- FIX: SmartScreen prevented an unrecognized app from starting
- Turning off the Smart Screen filter
- Windows Defender SmartScreen prevented an unrecognized app from starting
- What to do when Windows Defender blocks unrecognized apps
- What does this prompt means
- How to disable SmartScreen
- [SOLVED] Windows Defender SmartScreen prevented an unrecognized app error
- What is SmartScreen?
- Why has SmartScreen prevented my application?
- How do I run an application SmartScreen has prevented?
- How do I completely disable Window Defender SmartScreen?
- Is SmartScreen a privacy issue?
- How to avoid the “Windows Defender SmartScreen prevented an unrecognized app from starting warning”
- 4 Answers 4
- Windows SmartScreen preventing installer from Running #32
- Comments
- paperclip commented Mar 26, 2017
- paperclip commented Mar 26, 2017
- mintty commented Mar 26, 2017
- spgennard commented Apr 3, 2017
- mintty commented Apr 3, 2017
- mintty commented Apr 13, 2017
- paperclip commented Apr 14, 2017
- mintty commented Apr 17, 2017
- willpower232 commented May 5, 2017
- mintty commented May 5, 2017
- willpower232 commented May 5, 2017
- mintty commented May 19, 2017
- ryanerwin commented May 22, 2017 •
- mintty commented May 22, 2017
- ryanerwin commented May 22, 2017
- mintty commented May 22, 2017
- ryanerwin commented May 22, 2017
- mintty commented May 22, 2017
- mintty commented May 22, 2017
- PhilipDaniels commented May 22, 2017
- mintty commented May 22, 2017
- mintty commented May 22, 2017
- willpower232 commented May 22, 2017
- fti7 commented Jun 20, 2017
- mintty commented Jun 20, 2017
- nyuszika7h commented Jul 20, 2017 •
- fti7 commented Jul 20, 2017
- lucastheisen commented Jul 21, 2017
- paperclip commented Jul 22, 2017
- mintty commented Jul 22, 2017
- lucastheisen commented Jul 22, 2017
- lucastheisen commented Jul 22, 2017
- fuzzykiller commented Jul 31, 2017
- mintty commented Jul 31, 2017
- ukreddy-erwin commented Aug 30, 2017
- mintty commented Oct 23, 2017
- navossoc commented Oct 29, 2017 •
- mintty commented Oct 30, 2017
- navossoc commented Oct 30, 2017
- mintty commented Oct 30, 2017
- navossoc commented Oct 30, 2017 •
FIX: SmartScreen prevented an unrecognized app from starting
Smart Screen is a security module that was introduced by Microsoft and integrated into several Microsoft utilities such as Internet Explorer 8, 9, 10, 11 with a main focus to improve security. When you try to install a certain software or an app that is not included in the windows store, a warning message pops up automatically to notify you that it may not be a safe choice to install; but on a gentler note it still gives you an option to run the program anyway.
In addition to this, Smart Screen automatically checks the websites we visit so as to continuously update a list of reported phishing sites and malicious software websites. All this may seem annoying at times but it basically keeps the PCs safe from malicious viruses or malware.
In this guide we will explore ways of sorting out the Smart Screen issue. At some point it just starts getting on your nerves; after all you are aware of what you install as well as the sites you visit.
Turning off the Smart Screen filter
First things first, if you want to turn the Smart Screen filter ensure that you have a powerful antivirus program installed on your PC. This will protect you from the different malware and viruses that may accompany the programs that you want to install. Here are a few steps to get you there.
Hold the Windows Key and Press X. Choose Control Panel
Now click on System and Security -> Go to Security and Maintenance. On the left hand side of the screen choose Change Windows Smart Screen Settings.
