RAMMap v1.60
By Mark Russinovich
Published: October 15, 2020

Run now from Sysinternals Live.
Have you ever wondered exactly how Windows is assigning physical memory, how much file data is cached in RAM, or how much RAM is used by the kernel and device drivers? RAMMap makes answering those questions easy. RAMMap is an advanced physical memory usage analysis utility for Windows Vista and higher. It presents usage information in different ways on its several different tabs:
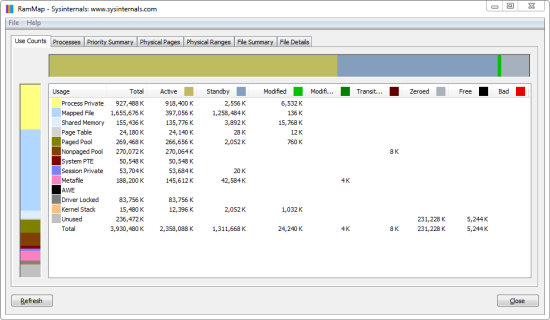
- Use Counts: usage summary by type and paging list
- Processes: process working set sizes
- Priority Summary: prioritized standby list sizes
- Physical Pages: per-page use for all physical memory
- Physical Ranges: physical memory addresses
- File Summary: file data in RAM by file
- File Details: individual physical pages by file
Use RAMMap to gain understanding of the way Windows manages memory, to analyze application memory usage, or to answer specific questions about how RAM is being allocated. RAMMap’s refresh feature enables you to update the display and it includes support for saving and loading memory snapshots.
For definitions of the labels RAMMap uses as well as to learn about the physical-memory allocation algorithms used by the Windows memory manager, please see Windows Internals, 5^th^ Edition.
Related Links
- Windows Internals Book The official updates and errata page for the definitive book on Windows internals, by Mark Russinovich and David Solomon.
- Windows Sysinternals Administrator’s ReferenceThe official guide to the Sysinternals utilities by Mark Russinovich and Aaron Margosis, including descriptions of all the tools, their features, how to use them for troubleshooting, and example real-world cases of their use.

Run now from Sysinternals Live.
Runs on:
- Client: Windows Vista and higher.
- Server: Windows Server 2008 and higher.
Memory-mapped files
A memory-mapped file contains the contents of a file in virtual memory. This mapping between a file and memory space enables an application, including multiple processes, to modify the file by reading and writing directly to the memory. You can use managed code to access memory-mapped files in the same way that native Windows functions access memory-mapped files, as described in Managing Memory-Mapped Files.
There are two types of memory-mapped files:
Persisted memory-mapped files
Persisted files are memory-mapped files that are associated with a source file on a disk. When the last process has finished working with the file, the data is saved to the source file on the disk. These memory-mapped files are suitable for working with extremely large source files.
Non-persisted memory-mapped files
Non-persisted files are memory-mapped files that are not associated with a file on a disk. When the last process has finished working with the file, the data is lost and the file is reclaimed by garbage collection. These files are suitable for creating shared memory for inter-process communications (IPC).
Processes, Views, and Managing Memory
Memory-mapped files can be shared across multiple processes. Processes can map to the same memory-mapped file by using a common name that is assigned by the process that created the file.
To work with a memory-mapped file, you must create a view of the entire memory-mapped file or a part of it. You can also create multiple views to the same part of the memory-mapped file, thereby creating concurrent memory. For two views to remain concurrent, they have to be created from the same memory-mapped file.
Multiple views may also be necessary if the file is greater than the size of the application’s logical memory space available for memory mapping (2 GB on a 32-bit computer).
There are two types of views: stream access view and random access view. Use stream access views for sequential access to a file; this is recommended for non-persisted files and IPC. Random access views are preferred for working with persisted files.
Memory-mapped files are accessed through the operating system’s memory manager, so the file is automatically partitioned into a number of pages and accessed as needed. You do not have to handle the memory management yourself.
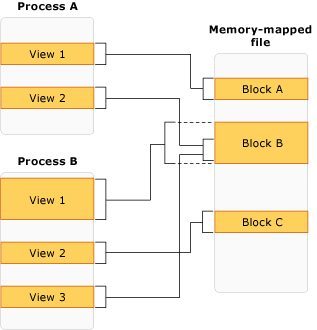
The following illustration shows how multiple processes can have multiple and overlapping views to the same memory-mapped file at the same time.
