrapped across several lines here because of formatting constraints.
Step 3: Verify that access-denied assistance is configured correctly
You can verify that the access-denied assistance is configured correctly by having a user who is running Windows 8 try to access a share or a file in that share that they do not have access to. When the access-denied message appears, the user should see a Request Assistance button. After clicking the Request Assistance button, the user can specify a reason for access and then send an email to the folder owner or file server administrator. The folder owner or file server administrator can verify for you that the email arrived and contains the appropriate details.
If you want to verify access-denied assistance by having a user who is running Windows Server 2012 , you must install the Desktop Experience before connecting to the file share.
Access Denied when running Windows Service
I have created a Windows Service using ASP.Net Core 3.x and C#. I started with the new Windows Service template when I built the project. When I run it from my development environment or from a console window it runs fine. When I install it as a Windows Service and attempt to start the service I get an «Error 5: Access is denied.» error.
I tried numerous things which I will outline below to eliminate the error but nothing seemed to work so I downloaded the sample app provided by Microsoft, at sample
Same result. when I run the sample app from within Visual Studio it runs fine, when running as a service I get the Access Denied error.
I am running all of this on my local machine, which I am an admin on.
I originally tried to run it using the default Local System account; got the Access Denied error. I changed the Log On As to my domain account, the same one I use to log into my local machine which is an admin on this machine; got the same Access Denied error.
My account has the privilege set to run as a service.
The Event Viewer just shows the one message which says «Access Denied», no other messages are created.
I believe the Access Denied error is occurring before the C# code is even executed. What makes me believe this is that I added one line to the very top of the Program.Main. File.WriteAllText(«C:\\temp\\ws.log», $»Test of Worker Service @
I have read numerous web sites, include this one and this one. No luck, everything I tried from these sites still produce the Access Denied error.
I have run out of ideas and am hoping someone here can provide me the answer. Thanks!
How to troubleshoot Active Directory replication error 5 in Windows Server: Access is denied
This article describes the symptoms, cause, and resolution of situations in which Active Directory replication fails with error 5: Access is denied.
Original product version: В Windows Server 2012 R2
Original KB number: В 3073945
Symptoms
You may encounter one or more of the following symptoms when Active Directory replications fail with error 5.
Symptom 1
The Dcdiag.exe command-line tool reports that the Active Directory replication test fails with error status code (5). The report resembles the following:
Testing server: Site_Name\Destination_DC_Name
Starting test: Replications
*Replications Check
[Replications Check,Destination_DC_Name] A recent replication attempt failed:
From Source_DC to Destination_DC
Naming Context: Directory_Partition_DN_Path
The replication generated an error (5):
Access is denied.
The failure occurred at Date Time.
The last success occurred at Date Time.
Number failures have occurred since the last success.
Symptom 2
The Dcdiag.exe command-line tool reports that the DsBindWithSpnEx function fails with error 5 by running the DCDIAG /test:CHECKSECURITYERROR command.
Symptom 3
The REPADMIN.exe command-line tool reports that the last replication attempt failed with status 5.
The REPADMIN commands that frequently cite the five status include but aren’t limited to the following:
- REPADMIN /KCC
- REPADMIN /REPLICATE
- REPADMIN /REPLSUM
- REPADMIN /SHOWREPL
- REPADMIN /SHOWREPS
- REPADMIN /SYNCALL
Sample output from the REPADMIN /SHOWREPL command follows. This output shows incoming replication from DC_2_Name to DC_1_Name failing with the «Access is denied» error.
Site_Name\DC_1_Name
DSA Options: IS_GC
Site Options: (none)
DSA object GUID: GUID
DSA invocationID: invocationID
==== INBOUND NEIGHBORS======================================
DC= DomainName,DC=com
Site_Name\DC_2_Name via RPC
DSA object GUID: GUID
Last attempt @ Date Time failed, result 5(0x5):
Access is denied.
consecutive failure(s).
Last success @ Date Time.
Symptom 4
NTDS KCC, NTDS General, or Microsoft-Windows-ActiveDirectory_DomainService events with the five status are logged in the Directory Services log in Event Viewer.
