- Service User Accounts
- How to Allow Non-Admin Users to Start/Stop Windows Service?
- Setting Windows Service Permissions Using the SC.exe (Service controller) Tool
- Using the SubInACL to Allow a User to Start/Stop/Restart Service
- How to Change Windows Service Permission Using Process Explorer?
- Setting Windows Service Permissions Using PowerShell
- Using Security Templates to Manage Service Permissions
- How to Grant Users Rights to Manage a Service using GPO?
- Вход в качестве службы Log on as a service
- Справочные материалы Reference
- Возможные значения Possible values
- Рекомендации Best practices
- Location Location
- Значения по умолчанию Default values
- Управление политикой Policy management
- Групповая политика Group Policy
- Вопросы безопасности Security considerations
- Уязвимость Vulnerability
- Противодействие Countermeasure
Service User Accounts
Each service executes in the security context of a user account. The user name and password of an account are specified by the CreateService function at the time the service is installed. The user name and password can be changed by using the ChangeServiceConfig function. You can use the QueryServiceConfig function to get the user name (but not the password) associated with a service object. The service control manager (SCM) automatically loads the user profile.
When starting a service, the SCM logs on to the account associated with the service. If the log on is successful, the system produces an access token and attaches it to the new service process. This token identifies the service process in all subsequent interactions with securable objects (objects that have a security descriptor associated with them). For example, if the service tries to open a handle to a pipe, the system compares the service’s access token to the pipe’s security descriptor before granting access.
The SCM does not maintain the passwords of service user accounts. If a password is expired, the logon fails and the service fails to start. The system administrator who assigns accounts to services can create accounts with passwords that never expire. The administrator can also manage accounts with passwords that expire by using a service configuration program to periodically change the passwords.
If a service needs to recognize another service before sharing its information, the second service can either use the same account as the first service, or it can run in an account belonging to an alias that is recognized by the first service. Services that need to run in a distributed manner across the network should run in domain-wide accounts.
You can specify one of the following special accounts instead of specifying a user account for the service:
How to Allow Non-Admin Users to Start/Stop Windows Service?
By default, common (non-admin) users cannot manage Windows services. This means that users cannot stop, start, restart, or change the settings/permissions of Windows services. In some cases, it is necessary for a user to have the permissions to restart or manage certain services. In this article we’ll look at several ways to manage the permissions for Windows services. In particular, we’ll show you how to allow a non-admin user to start, stop and restart a specific Windows service by granting the appropriate permissions.
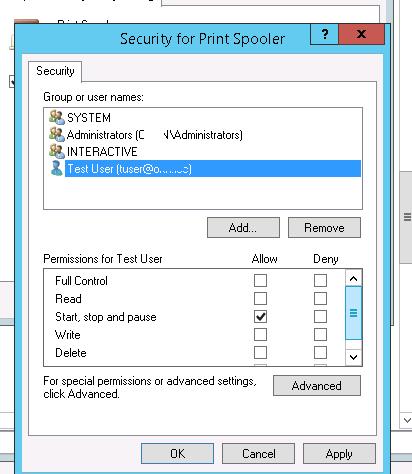
Suppose, you need to grant the domain account contoso\tuser the permissions to restart the Print Spooler service (service name – spooler). When the non-admin tries to restart the service, an error appears:
There is no simple and convenient built-in tool to manage services permissions in Windows. We’ll consider some ways to grant the permissions to a user to manage service:
Setting Windows Service Permissions Using the SC.exe (Service controller) Tool
A standard built-in Windows method to manage system service permissions supposes using the sc.exe (Service Controller) tool. The main problem with using this utility is the complex syntax of the service permissions format (the SDDL format — Security Description Definition Language).
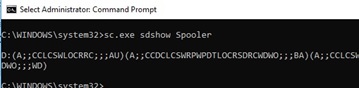
You can get the current permissions for a Windows service as an SDDL string like this:
sc.exe sdshow Spooler
What do all these symbols mean?
The first letter after brackets means: allow (A) or deny (D).
The next set of symbols is assignable permissions.
The last 2 characters are the objects (user, group or SID) that are granted permissions. There is a list of predefined groups.