The following image shows multiple and overlapped views to a memory-mapped file:
Programming with Memory-Mapped Files
The following table provides a guide for using memory-mapped file objects and their members.
| Task | Methods or properties to use |
|---|---|
| To obtain a MemoryMappedFile object that represents a persisted memory-mapped file from a file on disk. | MemoryMappedFile.CreateFromFile method. |
| To obtain a MemoryMappedFile object that represents a non-persisted memory-mapped file (not associated with a file on disk). | MemoryMappedFile.CreateNew method. MemoryMappedFile.CreateOrOpen method. |
| To obtain a MemoryMappedFile object of an existing memory-mapped file (either persisted or non-persisted). | MemoryMappedFile.OpenExisting method. |
| To obtain a UnmanagedMemoryStream object for a sequentially accessed view to the memory-mapped file. | MemoryMappedFile.CreateViewStream method. |
| To obtain a UnmanagedMemoryAccessor object for a random access view to a memory-mapped fie. | MemoryMappedFile.CreateViewAccessor method. |
| To obtain a SafeMemoryMappedViewHandle object to use with unmanaged code. | MemoryMappedFile.SafeMemoryMappedFileHandle property. MemoryMappedViewStream.SafeMemoryMappedViewHandle property. |
| To delay allocating memory until a view is created (non-persisted files only). (To determine the current system page size, use the Environment.SystemPageSize property.) | CreateNew method with the MemoryMappedFileOptions.DelayAllocatePages value. CreateOrOpen methods that have a MemoryMappedFileOptions enumeration as a parameter. |
Security
You can apply access rights when you create a memory-mapped file, by using the following methods that take a MemoryMappedFileAccess enumeration as a parameter:
You can specify access rights for opening an existing memory-mapped file by using the OpenExisting methods that take an MemoryMappedFileRights as a parameter.
In addition, you can include a MemoryMappedFileSecurity object that contains predefined access rules.
To apply new or changed access rules to a memory-mapped file, use the SetAccessControl method. To retrieve access or audit rules from an existing file, use the GetAccessControl method.
Examples
Persisted Memory-Mapped Files
The CreateFromFile methods create a memory-mapped file from an existing file on disk.
The following example creates a memory-mapped view of a part of an extremely large file and manipulates a portion of it.
If you would like to see code comments translated to languages other than English, let us know in this GitHub discussion issue.
The following example opens the same memory-mapped file for another process.
Non-Persisted Memory-Mapped Files
The CreateNew and CreateOrOpen methods create a memory-mapped file that is not mapped to an existing file on disk.
The following example consists of three separate processes (console applications) that write Boolean values to a memory-mapped file. The following sequence of actions occur:
Process A creates the memory-mapped file and writes a value to it.
Process B opens the memory-mapped file and writes a value to it.
Process C opens the memory-mapped file and writes a value to it.
Process A reads and displays the values from the memory-mapped file.
After Process A is finished with the memory-mapped file, the file is immediately reclaimed by garbage collection.
To run this example, do the following:
Compile the applications and open three Command Prompt windows.
In the first Command Prompt window, run Process A .
In the second Command Prompt window, run Process B .
Return to Process A and press ENTER.
In the third Command Prompt window, run Process C .
Memory Map (x86)
This article describes the contents of the computer’s physical memory at the moment that the BIOS jumps to your bootloader code.
Contents
Real mode address space (
When a typical x86 PC boots it will be in Real Mode, with an active BIOS. During the time the CPU remains in Real Mode, IRQ0 (the clock) will fire repeatedly, and the hardware that is used to boot the PC (floppy, hard disk, CD, Network card, USB) will also generate IRQs. This means that during the PC boot process, the Real Mode IVT (see below) must be carefully preserved, because it is being used.
When the IVT is activated by an IRQ, it will call a BIOS routine to handle the IRQ. Bootloaders will also access BIOS functions. This means that the two memory workspaces that the BIOS uses (the BDA and the EBDA) must also be carefully preserved during boot. Also, every time the BIOS handles an IRQ0 (18 times a second), several bytes in the BDA get overwritten by the BIOS — so do not attempt to store anything there while IRQs are active in Real Mode.