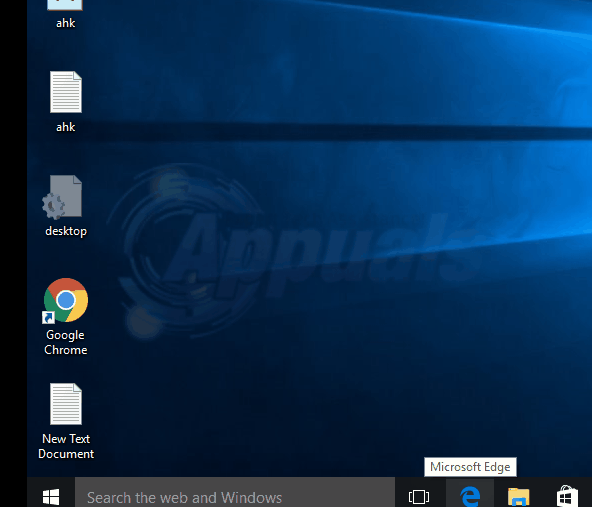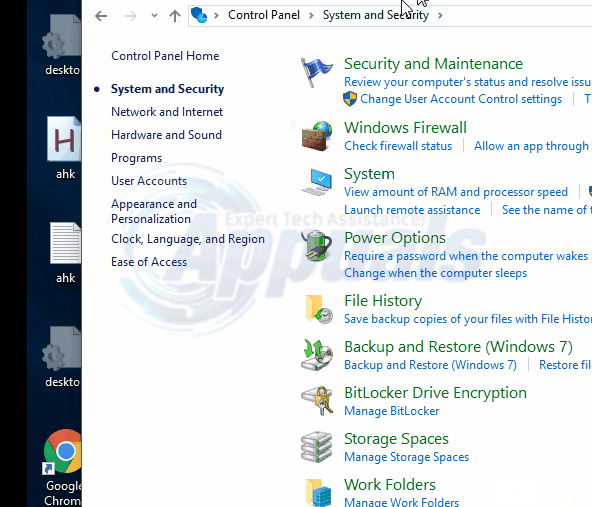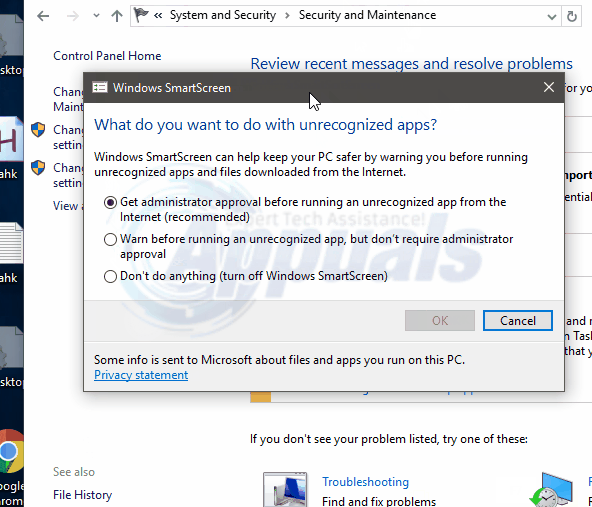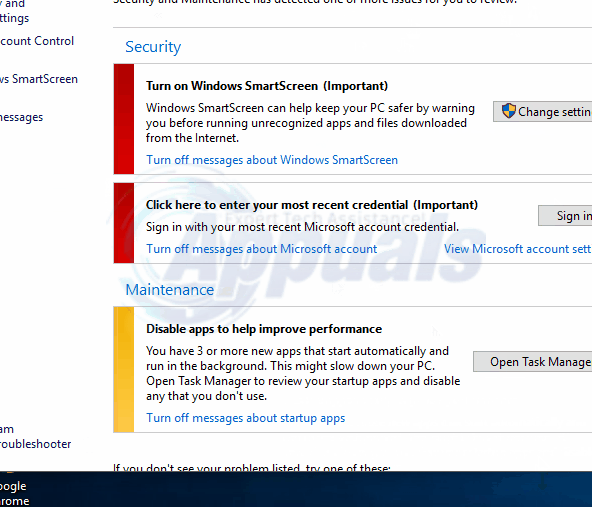
Now choose “Don’t do anything” (Turn off Windows Smart Screen). Make sure that you save/apply the changes that you have effected.
In case you need the Smart Screen up and running the same steps apply. However at step five make sure you choose “turn on windows Smart Screen”. There you go, Smart Screen has been disabled.
You still have some options open to you once Smart Screen is off. Once Smart Screen has been disabled, you may still get a warning or prompt with the wording “The publisher could not be verified. Are you sure you want to run this software?” You may probably also want to completely stop Windows from adding the zone info in the file’s substitute stream; so that you no longer receive such warnings. Here’s how:
Press Windows + R and type gpedit.msc. You can just as well type that right at the start menu, it will automatically appear.