Instead of a predefined group, you can explicitly specify a user or group by SID. To get the SID for the current user, you can use the command:
Or you can find the SID for any domain user using the Get-ADUser cmdlet:
Get-ADUser -Identity ‘sadams’ | select SID
You can get the SID of the AD security group using the Get-ADGroup cmdlet:
In order to assign the SDDL permissions string for a specific service, you can use the sc sdset command. For example, the permissions can be granted to a user with the following command:
sc sdset Spooler «D:(A;;CCLCSWRPWPDTLOCRRC;;;SY)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)(A;;CCLCSWLOCRRC;;;IU)(A;;CCLCSWLOCRRC;;;SU)(A;;RPWPCR;;;S-1-5-21-2133228432-2794320136-1823075350-1000)S:(AU;FA;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;WD)»
Using the SubInACL to Allow a User to Start/Stop/Restart Service
It is easier to use a command line tool SubInACL from the Sysinternals (by Mark Russinovich) to manage the service permissions. The syntax of this tool is much easier and more convenient. Here is how you can grant the restart permissions for a service using the SubInACL:
- Download subinacl.msi from this webpage (https://www.microsoft.com/en-us/download/details.aspx?id=23510) and install it on the target system;
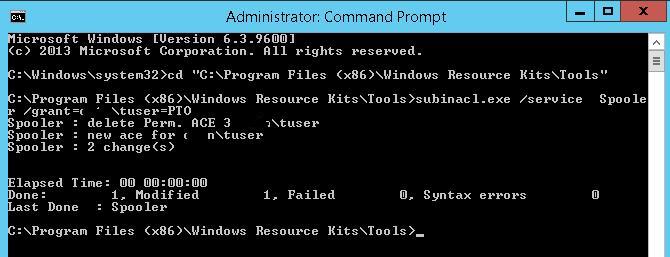
- In the elevated command prompt, go to the directory containing the tool: cd “C:\Program Files (x86)\Windows Resource Kits\Tools\»
- Run the command: subinacl.exe /service Spooler /grant=contoso\tuser=PTO
If you did everything right, the service should restart.
subinacl.exe /service Spooler /revoke=contoso\tuser
How to Change Windows Service Permission Using Process Explorer?
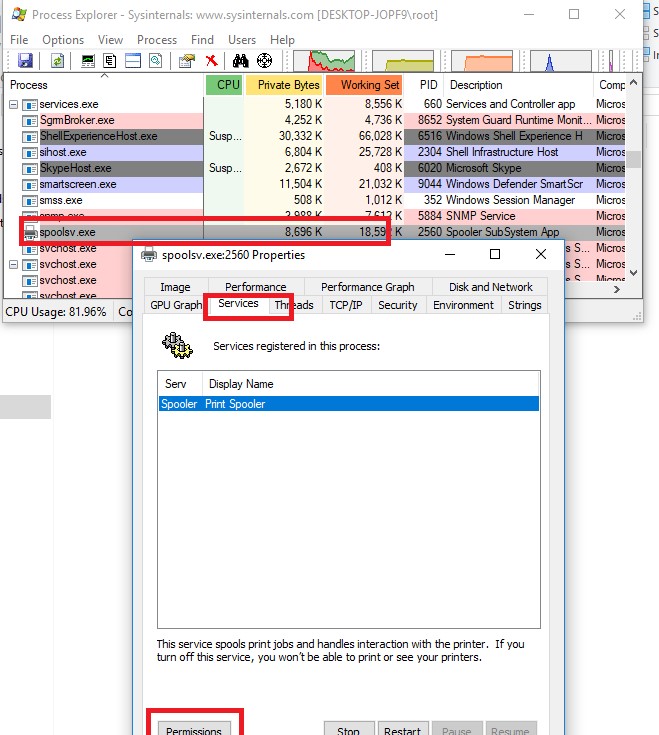
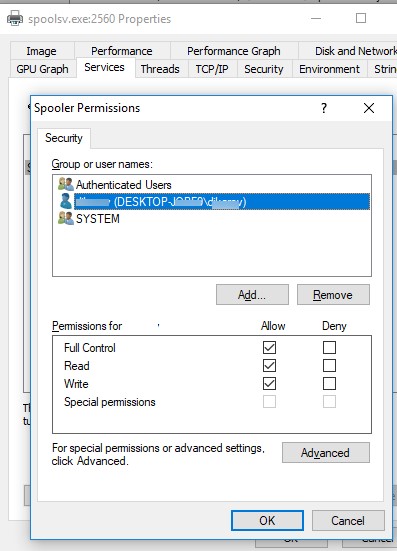
You can change Windows service permissions using one more Sysinternals utility – Process Explorer. Run the Process Explorer as administrator and find the process of the service you need. In our example, this is spoolsv.exe (the spooler executable – C:\Windows\System32\spoolsv.exe ). Open the process properties and click the Services tab.
