TCPView v4.0
By Mark Russinovich
Published: March 23, 2021

Run now from Sysinternals Live.
Introduction
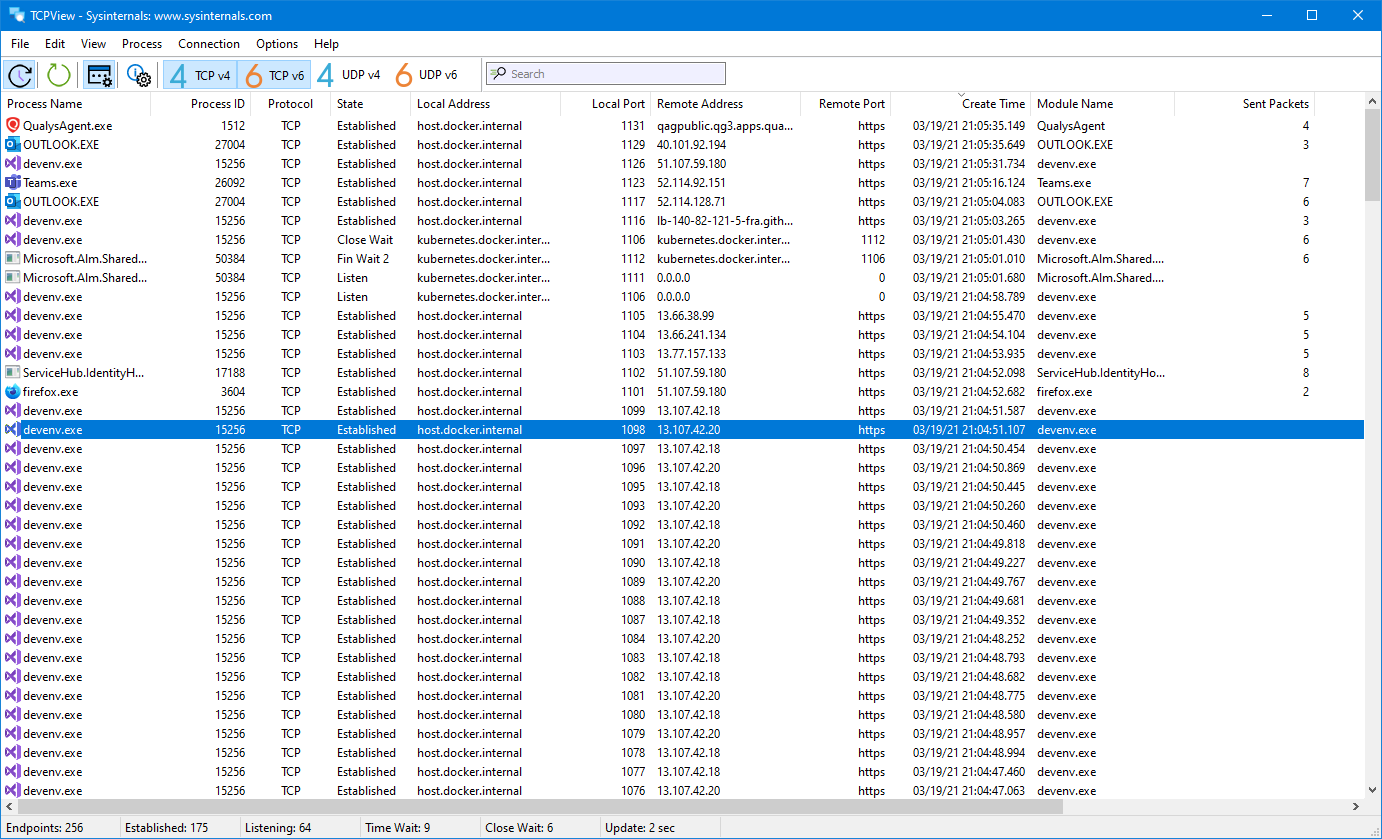
TCPView is a Windows program that will show you detailed listings of all TCP and UDP endpoints on your system, including the local and remote addresses and state of TCP connections. On Windows Server 2008, Vista, and XP, TCPView also reports the name of the process that owns the endpoint. TCPView provides a more informative and conveniently presented subset of the Netstat program that ships with Windows. The TCPView download includes Tcpvcon, a command-line version with the same functionality.