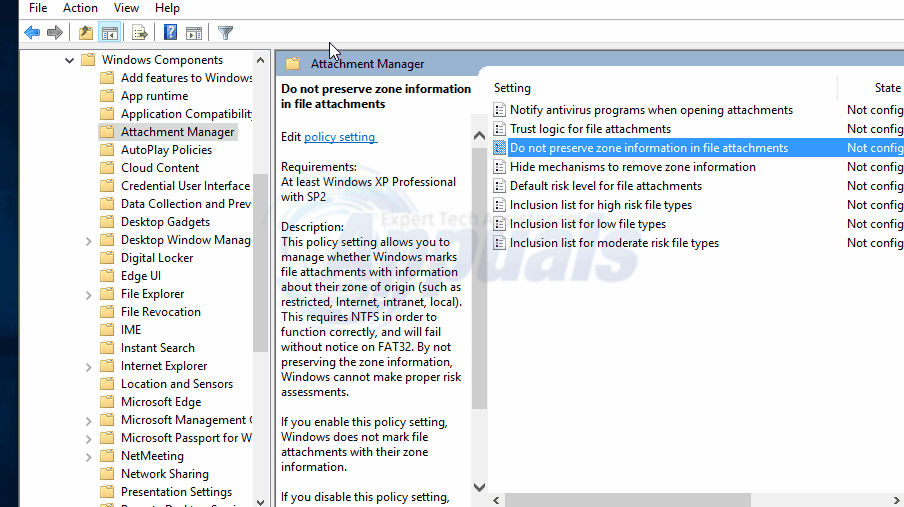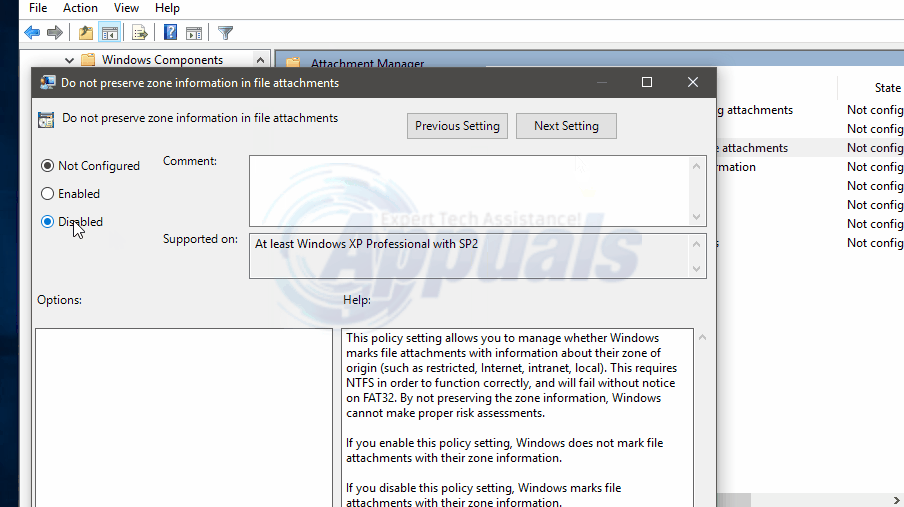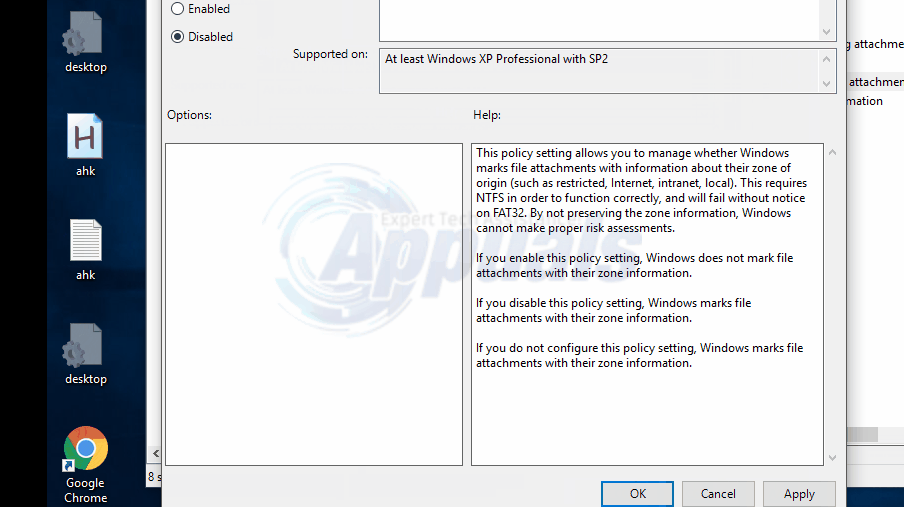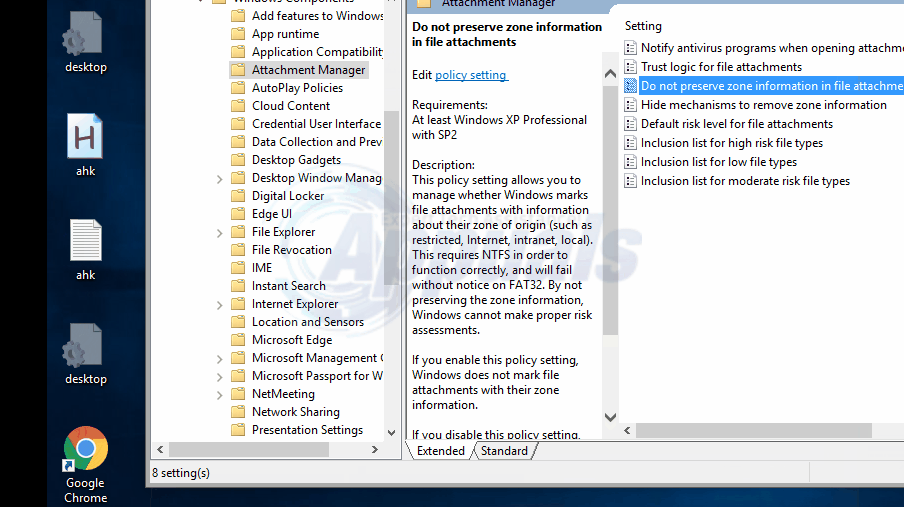
Navigate to User Configuration, then to Administrative Templates. Next, select Windows components and then Attachment manager.