After all the BIOS functions have been called, and your kernel is loaded into memory somewhere, the bootloader or kernel may exit Real Mode forever (often by going into 32bit Protected Mode). If the kernel never uses Real Mode again, then the first 0x500 bytes of memory in the PC may be reused and overwritten. (However, it is very common to temporarily return to Real Mode in order to change the Video Display Mode.)
When the CPU is in Protected Mode, System Management Mode (SMM) is still invisibly active, and cannot be shut off. SMM also seems to use the EBDA. So the EBDA memory area should never be overwritten.
Note: the EBDA is a variable-sized memory area (on different BIOSes). If it exists, it is always immediately below 0xA0000 in memory. It is absolutely guaranteed to be at most 128 KiB in size. Older computers typically uses 1 KiB from 0x9FC00 — 0x9FFFF, modern firmware can be found using significantly more. You can determine the size of the EBDA by using BIOS function INT 12h, or by examining the word at 0x413 in the BDA (see below). Both of those methods will tell you how much conventional memory is usable before the EBDA.
It should also be noted that your bootloader code is loaded and running in memory at physical addresses 0x7C00 through 0x7DFF. So that memory area is likely to also be unusable until execution has been transferred to a second stage bootloader, or to your kernel.
Overview
| Real mode address space (the first MiB) | |||||
|---|---|---|---|---|---|
| 0x00000000 | 0x000003FF | 1 KiB | Real Mode IVT (Interrupt Vector Table) | unusable in real mode | 640 KiB RAM («Low memory») |
| 0x00000400 | 0x000004FF | 256 bytes | BDA (BIOS data area) | ||
| 0x00000500 | 0x00007BFF | almost 30 KiB | Conventional memory | usable memory | |
| 0x00007C00 | 0x00007DFF | 512 bytes | Your OS BootSector | ||
| 0x00007E00 | 0x0007FFFF | 480.5 KiB | Conventional memory | ||
| 0x00080000 | 0x0009FFFF | 128 KiB | EBDA (Extended BIOS Data Area) | partially used by the EBDA | |
| 0x000A0000 | 0x000BFFFF | 128 KiB | Video display memory | hardware mapped | 384 KiB System / Reserved («Upper Memory») |
| 0x000C0000 | 0x000C7FFF | 32 KiB (typically) | Video BIOS | ROM and hardware mapped / Shadow RAM | |
| 0x000C8000 | 0x000EFFFF | 160 KiB (typically) | BIOS Expansions | ||
| 0x000F0000 | 0x000FFFFF | 64 KiB | Motherboard BIOS | ||
BIOS Data Area (BDA)
The BDA is only partially standardized and mostly relevant for real mode BIOS operations. The following is a partial list. See the External Links references below for more detail.
| start | end | size | region/exception | description |
|---|---|---|---|---|
| High Memory | ||||
| 0x00100000 | 0x00EFFFFF | 0x00E00000 (14 MiB) | RAM — free for use (if it exists) | Extended memory 1, 2 |
| 0x00F00000 | 0x00FFFFFF | 0x00100000 (1 MiB) | Possible memory mapped hardware | ISA Memory Hole 15-16MB 3 |
| 0x01000000 | . | . (whatever exists) | RAM — free for use | More Extended memory 1 |
| 0xC0000000 (sometimes, depends on motherboard and devices) | 0xFFFFFFFF | 0x40000000 (1 GiB) | various (typically reserved for memory mapped devices) | Memory mapped PCI devices, PnP NVRAM?, IO APIC/s, local APIC/s, BIOS, . |
| 0x0000000100000000 (possible memory above 4 GiB) | . | . (whatever exists) | RAM — free for use (PAE/64bit) | More Extended memory 1 |
| . | . | . | Possible memory mapped hardware | Potentially usable for memory mapped PCI devices in modern hardware (but typically not, due to backward compatibility) |
1 : Different computers have different amounts of RAM, therefore the amount of extended memory you might find will vary and may be anything from «none» (e.g. an old 80386 system) to «lots».
2 : Free for use except that your bootloader (ie. GRUB) may have loaded your «modules» here, and you don’t want to overwrite those.