Using TCPView
When you start TCPView it will enumerate all active TCP and UDP endpoints, resolving all IP addresses to their domain name versions. You can use a toolbar button or menu item to toggle the display of resolved names. On Windows XP systems, TCPView shows the name of the process that owns each endpoint.
By default, TCPView updates every second, but you can use the Options|Refresh Rate menu item to change the rate. Endpoints that change state from one update to the next are highlighted in yellow; those that are deleted are shown in red, and new endpoints are shown in green.
You can close established TCP/IP connections (those labeled with a state of ESTABLISHED) by selecting File|Close Connections, or by right-clicking on a connection and choosing Close Connections from the resulting context menu.
You can save TCPView’s output window to a file using the Save menu item.
Using Tcpvcon
Tcpvcon usage is similar to that of the built-in Windows netstat utility:
Usage:
| Parameter | Description |
|---|---|
| -a | Show all endpoints (default is to show established TCP connections). |
| -c | Print output as CSV. |
| -n | Don’t resolve addresses. |
Microsoft TCPView KB Article
This Microsoft KB article references TCPView:

Run now from Sysinternals Live.
Runs on:
- Client: Windows 8.1 and higher.
- Server: Windows Server 2012 and higher.
—>
netstat
Applies to: Windows Server (Semi-Annual Channel), Windows Server 2019, Windows Server 2016, Windows Server 2012 R2, Windows Server 2012
Displays active TCP connections, ports on which the computer is listening, Ethernet statistics, the IP routing table, IPv4 statistics (for the IP, ICMP, TCP, and UDP protocols), and IPv6 statistics (for the IPv6, ICMPv6, TCP over IPv6, and UDP over IPv6 protocols). Used without parameters, this command displays active TCP connections.
This command is available only if the Internet Protocol (TCP/IP) protocol is installed as a component in the properties of a network adapter in Network Connections.
Syntax
Parameters
| Parameter | Description |
|---|---|
| -a | Displays all active TCP connections and the TCP and UDP ports on which the computer is listening. |
| -b | Displays the executable involved in creating each connection or listening port. In some cases well-known executables host multiple independent components, and in these cases the sequence of components involved in creating the connection or listening port is displayed. In this case the executable name is in [] at the bottom, on top is the component it called, and so forth until TCP/IP was reached. Note that this option can be time-consuming and will fail unless you have sufficient permissions. |
| -e | Displays Ethernet statistics, such as the number of bytes and packets sent and received. This parameter can be combined with -s. |
| -n | Displays active TCP connections, however, addresses and port numbers are expressed numerically and no attempt is made to determine names. |
| -o | Displays active TCP connections and includes the process ID (PID) for each connection. You can find the application based on the PID on the Processes tab in Windows Task Manager. This parameter can be combined with -a, -n, and -p. |
| -p |
Remarks
The netstat command provides statistics for the following:
| Parameter | Description |
|---|---|
| Proto | The name of the protocol (TCP or UDP). |
| Local address | The IP address of the local computer and the port number being used. The name of the local computer that corresponds to the IP address and the name of the port is shown unless the -n parameter is specified. If the port is not yet established, the port number is shown as an asterisk (*). |
| Foreign address | The IP address and port number of the remote computer to which the socket is connected. The names that corresponds to the IP address and the port are shown unless the -n parameter is specified. If the port is not yet established, the port number is shown as an asterisk (*). |
| State | Indicates the state of a TCP connection, including:
|
Examples
To display both the Ethernet statistics and the statistics for all protocols, type:
To display the statistics for only the TCP and UDP protocols, type:
To display active TCP connections and the process IDs every 5 seconds, type:
To display active TCP connections and the process IDs using numerical form, type:
Viewing and killing TCP IP connections Windows
Many time in troubleshooting or needing to view network traffic information or connection information, seeing your TCP/IP connections in Windows can provide valuable insight into problems or issues that may be going on in Windows with connectivity. Also, viewing connection information is a great way to narrow down on possible backdoor traffic to a workstation if malware is suspected. In this guide, we want to look at several tools and utilities to both view connection information as well as kill TCP connections in Windows that may be problematic or malicious.
Windows itself has many really nice tools built-in that will enable you to see TCP and UDP connections right out of the box via the commandline. Especially the later versions of Windows which include Powershell expand these capabilities as well.