Double click on the policy entry that reads “Do not preserve zone information in file attachments” Activate it and then click/tap on OK.
The same can be achieved via editing system registry editor.
- Go to the Registry Editor (type regedit on the Run window)
- Navigate to this key:
“HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Attachments”
- If this key does not exist, create one yourself.
- Make a new DWORD and name it “SaveZoneInformation”. Set it to 1.
From hereinafter, you will not be required to unblock files downloaded via your browsers and downloader apps so long as they adhere to this setting.
Windows Defender SmartScreen prevented an unrecognized app from starting
Windows Defender is a very good built-in security tool. However, it can occasionally be quite a bothersome experience due to frequent notifications and actions. Microsoft can say that’s for your own good, but that’s something a user needs to decide. Let’s take Windows Defender‘s SmartScreen which deals with third-party apps. Lots of users are not thrilled by frequent preventive blockage of apps in Windows 10.
We gave our best to explain why this is the case and how to disable SmartScreen on your own accord.
What to do when Windows Defender blocks unrecognized apps
What does this prompt means
Windows SmartScreen is part of Windows Defender which deals with unknown (uncertified) apps. If a third-party application is not certified or it’s known as a malicious piece of software, Windows will prevent it from installing or executing. If you’ve downloaded a third-party application from an untrusted source, chances are that it’ll get blocked.
This is the first line of defense against malicious software and we wouldn’t recommend disabling it. At least, if you’re not 100% sure that the applications you install are not a threat to your system. Or have an alternative way to locate possible threats.
Allowing the app to run and dismissing the prompt is a rather simple task. Just click “More” below the warning. Then click on the Run anyway and you’re good to go. After that, you should be able to run the application. Now, for some applications, this stands only for the installation part. If you want to avoid blocking during the usage, right-click on the shortcut and open Properties. Under the General tab, at the bottom, check the “Unblock” box.
How to disable SmartScreen
On the other hand, if you’re tired of SmartScreen’s methods or have a third-party tool which deals with this kind of threats, you can disable it for good. Since the introduction of Windows Security Center, you can disable this feature with ease. We made sure to provide you with the required steps below.
- READ ALSO: Fix: ‘Your Administrator Has Blocked This Program’ in Windows 10, 8.1 and 7
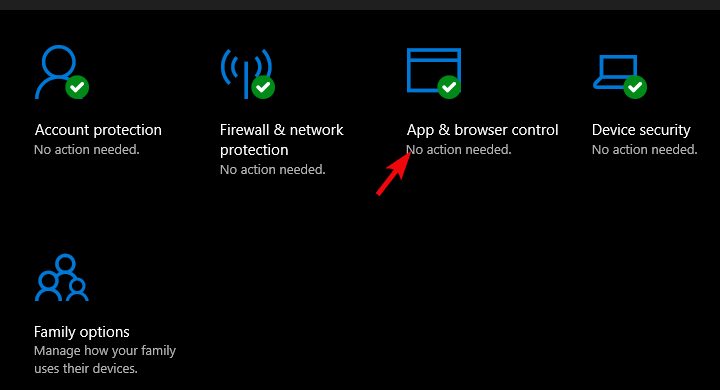
- Open Windows Defender from the notification area.
- Select App & browser control.