The following table summarizes Active Directory events that frequently cite the 8524 status.
| Event ID | Source | Event string |
|---|---|---|
| 1655 | NTDS General | Active Directory tried to communicate with the following global catalog and the attempts were unsuccessful. |
| 1925 | NTDS KCC | The attempt to establish a replication link for the following writable directory partition failed. |
| 1926 | NTDS KCC | The attempt to establish a replication link to a read-only directory partition with the following parameters failed. |
Symptom 5
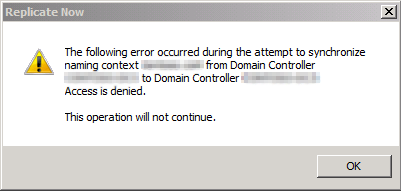
When you right-click the connection object from a source domain controller in Active Directory Sites and Services and then select Replicate Now, the process fails, and you receive the following error:
The following error occurred during the attempt to synchronize naming context %directory partition name% from Domain Controller Source DC to Domain Controller Destination DC: Access is denied.
The operation will not continue.
The following screenshot represents a sample of the error:
Workaround
Use the generic DCDIAG command-line tool to run multiple tests. Use the DCDIAG /TEST:CheckSecurityErrors command-line tool to perform specific tests. (These tests include an SPN registration check.) Run the tests to troubleshoot Active Directory operations replication failing with error 5 and error 8453. However, be aware that this tool does not run as part of the default execution of DCDIAG.
To work around this issue, follow these steps:
- At command prompt, run DCDIAG on the destination domain controller.
- Run DCDAIG /TEST:CheckSecurityError .
- Run NETDIAG.
- Resolve any faults that were identified by DCDIAG and NETDIAG.
- Retry the previously failing replication operation.If replications continue to fail, see the «Causes and solutions» section.
Causes and solutions
The following causes may result in error 5. Some of them have solutions.
Cause 1: The RestrictRemoteClients setting in the registry has a value of 2
If the Restrictions for Unauthenticated RPC clients policy setting are enabled and is set to Authenticated without exceptions, the RestrictRemoteClients registry value is set to a value of 0x2 in the HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\RPC registry subkey.
This policy setting enables only authenticated remote procedure call (RPC) clients to connect to RPC servers that are running on the computer on which the policy setting is applied. It doesn’t allow for exceptions. If you select this option, a system can’t receive remote anonymous calls by using RPC. This setting should never be applied to a domain controller.
Disable the Restrictions for Unauthenticated RPC clients policy setting that restricts the RestrictRemoteClients registry value to 2.
The policy setting is located in the following path: Computer Configuration\Administrative Templates\System\Remote Procedure Call\Restrictions for Unauthenticated RPC clients
Delete the RestrictRemoteClients registry setting, and then restart.
Cause 2: The CrashOnAuditFail setting in the registry of the destination domain controller has a value of 2
A CrashOnAduitFail value of 2 is triggered if the Audit: Shut down system immediately if unable to log security audits policy setting in Group Policy is enabled and the local security event log becomes full.
Active Directory domain controllers are especially prone to maximum-capacity security logs when auditing is enabled and the size of the security event log is constrained by the Do not overwrite events (clear log manually) and Overwrite as needed options in Event Viewer or their Group Policy equivalents.
Follow the steps in this section carefully. Serious problems might occur if you modify the registry incorrectly. Before you modify it, back up the registry for restoration in case problems occur.
- Clear the security event log, and save it to an alternative location as required.
- Reevaluate any size constraints on the security event log. This includes policy-based settings.
- Delete and then re-create a CrashOnAuditFail registry entry as follows:Registry subkey: HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\LSA
Value Name: CrashOnAuditFail
Value Type: REG_DWORD
Value Data: 1 - Restart the destination domain controller.
Cause 3: Invalid trust
If Active Directory replication fails between domain controllers in different domains, you should verify the health of trust relationships along the trust path.
You can try the NetDiag Trust Relationship test to check for broken trusts. The Netdiag.exe utility identifies broken trusts by displaying the following text:
Trust relationship test. . . . . . : Failed
Test to ensure DomainSid of domain ‘domainname‘ is correct.
[FATAL] Secure channel to domain ‘domainname‘ is broken.