Click the Permissions button and add the user or group in the window that opens. After that select the permissions that you want to assign (Full Control/Write/Read).
Setting Windows Service Permissions Using PowerShell
In TechNet gallery there is a separate unofficial PowerShell module for managing permissions for different Windows objects – PowerShellAccessControl Module (you can download it here). This module also allows you to manage the service permissions. Install this module and import it into your PS session:
You can get the effective permissions for a specific Windows service from PowerShell like this:
Get-Service spooler | Get-EffectiveAccess -Principal corp\tuser
To allow non-admin user to start and stop spooler service, run the command:
Get-Service spooler | Add-AccessControlEntry -ServiceAccessRights Start,Stop -Principal corp\tuser
Using Security Templates to Manage Service Permissions
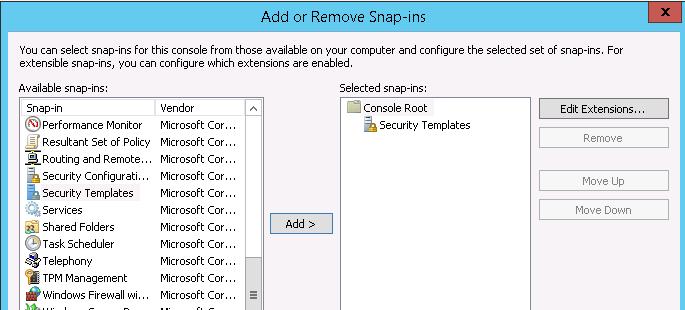
A visual (but requiring more actions) graphical way to manage service permissions is using Security Templates. Open mmc.exe console and add the Security Templates snap-in.
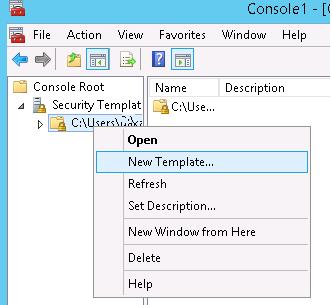
Create a new security template (New Template).
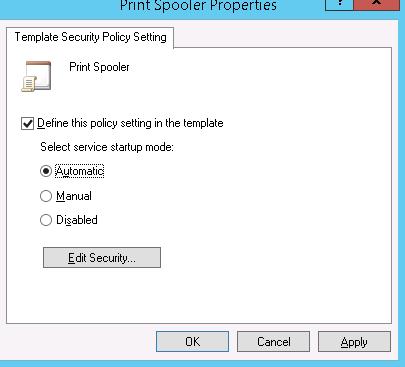
Specify the name for the new template and go to the System Services section. In the list of services select the service Print Spooler and open its properties.
Select the startup mode (Automatic) and click Edit Security.
Using the Add button, add a user account or a group to grant permissions to. In our case, Start, stop and pause permission is enough.
Save this template.
If you open this file, you can see that the information about the permissions is saved in the SDDL format, mentioned earlier. The string obtained in this way can be used as an argument of the sc.exe command.