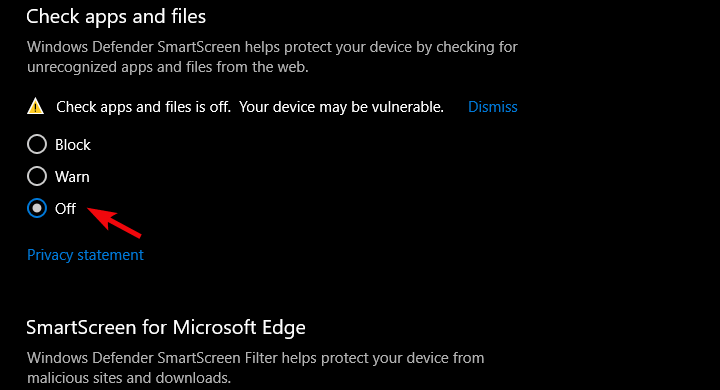
- Under the “Check apps and files” section, select Off.
After that, you shouldn’t see SmartScreen prompts anymore. Make sure to tell us whether this was a helpful read in the comments section below.
RELATED STORIES YOU SHOULD CHECK OUT:
[SOLVED] Windows Defender SmartScreen prevented an unrecognized app error
What is SmartScreen?
SmartScreen is a security feature built into Windows 10, specifically the Windows Defender tool.
Each time an application is ran Windows 10 will check if it is a “good” application against their catalog of applications.
It’s a good security measure and is particular helpful at stopping malware spreading through email attachments – where some users do not understand the difference between a legitimate document and an application.
Why has SmartScreen prevented my application?
Either it’s a known bad or unknown application.
Sometimes SmartScreen will prevent applications you know are not bad – for example, it’s a CMD or VBS script you wrote, or a program from a trusted source.
How do I run an application SmartScreen has prevented?
If you’re absolutely sure you can trust the application you can run it by
- Click on the ‘More info’ link
- Click on the ‘Run anyway’ button.
How do I completely disable Window Defender SmartScreen?
This is NOT recommended.
- In the taskbar, search for “App & browser control” and click on it when it appears in the search results
- Under ‘Check apps and files’ select ‘Off’
- Click ‘OK’ when prompted to apply the changes.
Is SmartScreen a privacy issue?
Much like anything in the Windows 10 environment – privacy is … secretive which means it’s lacking.
Microsoft have said that they are not keeping personally identifiable information such as your IP address – but they do collect it when communicating with their online system.
Personally, I think the security benefits of SmartScreen out way the privacy issues – and even if you were to disable it, Windows 10 is like a leaking sieve when it comes to privacy. If privacy were a concern I would consider an alternative operating system.
How to avoid the “Windows Defender SmartScreen prevented an unrecognized app from starting warning”
My company distributes an installer to customers via our website. Recently when I download via the website and try to run the installer I get the warning message:
Windows Defender SmartScreen prevented an unrecognized app from starting. Running this app might put your PC at risk.
If I right-click on the installer and choose Properties I note the following:
Our installer is signed.
How do I find the reason for the Windows Defender SmartScreen warning?
I have not managed to find any log file for Windows Defender nor found anything in the Event Viewer.
4 Answers 4
If you have a standard code signing certificate, some time will be needed for your application to build trust. Microsoft affirms that an Extended Validation (EV) Code Signing Certificate allows us to skip this period of trust-building. According to Microsoft, extended validation certificates allow the developer to immediately establish a reputation with SmartScreen. Otherwise, the users will see a warning like «Windows Defender SmartScreen prevented an unrecognized app from starting. Running this app might put your PC at risk.», with the two buttons: «Run anyway» and «Don’t run».
Another Microsoft resource states the following (quote): «Although not required, programs signed by an EV code signing certificate can immediately establish a reputation with SmartScreen reputation services even if no prior reputation exists for that file or publisher. EV code signing certificates also have a unique identifier which makes it easier to maintain reputation across certificate renewals.»
My experience is as follows. Since 2005, we have been using regular (non-EV) code signing certificates to sign .MSI, .EXE and .DLL files with time stamps, and there has never been a problem with SmartScreen until 2018, when there was just one case when it took 3 days for a beta version of our application to build trust since we have released it to beta testers, and it was in the middle of certificate validity period. I don’t know what SmartScreen might not like in that specific version of our application, but there have been no SmartScreen complaints since then. Therefore, if your certificate is a non-EV, it is a signed application (such as an .MSI file) that will build trust over time, not a certificate. For example, a certificate can be issued a few months ago and used to sign many files, but for each signed file you publish, it may take a few days for SmartScreen to stop complaining about the file after publishing, as was in our case in 2018.
Windows SmartScreen preventing installer from Running #32
Comments
paperclip commented Mar 26, 2017
«Windows protected your PC»
«Windows SmartScreen prevented an unrecognized app from starting. Running this app might put your PC at risk.»
App: wsltty-0.7.5-install.exe
Publisher: Unknown publisher
Installer downloaded from github. Maybe false-positives would be reduced by signing and setting publisher? Also if you could publish the SHA256 of the installer it would be easier to verify it?