[% variable status code %]
For example, if you have a multi-domain forest that contains a root domain ( Contoso.COM ), a child domain ( B.Contoso.COM ), a grandchild domain ( C.B.Contoso.COM ), and a tree domain in same forest ( Fabrikam.COM ) and if replication is failing between domain controllers in the grandchild domain ( C.B.Contoso.COM ) and the tree domain ( Fabrikam.COM) , you should verify trust health between C.B.Contoso.COM and B.Contoso.COM , between B.Contoso.COM and Contoso.COM , and then finally between Contoso.COM and Fabrikam.COM .
If a shortcut trust exists between the destination domains, you don’t have to validate the trust path chain. Instead, you should validate the shortcut trust between the destination and source domain.
Check for recent password changes to the trust by running the following command:
Verify that the destination domain controller is transitively inbound replicating the writable domain directory partition where trust password changes may take effect.
Commands to reset trusts from the root domain PDC are as follows:
Commands to reset trusts from the child domain PDC are as follows:
Cause 4: Excessive time skew
Kerberos policy settings in the default domain policy allow for a five-minute difference in system time (this is the default value) between KDC domain controllers and Kerberos target servers to prevent replay attacks. Some documentation states that the system time of the client and that of the Kerberos target must be within five minutes of one another. Other documentation states that, in the context of Kerberos authentication, the time that is important is the delta between the KDC that is used by the caller and the time on the Kerberos target. Also, Kerberos doesn’t care whether the system time on the relevant domain controllers matches current time. It cares only that the relative time difference between the KDC and target domain controller is within the maximum time skew that Kerberos policy allows. (The default time is five minutes or less.)
In the context of Active Directory operations, the target server is the source domain controller that is contacted by the destination domain controller. Every domain controller in an Active Directory forest that is currently running the KDC service is a potential KDC. Therefore, you have to consider time accuracy on all other domain controllers against the source domain controller. This includes time on the destination domain controller itself.
You can use the following two commands to check time accuracy:
- DCDIAG /TEST:CheckSecurityError
- W32TM /MONITOR
You can find sample output from DCDIAG /TEST:CheckSecurityError in the «More information» section. This sample shows excessive time skew on Windows Server 2003-based and Windows Server 2008 R2-based domain controllers.
Look for LSASRV 40960 events on the destination domain controller at the time of the failing replication request. Look for events that cite a GUID in the CNAME record of the source domain controller with extended error 0xc000133. Look for events that resemble the following:
The time at the Primary Domain Controller is different than the time at the Backup Domain Controller or member server by too large an amount
Network traces that capture the destination computer that connects to a shared folder on the source domain controller (and also other operations) may show the «An extended error has occurred» on-screen error, but a network trace displays the following:
-> KerberosV5 KerberosV5:TGS Request Realm: nltest /sc:query
netdom verify
On condition, reset the destination domain controller’s password by using NETDOM /RESETPWD.
Disable the Kerberos Key Distribution Center (KDC) service on the domain controller that is restarted.
From the console of the destination domain controller, run NETDOM RESETPWD to reset the password for the destination domain controller as follows:
Make sure that likely KDCs and the source domain controller (if these are in the same domain) inbound replicate knowledge of the destination domain controller’s new password.
Restart the destination domain controller to update Kerberos tickets and retry the replication operation.
Cause 6: The «Access this computer from network» user right isn’t granted to a user who triggers replication
In a default installation of Windows, the default domain controller policy is linked to the domain controller’s organization unit (OU). The OU grants the Access this computer from network user right to the following security groups:
| Local policy | Default domain controller policy |
|---|---|
| Administrators | Administrators |
| Authenticated Users | Authenticated Users |
| Everyone | Everyone |
| Enterprise Domain Controllers | Enterprise Domain Controllers |
| [Pre-Windows 2000 compatible Access] | Pre-Windows 2000 compatible Access |
If Active Directory operations fail with error 5, you should verify the following points:
- Security groups in the table are granted the Access this computer from network user right in the default domain controller’s policy.
- Domain controller computer accounts are located in the domain controller’s OU.
- The default domain controller’s policy is linked to the domain controller’s OU or to alternative OUs that are hosting computer accounts.
- Group Policy is applied on the destination domain controller that currently logs error 5.
- The Deny access this computer from network user right is enabled or doesn’t reference direct or transitive groups that the security context being used by the domain controller or user account that triggering replication.