[Unicode]
Unicode=yes
[Version]
signature=»$CHICAGO$»
Revision=1
[Service General Setting]
«Spooler»,2,»D:AR(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;SY)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)(A;;CCLCSWLOCRRC;;;IU)(A;;RPWPDTRC;;;S-1-5-21-3243688314-1354026805-3292651841-1127)S:(AU;FA;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;WD)»
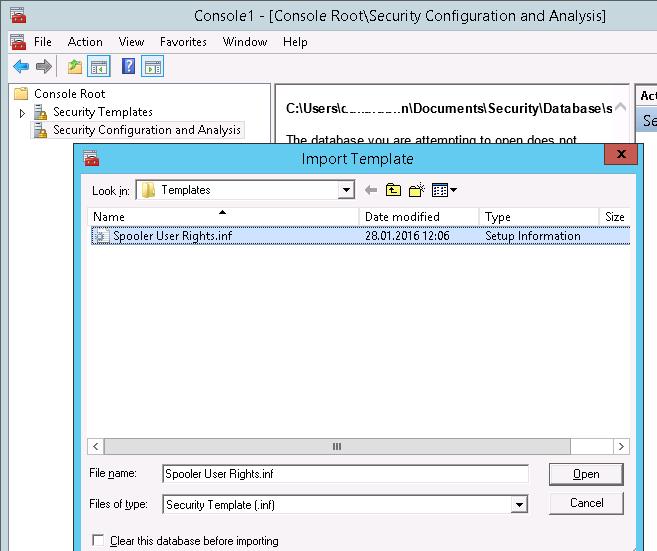
Now you only have to create a new database (Open Database) using the Security Configuration and Analysis snap-in and import your Security Template from the file Spooler User Rights.inf.
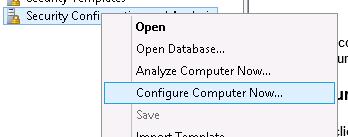
Apply this template by selecting Configure Computer Now option from the context menu.
Now you check that the user can allow manage the Print Spooler service under non-admin account.
How to Grant Users Rights to Manage a Service using GPO?
If you have to grant permissions to users to start/stop a service multiple servers or domain computer, it’s easier to use Group Policy (GPO) features:
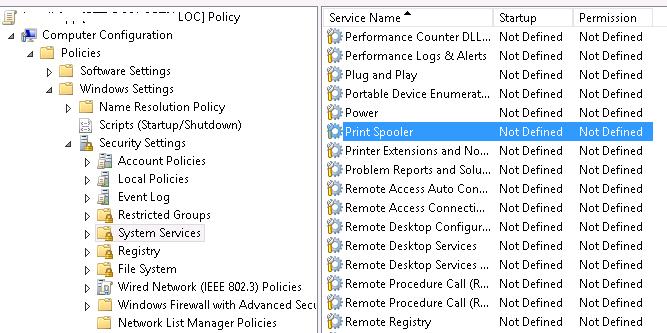
- Create a new GPO or edit the existing one, link it to the necessary Active Directory container (OU) with the computer objects . Go to the policy section Computer configuration -> Windows Settings -> Security Settings -> System Services;
- Find the Spooler service and grant permissions to the users like in the method described above. Save the changes;
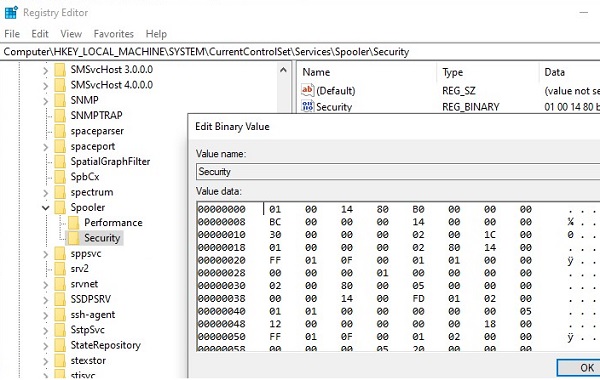
The security settings for all services for which you changed the default permissions are stored in their own registry key HKLM\System\CurrentControlSet\Services\ \Security in the Security parameter of the REG_BINARY type.
This means that one of the ways to set service permissions on other computers is to export/import this registry parameter (including through a GPO).
So, we looked at several ways to manage the Windows service permissions, which allow you to grant any permissions for system services to non-admin user. If the user requires remote access to the service, without granting it local logon or RDP access permissions, you must allow the user to connect remotely and enumerate services via Service Control Manager.
Вход в качестве службы Log on as a service
Область применения Applies to
В этой статье описываются рекомендации, рекомендации по расположению, значениям, **** управлению политиками и безопасности для параметра политики безопасности «Вход в качестве службы». This article describes the recommended practices, location, values, policy management, and security considerations for the Log on as a service security policy setting.
Справочные материалы Reference
Этот параметр политики определяет, какие учетные записи служб могут регистрировать процесс как службу. This policy setting determines which service accounts can register a process as a service. Запуск процесса под учетной записью службы не учитывает необходимость вмешательства человека. Running a process under a service account circumvents the need for human intervention.