The text was updated successfully, but these errors were encountered:
paperclip commented Mar 26, 2017
Image of the alert:
mintty commented Mar 26, 2017
After #31 and #28, this is getting really weird.
The installer was created with a Microsoft tool, so if they don’t recognize their own stuff, I can’t help it. Therefore marking ‘invalid’.
Also, I don’t feel the ambition to dig into the fiddly details of signing and all that stuff. If someone tells me how to do it, I’ll do it.
spgennard commented Apr 3, 2017
Have a read of the wiki on the subject, you have two solutions:
- This can be fixed by the author digitally signing the distributed software.
- A common distribution method for authors to bypass SmartScreen warnings is to pack their installation program (for example Setup.exe) into a ZIP-archive and distribute it that way
mintty commented Apr 3, 2017
- A common distribution method for authors to bypass SmartScreen warnings is to pack their installation program (for example Setup.exe) into a ZIP-archive and distribute it that way
Did you try this with wsltty? Even if it does, I guess zip archives are not really common for installation in the Windows world, especially as they depend on further tools being installed to work.
- This can be fixed by the author digitally signing the distributed software.
Sure, see my previous comment.
mintty commented Apr 13, 2017
Added note on project page. Is this sufficient to close the issue?
paperclip commented Apr 14, 2017
Sure, I don’t know much about signing Windows executables, so I can’t really help. I’d like it if you published sha512 checksums of the executables, to reduce the risk of alteration in transit, but I don’t want to give you extra work.
mintty commented Apr 17, 2017
I don’t want to give you extra work.
Thanks, you understood my previous comments well.
I don’t see how sha checksums should help with the original use case (the warning), they only make the ordinary user even more confused, by my experience.
Signing sounds better, so as I said, if anyone would provide a short how-to.
willpower232 commented May 5, 2017
I just encountered this for 0.7.6 and did not get a «run anyway» option.
I resolved it by viewing the properties and selecting «unblock».
mintty commented May 5, 2017
Thanks for the info; can you describe this more clearly so I can add a note to the project page?
I suppose properties of the installer, but I’m not aware of a standard «unblock» item.
willpower232 commented May 5, 2017
I right clicked the installer to get to the properties and checked the unblock text box and pressed OK and suddenly I was able to run it.
mintty commented May 19, 2017
Released 0.7.7. WSLtty should now be supporting third-party installation environments (#30).
ryanerwin commented May 22, 2017 •
Unfortunately Windows Defender SmartScreen is now outright blocking the download of WSLTTY-0.7.7.
I’ve looked into Windows code signing a bit. First, it looks like you’ll need to purchase an (SPC) code signing certificate. The most affordable that I was able to find is $80 from Comodo. For more references see this Quora post: Where can I find a free or cheap code signing certificate or aboutssl.com compare code signing certificates
centrum offers a free code signing certificate for open source authors, but requires the purchase of a $30 EUR usb token.
Once we’ve got the code signing certificate, we would need to sign:
- wslbridge.exe
- zoo.exe
- mintty.exe
- cygwin-console-helper.exe
- cygwin1.dll
- wsltty-0.7.7-install.exe
- If there’s an uninstaller exe (I didn’t notice one) that would need to be signed too
IE, every EXE, DLL, OCX or CAB must be signed.
Use the Microsoft’s SIGNTOOL command line to sign the actual binaries.
Centrum is probably the best deal so that no additional fee is required.
Note that you may need to do some certificate conversion along the way with makecert and pvk2pfx
mintty commented May 22, 2017
If my personal domain/hosting provider offers free certificates, will that work? Or is there a distinction for dedicated «code signing» certificates?
The concept of open source projects having to pay for such a signing feature sounds somewhat alien to me and I am not familiar with the infrastructure behind it. To make that clear, I am not willing to pay anything.
ryanerwin commented May 22, 2017
Nope, unfortunately the free certificates are connected to Letsencrypt which doesn’t support (SPC) code signing certificates. The reason is that all of Letsencrypt processes are automatic, so they would not be helpful in determining if a publisher is trustworthy.
I suggest a donation button on the wsltty page.
mintty commented May 22, 2017
So why should a certificate that assesses that the publisher controls domain xyz not be usable for code signing?
Anyway, as long as those security nerds don’t endeavour to present their brilliant mechanisms in clear and compact terms, and make reasonable offers to use them, I don’t feel like pursueing this further.
ryanerwin commented May 22, 2017
Sure would be unfortunate if less people end up using wsltty due to these silly code signing issues. Personally I’m amazed at how good WSL is, and how close wsltty gets to the feel of the native gnome-terminal . But conhost is soooooo horrible. Kind of a tragedy if that’s the window that people are looking at WSL through.