- Policy precedence, blocked inheritance, Microsoft Windows Management Instrumentation (WMI) filtering, or the like, isn’t preventing the policy setting from applying to domain controller role computers.
- Policy settings can be validated with the RSOP.MSC tool. However, GPRESULT /Z is the preferred tool because it’s more accurate.
- Local policy takes precedence over policy that is defined in sites, domains, and the OU.
- At one time, it was common for administrators to remove the «Enterprise domain controllers» and «Everyone» groups from the «Access this computer from network» policy setting in the default domain controller’s policy. However, removing both groups is fatal. There’s no reason to remove «Enterprise domain controllers» from this policy setting, because only domain controllers are a member of this group.
Cause 7: There’s an SMB signing mismatch between the source and destination domain controllers
| Policy setting | Registry path |
|---|---|
| Microsoft network client: Digitally sign communications (if server agrees) | HKEY_LOCAL_MACHINE\SYSTEM\CCS\Services\Lanmanworkstation\Parameters\Enablesecuritysignature |
| Microsoft network client: Digitally sign communications (always) | HKEY_LOCAL_MACHINE\SYSTEM\CCS\Services\Lanmanworkstation\Parameters\Requiresecuritysignature |
| Microsoft network server: Digitally sign communications (if server agrees) | HKEY_LOCAL_MACHINE\SYSTEM\CCS\Services\Lanmanserver\Parameters\Enablesecuritysignature |
| Microsoft network server: Digitally sign communications (always) | HKEY_LOCAL_MACHINE\SYSTEM\CCS\Services\Lanmanserver\Parameters\Requiresecuritysignature |
You should focus on SMB signing mismatches between the destination and source domain controllers. The classic cases involve a setting that is enabled or required on one side but disabled on the other.
Cause 8: UDP-formatted Kerberos packet fragmentation
Network routers and switches may fragment or completely drop large User Datagram Protocol (UDP)-formatted network packets that are used by Kerberos and Extension Mechanisms for DNS (EDNS0). Computers that are running Windows 2000 Server or Windows Server 2003 operating system families are especially vulnerable to UDP fragmentation on computers that are running Windows Server 2008 or Windows Server 2008 R2.
From the console of the destination domain controller, ping the source domain controller by its fully qualified computer name to identify the largest packet supported by the network route. To do this, run the following command:
If the largest non-fragmented packet is less than 1,472 bytes, try one of the following methods (in order of preference):
- Change the network infrastructure to appropriately support large UDP frames. This may require a firmware upgrade or configuration change on routers, switches, or firewalls.
- Set maxpacketsize (on the destination domain controller) to the largest packet identified by the PING -f -l command less 8 bytes to account for the TCP header, and then restart the changed domain controller.
- Set maxpacketsize (on the destination domain controller) to a value of 1 This triggers Kerberos authentication to use a TCP. Restart the changed domain controller to make the change take effect.
Retry the failing Active Directory operation.
Cause 9: Network adapters have the Large Send Offload feature enabled
- On the destination domain controller, open network adapter properties.
- Click the Configure button.
- Select the Advanced tab.
- Disable the IPv4 Large Send Offload property.
- Restart the domain controller.
Cause 10: Invalid Kerberos realm
The Kerberos realm is invalid if one or more of the following conditions are true:
- The KDCNames registry entry incorrectly contains the local Active Directory domain name.
- The PolAcDmN registry key and the PolPrDmN registry key don’t match.
Follow the steps in this section carefully. Serious problems might occur if you modify the registry incorrectly. Before you modify it, back up the registry for restoration in case problems occur.
Solution for the incorrect KDCNames registry entry
On the destination domain controller, run REGEDIT.
Locate the following subkey in the registry: HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Lsa\Kerberos\Domains
For each under the subkey, verify that the value for the KdcNames registry entry refers to a valid external Kerberos realm and not to the local domain or another domain in the same Active Directory forest.
Solution for mismatching PolAcDmN and PolPrDmN registry keys
This method is valid only for domain controllers that are running Windows 2000 Server.
Start Registry Editor.
In the navigation pane, expand Security.
On the Security menu, click Permissions to grant the Administrators local group full control of the SECURITY hive and its child containers and objects.