Commandline Tools
Powershell
With powershell we have a whole new array of commandlets to peer inside of and control what is going on with Network connections in Windows. There are two commands in general among others that provide really powerful monitoring inside of Powershell and that is the get-nettcpconnection and get-udpendpoint. Take a look at the whole list of new powershell commands for monitoring and controlling TCP activity here: https://technet.microsoft.com/en-us/library/hh826123.aspx
Get-NetTcpConnection – cmdlet gets current TCP connections. Use this cmdlet to view TCP connection properties such as local or remote IP address, local or remote port, and connection state.
Get-NetUDPEndpoint – gets current statistics for a UDP endpoint. The cmdlet returns UDP end point properties, such as local and remote UDP ports. If you do not specify any parameters, the cmdlet gets statistics for all UDP end points.
Netstat
Displays active TCP connections, ports on which the computer is listening, Ethernet statistics, the IP routing table, IPv4 statistics (for the IP, ICMP, TCP, and UDP protocols), and IPv6 statistics (for the IPv6, ICMPv6, TCP over IPv6, and UDP over IPv6 protocols). Used without parameters, netstat displays active TCP connections.
Below the command was issued netstat -ano
With the PID information you see above in the netstat output, you can use this number to correlate with PID information in Task Manager to identify the exact process and kill if need be.
Wkillcx is a small command-line utility to close any TCP connection under Windows XP/Vista/Seven as well as Windows Server 2003/2008. This is a great little commandline program that allows you to kill the remote IP:port connection information without knowing the PID. You simply issue the command, feed the appropriate connection information, it searches for that connection and kills it. Download wkillcx here: https://wkillcx.sourceforge.net/
GUI Tools
Along with the commandline tools included in Windows there are also a couple of really nice GUI tools that allow ones to see TCP activity as well as kill those TCP connections via killing the process that is spawning the TCP connections.
TCPView
TCPView is a Windows SysInternals Tool that is designed to basically show detailed listings of all TCP and UDP endpoints on your system, including the local and remote addresses and state of TCP connections. The download of the utility also includes a commandline version of the tool in tcpvcon. Download TCPView here: https://technet.microsoft.com/en-us/sysinternals/bb897437.aspx
Another really nice feature of TCPView is that you can right-click on any connection entry and then Kill the process that is using it:
Microsoft Message Analyzer 1.0
Microsoft Message Analyzer is a new tool for capturing, displaying, and analyzing protocol messaging traffic and other system messages. This is a relatively new tool that also can import data from the legacy Microsoft Network Protocol Analyzer 3.4.
This is a more full blown protocol analyzer, but can do many of the basic things we are referring too in the above guide. Download the Microsoft Message Analyzer here: https://www.microsoft.com/en-us/download/details.aspx?id=40308
Final Thoughts
Using the tools listed above, one can view network connection information via either the commandline or using GUI tools. This is extremely helpful when you are tracking down a rogue connection or a problematic process that has network hooks.
How can I see all active connections?
My Internet connection has been slow lately, and I think it might be a possible attack. A friend has told me to use Wireshark, but it is a big install, and I do not have the time to learn how to use it. Is there an easier way to see all the connections on my PC so I can take further action?
6 Answers 6
You are looking for the netstat command. This command should provide what you’re looking for:
if you would also like to see what programs are using the specified ports you can use:
to use the netstat program:
- Go to the start menu (or press Win + r and skip to step 3)
- If on XP, click «Run», If on vista or later, search for cmd in the search box and skip to step 4.
- type cmd
- after cmd opens, type netstat -a
- a list of all open connections with their ports will be displayed
more info about netstat:
I would also recommend running Autoruns and Process Explorer, also in the Sysinternals Suite to help diagnose your problem.
If you’re looking for a simple look at which connections are hungry on Windows 7 onwards, then bring up Task Manager, Performance tab, Resource Monitor, Network tab.
Prio (http://www.prnwatch.com/prio.html) can provide, as part of the Windows Task Manager, an updating list connections with some additional context that may help you make sense of what is going on.
You can see the active ports aligned with the processes in use.
It adds a lot of functionality to the task manager and it is all contained in one area.
I am not a computer scientist but I find that netstat is a bit slow and many connections pass through unrecorded, wireshark is fast but has too many packets to filter through and windows resource monitor is too hard to look through the list to see who is making connections.