- Collect donations on the wsltty github page to fund the code signing certificate purchase and renewal
- Ask for volunteer contributors that already have a code signing certificate and can sign wsltty at each release
- Provide detailed instructions that encourage users to compile wsltty themselves
mintty commented May 22, 2017
- Collect donations on the wsltty github page to fund the code signing certificate purchase and renewal
I guess my calculation would look like:
80$ – expense for certificate
200$ – compensation for effort and time spent on acquiring it
500$ – indemnification for mental twisting about certificate quirks
Don’t know how long it would take to collect the lump sum.
- Ask for volunteer contributors that already have a code signing certificate and can sign wsltty at each release
Hmm. Hmmmm. I’d prefer to be able to actually build the package myself. But maybe.
Aren’t there any community certificates, perhaps? Or a web service offering the packaging, including the signing. From source maybe, to ensure no malware is uploaded?
- Provide detailed instructions that encourage users to compile wsltty themselves
Such instructions are available: home page, «Installation from source repository». Would be easier though if ported to native WSL build. But this would require MS to support hybrid applications (using Windows APIs from WSL).
mintty commented May 22, 2017
See also #20 (comment);
the package could be wrapped in a Debian/Ubuntu package for WSL-based installation.
PhilipDaniels commented May 22, 2017
Price seems to have gone up a bit though.
mintty commented May 22, 2017
If you click on «Buy now», offers look different than before. 28€ open-source, 13€ professional, that’s counter-intuitive; also, would that be 28€ one-time or per year? Not very trust-building.
mintty commented May 22, 2017
Please recheck with 0.7.7.1.
willpower232 commented May 22, 2017
fti7 commented Jun 20, 2017
Any News here?
I got an Virus Warning from Symantec Endpoint Protection
Version/Installer Used: 0.7.7.2
Scan type: Auto-Protect Scan
Event: Security Risk Found!
Security risk detected: WS.Reputation.1
File: C:\Users\xxx\Downloads\wsltty-0.7.7.2-install.exe
Location: Quarantine
Computer: xxx
User: xxxx
Action taken: Quarantine succeeded : Access denied
Date found: Dienstag, 20. Juni 2017 16:51:07
mintty commented Jun 20, 2017
- There’s now also the option to install WSLtty from the repository (download or git checkout), provided you install a basic cygwin environment.
- Someone is planning on a third-party installer package (#30).
No news about the idea to sign the installer, whether that would help at all, and how it might work out.
nyuszika7h commented Jul 20, 2017 •
@fti7 WS.Reputation.1 does not mean malware, it means «likely to be a security risk» based on (indirect) community feedback. This is not surprising for an unsigned executable.
fti7 commented Jul 20, 2017
Sure 🙂 but unfortunately our Company Policy Blocks this kind of threat 🙁
lucastheisen commented Jul 21, 2017
The installer got blocked by our corporate scanner due to SONAR.Cryptlck!g147 .
paperclip commented Jul 22, 2017
According https://www.symantec.com/security_response/writeup.jsp?docid=2017-042422-5011-99 »
SONAR.Cryptlck!g147 is a heuristic detection to detect known variants of the Ransom.Cryptolocker family of threats. »
So it’s not a direct detection, but another of the heuristic checks, that might or might not be fixed with signing. Probably best to report to symantec as a false positive.
mintty commented Jul 22, 2017
. best to report to symantec as a false positive.
Thanks. May please somebody do so.
lucastheisen commented Jul 22, 2017
Thanks. May please somebody do so.
Your submission has been sent Sat Jul 22 08:31:33 PDT 2017. To make another submission, click here.
Symantec Security Response
lucastheisen commented Jul 22, 2017
Heard back from symantec. The agreed stating that after their investigation it was a false positive and will be whitelisted within the next 72 hours. I would paste the contents of their response, but the bottom of the email states that would be prohibited.
fuzzykiller commented Jul 31, 2017
So why should a certificate that assesses that the publisher controls domain xyz not be usable for code signing?
Because it does not have the appropriate certificate usage (Code Signing, OID 1.3.6.1.5.5.7.3.3) set. Even if you were to sign your code with it, it would not be a valid signature.
You may(!) have success with the Windows Application Certification Kit, as per this answer. I doubt it’s applicable here though.
mintty commented Jul 31, 2017
Thank you for contributing this information.
That means, however, that I’ll probably just close this issue as there is no remedy feasible.
Maybe issue #30 will help, once there is a 3rd party package.
ukreddy-erwin commented Aug 30, 2017
I am facing similar issue,so I have signed our product with godaddy certificate buy purchasing it.