Locate the following subkey in the registry:
HKEY_LOCAL_MACHINE\SECURITY\Policy\PolPrDmN
In the right-side pane of Registry Editor, click the No Name: REG_NONE registry entry one time.
On the View menu, click Display Binary Data.
In the Format section of the dialog box, click Byte.
The domain name is displayed as a string on the right side of the Binary Data dialog box. The domain name is the same as the Kerberos realm.
Locate the following subkey in the registry:
HKEY_LOCAL_MACHINE\SECURITY\Policy\PolACDmN
In the right-side pane of Registry Editor, double-click the No Name: REG_NONE entry.
In the Binary Editor dialog box, paste the value from the PolPrDmN registry subkey. (The value from the PolPrDmN registry subkey is the NetBIOS domain name).
Restart the domain controller.If the domain controller isn’t functioning correctly, see other methods.
Cause 11: There’s a LAN Manager Compatibility (LM Compatibility) mismatch between the source and destination domain controllers
Cause 12: Service principal names are either not registered or not present because of simple replication latency or a replication failure
Cause 13: Antivirus software uses a mini-firewall network adapter filter driver on the source or destination domain controller
Status
Microsoft has confirmed that this is a problem in the Microsoft products that are listed in the «Applies to» section.
More information
Active Directory errors and events such as those described in the «Symptoms» section can also fail with error 8453 together with the following, similar error string:
The following situations can cause Active Directory operations to fail with error 8453. However, these situations don’t cause failures with error 5.
- Naming context (NC) head isn’t permitted with the Replicating Directory Changes permission.
- The security principal starting replication isn’t a member of a group that is granted the Replicating Directory Changes permission.
- Flags are missing in the UserAccountControl attribute. These include the SERVER_TRUST_ACCOUNT flag and the TRUSTED_FOR_DELEGATION flag.
- The read-only domain controller (RODC) is joined in the domain without the ADPREP /RODCPREP command running first.
Sample output from DCDIAG /TEST:CheckSecurityError
Sample DCDIAG /test:CHECKSECURITYERROR output from a Windows Server 2008 R2 domain controller follows. This output is caused by excessive time skew.
Doing primary tests Testing server: \ Starting test: CheckSecurityError
Source DC has possible security error (1398).
Diagnosing.
Time skew error between client and 1 DCs! ERROR_ACCESS_DENIED
or down machine received by:
[ ] DsBindWithSpnEx() failed with error 1398,
There is a time and/or date difference between the client and server..
Ignoring DC in the convergence test of object
CN= ,OU=Domain Controllers,DC= ,DC=com, because we
cannot connect!
. failed test CheckSecurityError
Sample DCDIAG /CHECKSECURITYERROR output from a Windows Server 2003-based domain controller follows. This is caused by excessive time skew.
Doing primary tests
Testing server: \
Starting test: CheckSecurityError
Source DC has possible security error (5). Diagnosing.
Time skew error between client and 1 DCs! ERROR_ACCESS_DENIED or down machine recieved by:
Source DC _has possible security error (5). Diagnosing.
Time skew error: 7205 seconds different between:.[ ] DsBindWithSpnEx() failed with error 5,
Access is denied..
Ignoring DC in the convergence test of object CN= ,OU=Domain Controllers,DC= ,DC=com, because we cannot connect!
. failed test CheckSecurityError
Sample DCDIAG /CHECKSECURITYERROR output follows. It shows missing SPN names. (The output could vary from environment to environment.)
Doing primary tests
Testing server: \
Test omitted by user request: Advertising
Starting test: CheckSecurityError
* Dr Auth: Beginning security errors check’
Found KDC for domain in site
Checking machine account for DC on DC
* Missing SPN :LDAP/ . /
* Missing SPN :LDAP/ .
* Missing SPN :LDAP/
* Missing SPN :LDAP/ . /
* Missing SPN :LDAP/bba727ef-be4e-477d-9796-63b6cee3bSf.
* SPN found :E3514235-4B06-I1D1-ABГ4-00c04fc2dcd2/ /
* Missing SPN :HOST/ . /
* SPN found :HOST/ .
* SPN found :HOST/
* Missing SPN :HOST/ . /
* Missing SPN :GC/ . / Unable to verify the machine account ( ) for on .