Константа: SeServiceLogonRight Constant: SeServiceLogonRight
Возможные значения Possible values
- Определяемый пользователей список учетных записей User-defined list of accounts
- Не определено Not Defined
Рекомендации Best practices
- Свести к минимуму количество учетных записей, которые имеют это право пользователя. Minimize the number of accounts that are granted this user right.
Location Location
Computer Configuration\Windows Settings\Security Settings\Local Policies\User Rights Assignment Computer Configuration\Windows Settings\Security Settings\Local Policies\User Rights Assignment
Значения по умолчанию Default values
По умолчанию этот параметр является сетевой службой на контроллерах домена и сетевой службой на автономных серверах. By default this setting is Network Service on domain controllers and Network Service on stand-alone servers.
В следующей таблице приведены фактические и действующие значения по умолчанию для этой политики. The following table lists the actual and effective default policy values. На странице свойств политики также перечислены значения по умолчанию. The policy’s property page also lists default values.
| Тип сервера или объект групповой политики Server type or GPO | Значение по умолчанию Default value |
|---|---|
| Default Domain Policy Default Domain Policy | Не определено Not defined |
| Политика контроллера домена по умолчанию Default Domain Controller Policy | Не определено Not defined |
| Параметры по умолчанию для автономного сервера Stand-Alone Server Default Settings | Не определено Not defined |
| Действующие параметры по умолчанию для контроллера домена Domain Controller Effective Default Settings | Сетовая служба Network Service |
| Действующие параметры по умолчанию для рядового сервера Member Server Effective Default Settings | Сетовая служба Network Service |
| Действующие параметры по умолчанию для клиентского компьютера Client Computer Effective Default Settings | Сетовая служба Network Service |
Управление политикой Policy management
В этом разделе описаны компоненты, средства и рекомендации, которые помогут в управлении этой политикой. This section describes features, tools, and guidance to help you manage this policy.
Для активации этого параметра политики не требуется перезагрузка компьютера. A restart of the computer isn’t required for this policy setting to be effective.
Изменения прав пользователя вступают в силу при его следующем входе в учетную запись. Any change to the user rights assignment for an account becomes effective the next time the owner of the account logs on.
Групповая политика Group Policy
Если учетная запись пользователя подчиняется обеим политикам, то этот параметр политики «Запретить в качестве службы» переоменовывает этот параметр политики. The policy setting Deny logon as a service supersedes this policy setting if a user account is subject to both policies.
Параметры групповой политики применяются в следующем порядке, что перезапишет параметры на локальном устройстве при следующем обновлении групповой политики: Group Policy settings are applied in the following order, which will overwrite settings on the local device at the next Group Policy update:
- Параметры локальной политики Local policy settings
- Параметры политики сайта Site policy settings
- Параметры политики домена Domain policy settings
- Параметры политики подразделения OU policy settings
Вопросы безопасности Security considerations
В этом разделе описывается, как злоумышленник может использовать функцию или ее конфигурацию. This section describes how an attacker might exploit a feature or its configuration. В нем объясняется меры противодействия. It explains the countermeasure. Кроме того, он решает возможные отрицательные последствия противодействия. And it addresses the possible negative consequences of the countermeasure.
Уязвимость Vulnerability
Право входа в систему как пользователя службы позволяет учетным записям запускать сетевые службы или службы, которые непрерывно работают на компьютере, даже если никто не входит в консоль. The Log on as a service user right allows accounts to start network services or services that run continuously on a computer, even when no one is logged on to the console. Риск снижается, так как устанавливать и настраивать службы могут только пользователи с административными привилегиями. The risk is reduced because only users who have administrative privileges can install and configure services. Злоумышленник, который уже достиг этого уровня доступа, может настроить службу для запуска с помощью учетной записи Local System. An attacker who has already reached that level of access could configure the service to run with the Local System account.
Противодействие Countermeasure
По определению учетная запись сетевой службы имеет право входа в качестве пользователя службы. By definition, the Network Service account has the Log on as a service user right. Это право не предоставляется с помощью параметра групповой политики. This right isn’t granted through the Group Policy setting. Свести к минимуму количество других учетных записей, которые имеют это право пользователя. Minimize the number of other accounts that are granted this user right.