But the screen still appears.
As in the below link it is mentioned as it depends on the download frequency.
mintty commented Oct 23, 2017
#63 should eventually and finally resolve this issue.
navossoc commented Oct 29, 2017 •
@mintty A few years ago some certification authorities supported open source projects and provided certificates for digital code signing.
Like certum: https://www.certum.eu/certum/cert,offer_en_open_source_cs.xml
Not sure how it works now. It needs some research.
Anyway, to avoid for sure the Microsoft SmartScreen screen you will need a EV certificate. With a «standard» certificate you may need to build reputation, but it will be much easier than if it had not been signed at all.
About the #63, to submit Windows Store Apps you will probably need to sign it too 🤣
https://msdn.microsoft.com/en-us/library/windows/apps/br230260(v=vs.85).aspx
(except you will not have to worry with the smartscreen)
Selling digital certificates is a good way to get rich.
So, yeah, it sucks and maybe we are on the wrong line of work.
mintty commented Oct 30, 2017
Thanks for the hint. The information on their page is ambiguous so I sent them an enquirey and got the information that there is no free service. Still unclear whether the 28€ package is sufficient or the 86€ package with hardware would be needed. However, although I could easily afford it, I see no justification for spending money on my own open source project, nor the investigation into all the know-how, to add that. Some other way will have to be found. Or not.
navossoc commented Oct 30, 2017
I was reading about it and I think the «free service» become this 28€/86€ package.
If they (support) really can’t explain that, maybe it is best to leave at it is 😆
The process of signing the file is not complicated, at the beginning it’s just a pain in the ass, but once you automate is painless.
Either way, it is not a certificate that will tell us whether the file is trusted or not.
So I don’t care either, I was just trying to share some knowledge 😛
mintty commented Oct 30, 2017
Yes, thanks for sharing your knowledge. Could you perhaps share some more:
The process of signing the file is not complicated, at the beginning it’s just a pain in the ass, but once you automate is painless.
. in order to save me the pain in the ass (which, as I had claimed a few times here and in other issues, I am not willing to invest :/ ), by providing reproducible steps for actual signing, preferably command-line only? (Assuming I had a certificate eventually from somewhere. )
navossoc commented Oct 30, 2017 •
@mintty To be honest I ended up here by accident, then I saw the discussion and thrown a few words.
For what I have understand, you have a installer (.exe) that is currently unsigned.
A few years ago I got a certificate for driver signing and is real pain in the ass to get started with it.
First of all, you will need to buy a code sign certificate.
There are two major kinds: Regular and EV.
- Regular: You can use it to sign a .exe, .dll, java applets, etc. (Including drivers*, but Microsoft has changed some policies on Windows 10)
- EV: It does the same thing, but will get reputation on SmartScreen .
The EV certificates are really expensive and are extremely boring to get, because they (certification authorities) sell it for companies only (there a few exceptions) and will require a hardware token to store it.
It seems the EV is the only way to solve this SmartScreen issue for sure, but you may get a good reputation with a regular certificate.
After you purchase it, you will need to do some proof of identity.
They will likely call you or chat with you by webcam and will require you sign some documents.
After all this bureaucracy, you will get a email with a link to generate your own certificate.
If you use Internet Explorer, the process is really painless.
Just click the link, it will generate a certificate on your computer.
Having the certificate installed on your system, now you really can starting signing files.
There are a few ways to do it.
The easier one, just for testing, you can use a DigiCert Certificate Utility.
Just select the file and sign it. Test it and see if it works as planned.
(It really works with any certificate, it doesn’t matter if the certificate is not issued by DigiCert)
Considering everything goes ok, you can start automating it.
I’m using the signtool , you can get it by downloading Windows SDK.
It will be located on:
C:\Program Files (x86)\Windows Kits\10\bin\10.0.16299.0\x86
C:\Program Files (x86)\Windows Kits\10\bin\10.0.16299.0\x64
You can use something like this to automate it:
CERTSHA2 is the thumbprint of the certificate, you can check on the details tab.
I am not sure where you will build the installer, but for extra security.
You can also export your certificate with the private key and re import it using the «strong private key protection» and making it non exportable.
Be careful here, or you may need to generate another certificate.
There is another way too.
You can export it to a .pfx file and use it directly from the command line with a password (/f and /p flags).
This option is good if you use a build environment.
I prefer to use it on the Windows Certificate Store, because I sign files only on this computer.
Since you are targeting Windows 10, you don’t need to worry with sha1 certificates and windows patches that need to be installed on the clients.
Let me know if you need more details about any step.
English is not my native language, so it may be not as clear as I think I wrote it.